CVE-2024-41592 of DrayTek vigor3910
CVE-2024-41592 of DrayTek vigor3910
固件提取
看样子是有关mysql数据库偏移,因该是加密了
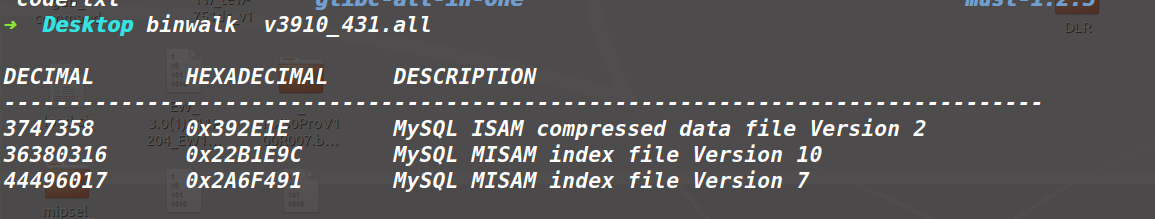
查看一下熵值,第二个是找的3912版本。
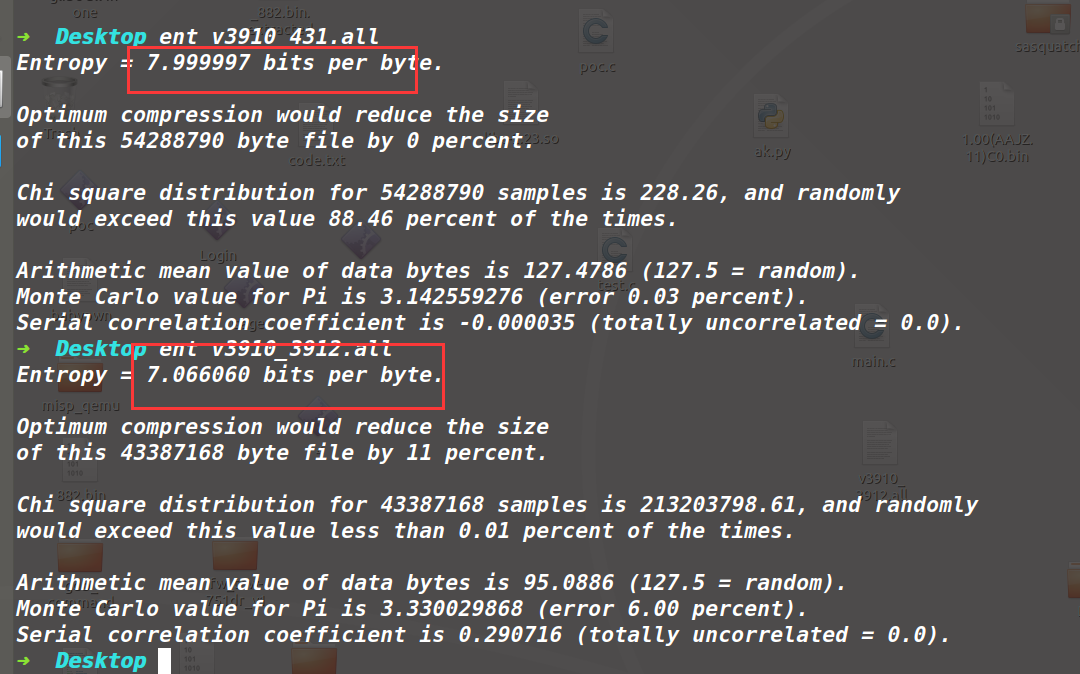
用ai分析一下
发现了 AES S-Box、AES 逆 S-Box,表明固件可能涉及 AES 加密。
发现 SHA256 哈希常量,表明使用了 SHA256 哈希算法。
发现 DES SP1/SP2,表明可能也涉及 DES 加密。
发现 PGP RSA 加密密钥,表明可能涉及 RSA 加密机制
➜ Desktop binwalk v3910_3912.all
275793 0x43551 Unix path: /home/keith/data2/cvma/firmware/bdk/libbdk-os/bdk-rlock.c
280352 0x44720 AES S-Box
280864 0x44920 AES Inverse S-Box
283888 0x454F0 SHA256 hash constants, little endian
472401 0x73551 Unix path: /home/keith/data2/cvma/firmware/bdk/libbdk-os/bdk-rlock.c
476960 0x74720 AES S-Box
477472 0x74920 AES Inverse S-Box
480496 0x754F0 SHA256 hash constants, little endian
571444 0x8B834 AES Inverse S-Box
571700 0x8B934 AES S-Box
573012 0x8BE54 SHA256 hash constants, little endian
833588 0xCB834 AES Inverse S-Box
833844 0xCB934 AES S-Box
835156 0xCBE54 SHA256 hash constants, little endian
2032925 0x1F051D Neighborly text, "neighbor %d too different %d from average %d, picking %d.LMC%d.R%d: MAJORTY: Byte %d: picking majority of %d over average %d."
