第九届工业信息安全技能大赛-典型工业场景锦标赛
reverse
babyre
import struct
def rol(val, r_bits, max_bits=32):
"""
Performs a left circular shift on a value.
"""
return (val << r_bits % max_bits) & (2**max_bits - 1) | \
((val & (2**max_bits - 1)) >> (max_bits - (r_bits % max_bits)))
def decrypt(encrypted_chunk, key_chunk):
"""
Decrypts a 4-byte chunk based on the reverse-engineered algorithm.
"""
rol_key = rol(key_chunk, 12)
xored = encrypted_chunk ^ rol_key
decrypted = rol(xored, 12)
return decrypted
# Provided data from the disassembly
secret = [0x8301F735, 0xEA586A9E, 0xFF89A3A9, 0x41C7EB25, 0x72001600, 0xB819FF5D, 0xCAFA972C]
# Correcting the third key value based on the prompt (0FEDCBA9h)
key = [0x12345678, 0x9ABCDEF0, 0x0FEDCBA9, 0x87654321]
flag_bytes = b""
# Loop through the secret data, decrypting each chunk
for i in range(len(secret)):
encrypted_chunk = secret[i]
# The key selection logic simplifies to (i % 4)
key_chunk = key[i % 4]
decrypted_dword = decrypt(encrypted_chunk, key_chunk)
# Convert the decrypted dword (32-bit integer) to bytes.
# '<I' means little-endian unsigned int.
flag_bytes += struct.pack('<I', decrypted_dword)
# Decode the bytes into a string and print
# Use .rstrip('\x00') to remove any trailing null bytes from padding.
flag = flag_bytes.decode('ascii').rstrip('\x00')
print(flag)
流量分析
异常的数据流量包
可以获得摩斯密码
flag{https://wwfu.lanzouo.com/i6D1D2y2vy8h/
....- ...-- ...-- ----- ..... .---- ---.. .. ... .- ... - .-. .. -. --. --- ..-. ..- ... . ..-. ..- .-.. -. ..- -- -... . .-. ...
4330518ISASTRINGOFUSEFULNUMBERS
4330518是密码。
tshark -r a.pcapng -Y "(tcp.srcport == 502) && !(modbus.func_code == 6) && frame.number <=2298" -e modbus.regval_uint16 -T fields > out.txt
import struct
with open('out.txt', 'r') as f:
data = f.read().strip()
data = data.replace('\n', ',')
arr = data.split(',')
barray = [struct.pack('>H', int(x)) for x in arr]
out = b''.join(barray)
with open('out.pdf', 'wb') as f:
f.write(out)
得到一个pdf 但是有密码。打开全选复制。

flag{MB03_40001}
工业控制协议流量分析1
frame.len > 53
长度53是正常包.
插入数据长度为 X-53, 长度55即插入55-53 = 插入2字符
拼接在一起即可
注: 6102包 长度56 插入3字符.查看是10ff. 经测试插入的是10f
flag{9471f432-a582-4884-b990-10f9c8ecd800}
工业控制协议流量分析2
tcp数据中有,ZIPDATA: 开头的包过滤出来 .
提取倒数第2字节保存成zip.解压提示有密码.
213号包
0000 45 00 00 38 00 01 00 00 40 06 f6 42 c0 a8 01 64 E..8....@..B...d
0010 c0 a8 01 c8 28 ac 00 66 00 00 00 00 00 00 00 00 ....(..f........
