第八届工业信息安全技能大赛-工业密码安全锦标赛
maigc_xor
from z3 import *
# Go代码输出的结果
res = [
[42, 172, 138, 158, 68, 113, 181],
[107, 222, 173, 166, 41, 41, 227],
[68, 137, 171, 166, 120, 99, 158],
[56, 140, 182, 166, 96, 113, 189],
[117, 187, 185, 156, 98, 105, 255],
[23, 179, 178, 150, 107, 107, 172],
[45, 162, 163, 149, 104, 121, 183]
]
# 创建一个Z3求解器实例
s = Solver()
# 定义未知变量:pad和flag字符
pad = [BitVec(f'p{i}', 8) for i in range(6)] # pad有6个字节
flag_chars = [[BitVec(f'f{i}_{j}', 8) for j in range(6)] for i in range(7)] # 每个分组6个字符
# 添加约束条件以匹配原始Go代码中的逻辑
for idx, r in enumerate(res):
s.add(r[0] == (flag_chars[idx][0] ^ flag_chars[idx][1] ^ flag_chars[idx][2] ^ pad[0]))
s.add(r[1] == (flag_chars[idx][3] ^ flag_chars[idx][4] ^ pad[1] ^ pad[2]))
s.add(r[2] == (pad[5] ^ flag_chars[idx][5] ^ pad[1] ^ pad[3]))
s.add(r[3] == (flag_chars[idx][3] ^ pad[3] ^ pad[4] ^ pad[1]))
s.add(r[4] == (flag_chars[idx][5] ^ pad[0] ^ flag_chars[idx][4] ^ pad[1]))
s.add(r[5] == (flag_chars[idx][2] ^ flag_chars[idx][4] ^ pad[0] ^ pad[1]))
s.add(r[6] == (flag_chars[idx][2] ^ flag_chars[idx][0] ^ flag_chars[idx][4] ^ pad[4]))
# 假设我们知道flag是以"flag{"开头并且以"}"结尾
for i, c in enumerate("flag{"):
s.add(flag_chars[0][i] == ord(c))
s.add(flag_chars[-1][-1] == ord('}'))
# 检查是否可满足
if s.check() == sat:
m = s.model()
recovered_pad = ''.join([chr(m.evaluate(pad[i]).as_long()) for i in range(6)])
print("Recovered pad:", [m.evaluate(pad[i]).as_long() for i in range(6)])
# Recovered flag
recovered_flag_parts = []
for group in flag_chars:
part = ''.join([chr(m.evaluate(group[i]).as_long()) for i in range(6)])
recovered_flag_parts.append(part)
recovered_flag = 'flag{' + ''.join(recovered_flag_parts).replace('flag{', '').replace('}', '') + '}'
print("Recovered flag:", recovered_flag)
else:
print("No solution found")
where_is_flag
from PIL import Image
def extract_secret(im, length):
s = im.size
bin_result = ""
k = 0
for i in range(1, s[0]):
for j in range(s[1]):
if k == length * 7: # 假设每个字符是7位长
break
idx = (i * j) % 3
p = bin(im.getpixel((i, j))[idx]).replace('0b', '')
bin_result += p[-1:] # 提取最低位
k += 1
if k == length * 7:
break
return bin_result
def b2s(b):
result = ''
for i in range(0, len(b), 7):
byte = b[i:i+7]
result += chr(int(byte, 2))
return result
def main():
# 知道flag的长度为25个字符(包括大括号),所以需要25*7=175个bit
secret_length = 48
im = Image.open("bbb.bmp") # 加密后的图片
bin_result = extract_secret(im, secret_length)
print("Extracted binary:", bin_result)
# 将二进制字符串转换为字符串
secret_message = b2s(bin_result)
print("Decoded message:", secret_message)
if __name__ == '__main__':
main()
familiar
import gmpy2
n = 7433166604546066296851187857545413118102149108465542022438296170488738990243656326069411283911168294481780327701530430267489379178590780782249823254565065027965908032345956666728934695536665936342119959622545637558604683037133397787684153158152950687269972576711906014809028870630994504448295283818804228756862167154985245680663124333286691472080427565303491535478046898258038401085285964694447018545143567346348581667268917650055650962771624689892101366751754977433342723455213785424010496651785503596778901392909315552472258750278651249345873524286442948157138526112873057659073045549811243810357893045271288179936621322627396579376155821316115555350821578082434156390955222019426794382731419379541176116421517581873156052673093336924051547420336003956739130042804412810072410433006404663082968625520321753458240738654820469510324963131310274635134023774008918051819930099214500521887468438182273081644764146105862803586454363505645850258633058562115509971967775930706734647175157263184226031904067881
e = 65537
