TrueCrypt
其实很早之前就知道这个软件,不过之前没有使用,今天折腾了一把,记录下使用过程中遇见的一些问题。
百度百科:
TrueCrypt,是一款免费开源的加密软件,同时支持Windows Vista,7/XP, Mac OS X, Linux 等操作系统。TrueCrypt不需要生成任何文件即可在硬盘上建立虚拟磁盘,用户可以按照盘符进行访问,所有虚拟磁盘上的文件都被自动加密,需要通过密码来进行访问。TrueCrypt 提供多种加密算法,包括:AES-256, Blowfish (448-bit key), CAST5, Serpent, Triple DES, and Twofish,其他特性还有支持FAT32和NTFS分区、隐藏卷标、热键启动等。
这个软件原来的官网是:http://www.truecrypt.org。不过现在官方号称这个软件已经不安全了。我们现在进去前面我说的那个官网就会自动跳转到http://truecrypt.sourceforge.net/这个网址。官方的解释是该软件不再安全,替代的产品是windows自带的bitlocker。原文如下:
WARNING: Using TrueCrypt is not secure as it may contain unfixed security issues
This page exists only to help migrate existing data encrypted by TrueCrypt.
The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP. Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform.
Migrating from TrueCrypt to BitLocker:
If you have the system drive encrypted by TrueCrypt:

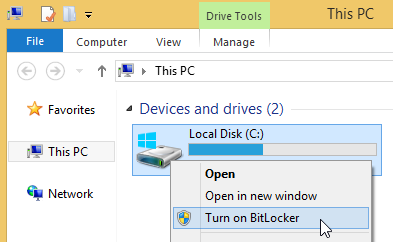
If you do not see the Turn on BitLocker menu item, click here.
Alternatively, use search in the Start menu or screen:

If you do not see the BitLocker item, click here.
If BitLocker reports Trusted Platform Module (TPM) unavailable error, click here.
If you have a non-system drive encrypted by TrueCrypt:
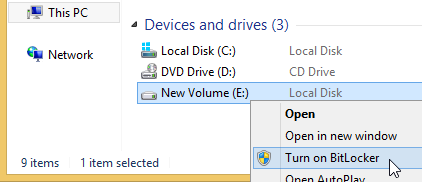
If you do not see the Turn on BitLocker menu item, click here.
If you do not have a spare drive, first decrypt the drive encrypted by TrueCrypt. Select the drive in TrueCrypt, open the Volumes menu and select Permanently Decrypt item (available in version 7.2). Then encrypt the drive by BitLocker (see above).
To mount a drive encrypted by BitLocker, open the drive in Explorer.
To dismount a removable drive encrypted by BitLocker, use Eject menu item or Safely Remove icon:

To dismount a non-removable drive encrypted by BitLocker, use Offline item in the context menu of the drive in Disk Management window:
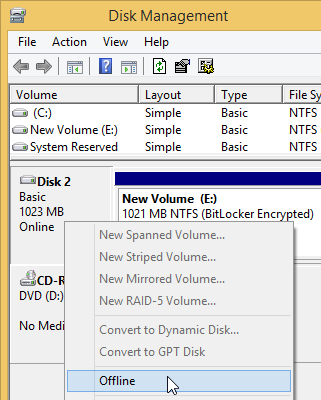
To mount the drive again, use Online item in the context menu of the drive.
If you have a file container encrypted by TrueCrypt:

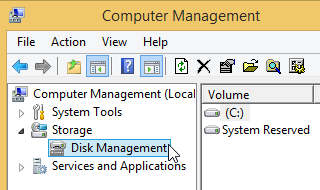
Alternatively, use search in the Start menu or screen:



If you do not see the Turn on BitLocker menu item, click here.
To dismount the drive, click the drive using the right mouse button in Explorer and select Eject:

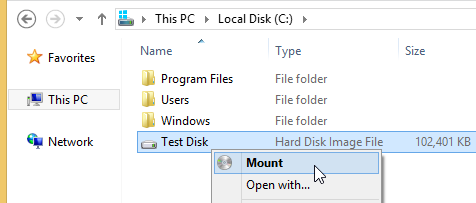
To mount the drive again, double click the virtual disk file (requires Windows 8 or later):
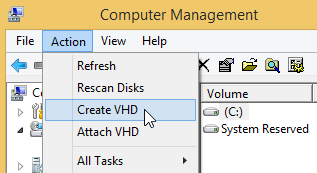
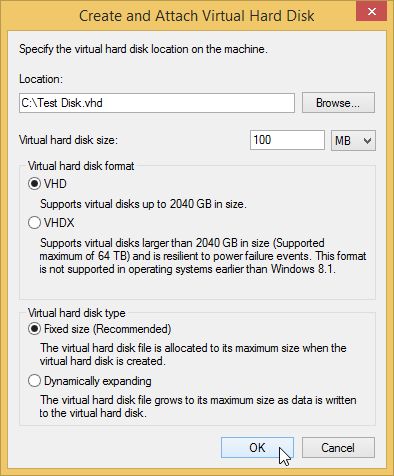
Alternatively, use Attach VHD in the Action menu of the Disk Management window:
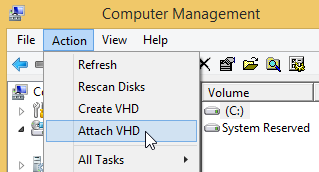
Download:
WARNING: Using TrueCrypt is not secure
You should download TrueCrypt only if you are migrating data encrypted by TrueCrypt.