0020 50 02 20 00 cf fd 00 00 4d 4d 53 5f 50 57 3a 4d P. .....MMS_PW:M
0030 4d 53 31 32 33 34 35 3b MS12345;
密码为 MMS12345
flag{6a46756d-df7e-4b66-87e4-1b2661676e40}
工业控制协议流量分析3
{"id": 3, "name": "tiger-f", "status": 135, "timestamp": 1692860628.46093}0Thacker
{"id": 3, "name": "tiger-l", "status": 262, "timestamp": 1692860629.462777}0Vhacker
{"id": 3, "name": "tiger-a", "status": 1007, "timestamp": 1692860630.4643118}0Uhacker
{"id": 3, "name": "tiger-g", "status": 590, "timestamp": 1692860631.4666204}0Shacker
{"id": 3, "name": "tiger-{", "status": 94, "timestamp": 1692860632.467778}0Uhacker
{"id": 3, "name": "tiger-r", "status": 394, "timestamp": 1692860633.4699678}0Shacker
{"id": 3, "name": "tiger-u", "status": 84, "timestamp": 1692860634.480414}0Uhacker
{"id": 3, "name": "tiger-E", "status": 765, "timestamp": 1692860635.4834943}0Uhacker
{"id": 3, "name": "tiger-f", "status": 934, "timestamp": 1692860636.4851058}0Uhacker
{"id": 3, "name": "tiger-6", "status": 319, "timestamp": 1692860637.4873934}0Shacker
{"id": 3, "name": "tiger-O", "status": 39, "timestamp": 1692860638.489548}0Thacker
{"id": 3, "name": "tiger-m", "status": 624, "timestamp": 1692860639.492195}0Uhacker
{"id": 3, "name": "tiger-q", "status": 584, "timestamp": 1692860640.4942486}0Uhacker
{"id": 3, "name": "tiger-h", "status": 548, "timestamp": 1692860641.4970875}0Uhacker
{"id": 3, "name": "tiger-A", "status": 205, "timestamp": 1692860642.4997754}0Uhacker
{"id": 3, "name": "tiger-l", "status": 372, "timestamp": 1692860643.5019176}0Thacker
{"id": 3, "name": "tiger-X", "status": 126, "timestamp": 1692860644.503635}0Uhacker
{"id": 3, "name": "tiger-I", "status": 410, "timestamp": 1692860645.5051255}0Uhacker
{"id": 3, "name": "tiger-Y", "status": 675, "timestamp": 1692860646.5060635}0Uhacker