c = 4896066942024423494775428930717797518176225129352389547116562246039742356340732801887831974435151317843940350598655464288244007068783158869872638955355172121708848380003408625893849771058853314682536406765102223030729764297269282582761121937524956261295322890335815629114967407737473562113743682971385288629876274395639870350376284423904698067079831636515992829922537762458203370151769454321108914704046994783664675102998124073240073918530967637316243250027764997179547647479557510916500940330126207546242897808450069733664678662889361557192033315130734802547176333740293397576656098603628476560536734171001805477737441181111686972059158188572134985422074132636536809885063797976899611460770896348750593762836364180260065309694421108983728919126430435304047072261475348658437464387152719141422764098092835998775929610013179801884637411252613606168844403203973330400286318625306002025700983088905695585654045697942236718844812339734512566139953767100521150322111624481559579992664054553034840417741808689
p = gmpy2.isqrt(n)
p = gmpy2.next_prime(p)
q = n // p
# init p q e c
from Crypto.Util.number import long_to_bytes, bytes_to_long
def decrypt_rsa():
import gmpy2
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(long_to_bytes(m))
decrypt_rsa()
丢失的密码
修改dat文件名为zip,解压得到webroot工程。
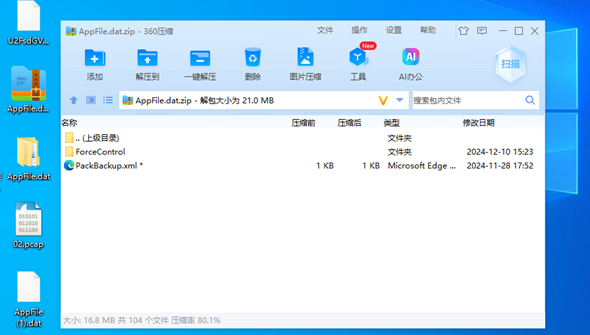
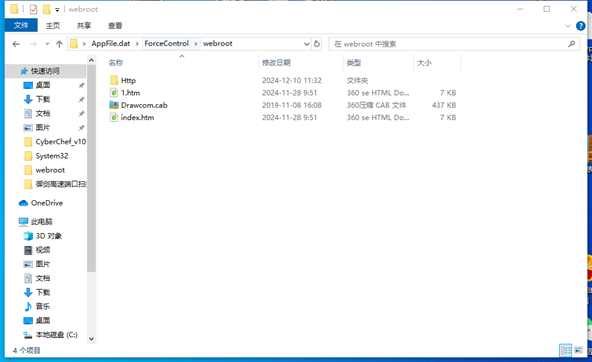
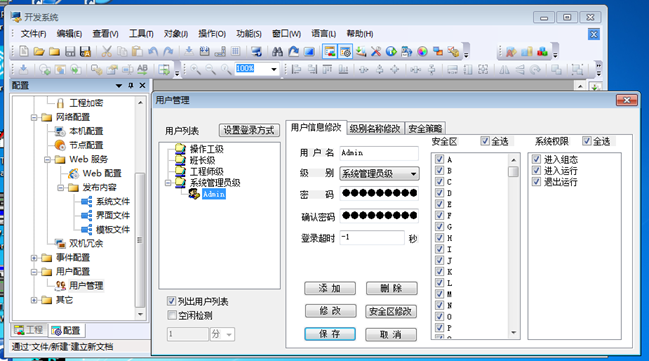
在http文件中,有dat文件,发现context.dat文件,它是力控项目中存储密码的文件,由于之前恢复项目失败,所以将所有dat文件移动到可开发的正常项目的sys目录下,开发系统后,在配置中进行查看,发现加密的admin用户密码。
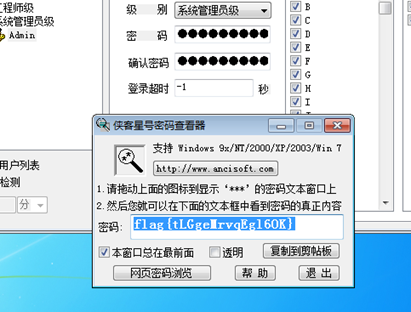
使用星号密码查看器,得到密码flag{tLGgeMrvqEgl6OK}
组态加密恢复
恢复项目后,发现提示为AES加密。
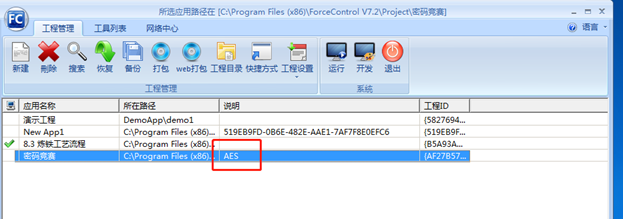
根据提示,启动循环泵后,发现流量1-流量五5,分别显示五个数字。
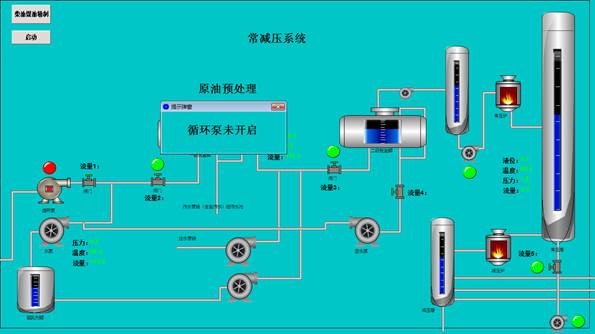
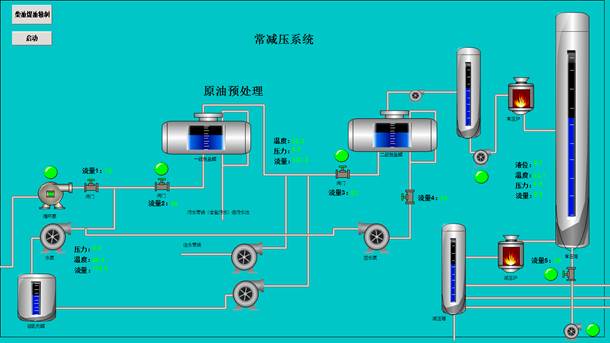
点开各阀门,根据管道顺序,分别得到压力1-压力5,五个数字。
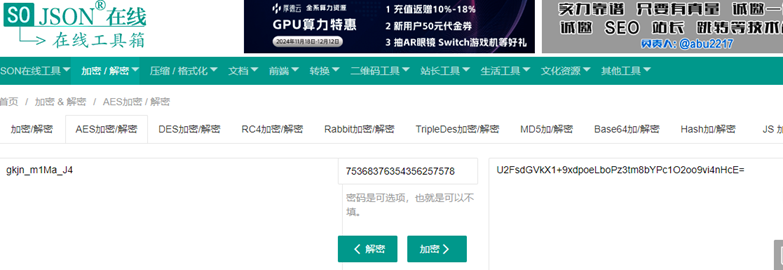
工程文件名为U2FsdGVkX1%2B9xdpoeLboPz3tm8bYPc1O2oo9vi4nHcE%3D_64,url转换得到U2FsdGVkX1+9xdpoeLboPz3tm8bYPc1O2oo9vi4nHcE=,使用AES在线解密,得到flag。
crack_hash
字符测试,需要 caaabaaacaaadaaaeaaafaaagaa 这么个长度.
