1、拉取helm charts,修改values文件,部署无tls的harbor仓库
helm repo add harbor https://helm.goharbor.io
helm repo update
helm pull harbor/harbor --version 1.12.6 --untar
cd harbor/
# values.yaml
···
···
expose:
type: ingress
ingress:
···
className: "traefik" # 使用traefik的ingress,这里根据你自己的来
···
hosts:
core: harbor.xwk.local # 设置域名
···
annotations:
kubernetes.io/ingress.class: "traefik" # 指定traefik ingress类
ingress.kubernetes.io/proxy-body-size: "20G" # 允许最大上传文件的大小
tls:
enabled: false # 先尝试使用无证书的方式部署一次,然后再开启他
···
externalURL: http://harbor.xwk.local # 域名,先不用https
···
harborAdminPassword: "xxxxx" # 设置密码
···
persistence:
enabled: true
resourcePolicy: "keep"
persistentVolumeClaim:
registry:
storageClass: "nfs-data" # 使用自己创建的存储类
accessMode: ReadWriteOnce
size: 5Gi # 大小自己定
chartmuseum:
storageClass: "nfs-data"
accessMode: ReadWriteOnce
size: 1Gi
jobservice:
storageClass: "nfs-data"
accessMode: ReadWriteOnce
size: 1Gi
database:
storageClass: "nfs-data"
accessMode: ReadWriteOnce
size: 1Gi
redis:
storageClass: "nfs-data"
accessMode: ReadWriteOnce
size: 5Gi
# 安装
helm install harbor -n harbor -f values.yaml .
# 确认状态
[root@master-11 harbor]# kubectl get pods -n harbor
NAME READY STATUS RESTARTS AGE
harbor-core-5ffbd9b549-7rnpg 1/1 Running 1 (84m ago) 22h
harbor-database-0 1/1 Running 1 (84m ago) 22h
harbor-jobservice-55b485f64-29ngv 1/1 Running 6 (82m ago) 22h
harbor-notary-server-65c8c65697-t4f8k 1/1 Running 4 (83m ago) 22h
harbor-notary-signer-bc9795958-c5qwm 1/1 Running 4 (83m ago) 22h
harbor-portal-7b479c466b-wtcrx 1/1 Running 1 (84m ago) 23h
harbor-redis-0 1/1 Running 1 (84m ago) 22h
harbor-registry-6677c6c9fd-2rjwk 2/2 Running 2 (84m ago) 22h
harbor-trivy-0 1/1 Running 1 (84m ago) 22h
2、尝试访问 (记得把你的代理全部都关了,不然会访问不到的)
# 添加hosts解析
echo "10.0.0.200 harbor.xwk.local" >> /etc/hosts # windows记得也添加一下
[root@master-11 harbor]# curl harbor.xwk.local
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8"/>
<title>Harbor</title>
<base href="/"/>
<meta name="viewport" content="width=device-width, initial-scale=1"/>
<link rel="icon" type="image/x-icon" href="favicon.ico?v=2"/>
<link rel="stylesheet" href="styles.878b6852c9b5f5ec.css"></head>
<body>
<harbor-app>
<div class="spinner spinner-lg app-loading app-loading-fixed">
Loading...
</div>
</harbor-app>
<script src="runtime.af360c985dadaace.js" type="module"></script><script src="polyfills.b51e06395e4620c9.js" type="module"></script><script src="scripts.67f785a8ff0b6aed.js" defer></script><script src="main.5f8a26ffdcab9d77.js" type="module"></script></body>