2057476 0x1F6504 Unix path: /home/keith/data2/cvma/firmware/bdk/libbdk-os/bdk-rlock.c
2058368 0x1F6880 AES S-Box
2058880 0x1F6A80 AES Inverse S-Box
2097576 0x2001A8 SHA256 hash constants, little endian
2119768 0x205858 LZMA compressed data, properties: 0x5D, dictionary size: 65536 bytes, uncompressed size: 2285466 bytes
2886744 0x2C0C58 LZMA compressed data, properties: 0x5D, dictionary size: 65536 bytes, uncompressed size: 311912 bytes
3001432 0x2DCC58 LZMA compressed data, properties: 0x5D, dictionary size: 65536 bytes, uncompressed size: 630975 bytes
3155544 0x302658 Flattened device tree, size: 3392 bytes, version: 17
3159128 0x303458 Flattened device tree, size: 157 bytes, version: 17
3159640 0x303658 Flattened device tree, size: 157 bytes, version: 17
3160152 0x303858 Flattened device tree, size: 6293 bytes, version: 17
3166808 0x305258 Flattened device tree, size: 7806 bytes, version: 17
3175000 0x307258 Flattened device tree, size: 4081 bytes, version: 17
3179096 0x308258 Flattened device tree, size: 555 bytes, version: 17
3180120 0x308658 Flattened device tree, size: 157 bytes, version: 17
3180632 0x308858 Flattened device tree, size: 6941 bytes, version: 17
3187800 0x30A458 Flattened device tree, size: 6840 bytes, version: 17
3194968 0x30C058 Flattened device tree, size: 3577 bytes, version: 17
3198552 0x30CE58 Flattened device tree, size: 467 bytes, version: 17
3199064 0x30D058 Flattened device tree, size: 5957 bytes, version: 17
3205208 0x30E858 Flattened device tree, size: 4633 bytes, version: 17
3210328 0x30FC58 Flattened device tree, size: 8926 bytes, version: 17
3219544 0x312058 Flattened device tree, size: 4170 bytes, version: 17
3224152 0x313258 Flattened device tree, size: 5910 bytes, version: 17
3230296 0x314A58 Flattened device tree, size: 5243 bytes, version: 17
3235928 0x316058 Flattened device tree, size: 3825 bytes, version: 17
3240024 0x317058 Flattened device tree, size: 5242 bytes, version: 17
3245656 0x318658 Flattened device tree, size: 3878 bytes, version: 17
3249752 0x319658 Flattened device tree, size: 674 bytes, version: 17
3250776 0x319A58 Flattened device tree, size: 6129 bytes, version: 17
3256920 0x31B258 Flattened device tree, size: 6854 bytes, version: 17
3264088 0x31CE58 Flattened device tree, size: 5542 bytes, version: 17
3269720 0x31E458 Flattened device tree, size: 4040 bytes, version: 17
3273816 0x31F458 Flattened device tree, size: 3863 bytes, version: 17
3277912 0x320458 Flattened device tree, size: 803 bytes, version: 17
3278936 0x320858 Flattened device tree, size: 6293 bytes, version: 17
3285592 0x322258 Flattened device tree, size: 4223 bytes, version: 17
3290712 0x323658 Flattened device tree, size: 6840 bytes, version: 17
3297880 0x325258 Flattened device tree, size: 6293 bytes, version: 17
3304536 0x326C58 Flattened device tree, size: 3618 bytes, version: 17
3308632 0x327C58 Flattened device tree, size: 3392 bytes, version: 17
3330136 0x32D058 Flattened device tree, size: 16045 bytes, version: 17
3346520 0x331058 Flattened device tree, size: 16045 bytes, version: 17
3362904 0x335058 Flattened device tree, size: 16045 bytes, version: 17
3379288 0x339058 Flattened device tree, size: 23438 bytes, version: 17
3402840 0x33EC58 Flattened device tree, size: 24916 bytes, version: 17
3427928 0x344E58 Flattened device tree, size: 17027 bytes, version: 17
3445336 0x349258 Flattened device tree, size: 22054 bytes, version: 17
3467864 0x34EA58 Flattened device tree, size: 15109 bytes, version: 17
3483224 0x352658 Flattened device tree, size: 15449 bytes, version: 17
3499096 0x356458 Flattened device tree, size: 16157 bytes, version: 17
3515480 0x35A458 Flattened device tree, size: 16623 bytes, version: 17
3532376 0x35E658 Flattened device tree, size: 15163 bytes, version: 17
3547736 0x362258 Flattened device tree, size: 16208 bytes, version: 17
3564182 0x366296 Copyright string: "Copyright (C) 2016, Cavium Inc."