搜了一下关键字是sm3 的hash.使用idapython跑出所有码表,不会的就用手中跑吧.然后处理一下.
import re
s = '''
0, 1a31687e1dcb7e3cec7bfbfd2d2670865b09b47f0546c5e83e7352422557c9dd
1, 7b55b1eda0fa4f17e8d7a6a60675f873c18ab057744167a13cfb8f78f91123d2
2, 8454f43b206332d1e379e91521d5bc254bf566481b9fbcb01c45f4132158ea62
3, 71e5027fbf5e26e0eccbbca70525f8afbc26b543a737477414f089bd82c9f403
4, 0a1caa0ce3266e23aad3bc0aa475f1e10521a0755214b8178d74adad5a535590
5, 4c6bdbaa691b3eaa8c9b14a36773f9e779f1bbdd7bac97001cee2b312175bafc
6, 1337863b1c4c290ac1dab5741565b0f9bc0f4fde51436b3c14355c6235b2cdd5
7, d82b7a3e09b41503fadbf6403d5ff9e4c6bc7cbd20b41864dc3790bd83dbdd9d
8, d2c865ed719de7c3c0dbdc63ab65fd9b85b14bf3fe0e860f3857785aa115ed3f
9, ebabef3bbe080c84c9cbbdb6e5dd49c74845eab97ce99a6f0879ca1ee410c21f
a, 9007621af14201fecb0bb7800d7ef191c4d9836f40cc9d27ae303d402007b77e
b, b1f96e1b7a2d3b76a2d3b4f666fdfd23c86e1f1b1049df0c1e609980a91a0b83
c, fd1e5d97e98e3a6ce05ffde8953dd8ce8e9534d6b92748cb14642b5601415b15
d, bf195426b725f7ccea1daa062575fa81ef26fedef950b9ce34e4ef34a515c91d
e, 8f0cc6be1ee60267e8d8cfcb34b5d51b8129efd629bdc2ed5ce089bc175596ad
f, a666fb86aca737d388daaf1e41759156b843584f89820d900c72f0d8a87430ba
g, 5881983b472c23bd7cda387d2121eaee5704bda42b65be430d773eb53155afb7
h, 33db2abca9545b08a81b3d980436f9c4d8fefc96a572d0b08c75e36d13cb9d3b
i, f3cd63c1e3bb613a69debc2fa175f9df6380cbbb36bffc529824b61d2916b815
j, 24c0710e24913468f9db29e8a975d5069d3571380de61f39085869724d502f58
k, 866b0483da9d4e51a8fbade2277deb043f14eee1717d17f9d962dc1ceb125ea1
l, f1c90f6762d8f00ff8d37d212165f9a972a0c0796b1f9f500df5b877a969706b
m, 156686463c186ff7f999b7e28d394050233a91308149d94d5dbec8d4415d2864
n, fc2041980925712a48fcf3f22356f8284ee8ac1eef1b94642c7743f5a71aef40
o, 0e3f9421d56711070adabdd035b1f9ac7aea49ac0973b6dc1e59ca3811621dc2
p, 7757181f2cb90715e8d9b0180d65ecc27e55a7c75b7860a5197e16b8337b18a0
q, 7852e8c80c0fcdb2ed9cadd83565e1a1ad4e7503b865c7d03cf8a778bdd712b6
r, 071d155ffbeef21461fa11096d677993dbb20ae7c7c591711d7e85540164f7db
s, f6d82d6a9aaf7454eadb9c9e2565dca1ea3b0a2ddcde29cf3e46495241513d9d
t, 99de1d4c3caf8d89fadf7c4cad15799c6c9a67b2c92ccef91d699ea06154e79a
u, a7804d461b5055337059fdf409763aad2b1bf33d18d6d74d0cd8b33c95b505a2
v, c102f233c5b54cdcec57b938047df05ff863d8291a84d1659cff713a3b7ecbef
w, 85307acbcba93c5dca9fb86ca575fea28a6bb12ff38ae4797c526212ab64feef
