【Crypto】wp
目录
6.ROT13+hex(base16)+base32+base64+base85
1.凯撒密码

见题目可知:凯撒密码
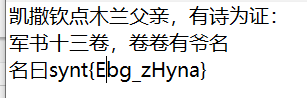
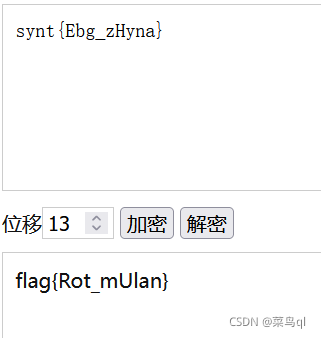
见synt可知移位13
2.rsa1
看到p,q,想到rsa
打开factordb
将一串大数放入计算
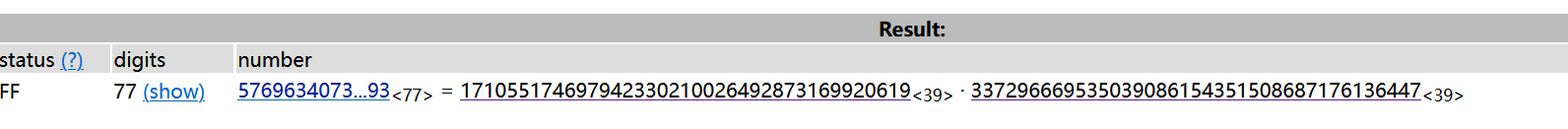
可见两个数分别为p和q
已知p+q=
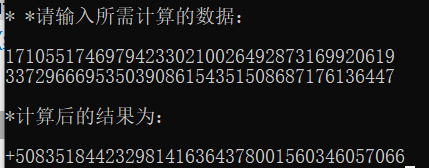
用sha1加密

3.rsa2
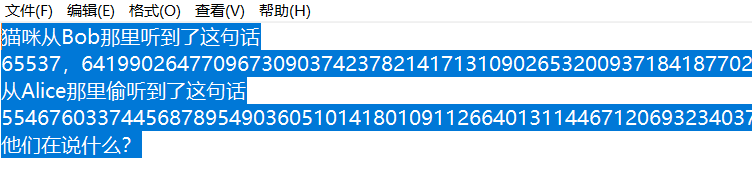
看到65537,想到rsa的e
尝试两个数,找出n(可分解为两个素数相乘)
