ISO/SAE 21434 工作产品与要求的映射关系
ISO/SAE 21434标准中一共要求输出42项工作产品,在附录A列出了网络安全活动和工作产品(WP)的关系,见下文表1。本文对其进一步完善,加入了每个工作产品对应的具体要求编号,见下文表2。
另外在标准中存在部分要求(RQ)没有明确说明对应的工作产出,在表2里对此类要求进行了高亮显示,其中一部分可以关联到已有的工作产品中,但仍有部分要求会产生新的工作产品。
PS:欢迎关注公众号Vehicle CyberSecurity,获取更多内容
表1 网络安全活动和工作产品的映射关系
|
Sub-clauses |
Work Product |
||
|
Organizational Cybersecurity Management |
|||
|
5.4.1 |
Cybersecurity Governance |
WP-05-01 |
Cybersecurity policy, rules and processes |
|
5.4.2 |
Cybersecurity Culture |
WP-05-01 |
Cybersecurity policy, rules and processes |
|
WP-05-02 |
Evidence of competence management, awareness management and continuous improvement |
||
|
5.4.3 |
Information Sharing |
WP-05-01 |
Cybersecurity policy, rules and processes |
|
5.4.4 |
Management Sytems |
WP-05-03 |
Evidence of the organization’s management systems |
|
5.4.5 |
Tool Management |
WP-05-04 |
Evidence of tool management |
|
5.4.6 |
Information Security Management |
WP-05-03 |
Evidence of the organization’s management systems |
|
5.4.7 |
Organizational cybersecurity Audit |
WP-05-05 |
Organizational cybersecurity audit report |
|
Project Dependent Cybersecurity Management |
|||
|
6.4.1 |
Cybersecurity Responsibilities |
WP-06-01 |
Cybersecurity plan |
|
6.4.2 |
Cybersecurity Planning |
||
|
6.4.3 |
Tailoring |
||
|
6.4.4 |
Reuse |
||
|
6.4.5 |
Component Out-of-context |
||
|
6.4.6 |
Off-the-shelf Component |
||
|
6.4.7 |
Cybersecurity Case |
WP-06-02 |
Cybersecurity case |
|
6.4.8 |
Cybersecurity Assessment |
WP-06-03 |
Cybersecurity assessment report |
|
6.4.9 |
Release for Post-development |
WP-06-04 |
Release for post-development report |
|
Distributed Cybersecurity Activities |
|||
|
7.4.1 |
Supplier Capability |
None |
Supplier capability evaluate |
|
7.4.2 |
Request for Quotation |
None |
Cybersecurity RFQ |
|
7.4.3 |
Alignment of Responsibilities |
WP-07-01 |
Cybersecurity interface agreement |
|
Continuous Cybersecurity Activities |
|||
|
8.3 |
Cybersecurity Monitoring |
WP-08-01 |
Sources for cybersecurity monitoring |
|
WP-08-02 |
Triage triggers for cybersecurity monitoring |
||
|
WP-08-03 |
Cybersecurity event triage |
||
|
8.4 |
Cybersecurity Event Evaluation |
WP-08-04 |
Cybersecurity event assessment |
|
8.5 |
Vulnerability Analysis |
WP-08-05 |
Vulnerability analysis |
|
8.6 |
Vulnerability Management |
WP-08-06 |
Vulnerability management |