3565735 0x3668A7 Copyright string: "copyright notice and this permission notice shall be"
5044992 0x4CFB00 CRC32 polynomial table, little endian
5048472 0x4D0898 AES Inverse S-Box
5056032 0x4D2620 AES S-Box
5087559 0x4DA147 Motorola S-Record; binary data in text format, record type: header
5244704 0x500720 Linux kernel ARM64 image, load offset: 0x80000, image size: 38436864 bytes, little endian, 4k page size,
5484848 0x53B130 SHA256 hash constants, little endian
12613408 0xC07720 ELF, 64-bit LSB shared object, version 1 (SYSV)
12661400 0xC13298 gzip compressed data, maximum compression, from Unix, last modified: 1970-01-01 00:00:00 (null date)
12740040 0xC265C8 Intel x86 or x64 microcode, sig 0xffffff80, pf_mask 0x00, 1DE0-08-26, size 2048
12740184 0xC26658 Intel x86 or x64 microcode, sig 0xffffff80, pf_mask 0x00, 1DE0-08-26, size 2048
12810384 0xC37890 DES SP2, little endian
12810896 0xC37A90 DES SP1, little endian
12836144 0xC3DD30 LZO compressed data
12838688 0xC3E720 CRC32 polynomial table, little endian
13101824 0xC7EB00 Copyright string: "Copyright (c) 1999-2006 Intel Corporation."
13109416 0xC808A8 Copyright string: "Copyright (c) 2009 - 2012 Intel Corporation."
13110200 0xC80BB8 Copyright string: "Copyright (c) 1999-2008 Intel Corporation."
13112616 0xC81528 Copyright string: "Copyright (c) 2013 - 2016 Intel Corporation."
14308136 0xDA5328 Unix path: /dev/vc/0
14379920 0xDB6B90 Ubiquiti partition header, header size: 56 bytes, name: "PARTNAME=%s", base address: 0x74790A00, data size: 23295090 bytes
14387096 0xDB8798 xz compressed data
14470072 0xDCCBB8 Unix path: /lib/firmware/updates/4.9.0-OCTEONTX_SDK_6_2_0_p3_build_38
14564560 0xDE3CD0 Ubiquiti firmware additional data, name: UTE DEVICE DIAGNOSTIC, size: 1145372672 bytes, size2: 0 bytes, CRC32: 0
14612912 0xDEF9B0 Copyright string: "Copyright(c) 1999-2006 Intel Corporation"
14689831 0xE02627 Copyright string: "Copyright 2005-2007 Rodolfo Giometti giometti@linux.it"
14712897 0xE08041 Copyright string: "Copyright(c) Pierre Ossman"
14748680 0xE10C08 Unix path: /sys/firmware/devicetree/base
14749480 0xE10F28 Unix path: /sys/firmware/fdt': CRC check failed
14764721 0xE14AB1 Neighborly text, "neighbor table overflow!ate is %x"
15528256 0xECF140 LZ4 compressed data, legacy
15534992 0xED0B90 Copyright string: "Copyright 2003,2004 Andi Kleen, SuSE Labs."
