ingress生产环境安装方法
下载的Nginx Controller helm chart版本必须跟当前k8s版本兼容
官方参考地址:
Supported Versions table
| Supported | Ingress-NGINX version | k8s supported version | Alpine Version | Nginx Version | Helm Chart Version |
|---|---|---|---|---|---|
| 🔄 | v1.12.0 | 1.32, 1.31, 1.30, 1.29, 1.28 | 3.21.0 | 1.25.5 | 4.12.0 |
| 🔄 | v1.12.0-beta.0 | 1.32, 1.31, 1.30, 1.29, 1.28 | 3.20.3 | 1.25.5 | 4.12.0-beta.0 |
| 🔄 | v1.11.4 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.21.0 | 1.25.5 | 4.11.4 |
| 🔄 | v1.11.3 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.3 | 1.25.5 | 4.11.3 |
| 🔄 | v1.11.2 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.0 | 1.25.5 | 4.11.2 |
| 🔄 | v1.11.1 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.0 | 1.25.5 | 4.11.1 |
| 🔄 | v1.11.0 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.0 | 1.25.5 | 4.11.0 |
| v1.10.6 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.21.0 | 1.25.5 | 4.10.6 | |
| v1.10.5 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.3 | 1.25.5 | 4.10.5 | |
| v1.10.4 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.0 | 1.25.5 | 4.10.4 | |
| v1.10.3 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.0 | 1.25.5 | 4.10.3 | |