{"id": 3, "name": "tiger-x", "status": 902, "timestamp": 1692860647.5076697}0Uhacker
{"id": 3, "name": "tiger-m", "status": 853, "timestamp": 1692860648.5094569}0Uhacker
{"id": 3, "name": "tiger-n", "status": 211, "timestamp": 1692860649.5110319}0Uhacker
{"id": 3, "name": "tiger-R", "status": 691, "timestamp": 1692860650.5117116}0Uhacker
{"id": 3, "name": "tiger-1", "status": 183, "timestamp": 1692860651.5137799}0Uhacker
{"id": 3, "name": "tiger-X", "status": 609, "timestamp": 1692860652.5154688}0Shacker
{"id": 3, "name": "tiger-L", "status": 60, "timestamp": 1692860653.517407}0Shacker
{"id": 3, "name": "tiger-C", "status": 623, "timestamp": 1692860654.51978}0Thacker
{"id": 3, "name": "tiger-6", "status": 40, "timestamp": 1692860655.5229137}0Uhacker
{"id": 3, "name": "tiger-R", "status": 674, "timestamp": 1692860656.5254927}0Vhacker
{"id": 3, "name": "tiger-1", "status": 1007, "timestamp": 1692860657.5279772}0Shacker
{"id": 3, "name": "tiger-]", "status": 292, "timestamp": 1692860658.53106}0Uhacker
{"id": 3, "name": "tiger-}", "status": 435, "timestamp": 1692860659.5319245}
直接提取 tiger- 后面拼出
flag{ruEf6OmqhAlXIYxmnR1XLC6R1]}
工控协议隐蔽通道分析
((s7comm.param.func == 0x05 && !(frame[71:5] == 00:04:00:01:66)) && (s7comm.param.item.area == 0x84 or s7comm.param.item.area == 0x83)) && (s7comm.param.item.length > 37)
找到4个zip组合.需要密码
849包 HINT::PASSWORD_ENCRYPTED_WITH_CAESAR_SHIFT_3
431包 !DATA_BEGIN_AT_ASCII_VALUES_OF_'f'
623包 looking_at_M_area}
849包 HINT::PASSWORD_ENCRYPTED_WITH_CAESAR_SHIFT_3
853包 提示只看写入操作 FOCUS_ON_S7_WRITE_VARIABLE_OPERATIONS_ONLY
973 flag{n0t
提示 ALL_DATA_FRAGMENTS_IN_M_AREA
1131包 PASSWORD_IN_DB_AREA_ADDRESS_0x60_WITH_CAESAR_CIPHER
1171包 th3_r34l_
过滤找到密码密文
(s7comm.param.item.address == 0x00060)
479包 CAES_l_3:V0F3PP34
根据提示 HINT::PASSWORD_ENCRYPTED_WITH_CAESAR_SHIFT_3
zip在这里 https://wwvo.lanzouo.com/izuYj35g9n1i