那么另一个数就是c了
from Crypto.Util.number import *
import gmpy2
# 由题目可知
c = 55467603374456878954903605101418010911266401311446712069323403726580883739934
e = 65537
n = 64199026477096730903742378214171310902653200937184187702996339280215555390807
# yafu 分解 n 可得 p 和 q
p = 214632396793808784541787006171047378643
q = 299111538780284425759013610980166311149
# 计算私钥 d
d = gmpy2.invert(e, (p-1)*(q-1))
# 解密 m
m = pow(c,d,n)
print(long_to_bytes(m))
# b'flag{now_y0u_know_rsa}'运行输出flag
4.摩斯密码+base32+base64+7bit编码
打开附件 
发现是摩斯密码,解码
JFCFSMSOPJNG2T2HJJVE22TDGVHDETTJLFVESMKZNJUGWT2ULJUU2MSRGFHGUSL2JYZES6SPI5GXQTTKNN5FURCWNJHUITL2JZLUKM2PIRUGUT2HJJVVUR2NGRNFITLYLEZEM3COI5HGYWSUIF5A
base32后:
IDY2NzZmOGJjMjc5N2NiYjI1YjhkOTZiM2Q1NjIzN2IzOGMxNjkzZDVjODMzNWE3ODhjOGJkZGM4ZTMxY2FlNGNlZTAz
base64后:
6676f8bc2797cbb25b8d96b3d56237b38c1693d5c8335a788c8bddc8e31cae4cee03
