k8s 部署dashboard 2.7.0
查看dashboard版本兼容性
| Kubernetes version | 1.22 | 1.23 | 1.24 | 1.25 |
|---|---|---|---|---|
| Compatibility | ? | ? | ? | ✓ |
k8s版本:v1.25.2
准备dashboard yaml文件
# wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml准备image
# docker pull docker.io/kubernetesui/dashboard:v2.7.0
# docker tag docker.io/kubernetesui/dashboard:v2.7.0 192.168.174.120/baseimages/dashboard:v2.7.0
# docker pull docker.io/kubernetesui/metrics-scraper:v1.0.8
# docker tag docker.io/kubernetesui/metrics-scraper:v1.0.8 192.168.174.120/baseimages/metrics-scraper:v1.0.7
# docker push 192.168.174.120/baseimages/metrics-scraper:v1.0.8
# docker push 192.168.174.120/baseimages/dashboard:v2.7.0修改yaml文件image地址
# sed -i 's@kubernetesui/dashboard:v2.7.0@192.168.174.120/baseimages/dashboard:v2.7.0@g' recommended.yaml
# sed -i 's@kubernetesui/metrics-scraper:v1.0.8@192.168.174.120/baseimages/metrics-scraper:v1.0.8@g' recommended.yaml 开放访问端口
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30003
selector:
k8s-app: kubernetes-dashboard部署dashboard
# kubectl apply -f recommended.yaml namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created查看pod信息
# kubectl get pod -n kubernetes-dashboard -o wideNAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
kubernetes-dashboard dashboard-metrics-scraper-c5f49cc44-cdbsn 1/1 Running 0 4m7s 10.200.154.199 192.168.174.106 <none> <none>
kubernetes-dashboard kubernetes-dashboard-688994654d-mt7nl 1/1 Running 0 4m7s 10.200.44.193 192.168.174.107 <none> <none>创建用户
admin-user.yml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin # 默认内置的 ClusterRole, 超级用户(Super-User)角色(cluster-admin)
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard创建用户
# kubectl apply -f admin-user.yml serviceaccount/admin-user created
clusterrolebinding.rbac.authorization.k8s.io/admin-user created创建临时token
# kubectl -n kubernetes-dashboard create token