工作随笔----fip.bin镜像介绍
fip.bin 文件说明
fip.bin文件的结构说明
/*
* load_addr_hi and load_addr_lo: image load address.
* image_id: 0 - pager, 1 - paged
* size: image size in bytes.
*/
typedef struct optee_image {
uint32_t load_addr_hi;
uint32_t load_addr_lo;
uint32_t image_id;
uint32_t size;
} optee_image_t;
#define TEE_MAGIC_NUM_OPTEE 0x4554504f
/*
* magic: header magic number.
* version: OPTEE header version:
* 1 - not supported
* 2 - supported
* arch: OPTEE os architecture type: 0 - AARCH32, 1 - AARCH64.
* flags: unused currently.
* nb_images: number of images.
*/
typedef struct optee_header {
uint32_t magic;
uint8_t version;
uint8_t arch;
uint16_t flags;
uint32_t nb_images;
optee_image_t optee_image_list[];
} optee_header_t;
系统启动的打印信息:
OPTEE header info:
INFO: magic=0x4554504f
INFO: version=0x2
INFO: arch=0x0
INFO: flags=0x0
INFO: nb_images=0x2
Image id=4 loaded: 0x2ffc0000 - 0x2ffc002c
INFO: OPTEE ep=0x2ffc0000
Fip文件具体组成如下:
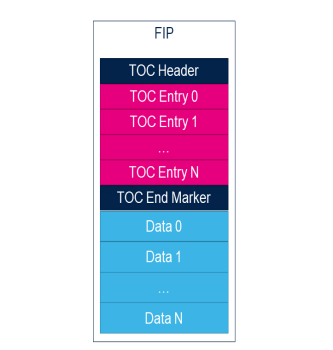
name`: The name of the ToC. This is currently used to validate the header.
`serial_number`: A non-zero number provided by the creation tool
`flags`: Flags associated with this data.
Bits 0-31: Reserved
Bits 32-47: Platform defined
Bits 48-63: Reserved
A ToC entry has the following fields:
`uuid`: All files are referred to by a pre-defined Universally Unique
IDentifier [UUID] . The UUIDs are defined in
`include/tools_share/firmware_image_package.h`. The platform translates
the requested image name into the corresponding UUID when accessing the
package.
`offset_address`: The offset address at which the corresponding payload data
can be found. The offset is calculated from the ToC base address.
`size`: The size of the corresponding payload data in bytes.
`flags`: Flags associated with this entry. None are yet defined.
typedef struct fip_toc_header {
uint32_t name;
uint32_t serial_number;
uint64_t flags;
} fip_toc_header_t; 16字节
typedef struct fip_toc_entry {
uuid_t uuid; 16字节
uint64_t offset_address;
uint64_t size;
uint64_t flags;
} fip_toc_entry_t; 40字节
#define TOC_HEADER_NAME 0xAA640001
toc end marker 没有找到具体的说明,推算出长度是200字节
Toc文件头总长度 296(16+40+40+200)字节
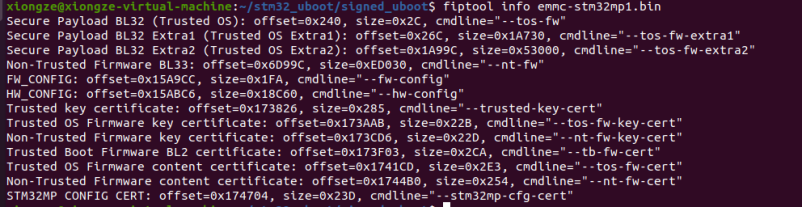
查看fip文件信息 fiptool info ../fip/fip-stm32mp151c-wb-optee.bin
Secure Payload BL32 (Trusted OS): offset=0x128, size=0x2C, cmdline="--tos-fw"
Secure Payload BL32 Extra1 (Trusted OS Extra1): offset=0x154, size=0x1A730, cmdline="--tos-fw-extra1"
Secure Payload BL32 Extra2 (Trusted OS Extra2): offset=0x1A884, size=0x53000, cmdline="--tos-fw-extra2"
Non-Trusted Firmware BL33: offset=0x6D884, size=0xED0BC, cmdline="--nt-fw" 文件大小448644
FW_CONFIG: offset=0x15A940, size=0x1FA, cmdline="--fw-config" 文件大小506
