采用Ingress暴露容器化应用(Nginx)
1.部署容器化应用
[root@k8smaster ~]# kubectl create deployment nginx --image=nginx
deployment.apps/nginx created
2.暴露该服务
[root@k8smaster ~]# kubectl expose deployment nginx --port=80 --target-port=80 --type=NodePort
service/nginx exposed
[root@k8smaster ~]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 47h
nginx NodePort 10.107.162.17 <none> 80:32159/TCP 34s
springboot-k8s NodePort 10.104.165.244 <none> 8080:31129/TCP 6h24m
tomcat NodePort 10.108.243.100 <none> 8080:31891/TCP 32h
3.部署ingress inginx
[root@k8smaster ~]# kubectl apply -f ingress-deploy.yaml
namespace/ingress-nginx created
serviceaccount/ingress-nginx created
configmap/ingress-nginx-controller created
clusterrole.rbac.authorization.k8s.io/ingress-nginx created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created
role.rbac.authorization.k8s.io/ingress-nginx created
rolebinding.rbac.authorization.k8s.io/ingress-nginx created
service/ingress-nginx-controller-admission created
service/ingress-nginx-controller created
deployment.apps/ingress-nginx-controller created
validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created
serviceaccount/ingress-nginx-admission created
clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
role.rbac.authorization.k8s.io/ingress-nginx-admission created
rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
job.batch/ingress-nginx-admission-create created
job.batch/ingress-nginx-admission-patch created
[root@k8smaster ~]#
4.查看ingress状态
[root@k8smaster ~]# kubectl get service -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.99.29.48 <none> 80:31771/TCP,443:32731/TCP 59s
ingress-nginx-controller-admission ClusterIP 10.98.171.141 <none> 443/TCP 59s
[root@k8smaster ~]# kubectl get deploy -n ingress-nginx
NAME READY UP-TO-DATE AVAILABLE AGE
ingress-nginx-controller 0/1 1 0 77s
[root@k8smaster ~]# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-p6xhl 0/1 Completed 0 92s
ingress-nginx-admission-patch-lxm5j 0/1 Completed 3 92s
ingress-nginx-controller-668848df7f-kw62q 0/1 Running 0 92s
5.创建ingress规则
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: k8s-ingress
spec:
rules:
- host: www.abc.com
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: nginx
port:
number: 80
[root@k8smaster ~]#
[root@k8smaster ~]# kubectl apply -f ingress-nginx-rule.yaml
ingress.networking.k8s.io/k8s-ingress created
[root@k8smaster ~]#
6.查规则
[root@k8smaster ~]# kubectl get ing
Warning: extensions/v1beta1 Ingress is deprecated in v1.14+, unavailable in v1.22+; use networking.k8s.io/v1 Ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
k8s-ingress <none> www.abc.com 192.168.1.201 80 73s
[root@k8smaster ~]#
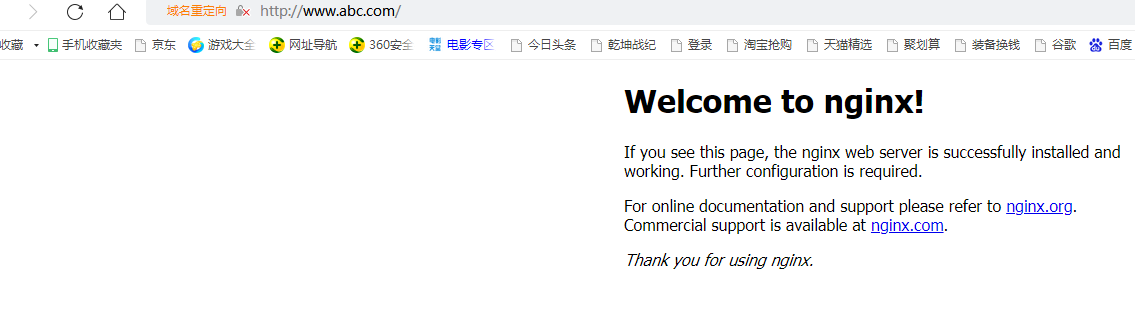
访问:http://192.168.1.201/
或者电脑C:\Windows\System32\drivers\etc 修改hosts 加上192.168.1.201 www.abc.com 然后浏览器访问www.abc.com



 浙公网安备 33010602011771号
浙公网安备 33010602011771号