Apache 2 & PHP 8 errors All In One
Apache 2 & PHP 8 errors All In One
errors
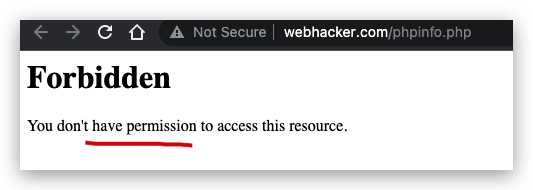
You don‘t have permission to access this resource.❌
http://www.webhacker.com/phpinfo.php
solutions
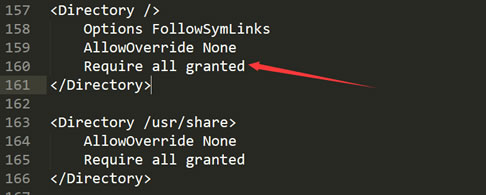
✅ 1. 修改 httpd.conf 配置文件, 把 "Require all denied" 修改成 Require all granted
/usr/local/etc/httpd/httpd.conf
#
# Deny access to the entirety of your server's filesystem. You must
# explicitly permit access to web content directories in other
# <Directory> blocks below.
#
<Directory />
AllowOverride none
# Require all denied
Require all granted
</Directory>
✅ 2. 修改 httpd-vhosts.conf 配置文件, 新增 <Directory /> 配置,并开启 Require all granted
/usr/local/etc/httpd/extra/httpd-vhosts.conf
## PHP 8.1
<VirtualHost *:80>
ServerAdmin webmaster@www.webhacker.com
# DocumentRoot "/Library/WebServer/Documents"
# DocumentRoot "/usr/local/var/www"
DocumentRoot "/usr/local/var/php8"
# DocumentRoot "/usr/local/opt/httpd/docs/php8"
# DocumentRoot "/usr/local/opt/httpd/docs/www.webhacker.com"
<Directory />
AllowOverride none
# Require all denied
Require all granted
</Directory>
ServerName webhacker.com
ServerAlias www.webhacker.com
ErrorLog "/usr/local/var/log/httpd/www.webhacker.com-error_log"
CustomLog "/usr/local/var/log/httpd/www.webhacker.com-access_log" common
</VirtualHost>
demos
http://localhost:80/phpinfo.php
http://www.webhacker.com/phpinfo.php
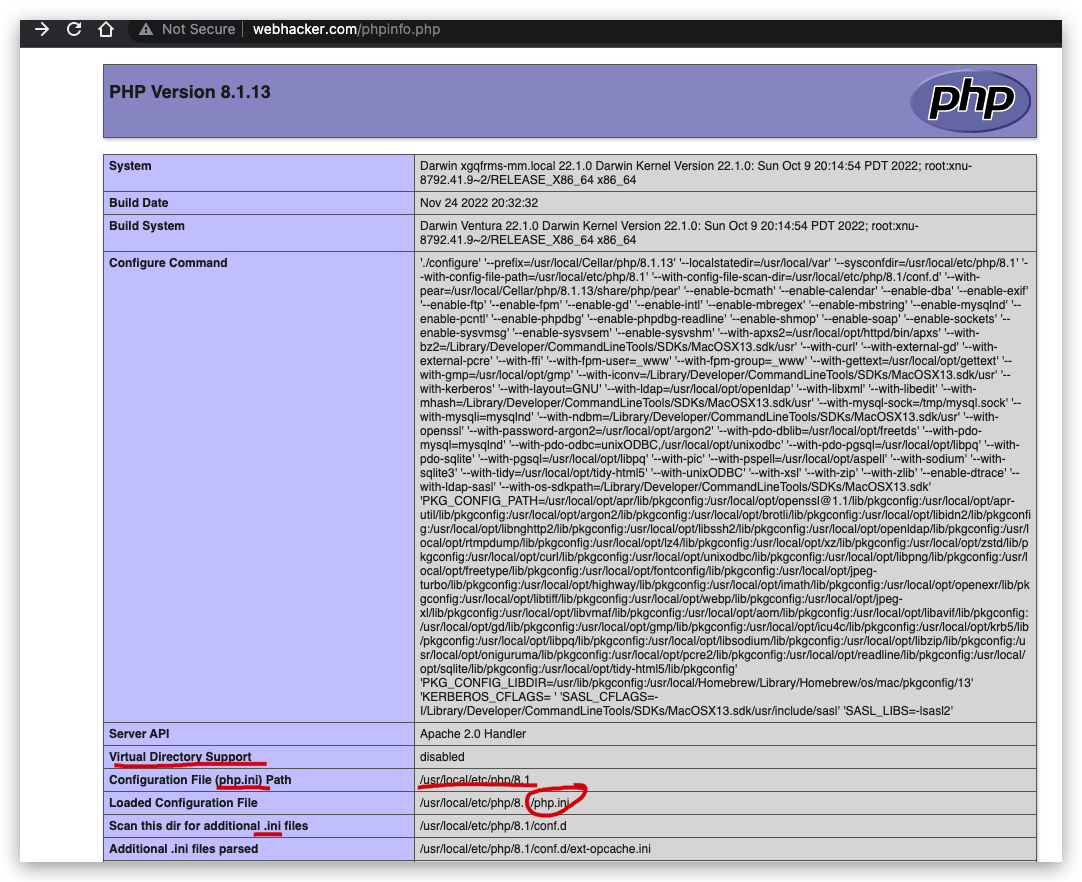
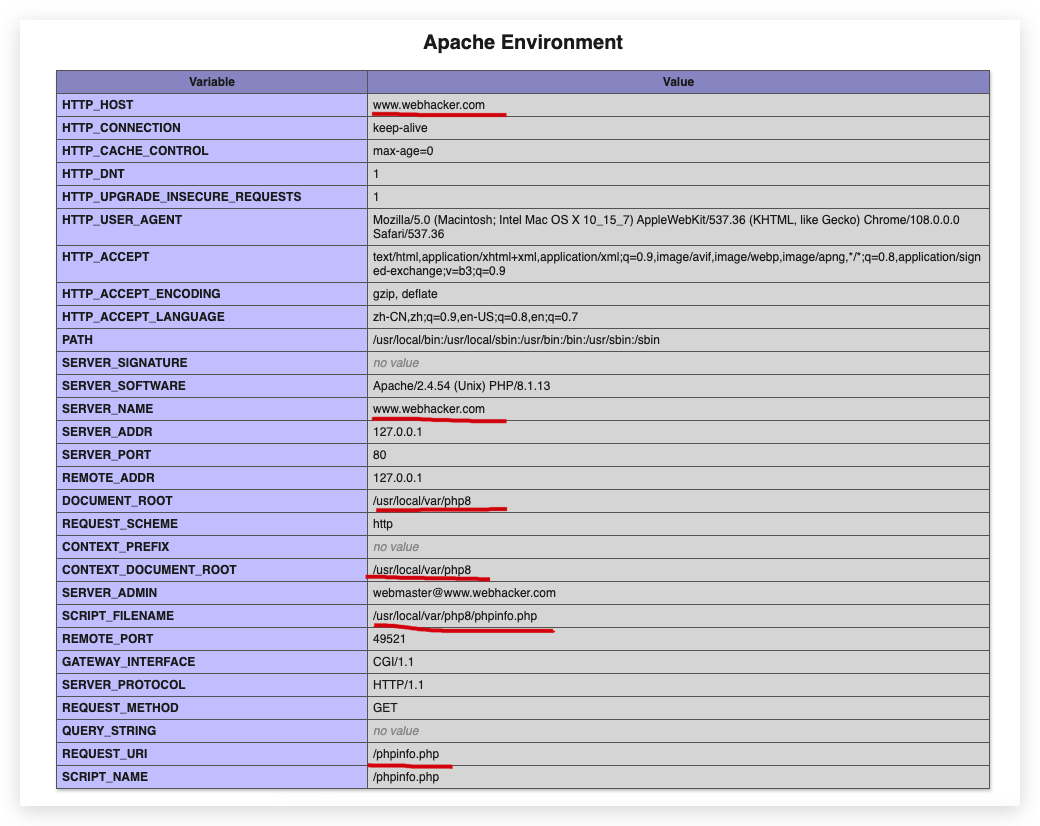
Apache Environment
自定义 hosts 域名