x, bed9b252c66826c8e8dd343007757e5b70719558aaf623441c7ab1fc31114b88
y, 0347af304e45bc07ac92387c8017acaeada86e8a54c1e27f1a757feee045f99a
z, 4fb6bc6207f8310ed9dbbebd65fca672e7a7b0038718ce6b16558ad1227373c8
A, 7a2ec6ad025e81bde8dbbe842770d3aafb704d3a11a4ea46dc75d800e35e09fb
B, cf203e1629b6fcffa8dba8ae2c545c46a7e26c8bcde9c06458d12006615d658a
C, 5cbd9011ab53c845a8dbcd43298c3da6abc3f6a4fe2cf8845d73a7a823102d6e
D, f8a50f224845f567f89b9d503579e919148fb97a97e6a69a1c3444f61971ba26
E, 2f284c3511e0f791e0cbbd032145587197313353e296b3f11a7ba3b91945ad09
F, eb51c1daf4ce24a6cb5c3cf62d41eb5809147a69b6bb2ae0aef286b02416da6b
G, 502e42ff3cf5be936c9be50aa577f99cf7a00ff86464edb33c3059ade1159198
H, 99dafbffd21bf1c7e15bbfc43557f1cc82b6f29dd325584fbc6470a8975640c9
I, ec1556cda4a92c46fcc37d4f2de7fde121cf38965721db1a995e08f9895d38f4
J, c05a912201ae148988d99fc16575f92a98ac23bc285402f33dfe8f1a4707e3a1
K, 64f062716fa2fe44a89b7dfa356d7907ab837fa47b64c0792e7d149c217cc93e
L, 89843fc991be4a4ce79fbda80f979998f5da05e91044d3cc9cefec3561d1a369
M, ad3a65d3da139296e05fbebfb074ab9871f84e92adee6916544247df605e44b9
N, cb8d0f0f7c5b7033ccdbbc99a5517877b5a78aaf15cb344a1d5477fca157093a
O, 9bc5e089b91d0405e9d38df52c3549cb1eb228b20c71c5423c3698eb6157340d
P, 8fe0c5bab43ea56ea84fae342cd4f844e6b666b71485395154c77b2f05432ec1
Q, d6d3f208011ea62249dbbf5a25119a300eb576394feda4bc1c7ec6b423d0aa67
R, cef1906200c43bf1e8f9b8213f117cb06de4cc5fd33383764eef29d629720fa5
S, d74d91acc6d49b8e52db84fb3935e9e8f65fcce89f6d758a15f5ec8321d57f10
T, c47599c9eaafe947ab9a36f8257bf4718d43942a8e9521155c042dd3a1177b21
U, c3c575b3921d89492cdfbc0b615e5a71b7dec9345314066c5d741985a1409e3c
V, 47be4865a7dc8490f04278db2475fbfe805119e22c4955361460f08e30500aa6
W, b10fb7cd089e86e178feb5675133dbd26eaa40065cafc16e144aacf029736db9
X, 347497227c946131addbff8425704189ea778009f21b12231976c97ba137e735
Y, 7ef080b118fe9571608acc032653dc265b2c06fa402fb34e3d5d11920147e5f6
Z, 331ed6b564ca4cbfc81b796905dd715df488784699b6ae6cdc5a736301072b43
!, 27752ae6584b15f9a0fb98ab02456913884f1944f7fd0056cdb7234a2011f957
", bfbd007d1daa7a54c059bcea2565fff0714e58d6e390543e5f7742463955e62f
#, 5198c6bc7d11e1aafada9d8e35fcf5c7ff13cd7231e1dcb11c2408f3a715b791
$, dfeaad73e2c8ce0478af91c481f55c9643f05bfd72e98fce2c75da02655bb892
%, a1dbd06ff08d5af6e8f33dbb2250711fb72e75b31774aa5f0056017a257001d0