TrueCrypt 7.2 sig key
If you use TrueCrypt on other platform than Windows, click here.
然后我自己下载使用了一下官网提供的最后的那个版本,结果发现可以安装,不过使用的时候会提示不安全而不能正常使用。于是就在我打算放弃使用这个软件的时候,我又发现了这篇帖子:http://www.52pojie.cn/thread-325161-1-1.html
TrueCrypt不会死 -- 瑞士网友创建TrueCrypt新家园
在一个国外的网站上看到了一篇关于著名加密软件TrueCrypt的英语文章,我把主要意思翻译了一下,供有兴趣的网友参考。
The development of TrueCrypt, an open source piece of software used for on-the-fly encryption, has been terminated and users have been advised not to use it because it is not secure enough. Now, it seems that another team of developers have forked the software and rebased it in Switzerland.
The abrupt announcement of the demise of TrueCrypt took everyone by surprise and some of its users have been disappointed that their favorite software is no longer being developed. The Sourceforge website, where the project was keeping its files, is now plastered with warnings that TrueCrypt is no longer secure because it is full of security issues.
Fortunately for us, TrueCrypt was an open source project and that meant that anyone could take it and fork it into another version, and try to fix some of the problems reported. Whether this will be a success remains to be seen, but at least there is a chance that it will live on.
Many users think that the TrueCrypt project has been forced to close its doors by various other malevolent forces, like the US government, for example. To be fair, the US government is accused of many such acts, but it is likely that it's not actually responsible for all of them.
So, TrueCrypt has now been rebased in Switzerland and the project has been forked by another team of developers. They are promising that the security problems will be fixed and that no one will be able to force them to close the gates.
“Currently it is very unclear what really happened. Was it really just the end of a 10 year effort, or was it driven by some government? While a simple defacement is more and more unlikely we still don't know where this is going. However the last 36 hours showed clearly that TrueCrypt is a fragile product and must be based on more solid ground. We start now with offering to download the Truecrypt file as is, and we hope we can organize a solid base for the Future,” reads the new truecrypt.ch website.
曾获包括斯诺登(Edward Snowden)在内的专业人士推荐并使用过的流行达十年之久的著名加密软件TrueCrypt,于2014年5月28日突遭关闭,其官方网站被重定向到 SourceForge网页并且警告称该软件并不安全,建议所有TrueCrypt用户将加密的数据迁移到Bitlocker,这一消息对于很多习惯了使用TrueCrypt的用户来说犹如一颗重磅炸弹!TrueCrypt项目究竟发生了什么?对于TrueCrypt突遭神秘关闭的背景、真实原因,一时间各种猜测纷至沓来:网站被黑、有人恶作剧、主要开发者已经放弃开发甚至已经死亡、项目被NSA盯上并遭到胁迫、发现重大安全漏洞甚至已经被胁迫植入后门等等。
真正的背景如何,有待进一步观察。不过已经有一些热心的网友开始行动起来准备拯救他们一直以来心爱的加密软件,一个瑞士的开发者团队刚刚组建了TrueCrypt新的网上家园。他们决心修复TrueCrypt的安全漏洞并且承诺没有人能够强迫他们关闭大门!
参见:
Steve Gibson: TrueCrypt is still safe to use(TrueCrypt仍然可以安全使用) https://www.grc.com/misc/truecrypt/truecrypt.htm
TrueCrypt瑞士开发团队官网:If TrueCrypt.org really is dead, we will try to organize a future. http://truecrypt.ch/
英文原文:https://www.grc.com/misc/truecrypt/truecrypt.htm
 | TrueCryptⓇ | |
| Final Release Repository |
| Phase 2 of the TrueCrypt Audit FINISHED! No significant cryptographic problems foundAnd see why the TrueCrypt spinoffs are violations of the TrueCrypt license. |
Recent attempts to download the TrueCrypt files here, using Chrome or Firefox (Mozilla uses Google's technology), have been generating false-positive malware infection warnings. They must be false-positives because no change has been made to the files since this page was put up nearly a year ago (May 29th, 2014) and many people have confirmed that the downloaded binaries have not changed and that their cryptographic hashes still match.
Also, the well-known and respected “VirusTotal” site, which scans files through all virus scanners reports ZERO hits out of 57 separate virus scan tests: VirusTotal scan results.
We have no idea where or why Google got the idea that there was anything wrong with these files. This just appears to be “The Google” doing their best to protect us from ourselves. But that does misfire occasionally. We expect it to fix itself within a day or two.
Although the disappearance of the TrueCrypt site, whose ever-presence the Internet community long ago grew to take for granted, shocked and surprised many, it clearly came as no surprise to the developers who maintained the site and its namesake code for the past ten years. An analysis of the extensive changes made to TrueCrypt's swan song v7.2 release, and to the code's updated v3.1 license, shows that this departure, which was unveiled without preamble, was in fact quite well planned.
For reasons that remain a titillating source of hypothesis, intrigue and paranoia, TrueCrypt's developers chose not to graciously turn their beloved creation over to a wider Internet development community, but rather, as has always been their right granted by TrueCrypt's longstanding license, to attempt to kill it off by creating a dramatically neutered 7.2 version that can only be used to view, but no longer to create new, TrueCrypt volumes.
