需求:
一、bind服务器软件安装
1.安装bind安装包
yum install bind-chroot -y
2.关闭防火墙
systemctl stop firewalld.service
(centos6 service iptables stop)
3.查看防火墙状态
service firewalld status
配置文件
cat /etc/named.conf
cat /etc/named.rfc1912.zones
cd /etc/named/自定义zone文件
自定义zone文件和named.rfc1912.zones文件名字要保持一致
二、修改配置
修改全局配置
检查配置是否正确
named-checkconf /etc/named.conf
// // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // // See the BIND Administrator's Reference Manual (ARM) for details about the // configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html options { listen-on port 53 { any; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.root.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
配置zone
vim /etc/named.rfc1912.zones
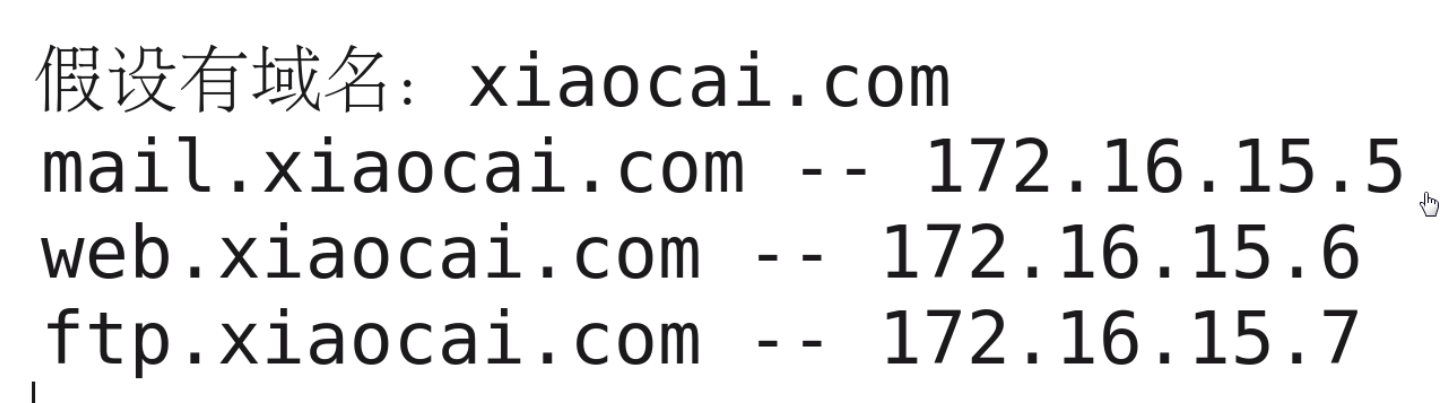
zone "xiaocai.com" IN { type master; file "xiaocai.com.zone"; allow-update {none; }; };
file文件在/var/named/目录下要创建
cd /var/named/
目录下文件当作是模板
cp -a named.localhost xiaocai.com.zone
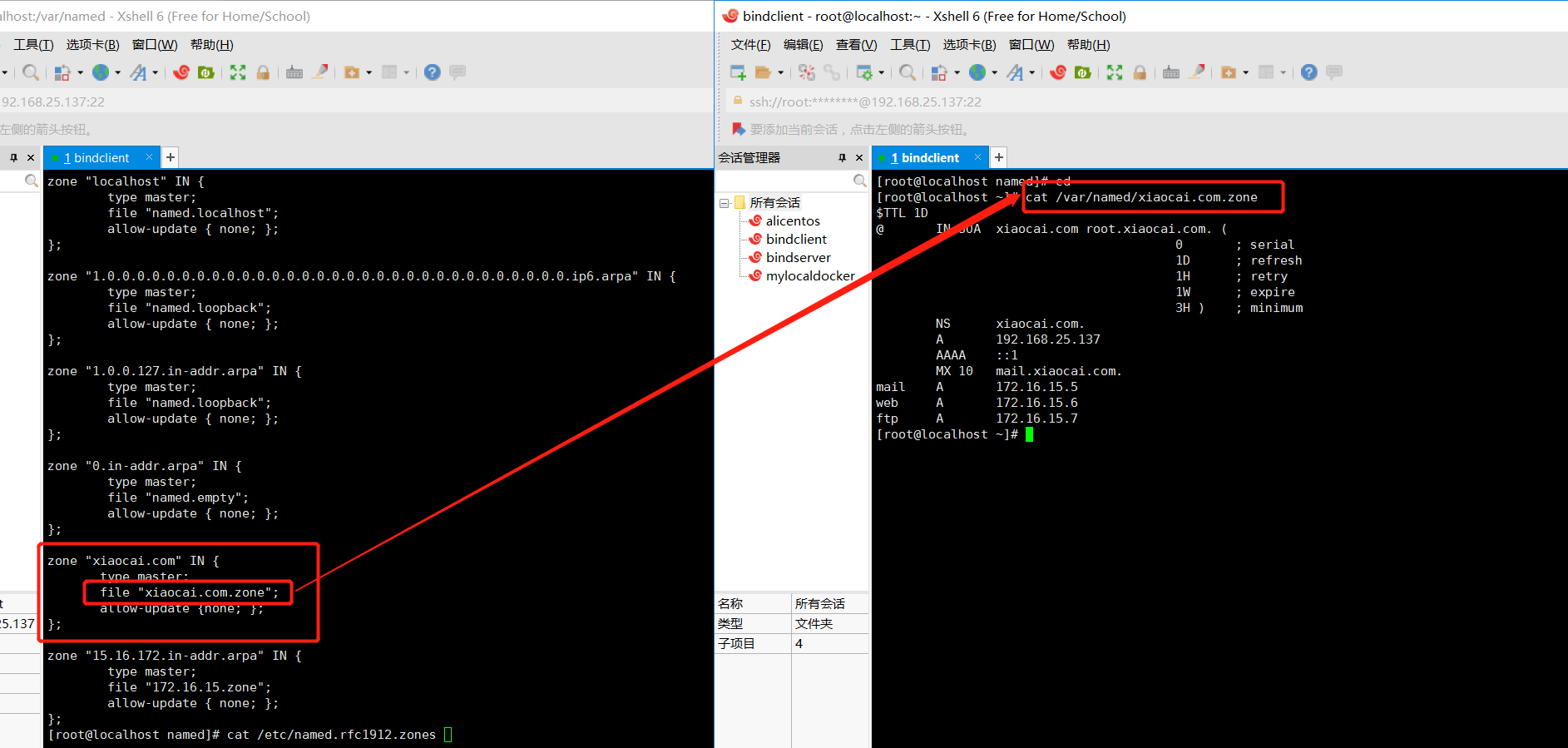
