HUE认证方式
HUE是一个支持数据库和数据仓库的开源SQL编辑器,官网
https://gethue.com/
HUE由python+django开发,其登录界面如下

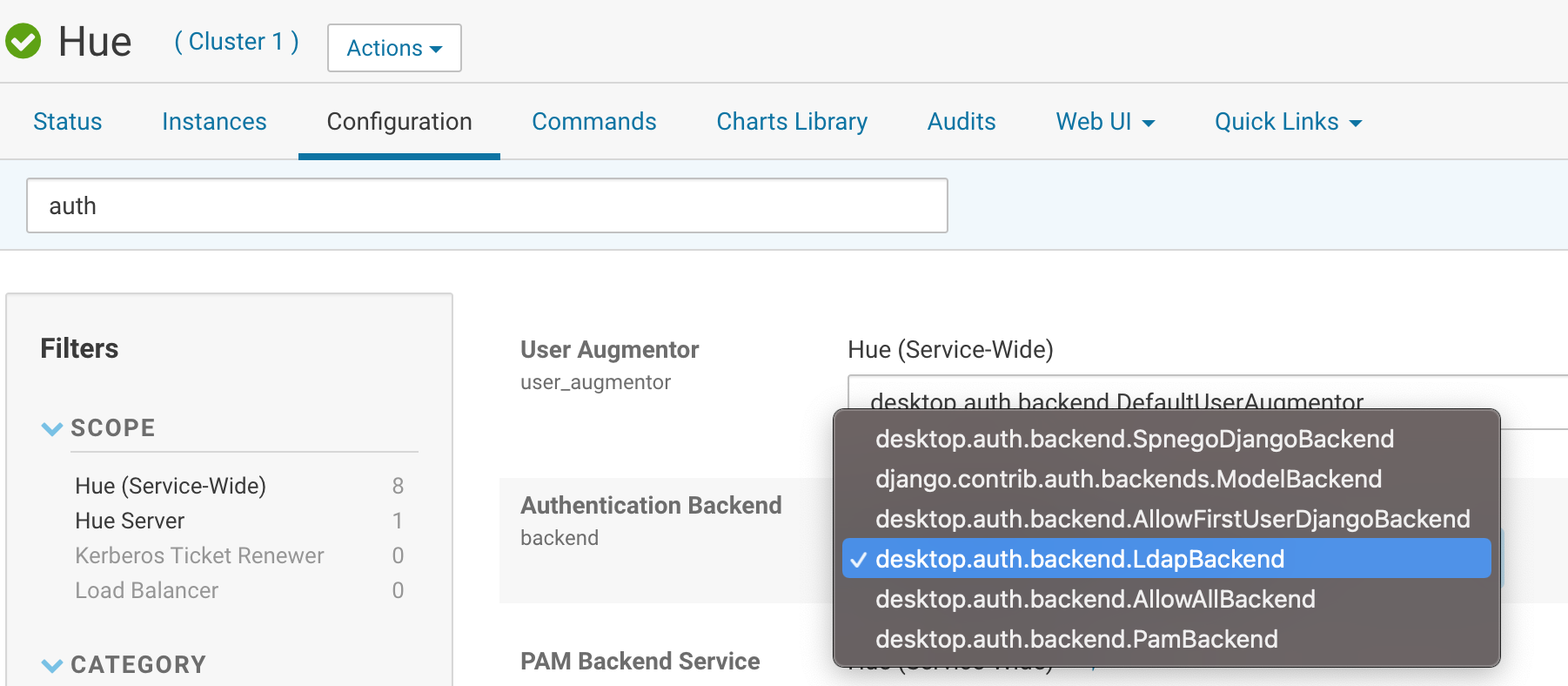
HUE官方支持多个认证方式,比如 django.contrib.auth.backends.ModelBackend,desktop.auth.backend.LdapBackend等,详见如下表格
| HUE支持的认证方式(也可以同时配置多个认证方式,配置文件中用逗号分隔) | 备注 |
| django.contrib.auth.backends.ModelBackend | 完整的Django后端认证 |
| desktop.auth.backend.AllowAllBackend | 没有认证,允许所有人 |
| desktop.auth.backend.AllowFirstUserDjangoBackend | 第一次登录的时候,会要求你创建用户 |
| desktop.auth.backend.LdapBackend | 连接LDAP服务器进行认证 |
| desktop.auth.backend.PamBackend | 使用PAM(Pluggable Authentication Modules)即可插拔式认证模块进行认证 |
| desktop.auth.backend.SpnegoDjangoBackend | Spnego模式是一种由微软提出的使用GSS-API接口的认证模式,它扩展了Kerberos协议 |
| desktop.auth.backend.RemoteUserDjangoBackend | Django支持使用远程用户方式进行认证 |
| libsaml.backend.SAML2Backend | SAML认证方式,一般用于支持SSO单点登录 |
| libopenid.backend.OpenIDBackend | OpenID认证方式,比如可以使用keycloak这个开源openid方案 |
| liboauth.backend.OAuthBackend | 新的认证方式,支持 Twitter, Facebook, Google+ 和 Linkedin |
各HUE版本支持的认证方式可以去源码里面进行查询,HUE认证的代码如下
https://github.com/cloudera/hue/blob/master/desktop/core/src/desktop/auth/backend.py
比如CDH5.16.2版本中的HUE3.9.0,只支持如下几种backend
https://github.com/cloudera/hue/blob/cdh5.16.2-release/desktop/core/src/desktop/auth/backend.py
如果要支持SAML认证,即libsaml.backend.SAML2Backend,则需要额外安装依赖
https://docs.cloudera.com/documentation/enterprise/6/6.3/topics/hue_sec_saml_auth.html
以及
https://gist.github.com/jbenninghoff/75a02c446f630dfb16886c9a5491fc4e#file-emr-hue-saml-conf-md
如果是HUE4.9.0,则除了上面的backend之外,还增加了KnoxSpnegoDjangoBackend和OIDCBackend
https://github.com/cloudera/hue/blob/branch-4.9.0/desktop/core/src/desktop/auth/backend.py
如果要支持openid认证,除了需要在hue.ini配置文件中将backend改成libopenid.backend.OpenIDBackend之外,还需要配置oidc相关的配置,如下
# The client ID as relay party set in OpenID provider oidc_rp_client_id=xxx # The client secret as relay party set in OpenID provider oidc_rp_client_secret=xx-xx-xx-xx-xx # The OpenID provider authoriation endpoint oidc_op_authorization_endpoint=https://keycloak.xxx.com/auth/realms/master/protocol/openid-connect/auth # The