| v1.10.2 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.20.0 | 1.25.5 | 4.10.2 | |
| v1.10.1 | 1.30, 1.29, 1.28, 1.27, 1.26 | 3.19.1 | 1.25.3 | 4.10.1 | |
| v1.10.0 | 1.29, 1.28, 1.27, 1.26 | 3.19.1 | 1.25.3 | 4.10.0 | |
| v1.9.6 | 1.29, 1.28, 1.27, 1.26, 1.25 | 3.19.0 | 1.21.6 | 4.9.1 | |
| v1.9.5 | 1.28, 1.27, 1.26, 1.25 | 3.18.4 | 1.21.6 | 4.9.0 | |
| v1.9.4 | 1.28, 1.27, 1.26, 1.25 | 3.18.4 | 1.21.6 | 4.8.3 | |
| v1.9.3 | 1.28, 1.27, 1.26, 1.25 | 3.18.4 | 1.21.6 | 4.8.* | |
| v1.9.1 | 1.28, 1.27, 1.26, 1.25 | 3.18.4 | 1.21.6 | 4.8.* | |
| v1.9.0 | 1.28, 1.27, 1.26, 1.25 | 3.18.2 | 1.21.6 | 4.8.* | |
| v1.8.4 | 1.27, 1.26, 1.25, 1.24 | 3.18.2 | 1.21.6 | 4.7.* | |
| v1.7.1 | 1.27, 1.26, 1.25, 1.24 | 3.17.2 | 1.21.6 | 4.6.* | |
| v1.6.4 | 1.26, 1.25, 1.24, 1.23 | 3.17.0 | 1.21.6 | 4.5.* | |
| v1.5.1 | 1.25, 1.24, 1.23 | 3.16.2 | 1.21.6 | 4.4.* | |
| v1.4.0 | 1.25, 1.24, 1.23, 1.22 | 3.16.2 | 1.19.10† | 4.3.0 | |
| v1.3.1 | 1.24, 1.23, 1.22, 1.21, 1.20 | 3.16.2 | 1.19.10† | 4.2.5 |
我使用的是k8s是1.20.15版本,所以选择 4.2.5 安装
Ingress Nginx Controller 安装
首先安装 Helm
wget https://get.helm.sh/helm-v3.6.3-linux-amd64.tar.gz
tar -zxvf helm-v3.6.3-linux-amd64.tar.gz
mv linux-amd64/helm /usr/local/bin/helm
