OpenSSL测试-HMAC
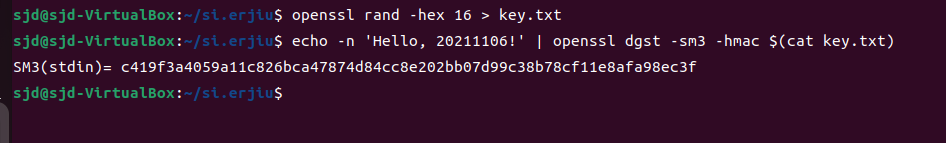
1 在openEuler(推荐)或Ubuntu中,使用OpenSSL命令行工具,对消息“Hello, 你的姓名学号!”使用HMAC-SM3进行验证。密钥为随机数,自己生成。提交命令行操作过程截图和结果。
2 使用C语言和OpenSSL库,在openEuler或Ubuntu上编写程序对字符串“Hello, 你的姓名学号!”进行HMAC-SM3加密。密钥同上。提交完整代码和程序运行结果截图以及两次结果的对比。
#include <openssl/evp.h>
#include <openssl/hmac.h>
#include <openssl/rand.h>
#include <string.h>
#include <stdio.h>
void handleErrors(void) {
fprintf(stderr, "Error occurred\n");
exit(1);
}
void generate_random_key(unsigned char *key, int key_len) {
if (RAND_bytes(key, key_len) != 1) {
handleErrors();
}
}
void hmac_sm3(const unsigned char *key, int key_len,
const unsigned char *data, int data_len,
unsigned char *digest, unsigned int *digest_len) {
HMAC_CTX *ctx;
if (!(ctx = HMAC_CTX_new())) {
handleErrors();
}
if (HMAC_Init_ex(ctx, key, key_len, EVP_sm3(), NULL) != 1) {
HMAC_CTX_free(ctx);
handleErrors();
}
if (HMAC_Update(ctx, data, data_len) != 1) {
HMAC_CTX_free(ctx);
handleErrors();
}
if (HMAC_Final(ctx, digest, digest_len) != 1) {
HMAC_CTX_free(ctx);
handleErrors();
}
HMAC_CTX_free(ctx);
}
int main(void) {
unsigned char key[16]; // Adjust the size of key if needed
unsigned char data[] = "Hello, 20211106!";
unsigned char digest[EVP_MAX_MD_SIZE];
unsigned int digest_len;
generate_random_key(key, sizeof(key));
printf("Generated Key: ");
for (int i = 0; i < sizeof(key); ++i) {
printf("%02x", key[i]);
}
printf("\n");
hmac_sm3(key, sizeof(key), data, sizeof(data) - 1, digest, &digest_len);
printf("HMAC-SM3 Digest: ");
for (unsigned int i = 0; i < digest_len; ++i) {
printf("%02x", digest[i]);
}
printf("\n");
return 0;
}
gcc -o sm3 sm3.c -lssl -lcrypto

3 使用龙脉智能钥匙完成2的内容,提交完整代码和程序运行结果截图以及两次结果的对比。
#include "generic.h"
#include <cstdio>
#include <iostream>
#include <string>
#include <vector>
using namespace std;
bool EncryptFile(const string &strSource,
const string &strDestination,
const string &strPassword);
//--------------------------------------------------------------------
// Begin main.
void main(void)
{
char szSrcFile[1024] = {0}; //sourcefile
char szTgtFile[1024] = {0}; //encryptfile
char szPassword[1024] = {0}; //password
printf("\nEncrypt a file.\n\nEnter the name of the file to be encrypt:\n");
scanf("%s", szSrcFile);
printf("Enter the name of the output file:\n");
scanf("%s", szTgtFile);
printf("Enter the password to encrypt the file:\n");
scanf("%s", szPassword);
if(EncryptFile(szSrcFile, szTgtFile, szPassword))
{
printf("Encrypt file successfully.\n");
}
else
{
printf("Encrypt file failed.\n");
}
}
//--------------------------------------------------------------------
// Code for the function EncryptFile called by main.
bool EncryptFile(const string &strSource,
const string &strDestination,
const string &strPassword)
{
//--------------------------------------------------------------------
// Declare and initialize local variables.