|
Concept Phases |
|||
|
9.3 |
Item Definition |
WP-09-01 |
Item definition |
|
9.4 |
Cybersecurity Goals |
WP-09-02 |
Threat analysis and risk assessment |
|
WP-09-03 |
Cybersecurity goals |
||
|
WP-09-04 |
Cybersecurity claims |
||
|
WP-09-05 |
Verification report |
||
|
9.5 |
Cybersecurity Concept |
WP-09-06 |
Cybersecurity concept |
|
WP-09-07 |
Verification report of cybersecurity concept |
||
|
Product Development Phases |
|||
|
10.4.1 |
Design |
WP-10-01 |
Refined cybersecurity specification |
|
WP-10-02 |
Cybersecurity requirements for post-development |
||
|
WP-10-03 |
Documentation of the modelling, design, or programming languages and coding guidelines |
||
|
WP-10-04 |
Verification report for the refined cybersecurity specification |
||
|
10.4.2 |
Integration and Verification |
WP-10-05 |
Vulnerability analysis report |
|
WP-10-06 |
Integration and verification specification |
||
|
WP-10-07 |
Integration and verification reports |
||
|
11.0 |
Cybersecurity Validation |
WP-11-01 |
Validation report |
|
Post-Development Phases |
|||
|
12.0 |
Production |
WP-12-01 |
Production control plan |
|
13.3 |
Cybersecurity Incident Response |
WP-13-01 |
Cybersecurity incident response plan |
|
13.4 |
Updates |
None |
Update plan |
|
14.3 |
End of Cybersecurity Support |
WP-14-01 |
Procedures to communicate end of cybersecurity support |
|
14.4 |
Decommissioning |
None |
Cybersecurity requirements for decommissioning |
|
Threat Analysis and Risk Assessment Methods |
|||
|
15.3 |
Asset Identification |
WP-15-01 |
Damage scenarios |
|
WP-15-02 |
Identified assets and cybersecurity properties |
||
|
15.4 |
Threat Scenario Identification |
WP-15-03 |
Threat scenarios |
|
15.5 |
Impact Rating |
WP-15-04 |
Impact rating, including the associated impact categories of the damage scenarios |
|
15.6 |
Attack Path Analysis |
WP-15-05 |
Identified attack paths |
|
15.7 |
Attack Feasibility Rating |
WP-15-06 |
Attack feasibility rating |
|
15.8 |
Risk Determination |
WP-15-07 |
Risk values |
|
15.9 |
Risk Treatment Decision |
WP-15-08 |
Risk treatment decision per threat scenario |
表2 网络安全活动、工作产品和要求直接的映射关系
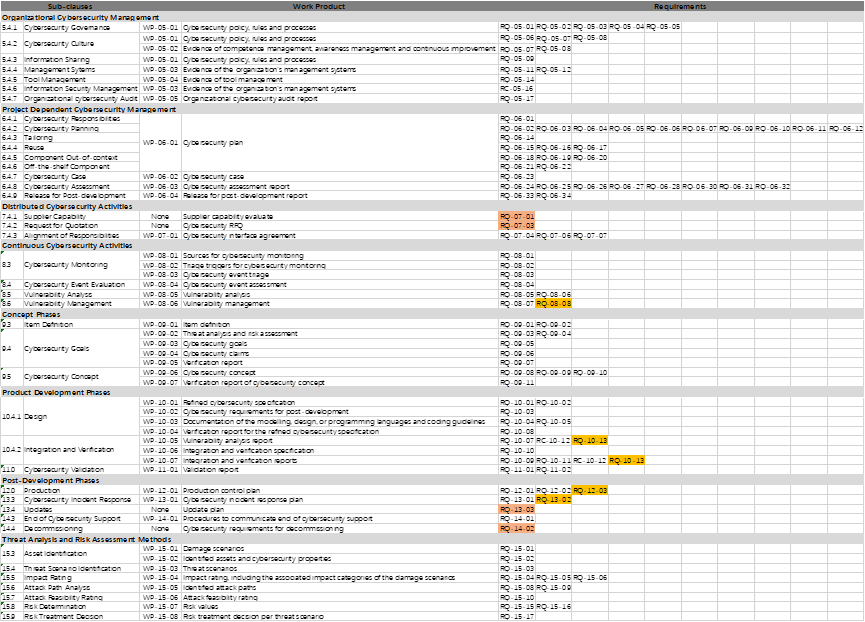
可以看到,在7.4.1.Supplier Capability、7.4.2.Request for Quotation、13.4.Updates和14.4.Decommissioning章节中并没有明确具体的工作产出,但是有具体的要求。





 浙公网安备 33010602011771号
浙公网安备 33010602011771号