题目提示为:7bit
原理如下:
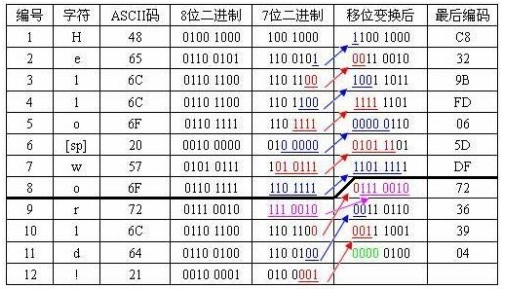
根据ASCII码 开始快乐的7bit解码时间
得到flag
5.栅栏密码+培根密码

肥肠神似英文句子,怀疑为栅栏密码
看得出来出题人费了大劲区分大小写,所以我们要十分给面子的试一下培根密码(谢谢你,出题人)
尝试一下将大、小写改为A、B或B、A
直接培根密码得出flag
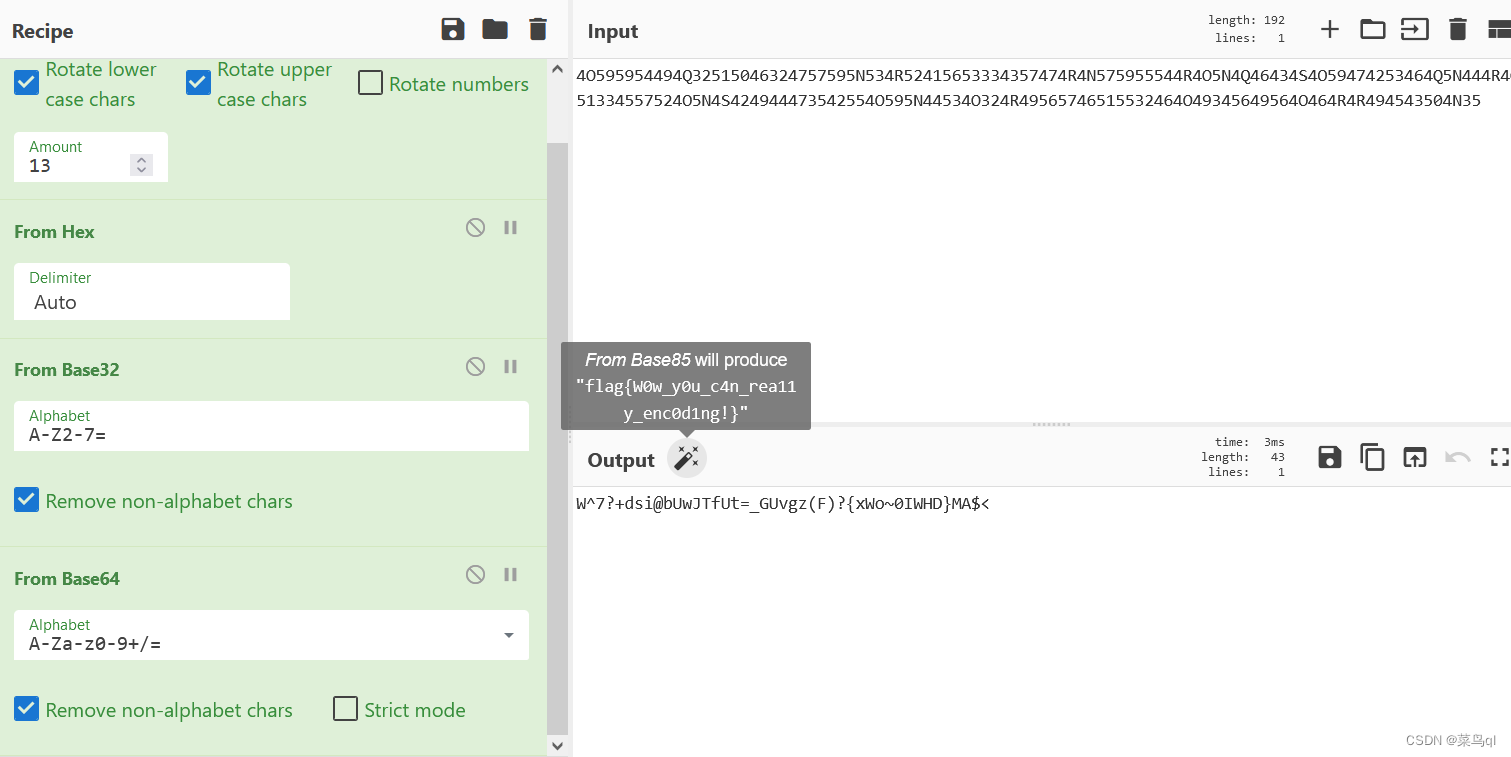
6.ROT13+hex(base16)+base32+base64+base85
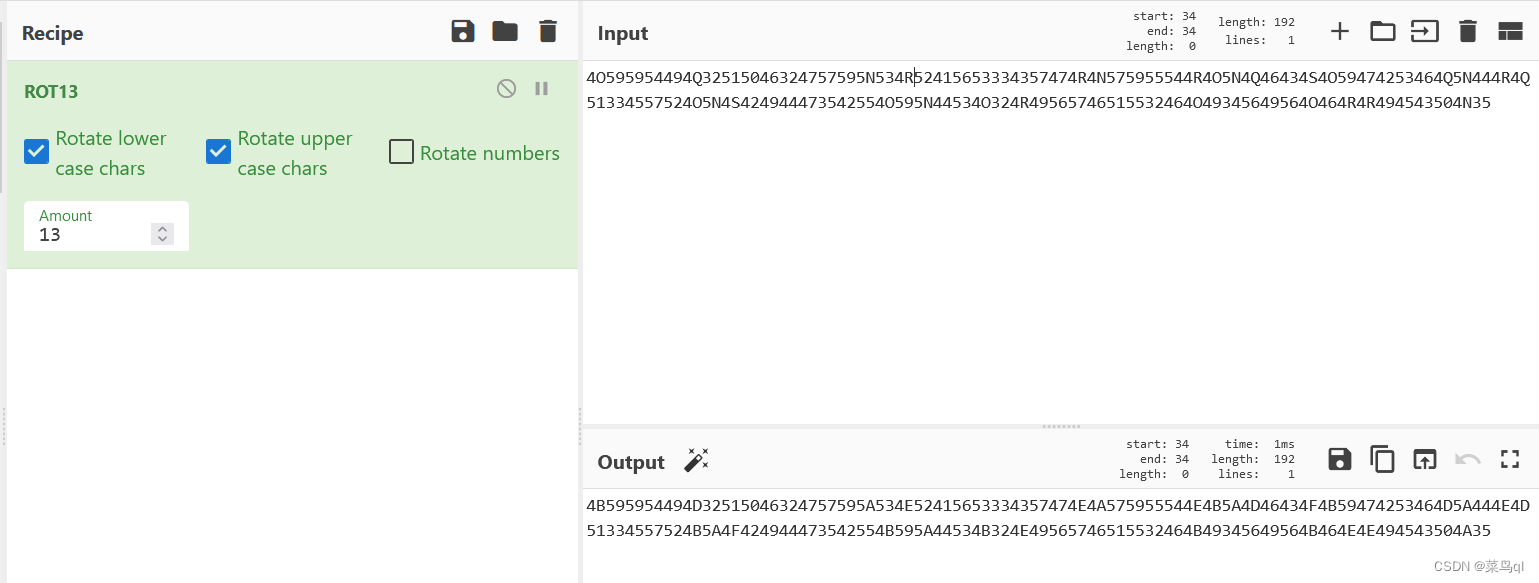
密码由数字0~9和字母A~F组成,用base16
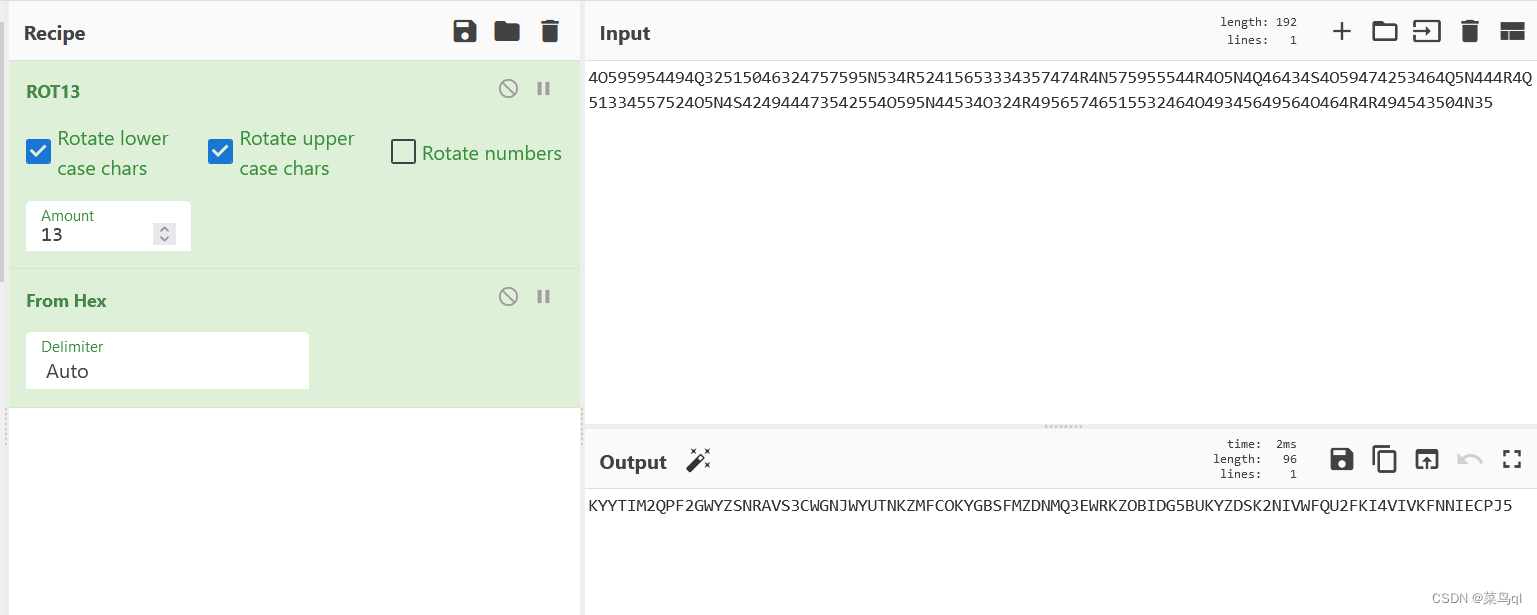