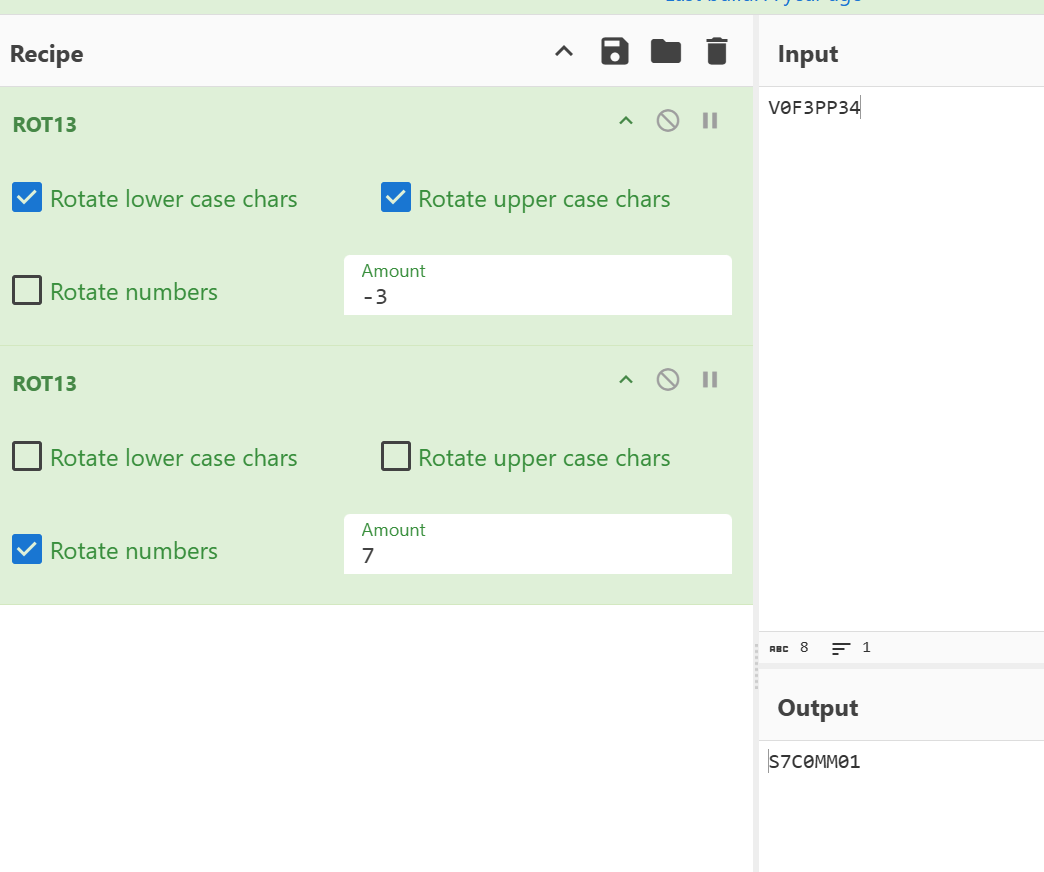
S7C0MM01 解压得到 flag
flag{S7c0mm_pr0t0col_st3g4n0graphy_mast3r}
日志分析
[2025-03-29 15:23:11] USER Operation Param: ZS0yZTE1ODcxZGRmMDR9
[2025-02-18 19:33:30] INFO System CheckSum: 1jNTMwLTRjNWMtOTg1
[2025-03-29 00:36:51] MAINT Remote Session ID: ZmxhZ3s0ZTU0ZmE3Yy
ZmxhZ3s0ZTU0ZmE3Yy1jNTMwLTRjNWMtOTg1ZS0yZTE1ODcxZGRmMDR9
flag{4e54fa7c-c530-4c5c-985e-2e15871ddf04}
固件分析
010打开翻一下.有个 base64. 是flag1 ZmxhZ3thNjMwMG
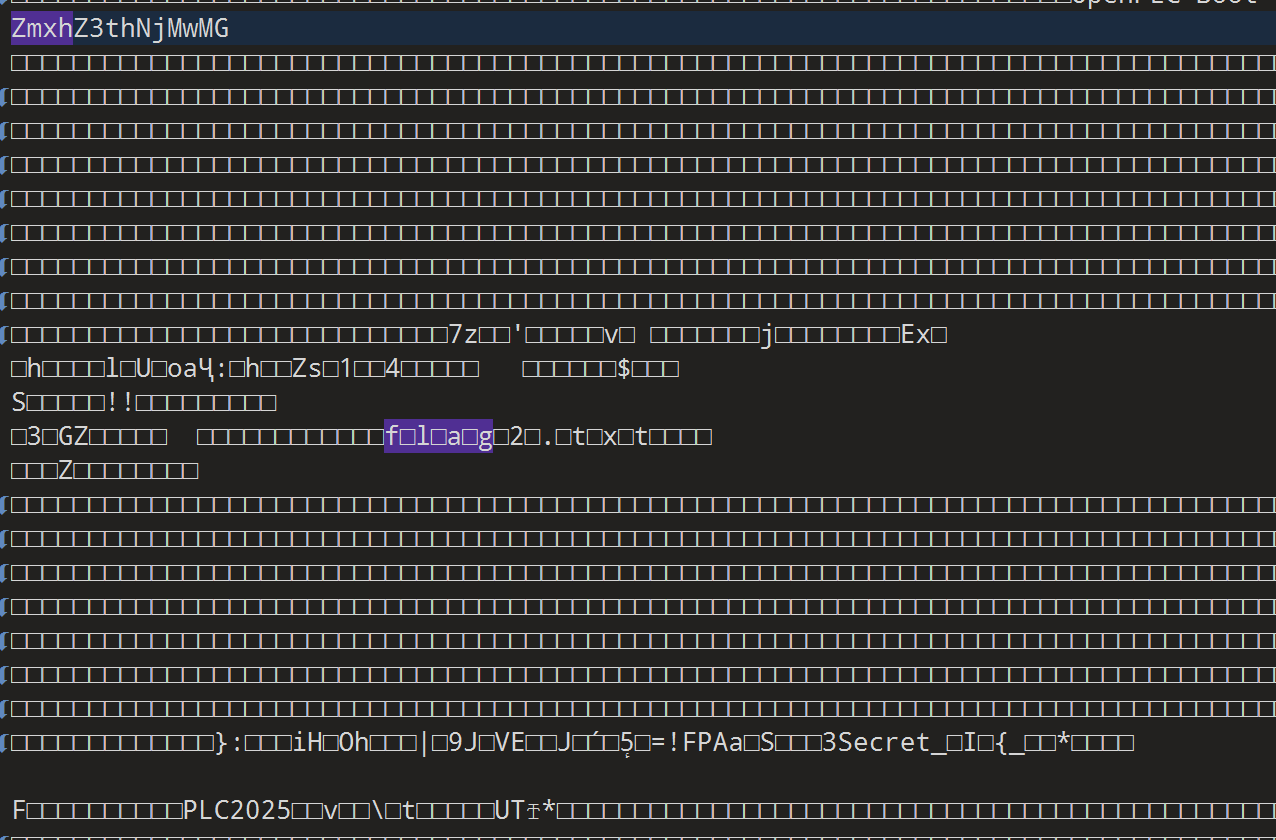
下面有个7z.
binwalk -Me 提取出来hidden.7z
S,3,Secret_,I{_F,PLC2025,v
生成一个字典跑一下
from itertools import combinations, permutations
# 原始元素
elements = ["S", "3", "Secret_", "I{_F", "PLC2025", "v"]
# 生成所有组合
all_combinations = []
# 2个元素组合
for combo in combinations(elements, 2):
all_combinations.append("".join(combo))
all_combinations.append("".join(combo[::-1]))
# 3个元素组合
for combo in combinations(elements, 3):
all_combinations.append("".join(combo))
all_combinations.append("".join(combo[::-1]))
for perm in list(permutations(combo))[:3]:
all_combinations.append("".join(perm))
# 4个元素组合
for combo in combinations(elements, 4):
all_combinations.append("".join(combo))
all_combinations.append("".join(combo[::-1]))
for perm in list(permutations(combo))[:2]:
all_combinations.append("".join(perm))
# 5个元素组合
for combo in combinations(elements, 5):
all_combinations.append("".join(combo))
all_combinations.append("".join(combo[::-1]))
# 全部元素组合
all_combinations.append("".join(elements))
all_combinations.append("".join(elements[::-1]))
# 特殊排列
special_orders = [
[elements[0], elements[2], elements[4], elements[1], elements[3], elements[5]],
[elements[5], elements[3], elements[1], elements[4], elements[2], elements[0]],
[elements[2], elements[4], elements[0], elements[5], elements[1], elements[3]]
]
for order in special_orders:
all_combinations.append("".join(order))