Then, leveraging the perverse and wrongheaded belief that software whose support was just cancelled renders it immediately untrustworthy, they attempted to foreclose on TrueCrypt's current and continued use by warning the industry that future problems would remain unrepaired. This being said of the latest 7.1a version of the code that has been used by millions, without change, since its release in February of 2012, more than 27 months before. Suddenly, for no disclosed reason, we should no longer trust it?
they still “owned” TrueCrypt, and that it was theirs to kill.
But that's not the way the Internet works. Having created something of such enduring value, which inherently requires significant trust and buy-in, they are rightly unable to now take it back. They might be done with it, but the rest of us are not.
The developers' jealousy is perhaps made more understandable by examining the code they have created. It is truly lovely. It is beautifully constructed. It is amazing work to be deeply proud of. Creating something of TrueCrypt's size and complexity, and holding it together as they did across the span of a decade, is a monumental and truly impressive feat of discipline. So it is entirely understandable when they imply, as quoted below, that they don't trust anyone else to completely understand and maintain their creation as they have. Indeed, it will not be easy. They might look at the coding nightmare atrocity that OpenSSL became over the same span of time and think: “Better to kill off our perfect creation than turn it over to others and have it become that.”
TrueCrypt's creators may well be correct. TrueCrypt may never be as pure and perfect as it is at this moment, today—in the form they created and perfected. Their true final version, 7.1a, may be the pinnacle of this story. So anyone would and should be proud to use and to continue to use this beautiful tool as it is today.
TrueCrypt's formal code audit will continue as planned. Then the code will be forked, the product's license restructured, and it will evolve. The name will be changed because the developers wish to preserve the integrity of the name they have built. They won't allow their name to continue without them. But the world will get some future version, that runs on future operating systems, and future mass storage systems.
There will be continuity . . . as an interesting new chapter of Internet lore is born.
Tweets from the @OpenCryptoAudit project:
- At 5:40am, 29 May 2014
We will be making an announcement later today on the TrueCrypt audit and our work ahead. - 9 hours later at 2:40pm, 29 May 2014
We are continuing forward with formal cryptanalysis of TrueCrypt 7.1 as committed, and hope to deliver a final audit report in a few months. - And eight minutes later at 2:48pm, 29 May 2014
We are considering several scenarios, including potentially supporting a fork under appropriate free license, w/ a fully reproducible build.
So it appears that the unexpected (putting it mildly) disappearance of TrueCrypt.org and the startling disavowal of TrueCrypt's bullet proof security will turn out to be a brief disturbance in the force. We should know much more about a trustworthy TrueCrypt in the late summer of 2014.
| Time to panic? No. The TrueCrypt development team's deliberately alarming and unexpected “goodbye and you'd better stop using TrueCrypt” posting stating that TrueCrypt is suddenly insecure (for no stated reason) appears only to mean that if any problems were to be subsequently found, they would no longer be fixed by the original TrueCrypt developer team . . . much like Windows XP after May of 2014. In other words, we're on our own.But that's okay, since we now know that TrueCrypt is regarded as important enough (see tweets above from the Open Crypto Audit and Linux Foundation projects) to be kept alive by the Internet community as a whole. So, thanks guys . . . we'll take it from here. |
| Note that once TrueCrypt has been independently audited it will be the only mass storage encryption solution to have been audited. This will likely cement TrueCrypt's position as the top, cross-platform, mass storage encryption tool. |
My two blog postings on the day, and the day after, TrueCrypt's self-takedown:
My third and final posting about this page, in order to allow feedback.
The posting generated many interesting comments:
| And then the TrueCrypt developers were heard from . . . Steven Barnhart (@stevebarnhart) wrote to an eMail address he had used before and received several replies from “David.” The following snippets were taken from a twitter conversation which then took place between Steven Barnhart (@stevebarnhart) and Matthew Green (@matthew_d_green):
|
| TrueCrypt v7.1a installation packages: | Downloads | |
| • TrueCrypt Setup 7.1a.exe (32/64-bit Windows) | 285,739 | |
| • TrueCrypt 7.1a Mac OS X.dmg | 66,215 | |
| • truecrypt-7.1a-linux-x64.tar.gz | 69,302 | |
| • truecrypt-7.1a-linux-x86.tar.gz | 42,687 | |
| • truecrypt-7.1a-linux-console-x64.tar.gz | 30,893 | |
| • truecrypt-7.1a-linux-console-x86.tar.gz | 24,388 | |
| The TrueCrypt User's Guide for v7.1a: | ||
| • TrueCrypt User Guide.pdf | 152,372 | |
| The TrueCrypt v7.1a source code as a gzipped TAR and a ZIP: | ||
| • TrueCrypt 7.1a Source.tar.gz | 24,977 | |
| • TrueCrypt 7.1a Source.zip | 30,683 | |
(Because caution is never foolish.)
- Many sites attempt to assert the authenticity of the files they offer by posting their cryptographic hash values. But if bad guys were able to maliciously alter the downloaded files, they could probably also alter the displayed hashes. Until we have secure DNS (DNSSEC, which will create a secured Internet-wide reference for many things besides IP addresses) the best we can do is host confirmation hashes somewhere else, under the theory that as unlikely as it is that this primary site was hacked, it's significantly less likely that two unrelated sites were both hacked.