helm version
将ingress的仓库添加到helm
helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
helm repo update
helm repo list
指定Helm chart版本,下载ingress nginx controller安装包
helm pull ingress-nginx/ingress-nginx --version 4.2.5
tar zvxf ingress-nginx-4.2.5.tgz
解压并更改对应的配置
tar zvxf ingress-nginx-4.2.5.tgz
cd ingress-nginx
vim values.yaml
需要修改values.yaml相关配置
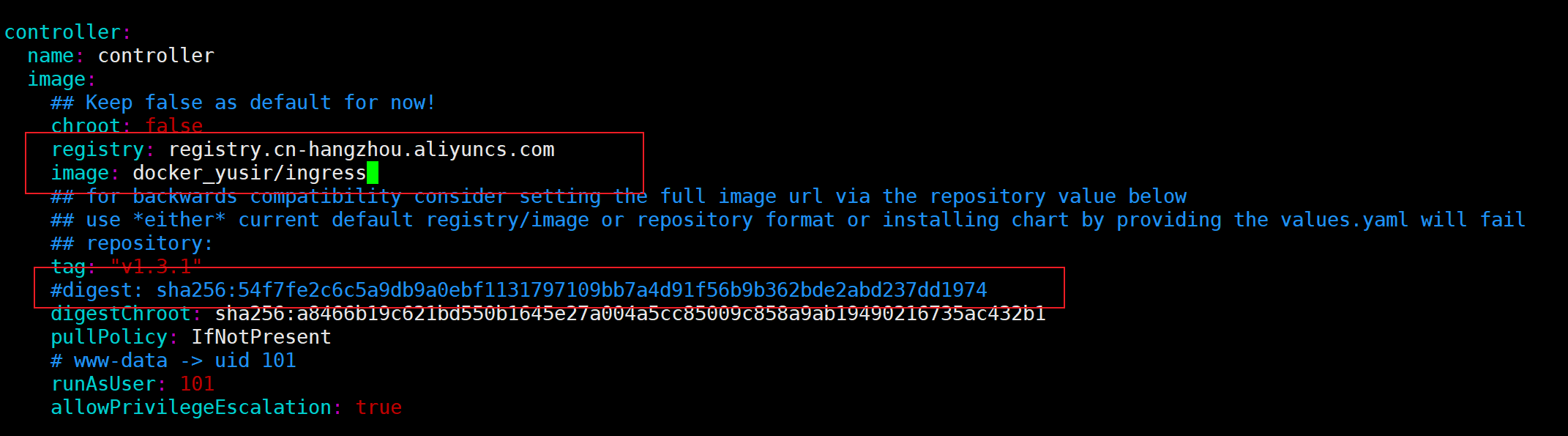
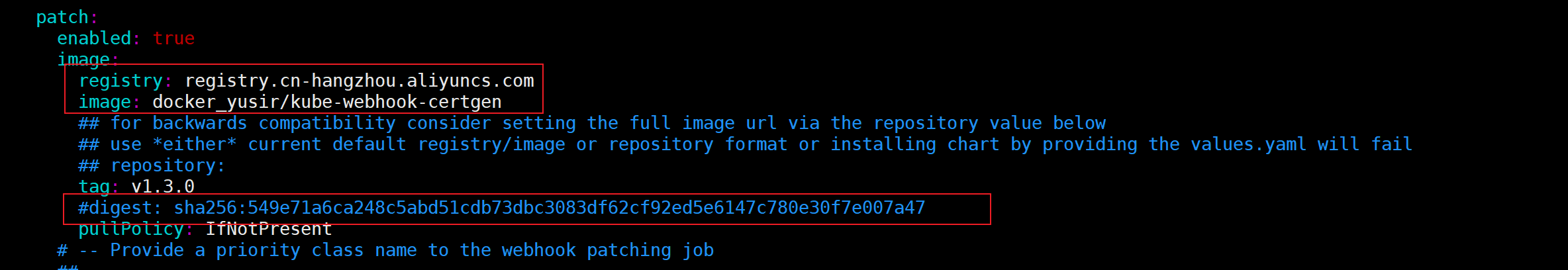
a) 修改Controller 和 admissionWebhook 的镜像地址为国内地址
推荐一个国内镜像网站:渡渡鸟镜像同步站
#用我的也可以
registry.cn-hangzhou.aliyuncs.com/docker_yusir/ingress:v1.3.0
registry.cn-hangzhou.aliyuncs.com/docker_yusir/kube-webhook-certgen:v1.3.0
b) 镜像的 digest 值注释
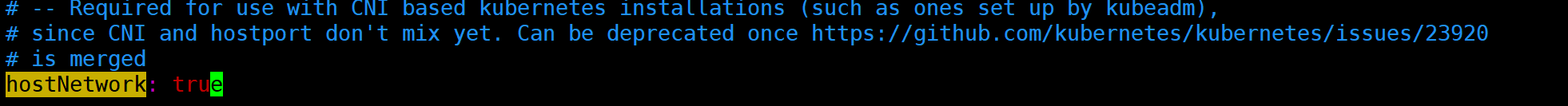
c) hostNetwork 设置为 true
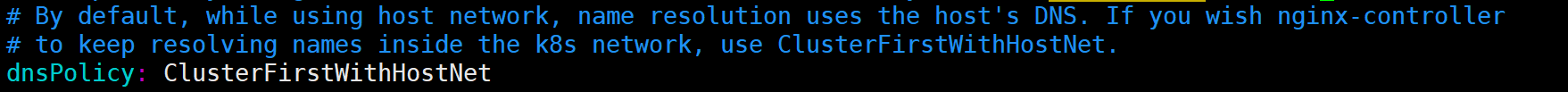
d) dnsPolicy 设置为 ClusterFirstWithHostNet
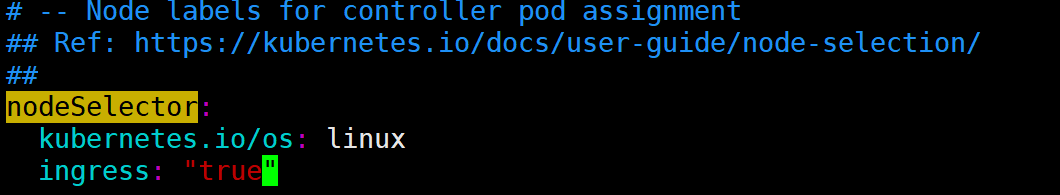
e) nodeSelector 添加 ingress: "true"部署至指定节点
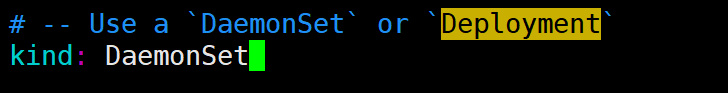
f) 类型更改为 kind: DaemonSet
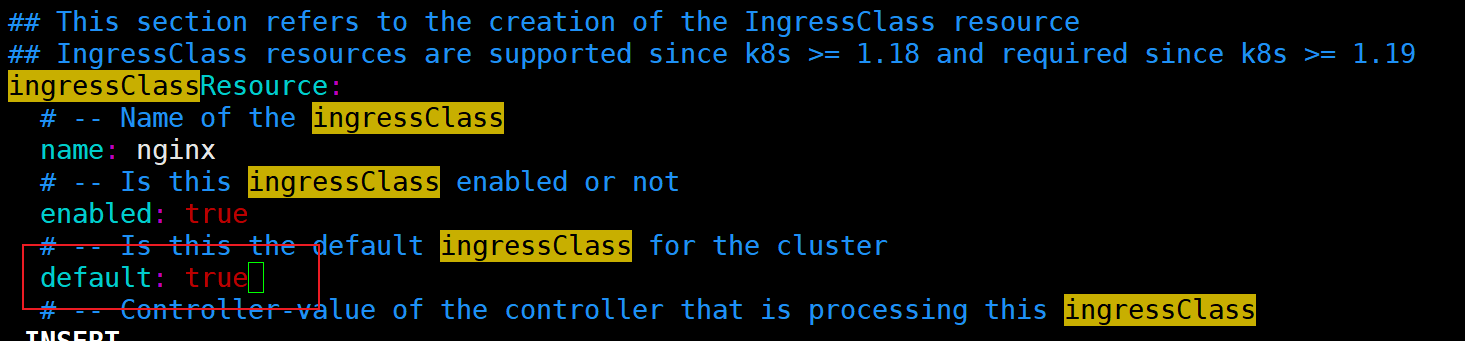
g) ingress nginx 设置为默认的 ingressClass
部署 ingress ,给需要部署 ingress 的节点上打标签
kubectl label node k8s-node02 ingress=true
kubectl create ns ingress-nginx
helm install ingress-nginx -n ingress-nginx .