15553064 0xED5228 AES S-Box
15553853 0xED553D AES Inverse S-Box
15983784 0xF3E4A8 Unix path: /usr/local/shk
16514636 0xFBFE4C eCos RTOS string reference: "ecosW"
16524059 0xFC231B HTML document header
16543893 0xFC7095 LUKS_MAGIC
16544849 0xFC7451 xz compressed data
16631913 0xFDC869 PGP RSA encrypted session key - keyid: D8020270 1B1148DC RSA Encrypt-Only 1024b
16915584 0x1021C80 Unix path: /dev/net/tun
17219408 0x106BF50 OpenSSL encryption, salted, salt: 0xC00770252D323573
17230315 0x106E9EB HTML document header
17252983 0x1074277 Private key in DER format (PKCS header length: 4, sequence length: 2345
17348619 0x108B80B OpenSSH RSA public key
18950509 0x121296D Unix path: /usr/lib64/tc/
19456566 0x128E236 gzip compressed data, ASCII, from VM/CMS, last modified: 2008-04-20 10:46:28
21215506 0x143B912 SHA256 hash constants, little endian
21237835 0x144104B AES Inverse S-Box
22985795 0x15EBC43 SHA256 hash constants, little endian
23842822 0x16BD006 Neighborly text, "neighbor C %s"
24116820 0x16FFE54 gzip compressed data, ASCII, from VM/CMS, last modified: 1995-10-23 23:02:27
24691169 0x178C1E1 Unix path: /var/run/isol_gN'
27184087 0x19ECBD7 XML document, version: "1.0"
27512658 0x1A3CF52 VMware4 disk image
27513305 0x1A3D1D9 Executable script, shebang: "/bin/sh"
27557271 0x1A47D97 AES Inverse S-Box
27557527 0x1A47E97 AES S-Box
27557815 0x1A47FB7 DES PC1 table
27557903 0x1A4800F DES PC2 table
27578667 0x1A4D12B Base64 standard index table
29314689 0x1BF4E81 Unix path: /dev/net/tun
29752737 0x1C5FDA1 Copyright string: "Copyright 1995-2005 Jean-loup Gailly "
30126655 0x1CBB23F Base64 standard index table
30669805 0x1D3FBED Unix path: /sys/class/net/%s/phy80211
31061945 0x1D9F7B9 Executable script, shebang: "/bin/bash"
32155706 0x1EAA83A SHA256 hash constants, little endian
33333893 0x1FCA285 gzip compressed data, maximum compression, has header CRC, last modified: 1974-10-07 02:33:45 (bogus date)
33789523 0x2039653 Certificate in DER format (x509 v3), header length: 4, sequence length: 7035
34782767 0x212BE2F PGP RSA encrypted session key - keyid: 16440001 299384E4 RSA (Encrypt or Sign) 1024b