FILE *hSource = NULL;
FILE *hDestination = NULL;
HCRYPTPROV hCryptProv = NULL;
HCRYPTKEY hKey = NULL;
HCRYPTHASH hHash = NULL;
//--------------------------------------------------------------------
// Open source file.
BeginAction("Open source file for read");
if(NULL != (hSource = fopen(strSource.c_str(), "rb")))
{
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
//--------------------------------------------------------------------
// Open destination file.
BeginAction("Open target file for write");
if(NULL != (hDestination = fopen(strDestination.c_str(), "wb")))
{
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
// Get a CSP handle.
BeginAction("CryptAcquireContext()");
if(CryptAcquireContext(&hCryptProv,
TEST_CONTAINER,
CSP_NAME,
PROV_RSA_FULL,
0))
{
ActionSuccess();
}
else // Container does not exists, let us create a new one.
{
ActionFailed(GetLastError());
BeginAction("CryptAcquireContext() CRYPT_NEWKEYSET");
if(CryptAcquireContext(&hCryptProv,
TEST_CONTAINER,
CSP_NAME,
PROV_RSA_FULL,
CRYPT_NEWKEYSET))
{
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
}
HCRYPTPROV_Holder holder(hCryptProv);
BeginAction("CryptCreateHash()");
if(CryptCreateHash(hCryptProv, CALG_MD5, 0, 0, &hHash))
{
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
BeginAction("CryptHashData()");
if(CryptHashData(hHash,
(BYTE *) strPassword.c_str(),
strPassword.length(),
0))
{
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
BeginAction("CryptDeriveKey()");
if(CryptDeriveKey(hCryptProv, ENCRYPT_ALGORITHM, hHash, KEYLENGTH, &hKey))
{
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
BeginAction("CryptDestroyHash()");
if(CryptDestroyHash(hHash))
{
hHash = NULL;
ActionSuccess();
}
else
{
ActionFailed(GetLastError());
return FALSE;
}
DWORD dwBlockLen = 0;
DWORD dwBufferLen = 0;
DWORD dwCount = 0;
dwBlockLen = 1000 - 1000 % ENCRYPT_BLOCK_SIZE;
//--------------------------------------------------------------------
// Determine the block size. If a block cipher is used,
// it must have room for an extra block.
if(ENCRYPT_BLOCK_SIZE > 1)
{
dwBufferLen = dwBlockLen + ENCRYPT_BLOCK_SIZE;
}
else
{
dwBufferLen = dwBlockLen;
}
vector<BYTE> pbBuffer;
pbBuffer.resize(dwBufferLen);
//--------------------------------------------------------------------
// In a do loop, encrypt the source file and write to the source file.
do
{
//--------------------------------------------------------------------
// Read up to dwBlockLen bytes from the source file.
dwCount = fread(&pbBuffer[0], 1, dwBlockLen, hSource);
if(ferror(hSource))
{
ShowSysError("Read plain text", GetLastError());
return FALSE;
}
//--------------------------------------------------------------------
// Encrypt
if(!CryptEncrypt(hKey,
0,
feof(hSource), //file end
0,
&pbBuffer[0], // [in] sourcefile; [out] encryptdata
&dwCount, //encryptdatalength
dwBufferLen)) // encrypt data length
{
ShowSysError("CryptEncrypt()", GetLastError());
return FALSE;
}
//--------------------------------------------------------------------
// Write data to the destination file.
fwrite(&pbBuffer[0], 1, dwCount, hDestination);
if(ferror(hDestination))
{
ShowSysError("Write cipher text", GetLastError());
return FALSE;
}
}
while(!feof(hSource));
//--------------------------------------------------------------------
// End the do loop when the last block of the source file has been
// read, encrypted, and written to the destination file.
//--------------------------------------------------------------------
// Close files.
if(hSource)
{
fclose(hSource);
}
if(hDestination)
{
fclose(hDestination);
}
if(hKey)
{
CryptDestroyKey(hKey);
}
return TRUE;
} // End of Encryptfile



 浙公网安备 33010602011771号
浙公网安备 33010602011771号