kubernetes单Master集群部署--Node节点部署组件(6)
1、kubelet组件授权
Master apiserver启用TLS认证后,Node节点kubelet组件想要加入集群,必须使用CA签发的有效证书才能与apiserver通信,当Node节点很多时,签署证书是一件很繁琐的事情,因此有了TLS Bootstrapping机制,kubelet会以一个低权限用户自动向apiserver申请证书,kubelet的证书由apiserver动态签署。
认证大致工作流程如图所示:

以下操作在k8s的master01上执行:
将kubelet-bootstrap用户绑定到系统集群角色
kubectl create clusterrolebinding kubelet-bootstrap \
--clusterrole=system:node-bootstrapper \
--user=kubelet-bootstrap
创建kubeconfig文件
在生成kubernetes证书的目录下执行以下命令生成kubeconfig文件:
# 创建kubelet bootstrapping kubeconfig
BOOTSTRAP_TOKEN=674c457d4dcf2eefe4920d7dbb6b0ddc
KUBE_APISERVER="https://10.11.97.191:6443"
#设置集群参数
kubectl config set-cluster kubernetes \
--certificate-authority=./ca.pem \
--embed-certs=true \
--server=${KUBE_APISERVER} \
--kubeconfig=bootstrap.kubeconfig
#设置客户端认证参数
kubectl config set-credentials kubelet-bootstrap \
--token=${BOOTSTRAP_TOKEN} \
--kubeconfig=bootstrap.kubeconfig
#设置上下文参数
kubectl config set-context default \
--cluster=kubernetes \
--user=kubelet-bootstrap \
--kubeconfig=bootstrap.kubeconfig
#设置默认上下文
kubectl config use-context default --kubeconfig=bootstrap.kubeconfig
#创建kube-proxy kubeconfig文件
kubectl config set-cluster kubernetes \
--certificate-authority=./ca.pem \
--embed-certs=true \
--server=${KUBE_APISERVER} \
--kubeconfig=kube-proxy.kubeconfig
kubectl config set-credentials kube-proxy \
--client-certificate=./kube-proxy.pem \
--client-key=./kube-proxy-key.pem \
--embed-certs=true \
--kubeconfig=kube-proxy.kubeconfig
kubectl config set-context default \
--cluster=kubernetes \
--user=kube-proxy \
--kubeconfig=kube-proxy.kubeconfig
kubectl config use-context default --kubeconfig=kube-proxy.kubeconfig
# ls
bootstrap.kubeconfig kube-proxy.kubeconfig
cat bootstrap.kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR2akNDQXFhZ0F3SUJBZ0lVQlFDRzk5aU5rK1VTMlFnOVUzc3g5Z0I4b3Vjd0RRWUpLb1pJaHZjTkFRRUwKQlFBd1pURUxNQWtHQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFXcHBibWN4RURBT0JnTlZCQWNUQjBKbAphV3BwYm1jeEREQUtCZ05WQkFvVEEyczRjekVQTUEwR0ExVUVDeE1HVTNsemRHVnRNUk13RVFZRFZRUURFd3ByCmRXSmxjbTVsZEdWek1CNFhEVEU1TURjeU5USXpNemt3TUZvWERUSTBNRGN5TXpJek16a3dNRm93WlRFTE1Ba0cKQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFXcHBibWN4RURBT0JnTlZCQWNUQjBKbGFXcHBibWN4RERBSwpCZ05WQkFvVEEyczRjekVQTUEwR0ExVUVDeE1HVTNsemRHVnRNUk13RVFZRFZRUURFd3ByZFdKbGNtNWxkR1Z6Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBOWRnTXo2d2JNMUtGQUdwS09HelAKZDRRdGdxWHFEUlQ4V0hMdGdwdzdxT0pDK0lzeXBDbXBTS0ZKZk5tZWVvcXJUV2hIZk1lR3hLVjRFTk90OTlHMQpmeThISldvSTVJZ000QkVNdjh5dlZzZ08rNzZiS1RoYnpaODFINUNyQjVjSFd1aDhXRGR3Nk5Jc1Q2L2FVWDVLCldLcXE0ZGNhb05FenFqVngxNkdPb1lma0hueTh2R2dZSVBBZ0VFME5CQzQ4VEMrTTI3eXg2cTJPOW5BY2wwcHQKaGdTaEZjeGo5aTFER3lhVVBDakhDMW5EUEtDNklpK1pGand6djEwOFBBaDJxcWlRR21mNFBTTTBDT283eXZrVgpXV3NlKzV2NGtoN3AvVmJIQWpkb0FIKzg4S1FQV0FYOHVnbGd5Zm5HTGJIRDloM0ZiQU9tb0xVdmlrYUsyRWowCnV3SURBUUFCbzJZd1pEQU9CZ05WSFE4QkFmOEVCQU1DQVFZd0VnWURWUjBUQVFIL0JBZ3dCZ0VCL3dJQkFqQWQKQmdOVkhRNEVGZ1FVR0I1dC9PY0pYM3lIR3dvNWtjRGpMN0p1eWhFd0h3WURWUjBqQkJnd0ZvQVVHQjV0L09jSgpYM3lIR3dvNWtjRGpMN0p1eWhFd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFKOHRldlRzMDQ2TXhwbUY5ZGQ2CmZwbnJENUJIaDZjdVdjK0FHV3ZDa05yc3l3Z3lRQTVRTzdheFhvR05xeVJjN2tvMGMzbE5HeHVTN2RpTVBOczUKTjBGd0RrZS9PTGwxendCYUR2MDZjOEgyZ2dKMi9pMWFNSytPYUFGNDIvbG9EUmVGTk9nSlRIOU9vcDlBVi9RWgpvOFpHVjJYcXdTZENMdEl1bVpodEVkKzJTQ0tKOCtsQ1lVYkxXaE5xd0prdXhvWGRjU3MxYUp1RVB5TXJ5TG5KCnVpNFp3M1R1WGsraFFqQTI1NkliNEFHMmZiWVdHclpwNmIyUU0za3JqaEVxYVBqLzBRMHZ6d2ZaQlk1S0RKNXEKNEpoM0pXTVN2Rk1RZXRHY09iSEN3dGEwamFaVTNuMmFBWGtRLzRPRnZ6VE5MVXdhSVJPNDZNRktldDhlcUhTbApRK1U9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
server: https://10.11.97.191:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubelet-bootstrap
name: default
current-context: default
kind: Config
preferences: {}
users:
- name: kubelet-bootstrap
user:
token: 0fb61c46f8991b718eb38d27b605b008
其中的server为apiserver地址,在default命名空间中生成了一个kuberlet-bootstrap用户
cat kube-proxy.kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR2akNDQXFhZ0F3SUJBZ0lVQlFDRzk5aU5rK1VTMlFnOVUzc3g5Z0I4b3Vjd0RRWUpLb1pJaHZjTkFRRUwKQlFBd1pURUxNQWtHQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFXcHBibWN4RURBT0JnTlZCQWNUQjBKbAphV3BwYm1jeEREQUtCZ05WQkFvVEEyczRjekVQTUEwR0ExVUVDeE1HVTNsemRHVnRNUk13RVFZRFZRUURFd3ByCmRXSmxjbTVsZEdWek1CNFhEVEU1TURjeU5USXpNemt3TUZvWERUSTBNRGN5TXpJek16a3dNRm93WlRFTE1Ba0cKQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFXcHBibWN4RURBT0JnTlZCQWNUQjBKbGFXcHBibWN4RERBSwpCZ05WQkFvVEEyczRjekVQTUEwR0ExVUVDeE1HVTNsemRHVnRNUk13RVFZRFZRUURFd3ByZFdKbGNtNWxkR1Z6Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBOWRnTXo2d2JNMUtGQUdwS09HelAKZDRRdGdxWHFEUlQ4V0hMdGdwdzdxT0pDK0lzeXBDbXBTS0ZKZk5tZWVvcXJUV2hIZk1lR3hLVjRFTk90OTlHMQpmeThISldvSTVJZ000QkVNdjh5dlZzZ08rNzZiS1RoYnpaODFINUNyQjVjSFd1aDhXRGR3Nk5Jc1Q2L2FVWDVLCldLcXE0ZGNhb05FenFqVngxNkdPb1lma0hueTh2R2dZSVBBZ0VFME5CQzQ4VEMrTTI3eXg2cTJPOW5BY2wwcHQKaGdTaEZjeGo5aTFER3lhVVBDakhDMW5EUEtDNklpK1pGand6djEwOFBBaDJxcWlRR21mNFBTTTBDT283eXZrVgpXV3NlKzV2NGtoN3AvVmJIQWpkb0FIKzg4S1FQV0FYOHVnbGd5Zm5HTGJIRDloM0ZiQU9tb0xVdmlrYUsyRWowCnV3SURBUUFCbzJZd1pEQU9CZ05WSFE4QkFmOEVCQU1DQVFZd0VnWURWUjBUQVFIL0JBZ3dCZ0VCL3dJQkFqQWQKQmdOVkhRNEVGZ1FVR0I1dC9PY0pYM3lIR3dvNWtjRGpMN0p1eWhFd0h3WURWUjBqQkJnd0ZvQVVHQjV0L09jSgpYM3lIR3dvNWtjRGpMN0p1eWhFd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFKOHRldlRzMDQ2TXhwbUY5ZGQ2CmZwbnJENUJIaDZjdVdjK0FHV3ZDa05yc3l3Z3lRQTVRTzdheFhvR05xeVJjN2tvMGMzbE5HeHVTN2RpTVBOczUKTjBGd0RrZS9PTGwxendCYUR2MDZjOEgyZ2dKMi9pMWFNSytPYUFGNDIvbG9EUmVGTk9nSlRIOU9vcDlBVi9RWgpvOFpHVjJYcXdTZENMdEl1bVpodEVkKzJTQ0tKOCtsQ1lVYkxXaE5xd0prdXhvWGRjU3MxYUp1RVB5TXJ5TG5KCnVpNFp3M1R1WGsraFFqQTI1NkliNEFHMmZiWVdHclpwNmIyUU0za3JqaEVxYVBqLzBRMHZ6d2ZaQlk1S0RKNXEKNEpoM0pXTVN2Rk1RZXRHY09iSEN3dGEwamFaVTNuMmFBWGtRLzRPRnZ6VE5MVXdhSVJPNDZNRktldDhlcUhTbApRK1U9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
server: https://10.11.97.191:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kube-proxy
name: default
current-context: default
kind: Config
preferences: {}
users:
- name: kube-proxy
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUQzakNDQXNhZ0F3SUJBZ0lVTC9HSGFlOHYyR0Y1SjRiZ0hIMklZc1FoNzEwd0RRWUpLb1pJaHZjTkFRRUwKQlFBd1pURUxNQWtHQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFXcHBibWN4RURBT0JnTlZCQWNUQjBKbAphV3BwYm1jeEREQUtCZ05WQkFvVEEyczRjekVQTUEwR0ExVUVDeE1HVTNsemRHVnRNUk13RVFZRFZRUURFd3ByCmRXSmxjbTVsZEdWek1CNFhEVEU1TURjeU5USXpNemt3TUZvWERUSTVNRGN5TWpJek16a3dNRm93YkRFTE1Ba0cKQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFVcHBibWN4RURBT0JnTlZCQWNUQjBKbGFVcHBibWN4RERBSwpCZ05WQkFvVEEyczRjekVQTUEwR0ExVUVDeE1HVTNsemRHVnRNUm93R0FZRFZRUURFeEZ6ZVhOMFpXMDZhM1ZpClpTMXdjbTk0ZVRDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTUFRVmVQYlB2dUQKaVRvZGxJYmlRamZxYzdsNlFJUE8zdDlEMG9FWFptcDlYVUtiaWg4U2kxOHZVR096aGVZZXFOWS9NNTdjeHVaRwpraVJtL053Q2ZBTFc0N0hZbHlCOFRWOFhyUWFuc3NBank5OVpjaGhoU3d3QkpydWhOLzBPRE5xeXplWGppL0dpCmUvSUgxRDFGSkY4Y2wwNGQyUzVBWWord1JNaGw0clMwbnZqaHNLVFc5M04wNTF1YXZidEltU2hWcVZpQmJiUTUKbGFmdEF0WTdRamQybEs0T29iSEdVeWFTVkNPNHFjVjk5WHp5cktwZUhlMHZRclUrQ3czbkplcEt0dy9JVWJtdgp1djBRSUF6NEJ4eFQwd0JYNGlJbWhoY1ZnQSttWnI0OEhvUVpjdjNvRlBUQ2VTWE9xcmV3dkl0eWszc013a09DClN0T0F0M0s5NGhNQ0F3RUFBYU4vTUgwd0RnWURWUjBQQVFIL0JBUURBZ1dnTUIwR0ExVWRKUVFXTUJRR0NDc0cKQVFVRkJ3TUJCZ2dyQmdFRkJRY0RBakFNQmdOVkhSTUJBZjhFQWpBQU1CMEdBMVVkRGdRV0JCUTZqbWdiKzJwWQp2TjJwa0dsVEtSYUFwT3NMVGpBZkJnTlZIU01FR0RBV2dCUVlIbTM4NXdsZmZJY2JDam1Sd09NdnNtN0tFVEFOCkJna3Foa2lHOXcwQkFRc0ZBQU9DQVFFQTg1UkNiQWNTNGZHdklUcUtlb0txMHdyc041aHBmZkhKWjBrcGVzdWIKUFhRd2IvdUJPQWFoaWltdXhWNFFWK3N2c3FrU3RzTEZId0M0NzlHbklZS3B5NnprRExpZWJqQUF3UHpRaE9kVwpoTkNuK041aXY0aXhpQkdxK3NCV0pnRC8yamRIczVlK2Q2TXZqZTRGeG8wYnBXYm1GTTE3dkdaS1F3aFNvUG54Cko0ci9hNHFrbmJBaUw4VDFKZGhaT2FVR1QxanFudnl6S2Fadk8vbXVNTDRLUkpVTyt4Vzk4ejJvSHZZQzVOYzkKd1ZCTzYzaVFMY0lZaWpBNzVPNzVTcFk4N3gyVmxyZ3htdEdrcmVLMlNRQUYrVXQ3K050Qjd5ak5PYUlURjZXdApCME0zMVEzMzI2bnY0VklQYUppQXlDNHlyNFh1aG5UWWhzM2NacWdSVFZCU0dnPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBd0JCVjQ5cysrNE9KT2gyVWh1SkNOK3B6dVhwQWc4N2UzMFBTZ1JkbWFuMWRRcHVLCkh4S0xYeTlRWTdPRjVoNm8xajh6bnR6RzVrYVNKR2I4M0FKOEF0YmpzZGlYSUh4Tlh4ZXRCcWV5d0NQTDMxbHkKR0dGTERBRW11NkUzL1E0TTJyTE41ZU9MOGFKNzhnZlVQVVVrWHh5WFRoM1pMa0JpUDdCRXlHWGl0TFNlK09HdwpwTmIzYzNUblc1cTl1MGlaS0ZXcFdJRnR0RG1WcCswQzFqdENOM2FVcmc2aHNjWlRKcEpVSTdpcHhYMzFmUEtzCnFsNGQ3UzlDdFQ0TERlY2w2a3EzRDhoUnVhKzYvUkFnRFBnSEhGUFRBRmZpSWlhR0Z4V0FENlptdmp3ZWhCbHkKL2VnVTlNSjVKYzZxdDdDOGkzS1Rld3pDUTRKSzA0QzNjcjNpRXdJREFRQUJBb0lCQVFDUDh1NWM0N01WMFNVbAp3SXZVZUhvRzdKcWxsaUlLYUI4VW1RR0pyVjhlU3kxOXdaUEk3QjQzVGYvamFlYmViWFkvZFlrYjlQN0NFbnh2CitoeGtUUnhqQ0dvSm5uck9aenVhSE9XYXlrK253R3lKenNFNzBwZnJ2R1VxVlkvZ0F3clJVeGdNeC9uWU5kN04Kck41K3VYYWtMb3FjaXJSKy9OUm1SWmVYMXYwT1Q4OVdVWU5uamdlTlI2N1U3ay92VG12K05HZVYzOWlqdXUrSwpqVlhEdlVSekNiMGdHU3pERnRVM1BJc21Zc2ZMTXl2Tmt2d2FOem1leFJHR3cyb0VIYkw4RWgyREhYRTJTNVU5CmlYVlZQT09SaG1RdWRQR3ZoM2Rjcy9qRjlpaURkaXpnYU8vQlFNaWtxaE91R0JqeGNOTTM1N0JSa2ZwQnBwWGUKbElFWEpjUGhBb0dCQVBiVUF3QkVsamxDbXpZQlBBTzNMNWVaRmtJSjdHQUtEMXZWRi9IZE94QkZPNFRaZjd4TApEc2l0VmI0MXRUN0djSGxIQ1B4OW05dENuQlludWxVNUpZVHA4SitIUWZHWGE5czB5eU9QaytqTWRERnMxS3U5ClRqa3hCMVNGd2hVSzYzYkN1aFhwWVVMaHpuYzlVUWc1UEMwVGRuRTJZNVdDZm40VFV4NXh2ZVRqQW9HQkFNY3oKWHJhLzdKdVdmWVFIR0RpK1l6Yy9vOXVFMmM0aEpKTW9NK2VFY1hQVDBEL3J0U1FwSnRVeC9La1lFV2ZUM2h3UQpaTnNiM3V2UHAwdWR2cFErUnMvQ0J6OHZDR05nZ1lMKzFCbEN2YjM1YmlraHJpV1ZVeGpRNE1CdVBQMmtDbkhuClZpTkdWcW52ZFBKRzZOT0kxVkhqR0FBWHhtWUNCSVF1SnFyck5jVVJBb0dBWmhsYXlIQ1doMGNDOXZyWnZWdTQKQndoZkNhQWJNN3JWa1pINjNxUTVlMGg0RDBMOHNJR0hzd0RvTjg3MWt1cjR1V0hsMkxPSWxkRGV5ZGRUSDArTgpNb2FtYndhL0ExVTBXeTlpVytwWEwzUHJHRXJCU2V6N2YzTEZhblFOelRDQUo5YnlySCttS01sSTQwL3N4ZThPCjhrSmJ1d2JaZUkzTER4R2xUekdUY0NzQ2dZRUF0QUpZNmI1ZisyMnYrUnBNS2lMcUY2Z2IwNmluQmwzdTVraGoKTnlqNU9SbEV6QzZkWDVNTWM0WWJjMWE3aTk3cWpPUEhzRFRzYXA0WTZQMGdsbWY4cDR3SDduSDdHNHEvSG5oWApoSWhLWEoxRmprZlFUa2cxY214M1hZMkE4aGhHRkE1Z1Nib3JZSjl5UitvS1JmWVdCMHkzaUlYemxJVG9QZVpTCnJRdW1hSEVDZ1lFQW5xNFlxcGRIOEhPL2FCTGYyWEF6aG9IN2pncUFsNUsrVlZYK3hKQ2ZFdWowMFYyRWJxc0oKQjNtTEY0cDRXcU9YVHdiTjc1VDJaMkM3b0JvZUs2UFRESWVGQ2l5V3V5YTJ1TzJhRHZZbmN6WjVCL3JvVTNQZQozVUpoZGZkMFlSTkorZUlUUU1sSW1DU2djUUtxV2FoaWlQVFBJell1b0Z1VzJvSE9NbDNzRzYwPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
将这两个文件拷贝到Node节点/opt/kubernetes/cfg目录下。
2、部署kubelet组件
将前面下载的二进制包中的kubelet和kube-proxy拷贝到/opt/kubernetes/bin目录下。
创建kubelet配置文件:
# cat /opt/kubernetes/cfg/kubelet
KUBELET_OPTS="--logtostderr=true \ --v=4 \ --address=10.11.97.71 \ --hostname-override=10.11.97.71 \ --kubeconfig=/opt/kubernetes/cfg/kubelet.kubeconfig \ --experimental-bootstrap-kubeconfig=/opt/kubernetes/cfg/bootstrap.kubeconfig \ --config=/opt/kubernetes/cfg/kubelet.config \ --cert-dir=/opt/kubernetes/ssl \ --pod-infra-container-image=registry.cn-hangzhou.aliyuncs.com/google-containers/pause-amd64:3.0"
参数说明:
- --hostname-override 在集群中显示的主机名
- --kubeconfig 指定kubeconfig文件位置,会自动生成
- --bootstrap-kubeconfig 指定刚才生成的bootstrap.kubeconfig文件
- --cert-dir 颁发证书存放位置
- --pod-infra-container-image 管理Pod网络的镜像
其中/opt/kubernetes/cfg/kubelet.config配置文件如下:
kind: KubeletConfiguration
apiVersion: kubelet.config.k8s.io/v1beta1
address: 192.168.31.65
port: 10250
readOnlyPort: 10255
cgroupDriver: cgroupfs
clusterDNS: ["10.0.0.2"]
clusterDomain: cluster.local.