35624713 0x21F9709 HTML document header
35813917 0x2227A1D Base64 standard index table
37477142 0x23BDB16 PNG image, 32 x 24, 8-bit/color RGBA, interlaced
37477218 0x23BDB62 Zlib compressed data, default compression
37505831 0x23C4B27 GIF image data, version "89a", 5 x
37562652 0x23D291C JPEG image data, EXIF standard
37565366 0x23D33B6 XML document, version: "1.0"
37578501 0x23D6705 Zlib compressed data, best compression
37583398 0x23D7A26 JPEG image data, JFIF standard 1.02, thumbnail 8x33
37688341 0x23F1415 Zlib compressed data, default compression
37692167 0x23F2307 XML document, version: "1.0"
37750923 0x240088B Zlib compressed data, best compression
37756477 0x2401E3D Zlib compressed data, best compression
37767404 0x24048EC JPEG image data, JFIF standard 1.02
37822653 0x24120BD Zlib compressed data, best compression
37831726 0x241442E XML document, version: "1.0"
37916959 0x242911F XML document, version: "1.0"
37933520 0x242D1D0 GIF image data, version "89a", 16 x 16
37935116 0x242D80C JPEG image data, JFIF standard 1.01
37988275 0x243A7B3 Zlib compressed data, default compression
38162968 0x2465218 XML document, version: "1.0"
38198982 0x246DEC6 PNG image, 260 x 362, 8-bit/color RGBA, non-interlaced
38319035 0x248B3BB Zlib compressed data, best compression
38322374 0x248C0C6 Zlib compressed data, best compression
38387343 0x249BE8F JPEG image data, JFIF standard 1.01
38387373 0x249BEAD TIFF image data, little-endian offset of first image directory: 8
38443154 0x24A9892 PNG image, 282 x 384, 8-bit
38561022 0x24C64FE ZBOOT firmware header, header size: 32 bytes, load address: 0x9C54505A, start address: 0x8B844857, checksum: 0x4F8B885F, version: 0xFF979388, image size: 991901497 bytes
38654882 0x24DD3A2 PNG image, 300 x 84, 8-bit/color RGBA, non-interlaced
38863643 0x251031B XML document, version: "1.0"
38873006 0x25127AE PNG image, 292 x 400, 8-bit/color RGBA, non-interlaced
38927380 0x251FC14 Zlib compressed data, best compression
38977369 0x252BF59 XML document, version: "1.0"
39352812 0x25879EC JPEG image data, JFIF standard 1.01