#安装错误,重新更新/卸载
helm upgrade ingress-nginx -n ingress-nginx
helm uninstall ingress-nginx -n ingress-nginx
检查是否安装成功
helm list -n ingress-nginx
kubectl get svc -n ingress-nginx
kubectl get daemonset -n ingress-nginx
kubectl get po -n ingress-nginx
#部署ingress的node节点执行
netstat -lntup |grep "80"
ps -ef|grep nginx
Ingress Nginx 入门使用
创建一个用于学习 Ingress 的 Namespace,之后所有的操作都在此 Namespace 进行:
kubectl create ns study-ingress
创建一个简单的 Nginx 模拟 Web 服务:
kubectl create deploy nginx --image=registry.cn-hangzhou.aliyuncs.com/docker_yusir/nginx:alpine -n study-ingress
然后创建该 Web 容器的 Service:
kubectl expose deploy nginx --port 80 -n study-ingress
之后创建 Ingress 指向上面创建的 Service:
vim web-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress
namespace: study-ingress
spec:
rules:
- host: nginx.test.com
http:
paths:
- backend:
service:
name: nginx
port:
number: 80
path: /
pathType: ImplementationSpecific
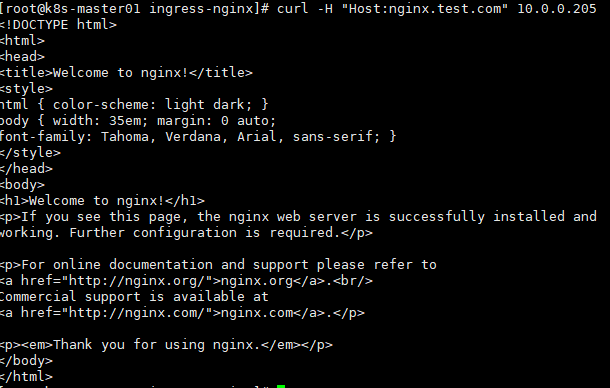
创建并验证 Ingress:
kubectl create -f web-ingress.yaml
curl -H "Host:nginx.test.com" 10.0.0.205 #使用本地host配置浏览器访问也可
Ingress Nginx 域名重定向 Redirect
在 Nginx 作为代理服务器时,Redirect 可用于域名的重定向,以下用 nginx.redirect.com 作为旧域名, baidu.com 作为新域名进行演示
vim redirect.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/permanent-redirect: https://www.baidu.com
nginx.ingress.kubernetes.io/permanent-redirect-code: '308'
name: nginx-redirect
namespace: study-ingress
spec:
rules:
- host: nginx.redirect.com
http:
paths:
- backend:
service:
name: nginx
port:
number: 80
path: /
pathType: ImplementationSpecific
使用 curl 命令进行验证,可以看到返回 308(请求被重定向的返回值),并且域名被重定向至www.baidu.com
curl -H "Host: nginx.redirect.com" 10.0.0.205
curl -H "Host: nginx.redirect.com" 10.0.0.205 -I

Ingress Nginx 前后端分离 Rewrite
创建deployment与service:
kubectl create deploy backend-api --image=registry.cn-hangzhou.aliyuncs.com/docker_yusir/ingress:backend-api -n study-ingress
kubectl expose deploy backend-api --port 80 -n study-ingress
查看 Service 地址,并且通过/api-a 访问测试:
[root@k8s-master01 tmp]# kubectl get svc -n study-ingress
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
backend-api ClusterIP 115.108.209.92 <none> 80/TCP 19s
backend-service ClusterIP 115.98.8.92 <none> 80/TCP 21h
nginx ClusterIP 115.106.151.72 <none> 80/TCP 2d7h
#访问接口返回404
[root@k8s-master01 tmp]# curl 115.108.209.92/api-a
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.27.0</center>