# 去重并保存到txt文件
unique_combinations = list(set(all_combinations))
with open('combinations.txt', 'w', encoding='utf-8') as f:
for combo in unique_combinations:
f.write(combo + '\n')
print(f"已生成 {len(unique_combinations)} 个组合,保存到 combinations.txt")
D:\CTF\tools\hashcat>.\hashcat.exe -m 11600 7z.hash combinations.txt --show
$7z$2$19$0$$8$ea5cd9d55be1b2350000000000000000$1514644019$32$18$8a0a10689c05051b6c0055a56f61d2b63ad21568fceb705a731b31d4d94134d8$14$00:Secret_PLC2025
密码是 Secret_PLC2025
flag2
E4MC01MGE4LTRm
010在openplc.img里搜索到 ohDPM2YtYjMzOS0zYWi
ID3M5Yzc2YWU5MDJ9
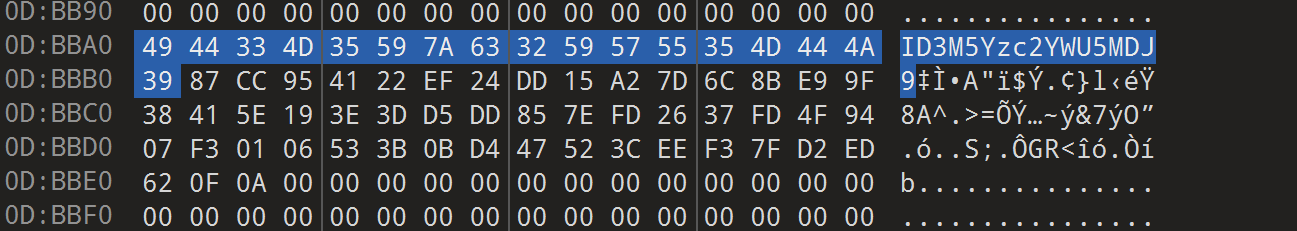
ZmxhZ3thNjMwMG
ID3M5Yzc2YWU5MDJ9
ohDPM2YtYjMzOS0zYWi
E4MC01MGE4LTRm
合并
ZmxhZ3thNjMwMGE4MC01MGE4LTRmohDPM2YtYjMzOS0zYWiID3M5Yzc2YWU5MDJ9
删一些光效的字符
flag{a6300a80-50a8-4f3f-b339-3ahs9c76ae902}
对照 uuid4
flag{695eb6d9-2e95-48c3-a154-ccec14445639}
将 上面的 iID3 删掉
flag{a6300a80-50a8-4f3f-b339-3ac9c76ae902}
梯形图
博图分析
1.216667
化工厂PLC程序逆向
_4j.tvf 找到

调试中改成53

flag{HACKCOEFF.Out}
flag{53.64}
Misc
工控宣传的隐蔽信号
MP3时间倒放,获得密码
s0803y0518
GIF逐帧切片 155帧获得二维码
修复二维码,获得字符串
GNalVNrhVOLZjRK7pMrJjPn3x
XXencode解码:
flag{aiyoubucuoo1}
抓内鬼啦
pcap导出文件,一个zip,一个PNG
part1 zip伪加密
获得Great_G0t_it!}
part2 PNG 零宽
获得二维码 Polis{W0w_Th1s_1s_f1agO1_
拼起来 Polis{W0w_Th1s_1s_f1agO1_Great_G0t_it!}
图片的奥密
爆破密码/按题目计算也行。
54450
原图显示为 flag{this is a fake}
文件中有10个base64 , 分别保存为图片。一个没用。其他拼成二维码。

扫码得到
fdvbpy4zl9klge9fb7n8caa0vz7g1600e557e2adb0b5eICphorM5FEDVW3LyOisUdX4kv9JtSmP01QxRBl6THjgAcnfYubGZqwKz7asnow
工业流量隐写分析
binwalk
formost 分离出一个压缩包
zip.png 扫出解压密码 解压得到 industrial_traffic_with_flag.pcap
搜索得到
ZmxhZ3tTN19QTEM=
flag{S7_PLC
53号包找到
0000 00 0c 29 83 51 3f 00 0c 29 1b 83 21 08 00 45 00 ..).Q?..)..!..E.
0010 00 42 00 01 00 00 40 06 f6 9b c0 a8 01 65 c0 a8 .B....@......e..
0020 01 64 00 66 00 66 00 00 00 00 00 00 00 00 50 18 .d.f.f........P.