39376497 0x258D671 TIFF image data, big-endian, offset of first image directory: 8
39492503 0x25A9B97 JPEG image data, JFIF standard 1.01
39746512 0x25E7BD0 Base64 standard index table
40074800 0x2637E30 AES S-Box
40075056 0x2637F30 AES Inverse S-Box
40145110 0x26490D6 HTML document header
40230112 0x265DCE0 Base64 standard index table
41733092 0x27CCBE4 Certificate in DER format (x509 v3), header length: 4, sequence length: 873
使用dd命令提取出文件从 LZ4 compressed data, legacy开始
dd if=v3910_3972.all of=fs.lz4 bs=1 skip=15613000 count=$((48978480-15613000))
使用dd后利用grep搜索关键词update、upgrade、firmware 等字符。刚开始是v3910_3912.all虽然找到了./etc/runcommand/fw_upload,但是里面并没有解密过程,又换成v3910_3972.all发现了fw_upacker。
找到./etc/runcommand/fw_upload其中包含了完整的固件升级流程。
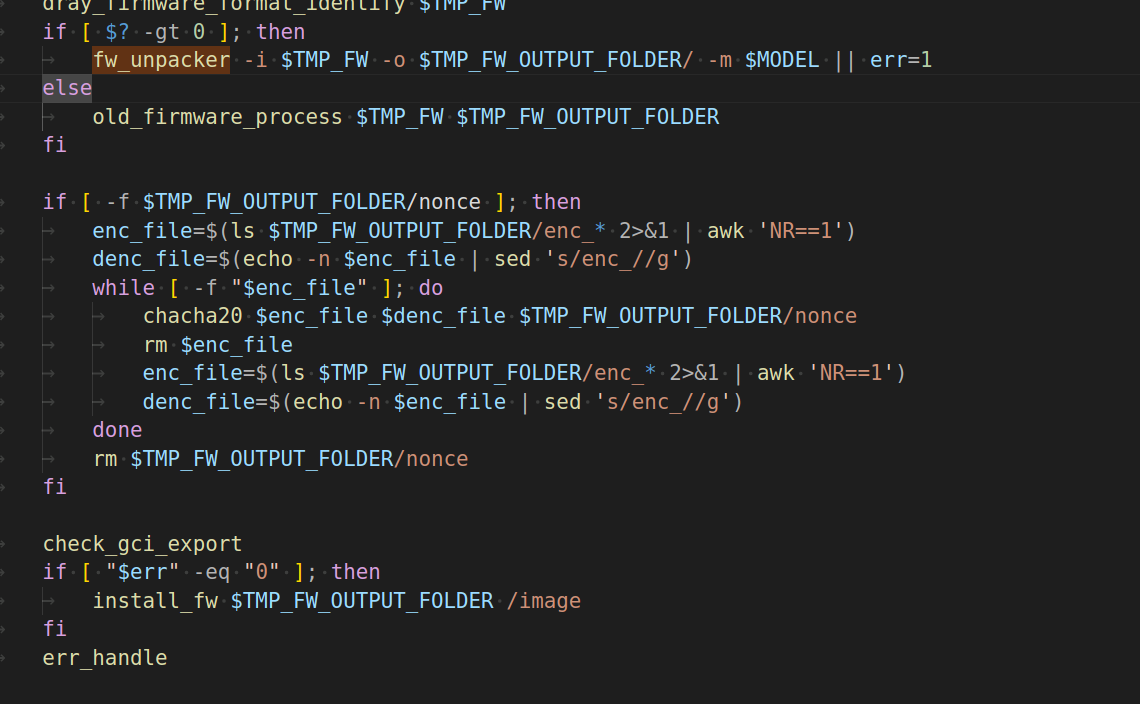
首先用fw_upacker解包一下,主要有三个参数,ai分析一下第一个是要解包的文件,第二个是解包后存放位置,第三个不知道,先随便测试一下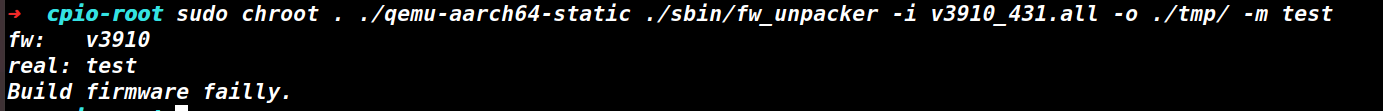
推测是固件版本v3910
下面就是用chacha20解密
while [ -f "$enc_file" ]; do chacha20 $enc_file $denc_file $TMP_FW_OUTPUT_FOLDER/nonce rm $enc_file enc_file=$(ls $TMP_FW_OUTPUT_FOLDER/enc_* 2>&1 | awk 'NR==1') denc_file=$(echo -n $enc_file | sed 's/enc_//g') done
主要是chacha20 $enc_file $denc_file $TMP_FW_OUTPUT_FOLDER/nonce 需要三个文件按照这种格式执行一下(chacha20加解密搜了一下是一种流密码,在解密时需要key也需要nonce,但是按照他这种格式没有发现要key,分析程分析时发现下面这个字符串,猜测是因为密钥是硬编码存储在chacha20可执行程序内部)
key为0DraytekKd5Eason3DraytekKd5Eason
下面就是解密一下
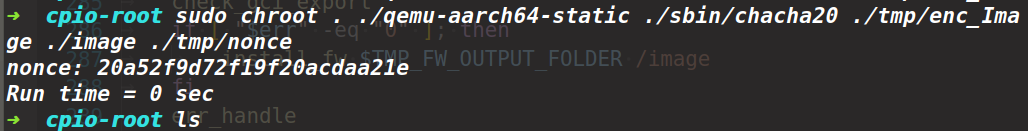
仿真启动
下面就是看一下启动文件,首先启动rc
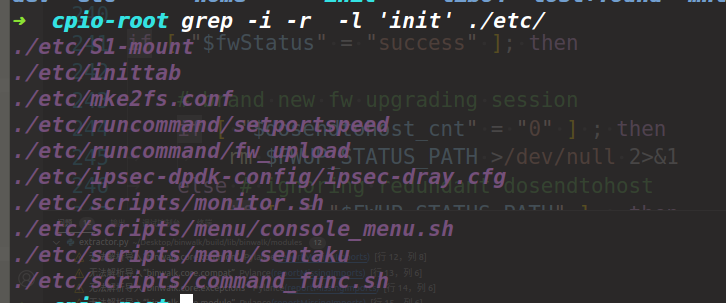
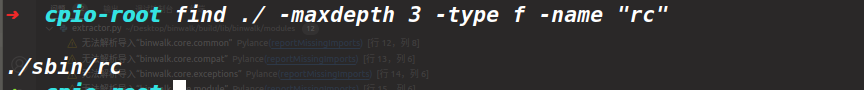
其实到这一步其实我已经不知道要怎么做了,后面完全是参考文章了主要还是很少去完整的思考一个仿真过程,对于其中的配置文件有哪些是需要关注的地方这一问题一直是一知半解的状态。
看别人的思路首先是找有哪些是在在后台运行的文件,用ai分析一下有下面几个文件。
/sbin/tcp_socket_server &
/sbin/update_ps &
/etc/runcommand/setportspeed all 0x000000000000 2>&1 >/dev/null &
/firmware/run.sh &
/firmware/recvCmd >> $recvLog 2>&1 &
nice -n 19 /sbin/dbglog_daemon.sh &
/sbin/set_linux_ip.sh
看一下run.py,意思就是当前环境是否处于纯linux环境,如果是就执行run_linux.sh(简单搜一下纯linux就是设备运行在标准 Linux 操作系统环境下,不使用 DPDK(通常用于高性能网络数据平面)不是很理解是什么意思。)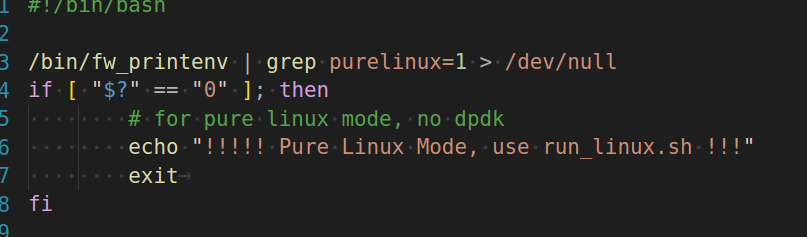
很明显是要运行run_linux.sh,下面就是看一下run_linux.sh
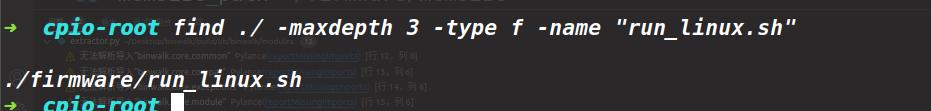