</body>
</html>
直接访问根路径没问题:
[root@k8s-master01 tmp]# curl 115.108.209.92
<!DOCTYPE html>
<html>
<head>
<title>Backend for Ingress Rewrite</title>
</head>
<body>
<h1> backend for ingress rewrite </h1>
<h2> Path: /api-a </h2>
</body>
</html>
通过 Ingress Nginx 的 Rewrite 功能,将/api-a 重写为“/”,配置示例如下:
vim ingress-rewrite.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /$2
name: backend-api
namespace: study-ingress
spec:
rules:
- host: nginx.test.com
http:
paths:
- backend:
service:
name: backend-api
port:
number: 80
path: /api-a(/|$)(.*)
pathType: ImplementationSpecific
测试验证nginx.test.com/api-a,访问成功

Ingress Nginx 错误代码重定向
修改 values.yaml 如下图所示位置:

更新 ConfigMap:(有些helm chart nginx controller版本可能config为空)
config:
apiVersion: v1
client_max_body_size: 20m
custom-http-errors: "404,415,503"

更新 Release:
helm upgrade ingress-nginx -n ingress-nginx .
更新后 Pod 会自动重启,并且会创建一个 defaultbackend:
[root@k8s-master01 ingress-nginx]# kubectl get po -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-controller-v5mrk 1/1 Running 0 65s
ingress-nginx-defaultbackend-7c8dc9665-wgjr7 1/1 Running 0 78s
更新完成以后访问一个不存在的页面,比如之前定义的 nginx.test.com。访问一个不存在的 页面 ,就会跳转到 Error Server 中的页面:

Ingress Nginx SSL
使用 OpenSSL 生成一个测试证书。如果 是生产环境,证书为在第三方公司购买的证书,无需自行生成:
[root@k8s-master01 crt]# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginx.test.com"
Generating a 2048 bit RSA private key
......................+++
..........................................+++
writing new private key to 'tls.key'
-----
配置 Ingress 添加 TLS 配置:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress
namespace: study-ingress
spec:
# 设置默认ingress
ingressClassName: nginx
rules:
- host: nginx.test.com
http:
paths:
- backend:
service:
name: nginx
port:
number: 80
path: /
pathType: ImplementationSpecific
#添加证书
tls:
- hosts:
- nginx.test.com
secretName: ca-secret
➢ hosts:证书所授权的域名列表,生产环境的证书一般为*.test.com等
➢ secretName:证书的 Secret 名字
➢ ingressClassName: ingress class 的名字,1.22+需要配置
更新该 Ingress
[root@k8s-master01 ~]# kubectl apply -f web-ingress.yaml
Warning: resource ingresses/nginx-ingress is missing the kubectl.kubernetes.io/last-applied-configuration annotation which is required by kubectl apply. kubectl apply should only be used on resources created declaratively by either kubectl create --save-config or kubectl apply. The missing annotation will be patched automatically.