0030 20 00 9a ef 00 00 03 00 00 24 01 00 00 fd 2d 32 ........$....-2
0040 30 32 35 5f 25 32 33 5f 49 43 53 25 37 44 ab ba 025_#_ICS}..
-2025_#_ICS}
flag{S7_PLC-2025_#_ICS}
why_not_substitution
from string import ascii_lowercase, digits
import hashlib
CHARSET = "!@#¥%" + ascii_lowercase + digits
n = len(CHARSET) # 41
P.<x> = PolynomialRing(GF(n))
# 已知信息
known_plain = "flkejiy"
enc = "quw7f59u51q¥##w¥w6q6s¥¥#w#661d¥"
known_hash = "7d41757168a2199b32cb1744de130fdebda25271116bc64eccf4e397770d73c2"
# 计算索引
plain_indices = [CHARSET.index(c) for c in known_plain]
enc_indices = [CHARSET.index(enc[i]) for i in range(len(known_plain))]
# 点对
points = [(plain_indices[i], enc_indices[i]) for i in range(len(known_plain))]
# 使用拉格朗日插值得到多项式f(度数<7)
f = P.lagrange_polynomial(points)
print("插值得到的多项式f:", f)
# 构建逆映射
inv_map = {}
collision = False
missing = set(range(n)) # 用于检查是否覆盖所有值
for i in range(n):
val = Integer(f(i)) # 转换为整数
if val in inv_map:
collision = True
print("碰撞检测: 值", val, "重复")
inv_map[val] = i
if val in missing:
missing.remove(val)
if collision:
print("多项式f存在碰撞,不是单射。")
if len(missing) > 0:
print("多项式f未覆盖所有值,不是满射。")
# 解密
flag = ''
decrypt_error = False
for c in enc:
idx = CHARSET.index(c)
if idx not in inv_map:
decrypt_error = True
print("解密错误: 值", idx, "无逆映射")
break
flag += CHARSET[inv_map[idx]]
if decrypt_error:
print("解密失败,请检查多项式。")
else:
# 验证hash
computed_hash = hashlib.sha256(flag.encode('utf-8')).hexdigest()
if computed_hash == known_hash:
print("找到flag:", flag)
else:
print("hash不匹配,flag:", flag, "computed_hash:", computed_hash)
插值得到的多项式f: 10*x^6 + 26*x^5 + 19*x^4 + 11*x^3 + 12*x^2 + x + 20
碰撞检测: 值 36 重复
碰撞检测: 值 27 重复
碰撞检测: 值 36 重复
碰撞检测: 值 36 重复
碰撞检测: 值 5 重复
碰撞检测: 值 8 重复
碰撞检测: 值 38 重复
碰撞检测: 值 7 重复
碰撞检测: 值 22 重复
碰撞检测: 值 7 重复
碰撞检测: 值 27 重复
碰撞检测: 值 3 重复
碰撞检测: 值 37 重复
碰撞检测: 值 8 重复
碰撞检测: 值 2 重复
碰撞检测: 值 8 重复
多项式f存在碰撞,不是单射。
多项式f未覆盖所有值,不是满射。
hash不匹配,flag: fl2wjqylqaf3772324f493372744a83 computed_hash: 676985daff40c8c58df0e7c1f643d25eb3dfd585b0a65e4f18a758d1ffcce613
设计图之秘
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "369875"
[i] Original filename: "flag.txt".
[i] Extracting to "car_flag.jpg.out".