failSwapOn: false
authentication:
anonymous:
enabled: true
注意:
1、readOnlyPort给cAdvisor端口。
2、authentication下面添加匿名用户,执行kubelet logs pod时,会提示没有权限。
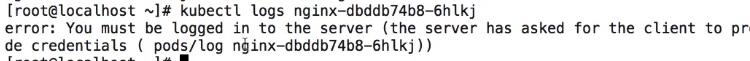
3、添加匿名用户后再次获取log
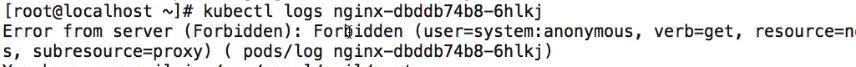
会发现还是没有权限,这时需要给匿名用户授权!!
kubectl create clusterrolebinding cluster-system-anonymous --clusterrole=cluster-admin --user=system:anonymous
给system:anonymous用户绑定到cluster-admin角色上,它具有系统管理员权限。
systemd管理kubelet组件
# cat /usr/lib/systemd/system/kubelet.service
[Unit] Description=Kubernetes Kubelet After=docker.service Requires=docker.service [Service] EnvironmentFile=/opt/kubernetes/cfg/kubelet ExecStart=/opt/kubernetes/bin/kubelet $KUBELET_OPTS Restart=on-failure KillMode=process [Install] WantedBy=multi-user.target
启动:
# systemctl daemon-reload
# systemctl enable kubelet
# systemctl restart kubelet
在Master审批Node加入集群:
启动后还没加入到集群中,需要手动允许该节点才可以。
在Master节点查看请求签名的Node:
# kubectl get csr
# kubectl certificate approve XXXXID
# kubectl get node
3、部署kube-proxy组件
创建kube-proxy配置文件:
# cat /opt/kubernetes/cfg/kube-proxy
KUBE_PROXY_OPTS="--logtostderr=true \ --v=4 \ --hostname-override=10.11.97.181 \ --cluster-cidr=10.0.0.0/24 \ --proxy-mode=ipvs \ --kubeconfig=/opt/kubernetes/cfg/kube-proxy.kubeconfig"
systemd管理kube-proxy组件:
# cat /usr/lib/systemd/system/kube-proxy.service
[Unit] Description=Kubernetes Proxy After=network.target [Service] EnvironmentFile=-/opt/kubernetes/cfg/kube-proxy ExecStart=/opt/kubernetes/bin/kube-proxy $KUBE_PROXY_OPTS Restart=on-failure [Install] WantedBy=multi-user.target
启动:
# systemctl daemon-reload
# systemctl enable kube-proxy
# systemctl restart kube-proxy
Node2部署方式一样。
4、查看集群状态
查看node
# kubectl get node
[root@k8s-master01 cfg]# kubectl get node NAME STATUS ROLES AGE VERSION 10.11.97.181 Ready <none> 20d v1.12.1 10.11.97.71 Ready <none> 20d v1.12.1
kubectl get cs
[root@k8s-master01 cfg]# kubectl get cs
NAME STATUS MESSAGE ERROR
scheduler Healthy ok
controller-manager Healthy ok
etcd-0 Healthy {"health":"true"}
etcd-1 Healthy {"health":"true"}
etcd-2 Healthy {"health":"true"}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号