ingress.networking.k8s.io/nginx-ingress configured
#报错忽略
使用curl进行测试,域名已经被重定向到 https
[root@k8s-master01 ~]# curl http://nginx.test.com -I
HTTP/1.1 308 Permanent Redirect
Date: Wed, 19 Feb 2025 17:43:15 GMT
Content-Type: text/html
Content-Length: 164
Connection: keep-alive
Location: https://nginx.test.com
使用浏览器访问,会自动跳转到 https

Ingress Nginx 匹配请求头
首先部署移动端应用:
kubectl create deploy mobile --image=registry.cn-hangzhou.aliyuncs.com/docker_yusir/ingress:mobile -n study-ingress
kubectl expose deploy mobile --port 80 -n study-ingress
通过kubectl create进行创建ingress
kubectl create ingress mobile --rule=m.test.com/*=mobile:80 -n study-ingress
创建电脑端应用
kubectl create deploy pc --image=registry.cn-hangzhou.aliyuncs.com/docker_yusir/ingress:pc -n study-ingress
kubectl expose deploy pc --port 80 -n study-ingress
创建电脑端的 Ingress,注意 Ingress annotations的 nginx.ingress.kubernetes.io/server-snippet配置。Snippet配置是专门用于一些复杂的Nginx配置,他与Nginx配置通用
vim pc-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/server-snippet: |
charset utf-8; # 强制声明字符编码为UTF-8
charset_types text/html application/json; # 指定需要添加编码的MIME类型
###当匹配到请求头http_user_agent为下面的设备则返回到mobile
set $agentflag 0;
if ($http_user_agent ~* "(Android|iPhone|WindowsPhone|UC|Kindle)" ){
set $agentflag 1;
}
if ( $agentflag = 1 ) {
return 301 http://m.test.com;
}
name: pc
namespace: study-ingress
spec:
rules:
- host: test.com
http:
paths:
- backend:
service:
name: pc
port:
number: 80
path: /
pathType: ImplementationSpecific
通过浏览器访问test.com(pc)

使用浏览器的开发者工具将终端类型改为 iPhone,刷新后此时后调转到mobile(访问mobile可能会出现字符错乱,参考pc ingress文件指定字符集即可)

Ingress Nginx 基本认证
有些网站可能需要通过密码来访问,对于这类网站可以使用 Nginx 的 basic-auth 设置密码访 问,具体方法如下,由于需要使用 htpasswd 工具,所以需要安装 httpd:
yum install httpd -y
使用 htpasswd 创建yusir 用户的密码:
[root@k8s-master01 ~]# htpasswd -c auth yusir
New password:
Re-type new password:
Adding password for user yusir
[root@k8s-master01 ~]# cat auth
yusir:$apr1$qWSKn1mN$IGfdAFbp5Uce4dkuLduTg0
基于之前创建的密码文件创建 Secret
kubectl create secret generic basic-auth --from-file=auth -n study-ingress
创建包含密码认证的 Ingress:
[root@k8s-master01 ~]# cat ingress-with-auth.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
# kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/auth-realm: Please Input Your Username and Password
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-type: basic
name: ingress-with-auth
namespace: study-ingress
spec:
ingressClassName: nginx # for k8s >= 1.22+
rules:
- host: auth.test.com
http:
paths:
- backend:
service:
name: nginx
port:
number: 80
path: /
pathType: ImplementationSpecific
➢ nginx.ingress.kubernetes.io/auth-type:认证类型,可以是 basic 和 digest
➢ nginx.ingress.kubernetes.io/auth-secret:密码文件的 Secret 名称
➢ nginx.ingress.kubernetes.io/auth-realm:需要密码认证的消息提醒
浏览器登陆测试访问

Ingress Nginx 黑/白名单
配置黑名单
配置黑名单禁止某一个或某一段IP,需要在Nginx Ingress的ConfigMap中配置,比如将 10.0.0.202(多个配置逗号分隔)添加至黑名单:
vim values.yaml
config:
block-cidrs: 10.0.0.202
滚动更新Nginx Ingress:
helm upgrade ingress-nginx -n ingress-nginx .