So, for those who double-knot their shoelaces, Taylor Hornby (aka FireXware) of Defuse Security is kindly hosting a page of hash values of every file listed above. And, being the thorough cryptographic code auditor that he is, Taylor first verified the files GRC is offering here against several independent archives:
Additional online TrueCrypt sites and repositories:
- The reconstructed browsable version of the truecrypt.org website. A terrific Canadian web developer, Andrew Y. (who also created the ScriptSafe Chrome browser extension to duplicate the script-disabling of Firefox's NoScript), captured some of the TrueCrypt.org website before it disappeared from the Internet and then reconstructed the missing pieces using the PDF manual. The result is a terrific web-browsable site for TrueCrypt.
- TrueCrypt.ch: A just launched, Swiss-based, possible new home for TrueCrypt. Follow these folks on Twitter: @TrueCryptNext. Given the deliberate continuing licensing encumbrance of the registered TrueCrypt trademark, it seems more likely that the current TrueCrypt code will be forked and subsequently renamed. In other words . . . for legal reasons it appears that what TrueCrypt becomes will not be called “TrueCrypt.”
- github.com/DrWhax/truecrypt-archive: This is a frequently cited and trusted archive maintained by Jurre van Bergen (@DrWhax) and Stefan Sundin. It contains a nearly complete, historical repository of previous TrueCrypt versions, tracking its evolution all the way back to when it was previously named “ScramDisk” (which is when we were first using and working with it).
- github.com/syglug/truecrypt: Another TrueCrypt v7.1 archive, though apparently not the latest. But readily browsable if someone wishes to poke around within the source with their web browser.
- IsTrueCryptAuditedYet.com: This is the home of the TrueCrypt auditing project. As the audit moves into its next phase, digging past the startup and boot loader and into the core crypto, updates will be posted and maintained here.