admin-usereyJhbGciOiJSUzI1NiIsImtpZCI6IklkYWRmQU53aV8yYlU4amdheGY0aXhseVNDMDhOZFg3SElVdjNFbHowaFEifQ.eyJhdWQiOlsiYXBpIiwiaXN0aW8tY2EiXSwiZXhwIjoxNjkxMTI4OTE3LCJpYXQiOjE2OTExMjUzMTcsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2YyIsImt1YmVybmV0ZXMuaW8iOnsibmFtZXNwYWNlIjoia3ViZXJuZXRlcy1kYXNoYm9hcmQiLCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoiYWRtaW4tdXNlciIsInVpZCI6IjBiOGU1NjJhLWMxOTEtNGQ4MC04MWFmLTRlMTJkYjlhOGU1OSJ9fSwibmJmIjoxNjkxMTI1MzE3LCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4tdXNlciJ9.UxTyvPSDJGvssJtfvZjUk-s4b2BrXWK58OoUmB3HuS5PYNPA3X9gtUoqwUncz-Mata9amFob14X9DObY7C7t9fJrxjZ8x8uqemyiwu_6IlDrOSugf3h0F-YJ84hupKlwCbdHs5LX18HEmt2yCoaHsUmSHQL2wQJ7cOW9SRZC5BJhRzXWhvBQ8zHk78612IWtFlbOdah75kVpR42qAhQHy5SVJRrgC337Por-L6xta9UyuvYNRGRyotMLsOIvaZgdfJDvFj9ujGORgWI7fIuP79fgVd9yUh4C9tEajUakXnm_kdlkWEoCHl_xupulytx0LShSQtMlaXdf6pR3h79uTg创建长期token
admin-user-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: admin-user-secret
namespace: kubernetes-dashboard
annotations:
kubernetes.io/service-account.name: admin-user
type: kubernetes.io/service-account-token创建secret资源
# kubectl apply -f admin-user-secret.yamlsecret/admin-user-secret created查看secret资源
# kubectl get secret -n kubernetes-dashboard NAME TYPE DATA AGE
admin-user-secret kubernetes.io/service-account-token 3 71s
kubernetes-dashboard-certs Opaque 0 294d
kubernetes-dashboard-csrf Opaque 1 294d
kubernetes-dashboard-key-holder Opaque 2 294d查看token
# kubectl get secret admin-user-secret -n kubernetes-dashboard -o jsonpath={".data.token"} | base64 -deyJhbGciOiJSUzI1NiIsImtpZCI6IklkYWRmQU53aV8yYlU4amdheGY0aXhseVNDMDhOZFg3SElVdjNFbHowaFEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXNlY3JldCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbi11c2VyIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMGI4ZTU2MmEtYzE5MS00ZDgwLTgxYWYtNGUxMmRiOWE4ZTU5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmFkbWluLXVzZXIifQ.zFKD9eXOqwyz2hX6hIWVYnGnOkgrqYDJhjd3OQlJkGXVwuaOemu4v6kKhAe6At7zW-4Ns4cpMqfREHUOXMazqMik_J0ON6Arr2J6Scs7wEYanH5yNG-cdTEH_HhwgGfNfY4jbnJy3CFXEHgxpxnWbImQTqXFUKPBMqiLKF3vCBzfe04hjfdw33QGOqzPGcAQCLeQfiHK51rvlOoXFqBs_A1g1ioIMsZ5iysj3GzrMhBmZDmFrO_EVk5JZuE8Akxf9hbyU5fwXQ5diyNWwHcosi73cKoAQ9n6mfSkxdrgqozYv_u0yzcrtKU6l9qi6-DjL-MtbPCZ44-V95n832SoDQ访问dashboard
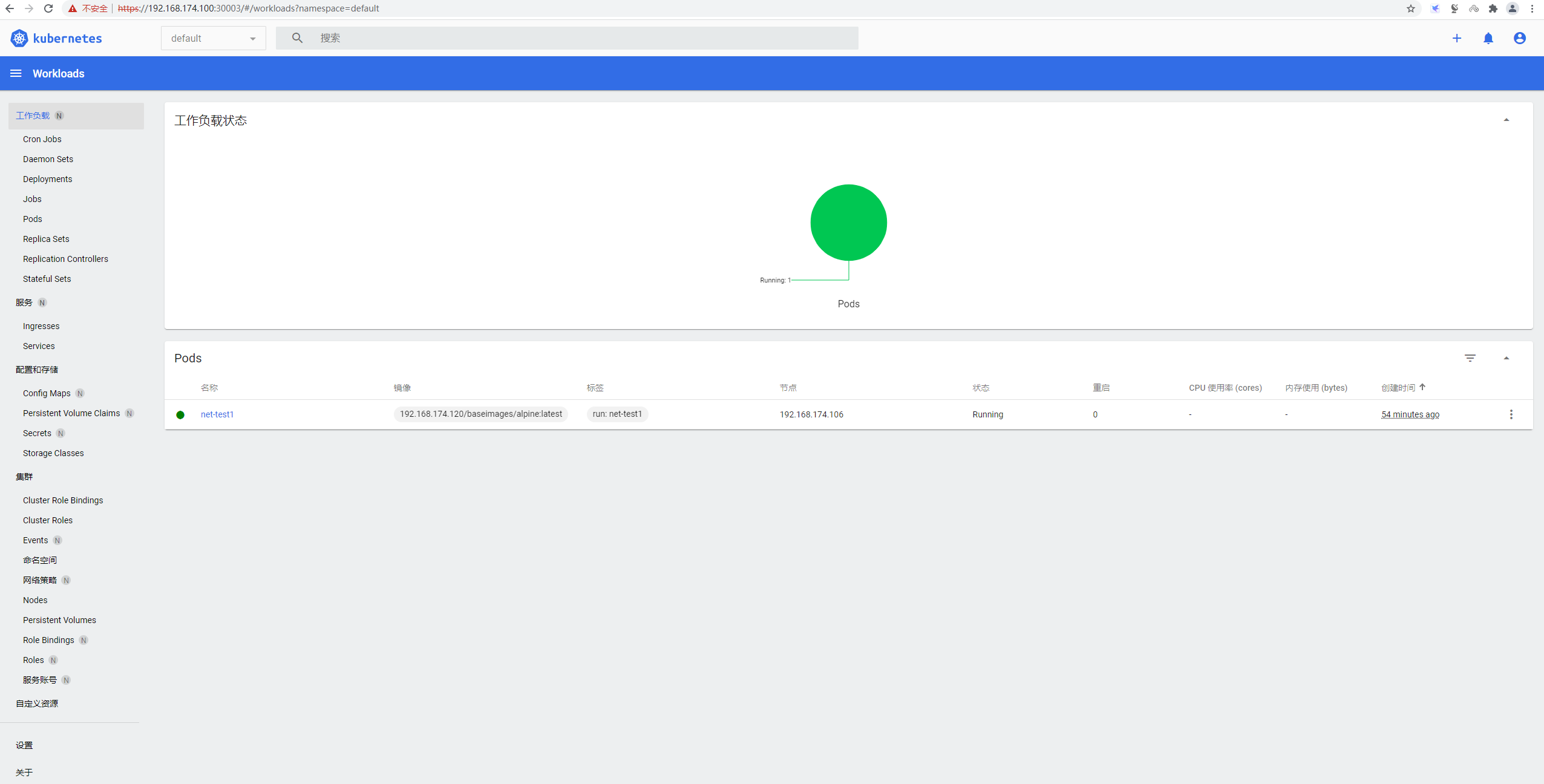
参考文档
https://github.com/kubernetes/dashboard
https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md


 浙公网安备 33010602011771号
浙公网安备 33010602011771号