此时使用10.0.0.202的节点访问报403,而没有配置黑名单的节点访问正常
[root@k8s-master02 ~]# ip addr|grep "10.0.0.202"
inet 10.0.0.202/24 brd 10.0.0.255 scope global ens32
You have new mail in /var/spool/mail/root
[root@k8s-master02 ~]# curl -H "Host:test.com" 10.0.0.205 -I
HTTP/1.1 403 Forbidden
Date: Sun, 23 Feb 2025 11:25:46 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 146
Connection: keep-alive
[root@k8s-master03 ~]# curl -H "Host:test.com" 10.0.0.205 -I
HTTP/1.1 200 OK
Date: Sun, 23 Feb 2025 11:23:46 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 503
Connection: keep-alive
Last-Modified: Thu, 20 Feb 2025 15:57:04 GMT
ETag: "67b750d0-1f7"
Accept-Ranges: bytes


配置白名单
白名单表示只允许某个IP可以访问,直接在yaml文件中配置即可(也可以通过ConfigMap 配置),比如只允许10.0.0.202访问,只需要添加一个nginx.ingress.kubernetes.io/whitelist source-range 即可:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: nginx
# 白名单
nginx.ingress.kubernetes.io/whitelist-source-range: 10.0.0.202
nginx.ingress.kubernetes.io/server-snippet: |
charset utf-8; # 强制声明字符编码为UTF-8
charset_types text/html application/json; # 指定需要添加编码的MIME类型
set $agentflag 0;
if ($http_user_agent ~* "(Android|iPhone|WindowsPhone|UC|Kindle)" ){
set $agentflag 1;
}
if ( $agentflag = 1 ) {
return 301 http://m.test.com;
}
name: pc
namespace: study-ingress
spec:
rules:
- host: test.com
http:
paths:
- backend:
service:
name: pc
port:
number: 80
path: /
pathType: ImplementationSpecific
更新ingress
kubectl replace -f pc-ingress.yaml
此时10.0.0.202节点访问正常,其他节点访问报403
[root@k8s-master02 ~]# ip addr|grep "10.0.0.202"
inet 10.0.0.202/24 brd 10.0.0.255 scope global ens32
You have new mail in /var/spool/mail/root
[root@k8s-master02 ~]# curl -H "Host:test.com" 10.0.0.205 -I
HTTP/1.1 200 OK
Date: Sun, 23 Feb 2025 11:37:39 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 503
Connection: keep-alive
Last-Modified: Thu, 20 Feb 2025 15:57:04 GMT
ETag: "67b750d0-1f7"
Accept-Ranges: bytes
[root@k8s-master01 ~]# curl -H "Host:test.com" 10.0.0.205 -I
HTTP/1.1 403 Forbidden
Date: Sun, 23 Feb 2025 11:38:25 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 146
Connection: keep-alive


Ingress Nginx速率限制
在面对一下限流降级的场景可能需要限制速率以降低后端压力,或者限制单个IP每秒的访问速率防止攻击。此时可以使用Nginx的rate limit进行配置。 首先没有加速率限制,使用ab进行访问,Failed requests为0:
[root@k8s-master01 ~]# ab -c 10 -n 100 https://test.com/ | grep requests
Complete requests: 100
Failed requests: 0
Time per request: 1.044 [ms] (mean, across all concurrent requests)
Percentage of the requests served within a certain time (ms)
添加速率限制nginx.ingress.kubernetes.io/limit connections,用于限制每个客户端 IP 地址的最大并发连接数。当设置为 1 时,表示每个 IP 同一时间只能建立一个连接
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/whitelist-source-range: 10.0.0.202
#添加客户访问速率限制
nginx.ingress.kubernetes.io/limit-connections: "1"
nginx.ingress.kubernetes.io/server-snippet: |
charset utf-8; # 强制声明字符编码为UTF-8
charset_types text/html application/json; # 指定需要添加编码的MIME类型
set $agentflag 0;
if ($http_user_agent ~* "(Android|iPhone|WindowsPhone|UC|Kindle)" ){
set $agentflag 1;
}
if ( $agentflag = 1 ) {
return 301 http://m.test.com;
}
name: pc
namespace: study-ingress
spec:
rules:
- host: test.com
http:
paths:
- backend:
service:
name: pc
port:
number: 80
path: /
pathType: ImplementationSpecific
再次使用ab测试,Failed requests为22:
[root@k8s-master01 ~]# ab -c 10 -n 100 http://test.com/ | grep requests
Complete requests: 100