&, a92fcb7a479ae4c6885fdf7c897db0148b16c03174bceeb57c6385972355ea47
', 24fc2e62b61cc72dc0d899788535d065ab78a15f8eab3cf31d59b5072151eee3
(, 37928248c49a7afc3ddb945784768beac2f6d2725dc0d492381679c6a948db30
), 485fccdb2813336aa8abb9a23515805ea4a901a8dac57e351d6a7fb620d93572
*, 2cddc7a226afc928e9d237a42d55f1487d96c2f77a6393b21b71370270d3885b
+, 01e7f436237b9fb1e89bb52513f7f8d9e4fa258216f8bcd79e346158e50825a7
,, 141f91cd2adeb565e0dc39741334b04bff38891d474e28fb3a7604b82292b6f4
-, 553db6591c813a5be0cb4dbc2e67a9fbece5a5b59cb705cc7e63628f23453e23
., 88ed98c0d435c597c88bbc155fc5184b19da480099fcbcfc9d6d82ab45d6939a
/, a966380ea3de103be4db9934297df8340f15ed5a6f596f7495737681801a2aaf
:, d58441950de67101bafba4fe6061ed6fdcc619eda5a5ea02bc3a3e70a947b947
;, f52aa64e7dc98f226ad9dcc265a95c8e24943967d7c33f1d10f3d339675b23c8
<, a9fdbcec7452a480f85bac8729adbf4dd6c75fb697355e8e2c71059d23590ad8
=, aa7d5282e99771880cff3c2e957dd50c1eb36a1a424360273b321846f137f829
>, 1814b20da195a1e4eceb6ddc7d7550b53a9def98319a8f7d1c657d79235887aa
?, 807c12464b6920bbe13abf8820ddb8177aa777d4cdb03c9f545520d62f40b648
@, 1c38370f17b16303edcaff6e3535c89a81ac6f95b01afbd11b6679820163df0c
[, a3220f15b84ae476ecda8cf7257c410fa3520b634161288d6cb3541b305c7f89
\, d46c76860e16e11feadb5ccca9756db52af983966b25d48db074671f2542d3c2
], 73f2de33bd1f3dc9f8dab8452131b8ed70006d9a50bb0fd6187514cc198b1a10
^, 04cc6ec7623d0944e81bb4d10d5f71aa43776fe449ed366a1430484a634244e6
_, a3dfc5921a0b5199e1cbb50e6535f01f87f6d41034f12b67086505a023572ae5
`, 55213381a327a665a8cba4602176d810f05b92a3bc64ca000cf1f67371d35e42
{, be547e87cffc9e1bf9b9fd9b2665fa41d60921274aa154e70560095f0253d0cd
|, 552a675751ef7628d87bb9a527a3d81ea68d0ddedc5feba474f754b9ac04f3eb
}, 2848d73ad31b879f9c59b40625f6dd523659ebdc216780e60af729cce1738fcc
~, 34f1079fef3e44daeadf5da62135fa3aea1c35440e84c4ce3937d5fc0117b8b3
'''
s = s.strip()
dic = {k: v for v, k in (line.split(', ') for line in s.splitlines())}
enc = open('out.bin', 'rb').read().hex()
# txt 64个一组
for x in re.findall('.{64}', enc):
print(dic[x.lower()], end='')
flag{SM3_me4n_1s_Sh4ngM1_3}
异常的协议读取
ip.dst == 192.168.1.181 的流量中有一条流量的端口为 10990, 包号为574,
正常的流量包为11000
研华SCADA
3284号包发现写入flag..的响应包是 Ao(mgHSIN`FE0fcCMYtY
直接解base85
flag{19YtrEkkl8}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号