HW_CONFIG: offset=0x15AB3A, size=0x170F8, cmdline="--hw-config" 文件大小94456
文件说明:
--soc-fw FILENAME EL3 Runtime Firmware BL31
--tos-fw FILENAME Secure Payload BL32 (Trusted OS)
--tos-fw-extra1 FILENAME Secure Payload BL32 Extra1 (Trusted OS Extra1)
--tos-fw-extra2 FILENAME Secure Payload BL32 Extra2 (Trusted OS Extra2)
--nt-fw FILENAME Non-Trusted Firmware BL33
--hw-config u-boot.dtb
--nt-fw u-boot-nodtb.bin不带dtb 的 uboot
-machine:~/stm32_uboot/output/optee$ fiptool unpack ../fip/fip-stm32mp151c-wb-optee.bin 解压后得到如下6个文件
tos-fw.bin tos-fw-extra1.bin tos-fw-extra2.bin nt-fw.bin fw-config.bin hw-config.bin
对应的源文件如下:
tee-header_v2-stm32mp151c-wb.bin ------> tos-fw.bin
tee-pager_v2-stm32mp151c-wb.bin ---> tos-fw-extra1.bin
tee-pageable_v2-stm32mp151c-wb.bin ----> tos-fw-extra2.bin
Build/optee/ftds/stm32mp151c-wb-fw-config.dtb ------> fw-config.bin
Build/defconfig/u-boot-stm32mp151c-wb.dtb ---> hw-config.bin
U-boot.bin 前448644字节数据 ----> nt-fw.bin 即该bin文件时不包含设备树的uboot文件
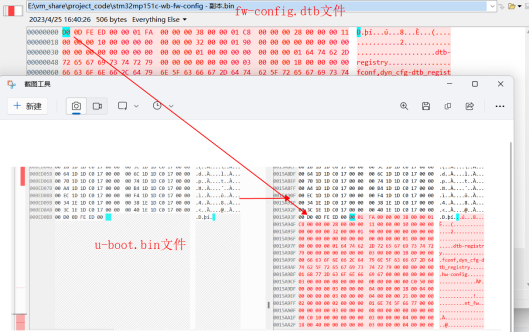
如上图所示,在uboot文件后拼接了stm32mp151c-wb-fw-config.dtb 文件
Data0-2:是 optee 3文件组成,组合的顺序依次是:tee-header_v2-stm32mp151c-wb.bin + tee-pager_v2-stm32mp151c-wb.bin (1a730)+ tee-pageable_v2-stm32mp151c-wb.bin
Data3:是uboot.bin文件0x10c12c:开头数据B8 00 00 EA 14 F0 9F E5 14 F0 9F E5 14 F0 9F E5 14 F0 9F E5 14 F0
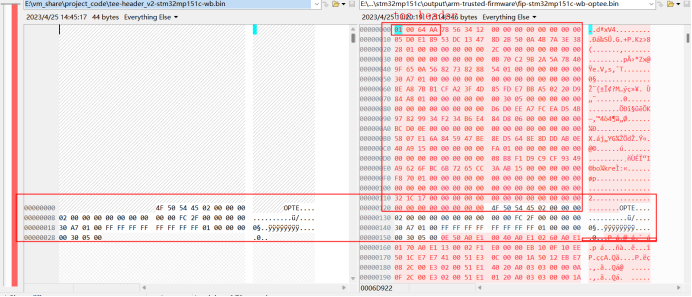
上图说明了 fip文件在header之后开始拼接了tee-header_v2-stm32mp151c-wb.bin 文件的数据
01 00 64 AA 78 56 34 12 00 00 00 00 00 00 00 00 ||
05 D0 E1 89 53 DC 13 47 8D 2B 50 0A 4B 7A 3E 38
28 01 00 00 00 00 00 00 2C 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00||0B 70 C2 9B 2A 5A 78 40
9F 65 0A 56 82 73 82 88 54 01 00 00 00 00 00 00
30 A7 01 00 00 00 00 00 00 00 00 00 00 00 00 00 ||
8E A8 7B B1 CF A2 3F 4D 85 FD E7 BB A5 02 20 D9
84 A8 01 00 00 00 00 00 00 30 05 00 00 00 00 00 //第三个文件的大小
00 00 00 00 00 00 00 00||D6 D0 EE A7 FC EA D5 4B
97 82 99 34 F2 34 B6 E4 84 D8 06 00 00 00 00 00
BC D0 0E 00 00 00 00 00 00 00 00 00 00 00 00 00 ||
58 07 E1 6A 84 59 47 BE 8E D5 64 8E 8D DD AB 0E
40 A9 15 00 00 00 00 00 FA 01 00 00 00 00 00 00
00 00 00 00 00 00 00 00||08 B8 F1 D9 C9 CF 93 49
A9 62 6F BC 6B 72 65 CC 3A AB 15 00 00 00 00 00
F8 70 01 00 00 00 00 00 00 00 00 00 00 00 00 00 ||
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
说明:以上的实际数据分析是基于不带证书的fip文件
带证书的fip文件信息如下所示:
测试发现 使用加签后的fip文件和单个源文件进行数据比较,发现不能再找到相同的数据段,说明fip加签后,针对每一个源文件都进行了加密处理。
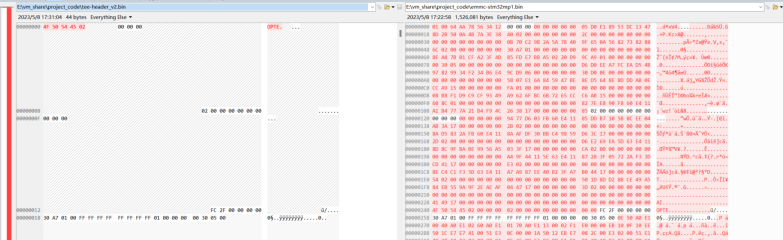
上图可以看出在header之后并没有拼接完整的 tee-header_v2-stm32mp151c-wb.bin 文件数据,而是源文件数据被“打乱”了。
以上是对fip镜像的数据的一些分析,该fip的生成时用fiptool工具生成,实质就是把 bl31 bl32 bl33 镜像组合打包。同时也可以带上证书参数来对fip进行签名,可以用fiptool info 命令对fip进行"解压" 得到制作fip镜像包含的源文件。





 浙公网安备 33010602011771号
浙公网安备 33010602011771号