Failed requests: 22
Time per request: 0.512 [ms] (mean, across all concurrent requests)
Percentage of the requests served within a certain time (ms)
还有很多其它方面的限制,常用的配置如下:
#限制每秒的连接,单个IP: nginx.ingress.kubernetes.io/limit-rps
#限制每分钟的连接,单个IP: nginx.ingress.kubernetes.io/limit-rpm
#限制客户端每秒传输的字节数,单位为K,需要开启proxy-buffering: nginx.ingress.kubernetes.io/limit-rate
# 速率限制白名单 nginx.ingress.kubernetes.io/limit-whitelist
使用Nginx 实现灰度/金丝雀发布
创建生产环境
首先创建模拟Production(生产)环境的Namespace和服务:
kubectl create ns production
kubectl create deploy production --image=registry.cn-hangzhou.aliyuncs.com/docker_yusir/ingress:production -n production
kubectl expose deploy production --port 80 -n production
kubectl create ingress production --rule=production.com/*=production:80 -n production

创建灰度环境
创建灰度命名空间
kubectl create ns canary
创建灰度版本的应用和Service:
kubectl create deploy canary --image=registry.cn-hangzhou.aliyuncs.com/docker_yusir/ingress:canary -n canary
kubectl expose deploy canary --port 80 -n canary
待程序启动完成后,通过Service访问该服务,会返回canary
[root@k8s-master01 tmp]# kubectl get svc -n canary
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
canary ClusterIP 115.106.48.138 <none> 80/TCP 33s
[root@k8s-master01 tmp]# curl 115.106.48.138
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Canary Environment</title>
<style>
body {
background-color: #e6e6fa; /* Light Purple */
font-family: Arial, sans-serif;
}
h1 {
color: blue;
}
</style>
</head>
<body>
<h1>Welcome to the Canary Environment!</h1>
<p>This is a test version of our application for gradual rollout and testing.</p>
</body>
</html>
Canary版本切入部分流量
创建灰度版本的Ingress时,需要添加两个注释,一个是nginx.ingress.kubernetes.io/canary, 表明是灰度环境,nginx.ingress.kubernetes.io/canary-weight表明切多少流量到该环境,本示例为 10%:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/canary: "true"
nginx.ingress.kubernetes.io/canary-weight: "10"
name: canary
namespace: canary
spec:
ingressClassName: nginx # for k8s >= 1.22+
rules:
- host: production.com
http:
paths:
- backend:
service:
name: canary
port:
number: 80
path: /
pathType: ImplementationSpecific
此时通过nginx.ingress.kubernetes.io/canary-weight: "10"设置的权重是10,即v1:v2为9:1
测试灰度发布
接下来使用shell脚本进行测试,此脚本会输出production和canary的访问次数比值:
[root@k8s-master01 ~]# cat test-canary.sh
#!/bin/bash
# 初始化计数器
production_count=0
canary_count=0
# 模拟100次请求
for i in {1..100}; do
response=$(curl -s production.com) # 替换为你的服务器地址
if [[ $response == *"Welcome to the Production Environment!"* ]]; then
((production_count++))
elif [[ $response == *"Welcome to the Canary Environment!"* ]]; then
((canary_count++))
fi
done
# 计算比例并输出结果
total_requests=$((production_count + canary_count))
echo "Total requests: $total_requests"
echo "Production hits: $production_count ($(awk "BEGIN{print ($production_count/$total_requests)*100}" | awk '{printf "%.2f", $1}')%)"
echo "Canary hits: $canary_count ($(awk "BEGIN{print ($canary_count/$total_requests)*100}" | awk '{printf "%.2f", $1}')%)"
ratio=$(awk "BEGIN{print $canary_count/$production_count}")
echo "Canary to Production ratio: $(awk "BEGIN{print $ratio}" | awk '{printf "%.2f", $1}')"
测试结果
[root@k8s-master01 ~]# chmod +x test-canary.sh
[root@k8s-master01 ~]# ./test-canary.sh
Total requests: 100
Production hits: 91 (91.00%)
Canary hits: 9 (9.00%)
Canary to Production ratio: 0.10



 浙公网安备 33010602011771号
浙公网安备 33010602011771号