test

http://localhost/xss.php?args=<script>alert("XSS 🐞")</script>
const pre = document.querySelector(`#pre`);
// const args = window.location.search;
const searchParams = (new URL(document.location)).searchParams;
// const args = searchParams.get('args');
for (const [key, value] of searchParams) {
//
}
for (const [key, value] of searchParams.entries()) {
//
}

http://localhost/?args=<script>alert("XSS 🐞")</script>
http://localhost/?args=<script>alert("XSS 🐞")</script>
encodeURIvsencodeURIComponent
encodeURI(`<script>alert("XSS%20🐞")</script>`)
// '%3Cscript%3Ealert(%22XSS%2520%F0%9F%90%9E%22)%3C/script%3E'
encodeURIComponent(`<script>alert("XSS%20🐞")</script>`)
// '%3Cscript%3Ealert(%22XSS%2520%F0%9F%90%9E%22)%3C%2Fscript%3E'
https://developer.mozilla.org/en-US/docs/Web/API/URL/searchParams
https://developer.mozilla.org/en-US/docs/Web/API/URLSearchParams
(🐞 反爬虫测试!打击盗版⚠️)如果你看到这个信息, 说明这是一篇剽窃的文章,请访问 https://www.cnblogs.com/xgqfrms/ 查看原创文章!
refs
https://github.com/xgqfrms/php
https://www.runoob.com/php/php-tutorial.html
https://www.w3school.com.cn/php/php_syntax.asp
©xgqfrms 2012-2021
www.cnblogs.com/xgqfrms 发布文章使用:只允许注册用户才可以访问!
原创文章,版权所有©️xgqfrms, 禁止转载 🈲️,侵权必究⚠️!
本文首发于博客园,作者:xgqfrms,原文链接:https://www.cnblogs.com/xgqfrms/p/16978984.html
未经授权禁止转载,违者必究!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号