Graphic designer William Culver spend a bit of time thinking about a logo for whatever TrueCrypt becomes in the future. The theme of an infinity symbol is meant to convey the endless lifetime of this terrific data encryption solution. As is made clear on William's page for this, he's releasing all copyright:

256 x 256 pixels
32 x 32 pixels
Additional Miscellany:
- Amazon uses TrueCrypt when exporting archived data to users. See the first Q&A of the link. TrueCrypt is a perfect solution for this. We have every reason to believe that it is utterly bulletproof and only TrueCrypt provides the universal Windows/Mac/Linux platform neutrality that this application requires.
瑞士继续维护这个软件的组织的官网是:https://truecrypt.ch/
下面说说我自己的总结:
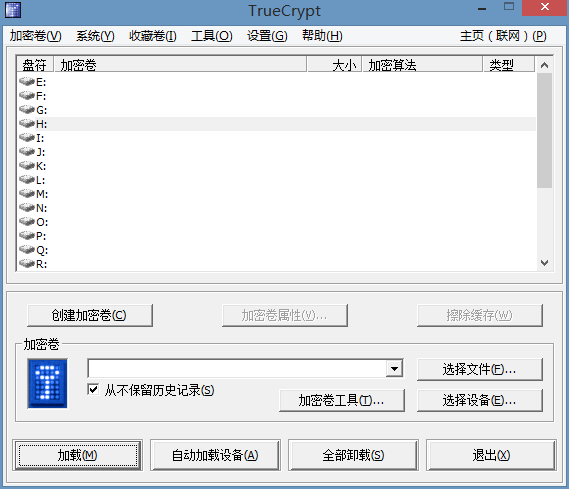
官网最新的7.2版本不能正常使用,不过他的老版本可以正常使用,比如7.2的上一个版本7.1a。这些继续维护他的网站提供了7.1a版本的下载,并做了一些改进。于是我安装了7.1a版本。安装好是英文的界面,不过网上很多简体中文语言包,复制到该软件的安装目录然后在软件的setting什么选择一下语言包即可,这个软件可以安装,也可以解压使用,很方便,安装好之后界面如下:
功能有很多,我说说几种常用的使用吧。
文件型加密:
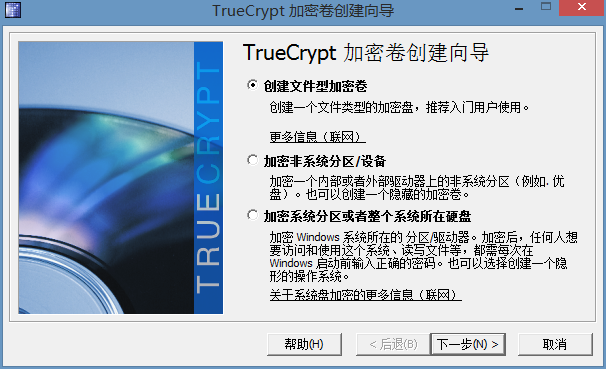
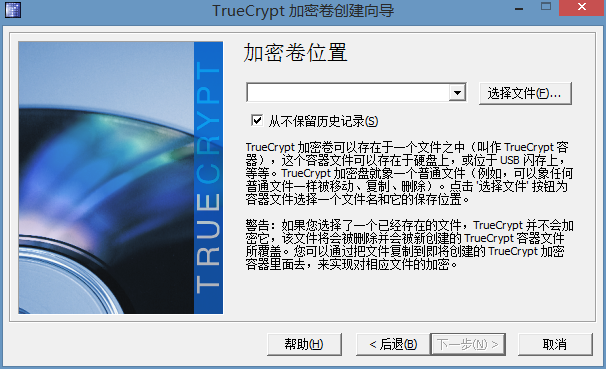
点击“创建加密卷”,
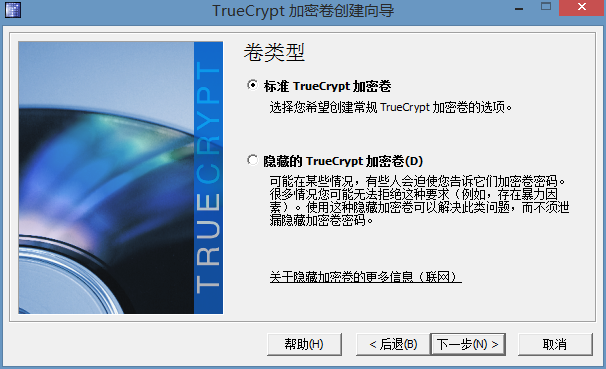
可以看见有三种,我现在说的就是第一种,第二种是以分区的形式,第三种是以系统分区的形式,也就是给你现在所使用的系统进行加密,开机的时候会提示你输入密码才能进入,继续说第一种,下一步。
下一步。
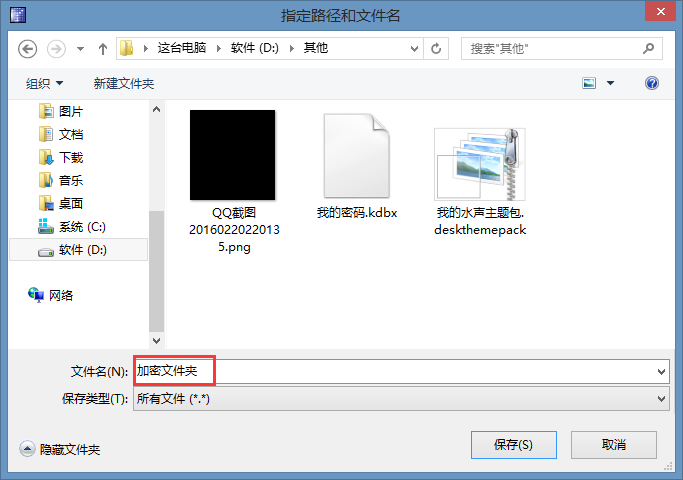
这个时候需要手动创建一个文件来作为你的加密分区,位置随便你,点击“选择文件”
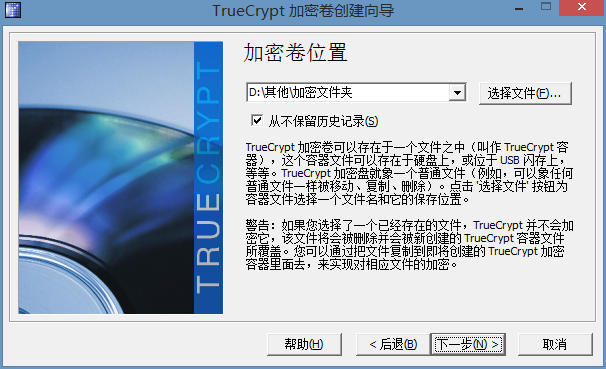
比如我输入“加密文件夹”然后确定。
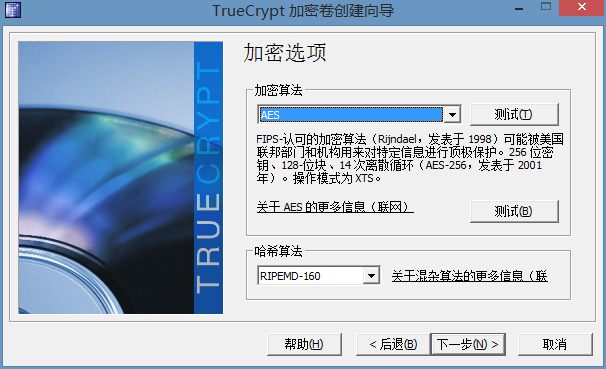
下一步,这里可改加密算法。
下一步。
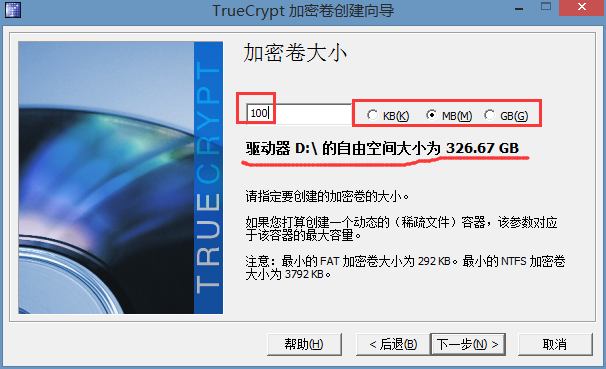
这里大小看你自己的需要,如果你要隐藏的东西很多就大点,此时下面为什么显示的是D盘呢?这是因为我刚才创建那个文件的时候创建在D盘里面,所以我们新创建的这个加密卷其实是用了D盘的空间,从D盘划分了一部分来使用,所以到时候我创建好这个加密卷的时候,这个加密卷有多大,那么D盘也就会相应的减少多大的空间。这里我就输入100MB,然后下一步,
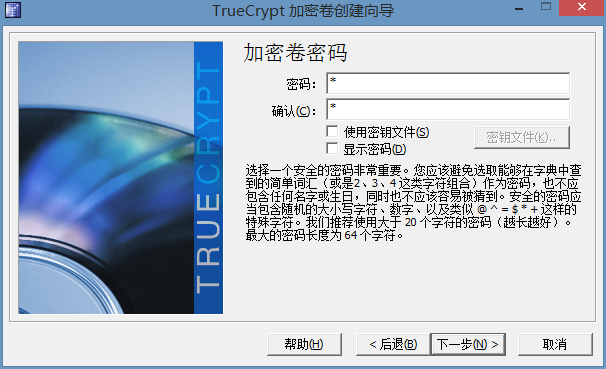
这里提示你输入密码,并且可以使用一个密钥文件,如果你觉得不够安全的话就可以使用一个密钥文件,这个文件可以是一张图片,一个mp3等等。然后到时候解密使用这个加密卷的时候没有这个密钥文件就不能解开,所以如果你使用了一个密钥文件,那么一定要保管好这个文件,不过到时候打不开你的加密卷是很悲催的。然后接着下一步。
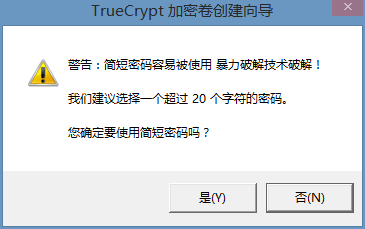
我的密码太短了,没关系,选“是”
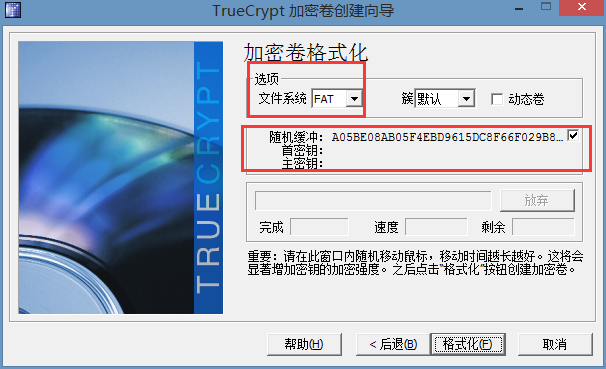
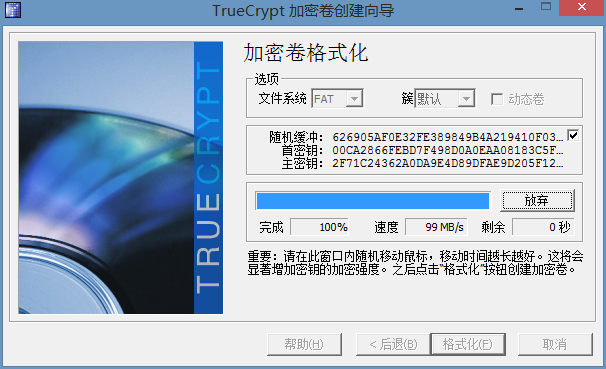
这里你可以选择不同文件系统来作为你加密卷的文件系统,并且可以移动鼠标来产生随机缓冲。然后选择“格式化”。