</html>

3、创建证书与密钥 (ai帮忙生成的)
# 生成 CA 私钥和 CA 根证书 (有效期 10 年)
openssl req -newkey rsa:4096 -nodes -sha256 -keyout ca.key -x509 -days 3650 -out ca.crt -subj "/C=CN/ST=Beijing/L=Beijing/O=MyCompany/OU=Harbor-CA/CN=harbor-ca"
# 准备 openssl.cnf,指定 SAN
cat > openssl.cnf <<EOF
[ req ]
default_bits = 4096
prompt = no
default_md = sha256
req_extensions = req_ext
distinguished_name = dn
[ dn ]
C = CN
ST = Beijing
L = Beijing
O = MyCompany
OU = Harbor
CN = harbor.xwk.local
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = harbor.xwk.local
DNS.2 = notary.harbor.xwk.local
EOF
# 生成私钥和证书签名请求
openssl req -new -nodes -keyout tls.key -out tls.csr -config openssl.cnf
# 用 CA 证书签发 Harbor TLS 证书
openssl x509 -req -days 3650 -in tls.csr \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-out tls.crt -extensions req_ext -extfile openssl.cnf
# 创建 Kubernetes Secret
kubectl create secret generic harbor-tls \
--from-file=tls.crt --from-file=tls.key --from-file=ca.crt -n harbor
# 将 CA 下发到所有 Harbor 节点的 containerd
mkdir -p /etc/containerd/certs.d/harbor.xwk.local/
cp ca.crt /etc/containerd/certs.d/harbor.xwk.local/ca.crt
mkdir -p /etc/containerd/certs.d/notary.harbor.xwk.local/
cp ca.crt /etc/containerd/certs.d/notary.harbor.xwk.local/ca.crt
4、修改values文件,将tls开启
# values.yaml
tls:
enabled: true # 开启tls
certSource: secret # 将auto改掉
secretName: "harbor-tls" # 指定刚才创建的secret名字
notarySecretName: "harbor-tls" # 指定刚才创建的secret名字
externalURL: https://harbor.xwk.local # 改成https
5、尝试推送镜像
[root@master-11 harbor]# nerdctl login harbor.xwk.local -uadmin
Enter Password:
WARNING: Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
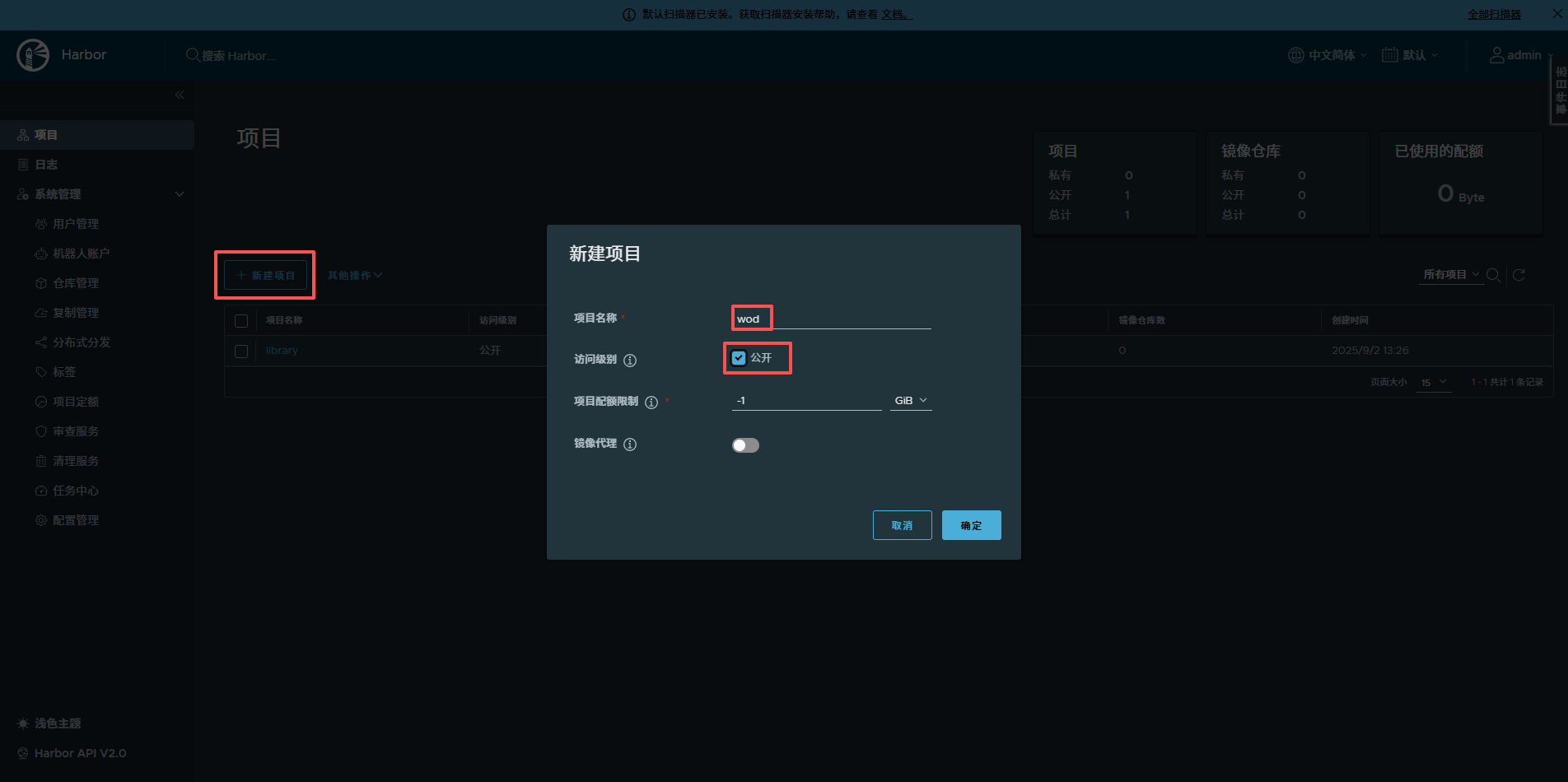
# 访问https://harbor.xwk.local/,不要去访问http,登录不上去的,然后再根据下图创建一个项目
# 拉取镜像并推送到仓库里,看到这个就表示您已经部署成功了
nerdctl pull registry.cn-beijing.aliyuncs.com/xwk123/nginx:aaa
nerdctl tag registry.cn-beijing.aliyuncs.com/xwk123/nginx:aaa harbor.xwk.local/wod/nginx:aaa
[root@master-11 ~]# nerdctl push harbor.xwk.local/wod/nginx:aaa
INFO[0000] pushing as a reduced-platform image (application/vnd.docker.distribution.manifest.v2+json, sha256:00a6cd1701e686b5641df850893ef00cf002df4274ddf8807dcffb4095361f04)
manifest-sha256:00a6cd1701e686b5641df850893ef00cf002df4274ddf8807dcffb4095361f04: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:8d838ad4ffcc14c8d3062c104f359c1570c0c914f4aca5ea7edf2121a5c71823: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 2.6 s total: 11.5 K (4.4 KiB/s)




 浙公网安备 33010602011771号
浙公网安备 33010602011771号