看一下前面的注释,看样子我们需要关注fw_setenv purelinux和setup_qemu_linux.sh
分析后者setup_qemu_linux.sh发现只要用来设置网络。用到了两张网卡,分别是eth0和eth1。先将网卡创建出来
sudo ip tuntap add dev eth0 mode tap
sudo ip tuntap add dev eth1 mode tap
sudo ip link set eth0 up
sudo ip link set eth1 up
下面就是启动环境
修改一下setup_qemu_linux.sh和run_linux.sh然后以此运行就可以启动服务了。
(刚开始我还想着用qemu-system-aarch64在chroot中启动,但是后来一看run_linux.sh就是启动脚本,这里的qemu-system-aarch64需要用他提供的源码编译一下地址:DrayTek File Server)
#!/bin/bash iflan=eth0 ifwan=eth1 mylanip="192.168.1.2" #reset switch to clear vlan settings in 3910 board # if [ -f /sbin/sw_setup ]; thenethtoolethtool # sw_setup hw_reset; sw_setup sw_reset # fi brctl delbr br-lan brctl delbr br-wan ip link add br-lan type bridge ip tuntap add qemu-lan mode tap brctl addif br-lan $iflan brctl addif br-lan qemu-lan ip addr flush dev $iflan ifconfig br-lan $mylanip ifconfig br-lan up ifconfig qemu-lan up ifconfig $iflan up ip link add br-wan type bridge ip tuntap add qemu-wan mode tap brctl addif br-wan $ifwan brctl addif br-wan qemu-wan ip addr flush dev $ifwan ifconfig br-lan $mylanip ifconfig br-wan up ifconfig qemu-wan up ifconfig $ifwan up brctl show #for speed test ethtool -K $iflan gro off ethtool -K $iflan gso off ethtool -K $ifwan gro off ethtool -K $ifwan gso off ethtool -K qemu-lan gro off ethtool -K qemu-lan gso off ethtool -K qemu-wan gro off ethtool -K qemu-wan gso off #for telnet from linux to drayos 192.168.1.1 ethtool -K br-lan tx off
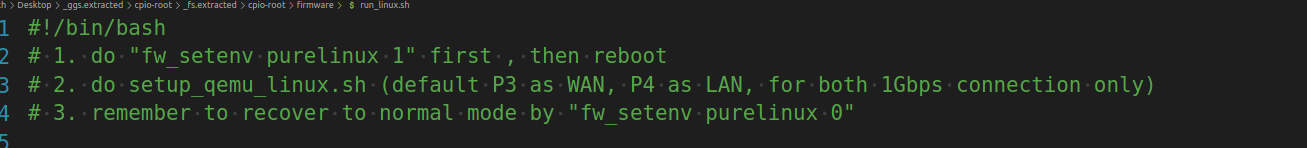
#!/bin/bash # 1. do "fw_setenv purelinux 1" first , then reboot # 2. do setup_qemu_linux.sh (default P3 as WAN, P4 as LAN, for both 1Gbps connection only) # 3. remember to recover to normal mode by "fw_setenv purelinux 0" rangen() { printf "%02x" `shuf -i 1-255 -n 1` } rangen1() { printf "%x" `shuf -i 1-15 -n 1` } wan_mac(){ idx=$1 printf "%02x\n" $((0x${C}+0x$idx)) | tail -c 3 # 3 = 2 digit + 1 terminating character } A=$(rangen); B=$(rangen); C=$(rangen); LAN_MAC="00:1d:aa:${A}:${B}:${C}" if [ ! -p serial0 ]; then mkfifo serial0 fi if [ ! -p serial1 ]; then mkfifo serial1 fi platform_path="./platform" echo "x86" > $platform_path