$TTL 1D @ IN SOA xiaocai.com root.xiaocai.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS xiaocai.com. A 192.168.25.137 AAAA ::1 MX 10 mail.xiaocai.com. mail A 172.16.15.5 web A 172.16.15.6 ftp A 172.16.15.7
把@改成zone, rname.invalid.是邮箱地址
开启服务
service named start
修改DNS解析服务器
[root@localhost named]# cat /etc/resolv.conf # Generated by NetworkManager search localdomain nameserver 192.168.25.137 #nameserver 192.168.25.2
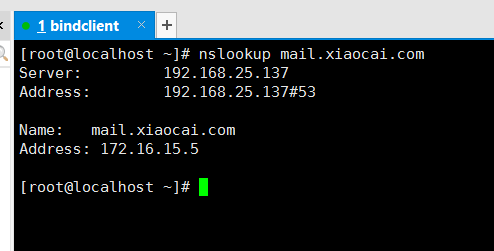
验证是否配置成功
nslookup mail.xiaocai.com
二、方向解析PTR
反向查找,通过ip查找域名
vim /etc/named.rfc1912.zones
zone "15.16.172.in-addr.arpa" IN { type master; file "172.16.15.zone"; allow-update { none; }; };
在file文件在/var/named/目录下要文件file,172.16.15.zone
cd /var/named/ cp -a named.loopback 172.16.15.zone
$TTL 1D @ IN SOA xiaocai.com. root.xiaocai.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS xiaocai.com. A 192.168.25.137 MX 10 mail.xiaocai.com AAAA ::1 5 PTR mail.xiaocai.com. 6 PTR web.xiaocai.com. 7 PTR ftp.xiaocai.com.
5,6,7数字代表的是网段
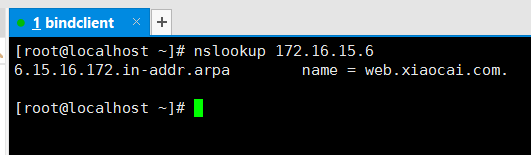
重启服务
service named restart nslookup 172.16.15.6







 浙公网安备 33010602011771号
浙公网安备 33010602011771号