得到 flag
flk5lsdiaenorfa1yeag7d21c78ad28c3ae25V6swgqhSAc3eyHJoQzMWFr491xktO8dGYRTXmCiPZNufBpl7b2UDK0Larm
所见即是开始
盲文读取出来
hanoi floor is 9
解压文件 提示
所解即所得;
一组格式为盘+当前柱+去往柱
def move(n, from_rod, to_rod, using_rod):
if n == 1:
print(f"{n}{from_rod}{to_rod}") # 格式:盘当前柱→去往柱,但注意这里盘子编号是1,因为n=1
else:
move(n-1, from_rod, using_rod, to_rod)
print(f"{n}{from_rod}{to_rod}") # 移动第n个盘子
move(n-1, using_rod, to_rod, from_rod)
move(9, "A", "C", "B")
flag字符串长度1533
1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB5AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC6AB1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA5CB1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB7AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC5BA1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA6BC1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB5AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC8AB1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA5CB1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB6CA1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC5BA1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA7CB1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB5AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC6AB1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA5CB1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB9AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC5BA1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA6BC1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB5AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC7BA1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA5CB1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB6CA1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC5BA1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA8BC1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB5AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC6AB1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA5CB1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB7AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC5BA1CB2CA1BA3CB1AC2AB1CB4CA1BA2BC1AC3BA1CB2CA1BA6BC1AC2AB1CB3AC1BA2BC1AC4AB1CB2CA1BA3CB1AC2AB1CB5AC1BA2BC1AC3BA1CB2CA1BA4BC1AC2AB1CB3AC1BA2BC1AC
Web
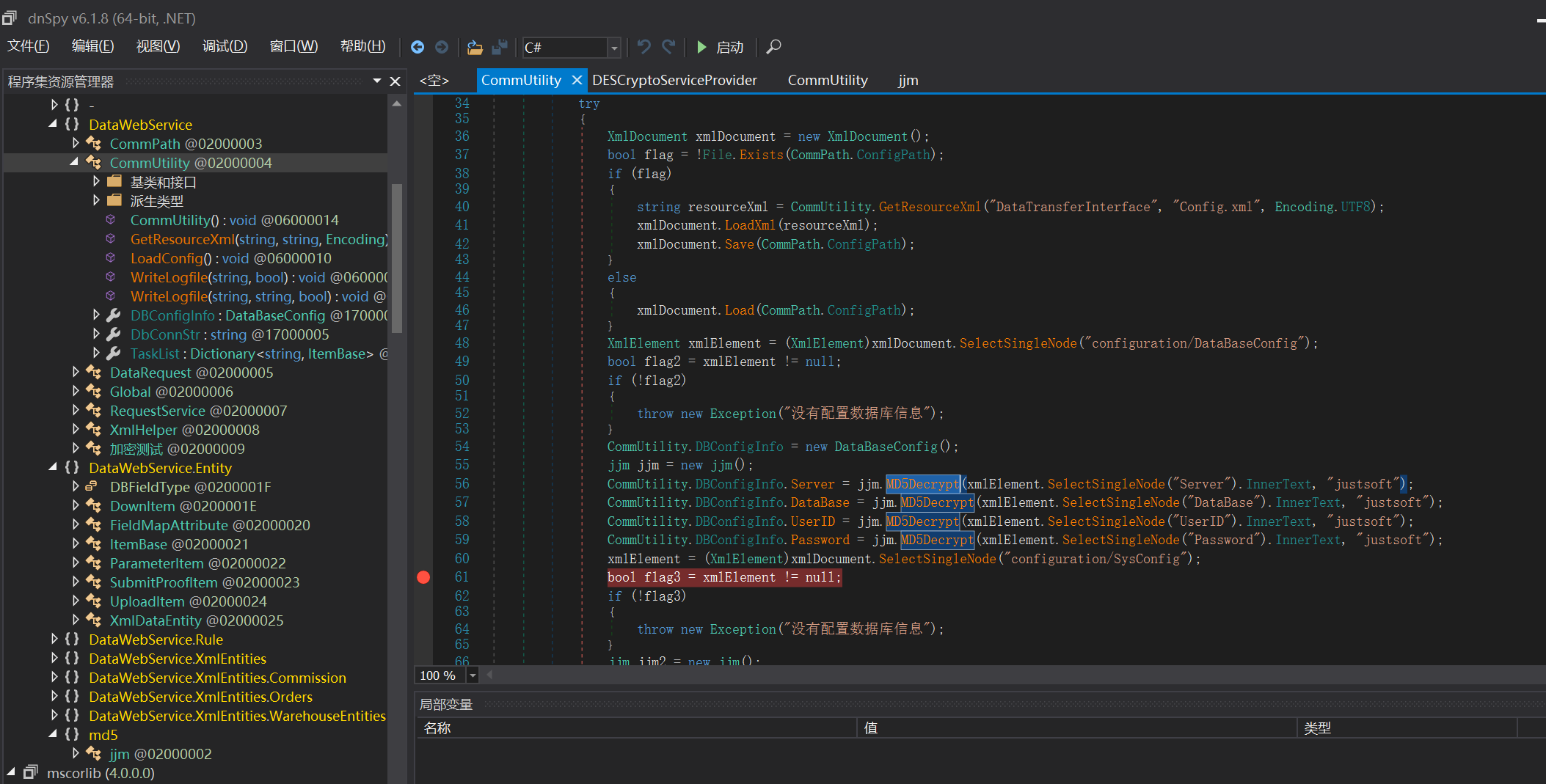
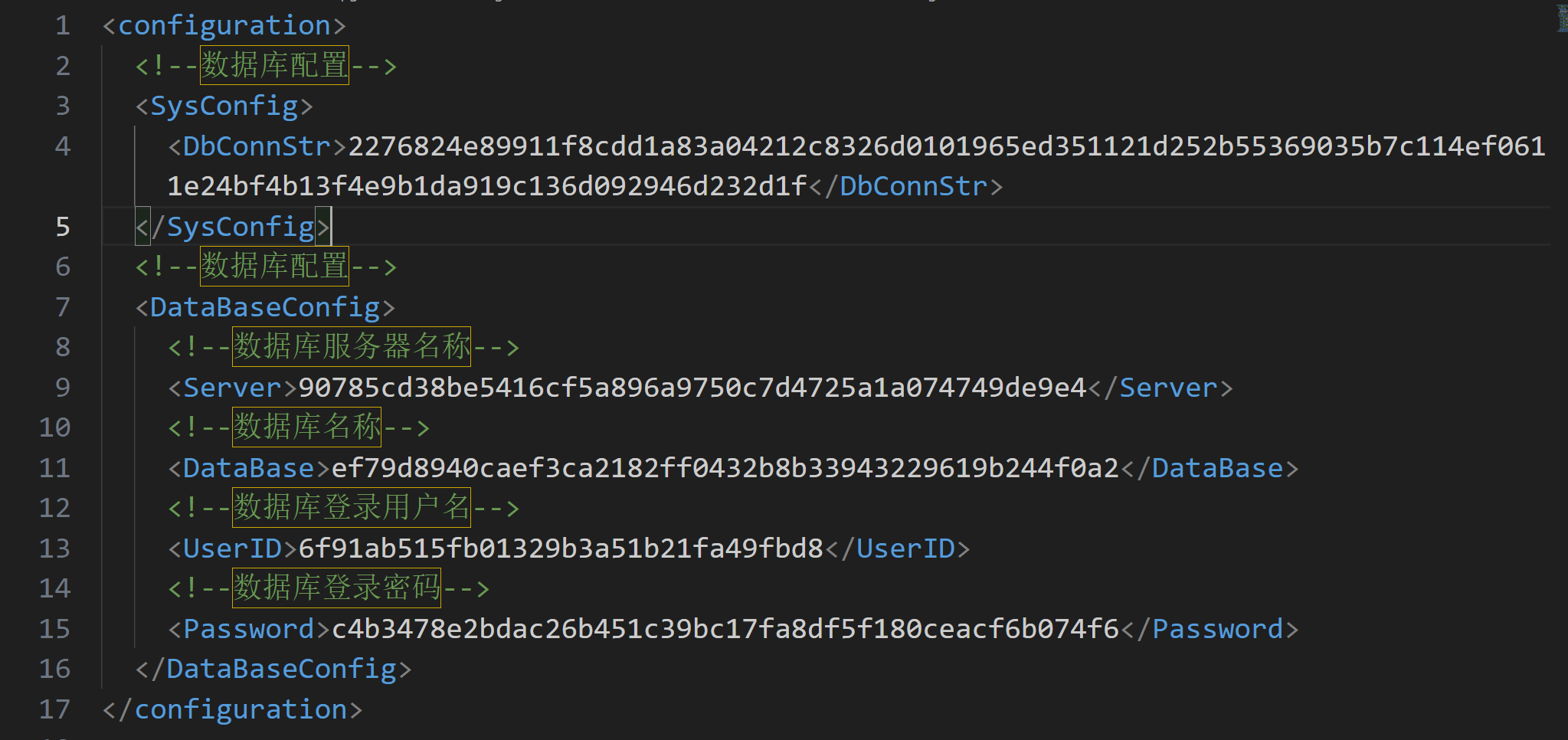
逆向dll文件发现config的解密函数,根据函数进行解密,2276824e89911f8cdd1a83a04212c8326d0101965ed351121d252b55369035b7c114ef0611e24bf4b13f4e9b1da919c136d092946d232d1f逆向md5解密得到flag{fq4rfbxg3mlvweaq5dvog39150b0471f1c5f7F3NUIYctiger}




 浙公网安备 33010602011771号
浙公网安备 33010602011771号