OpenID provider token endpoint oidc_op_token_endpoint=https://keycloak.xxx.com/auth/realms/master/protocol/openid-connect/token # The OpenID provider user info endpoint oidc_op_user_endpoint=https://keycloak.xxx.com/auth/realms/master/protocol/openid-connect/userinfo # The OpenID provider signing key in PEM or DER format ## oidc_rp_idp_sign_key=/path/to/key_file # The OpenID provider authoriation endpoint oidc_op_jwks_endpoint=https://keycloak.xxx.com/auth/realms/master/protocol/openid-connect/certs # Whether Hue as OpenID Connect client verify SSL cert oidc_verify_ssl=false # As relay party Hue URL path to redirect to after login login_redirect_url=http://xxx:8888/oidc/callback/ # The OpenID provider URL path to redirect to after logout logout_redirect_url=https://keycloak.xxx.com/auth/realms/master/protocol/openid-connect/logout # As relay party Hue URL path to redirect to after login login_redirect_url_failure=http://xxx:8888/hue/oidc_failed/ # Create a new user from OpenID Connect on login if it doesn't exist create_users_on_login=true # When creating a new user, which 'claims' attribute from the OIDC provider to be used for creating the username. # Default to 'preferred_username'. Possible values include: 'email' oidc_username_attribute=preferred_username
oidc_username_attribute配置除了preferred_username之外,还有email,name等其他选项,可以参考
https://openid.net/specs/openid-connect-core-1_0.html
注意oidc_username_attribute选择preferred_username,如果遇到以下报错
Caused by: org.apache.hadoop.security.authentication.util.KerberosName$NoMatchingRule: No rules applied to xxx@xxx.com
需要在core-site.xml中修改hadoop.security.auth_to_local配置,参考:大数据Kerberos认证报No rules applied to 以及
https://docs.cloudera.com/documentation/enterprise/6/6.3/topics/cdh_sg_kerbprin_to_sn.html
如果在HUE4.9.0版本中使用了OIDC认证,同时想对HUE用户默认添加组,即使用useradmin下面的default_user_group这个配置,是无法生效的,因为在HUE4.9.0源码中缺号了添加默认组的逻辑,而在最新的master分支上是有的,如下
如果想使用该配置,在python源码中添加上即可

本文只发表于博客园和tonglin0325的博客,作者:tonglin0325,转载请注明原文链接:https://www.cnblogs.com/tonglin0325/p/5743487.html




 浙公网安备 33010602011771号
浙公网安备 33010602011771号