enable_kvm_path="./enable_kvm" echo "kvm" > $enable_kvm_path cfg_path="./magic_file" echo "GCI_SKIP" > gci_magic mkdir -p ../data/uffs touch ../data/uffs/v3910_ram_flash.bin uffs_flash="../data/uffs/v3910_ram_flash.bin" echo "1" > memsize (sleep 20 && ethtool -K qemu-lan tx off) & model="./model" echo "3" > ./model rm -rf ./app && mkdir -p ./app/gci GCI_PATH="./app/gci" GCI_FAIL="./app/gci_exp_fail" GDEF_FILE="$GCI_PATH/draycfg.def" GEXP_FLAG="$GCI_PATH/EXP_FLAG" GEXP_FILE="$GCI_PATH/draycfg.exp" GDEF_FILE_ADDR="0x4de0000" GEXP_FLAG_ADDR="0x55e0000" GEXP_FILE_ADDR="0x55e0010" echo "0#" > $GEXP_FLAG echo "19831026" > $GEXP_FILE echo "GCI_SKIP" > $GDEF_FILE SHM_SIZE=16777216 ./qemu-system-aarch64 -M virt,gic_version=3 -cpu cortex-a57 -m 1024 -L ../usr/share/qemu \ -s\ -kernel ./vqemu/sohod64.bin $serial_option -dtb DrayTek \ -nographic $gdb_serial_option $gdb_remote_option \ -device virtio-net-pci,netdev=network-lan,mac=${LAN_MAC} \ -netdev tap,id=network-lan,ifname=qemu-lan,script=no,downscript=no \ -device virtio-net-pci,netdev=network-wan,mac=00:1d:aa:${A}:${B}:$(wan_mac 1) \ -netdev tap,id=network-wan,ifname=qemu-wan,script=no,downscript=no \ -device virtio-serial-pci -chardev pipe,id=ch0,path=serial0 \ -device virtserialport,chardev=ch0,name=serial0 \ -device loader,file=$platform_path,addr=0x25fff0 \ -device loader,file=$cfg_path,addr=0x260000 \ -device loader,file=$uffs_flash,addr=0x00be0000 \ -device loader,file=$enable_kvm_path,addr=0x25ffe0 \ -device loader,file=memsize,addr=0x25ff67 \ -device loader,file=$model,addr=0x25ff69 \ -device loader,file=$GDEF_FILE,addr=$GDEF_FILE_ADDR \ -device loader,file=$GEXP_FLAG,addr=$GEXP_FLAG_ADDR \ -device loader,file=$GEXP_FILE,addr=$GEXP_FILE_ADDR \ -device nec-usb-xhci,id=usb \ -device ivshmem-plain,memdev=hostmem \ -object memory-backend-file,size=${SHM_SIZE},share,mem-path=/dev/shm/ivshmem,id=hostmem
ida分析./vqemu/sohod64.bin文件,搜索字符串QUERY_STRING的方式对其定位。漏洞即使没有限制index,只要有足够多的&就可以不断地向栈中输入堆地址最终覆盖返回地址导致程序崩溃。
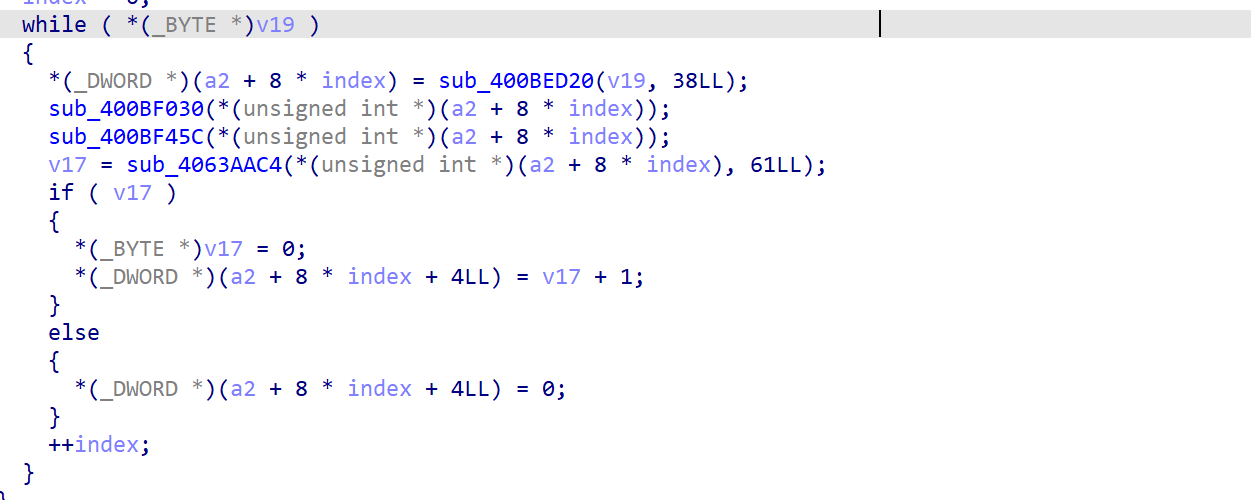
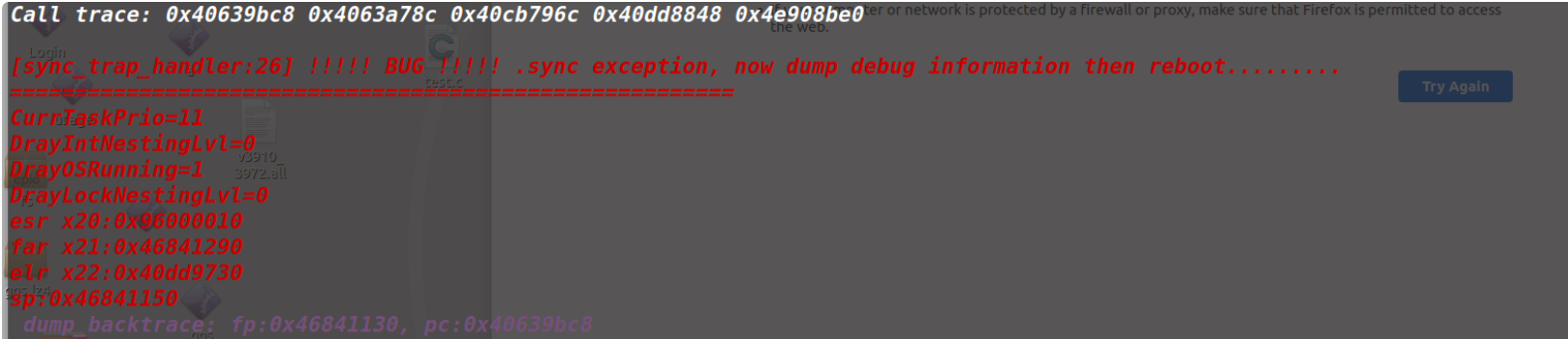
测试


 浙公网安备 33010602011771号
浙公网安备 33010602011771号