退出即可。
到这里创建文件型加密卷就完成了。那么该怎么使用这个呢?
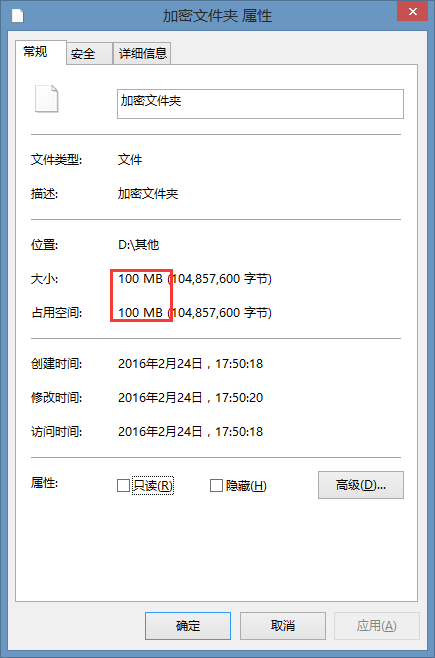
我们可以看见这个加密卷的大小是100MB。
相应的D盘也减少了100MB。
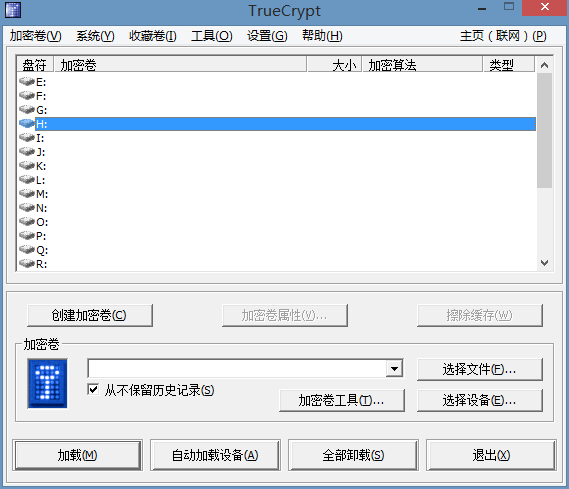
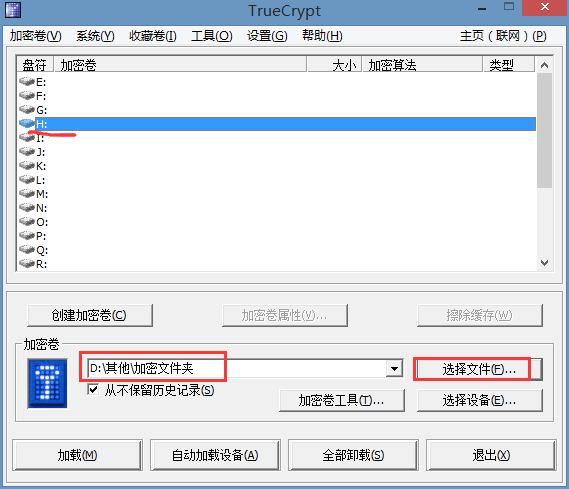
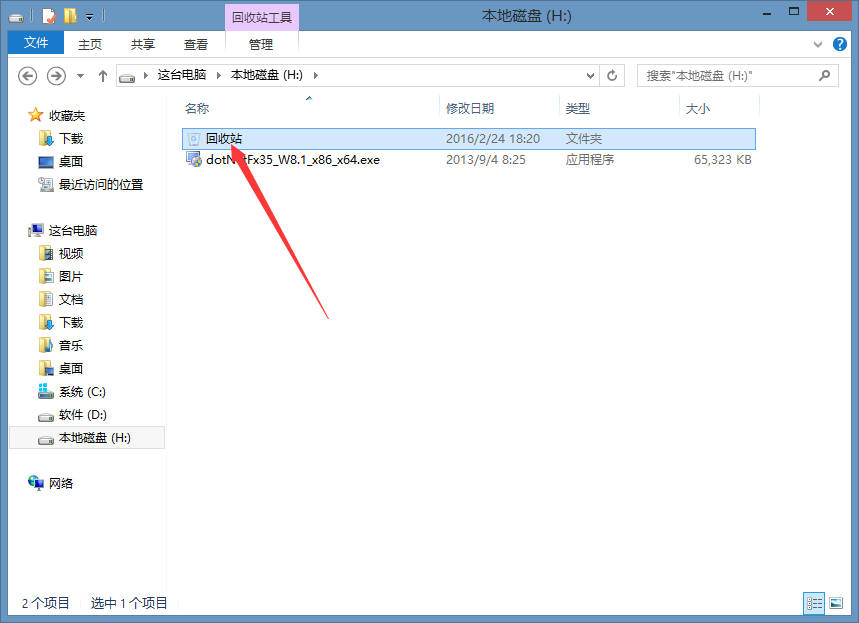
此时我们可以通过挂载这个加密卷来往里面添加一些我们想要隐藏的文件,方法:随便选择一个盘符,
然后选择我们刚才创建的那个文件。
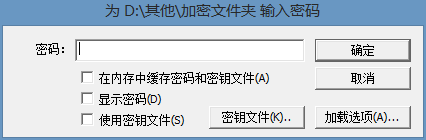
然后点击左下角的“挂载”,然后出现下面的提示,
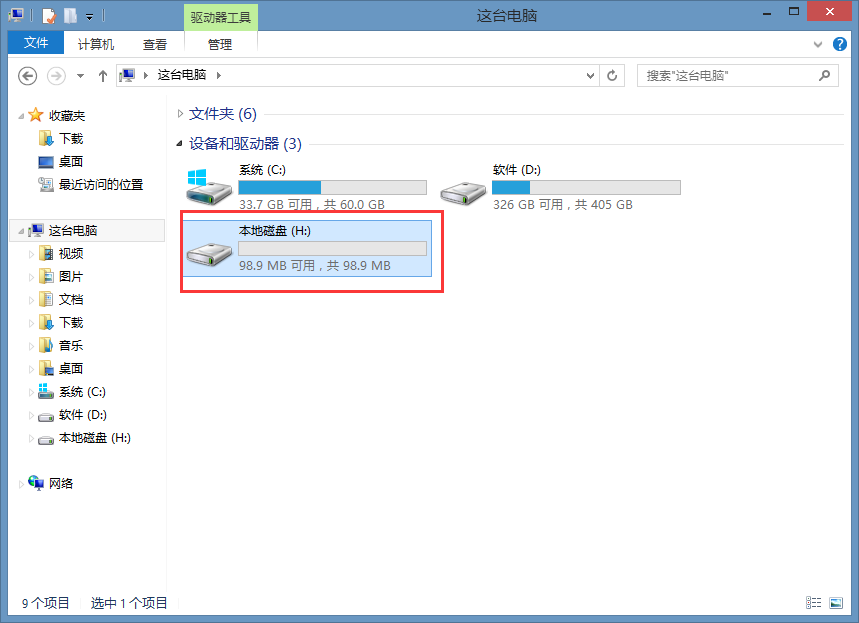
输入密码然后确定就会在资源管理器中看见多了一个盘符H。
此时就可以往这个加密卷中添加东西了。
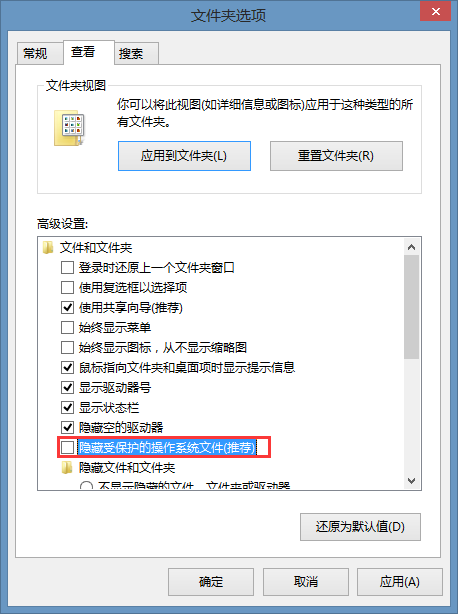
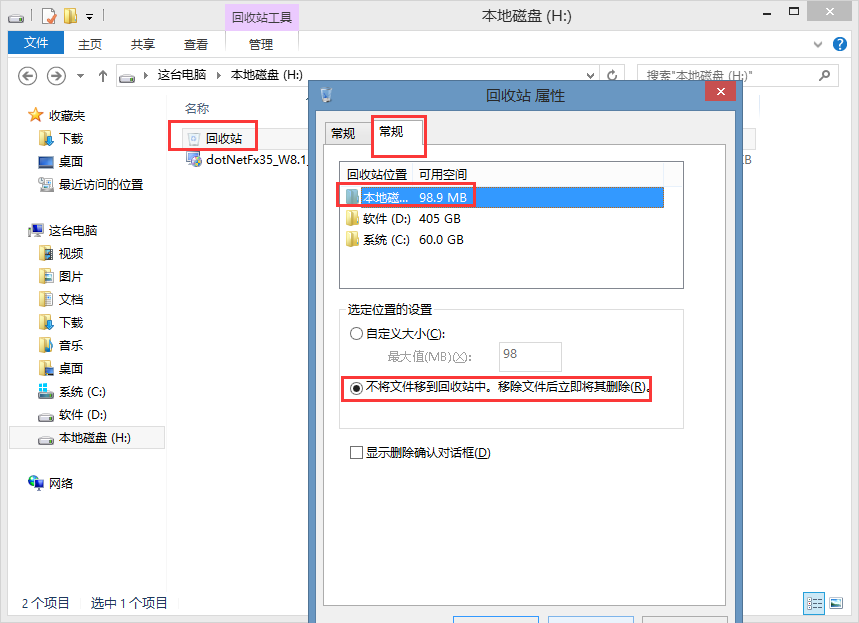
然后卸载之后就会隐藏掉这个加密卷了,别人不能看见,就算知道这个文件也没有密码打开。因为是文件型的加密卷,所以这个文件其实还是属于D盘,所以如果从D盘往这个加密卷中添加东西可以看见很快,不过由于我刚才选择的是FAT文件系统,所以不支持复制大于4G的文件,改成NTFS就可以了。还有就是我们在这个加密卷中删除一些东西之后我们会看见这个加密卷的可用空间还是一样,这是因为这个在这个加密卷中也存在一个回收站,删除的东西还是在这个加密卷中,这个回收站是隐藏的,所以看不见,可以通过取消勾选下图中的选项来看见。
可以在回收站上右击——属性让删除的文件不经过回收站。
还有我们手动删除了这个加密卷之后会发现他的空间归还给了原来的D盘,因为这个是文件型的加密卷。
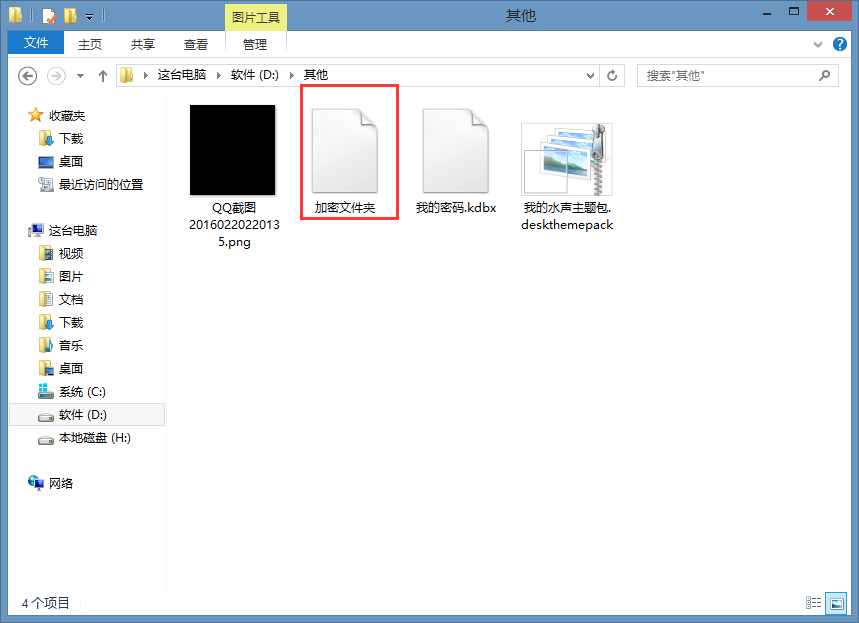
还有就是这个文件
可以随意更改名称,也可以添加扩展名。
这个软件还有很多其他的功能,比如加密windows,这里就不再讲了。





 浙公网安备 33010602011771号
浙公网安备 33010602011771号