密码由字母A~Z和数字2~7 组成,用base32
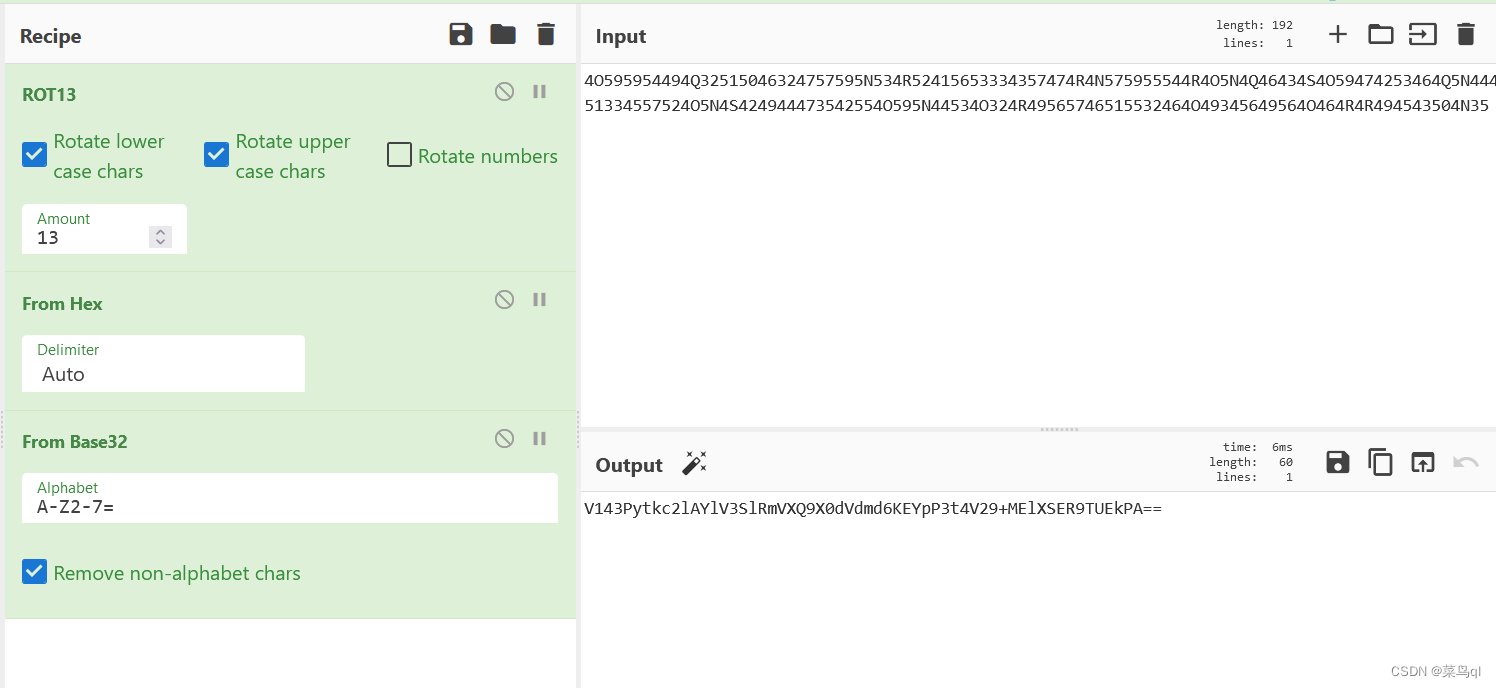
密码由A~Z,a~z,0~9,+,/组成,且末尾有=(
如果要编码的字节数不能被3整除,最后会多出1个或2个字节,那么可以使用下面的方法进行处理:(1)先使用0字节值在末尾补足,使其能够被3整除,然后再进行Base64的编码。
(2)在编码后的Base64文本后加上一个或两个=号,代表补足的字节数。
),用base64
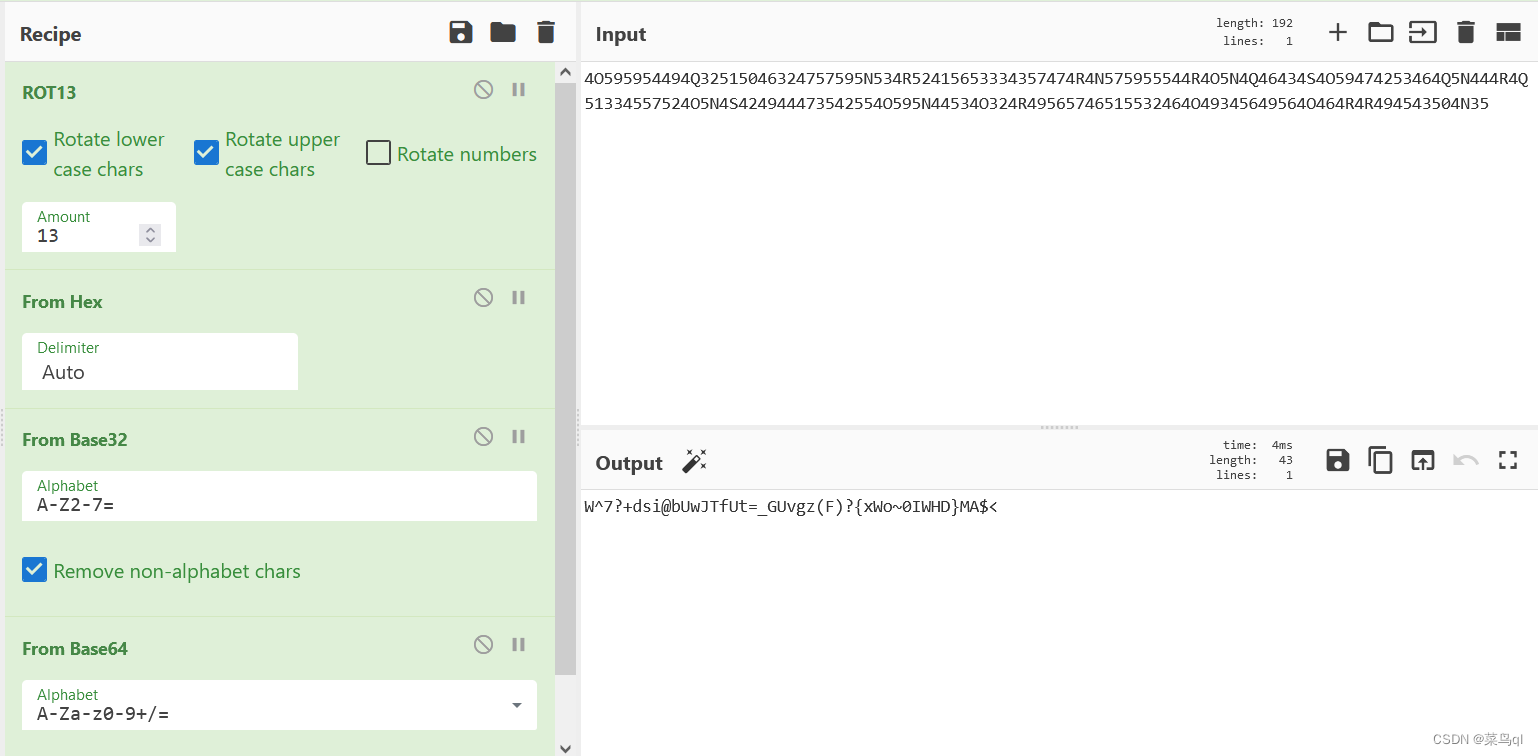
密码由0-9A-Za-z!#$%&()*+\-;<=>?@^_`{|}~组成,根据提示用base85
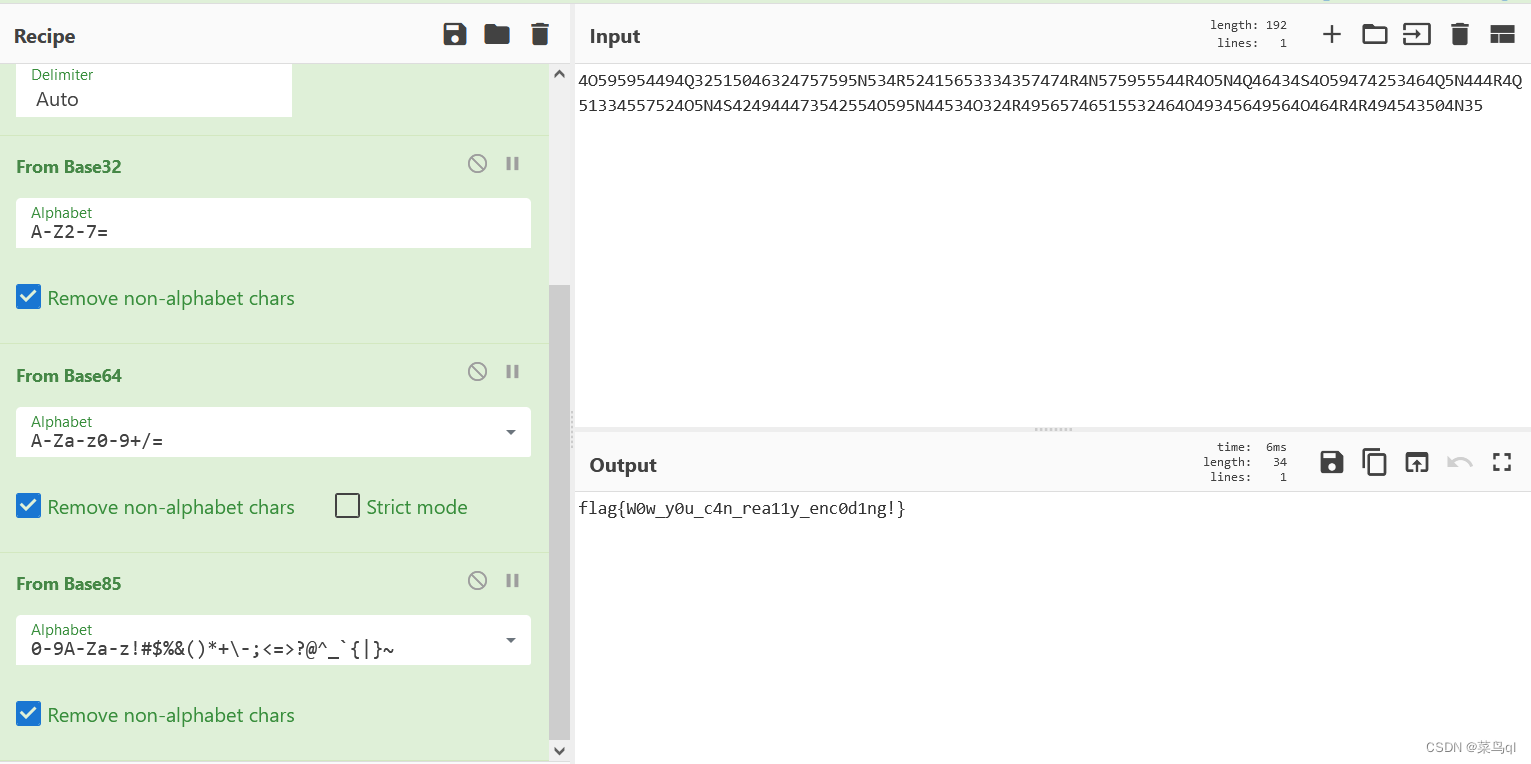
7.best_rsa
所给文件:

文件2同理
这可犯了难,怎么获取c,n,e呢
代码如下:
from Crypto.Util.number import *
from Crypto.PublicKey import RSA
import gmpy2
import binascii
c1=bytes_to_long(open('./cipher1.txt','rb').read())
c2=bytes_to_long(open('./cipher2.txt','rb').read())
pub1=RSA.importKey(open('./publickey1.pem').read())
pub2=RSA.importKey(open('./publickey2.pem').read())
n1= pub1.n
e1= pub1.e
n2= pub2.n
e2= pub2.e有了c1,n1,e1,c2,n2,e2,猜测为共模攻击:n1==n2
代码如下:
from Crypto.Util.number import *
from Crypto.PublicKey import RSA
import gmpy2
import binascii
c1=bytes_to_long(open('./cipher1.txt','rb').read())
c2=bytes_to_long(open('./cipher2.txt','rb').read())
pub1=RSA.importKey(open('./publickey1.pem').read())
pub2=RSA.importKey(open('./publickey2.pem').read())
n1= pub1.n
e1= pub1.e
n2= pub2.n
e2= pub2.e
assert n1==n2 #Python assert(断言)用于判断一个表达式,在表达式条件为 false 的时候触发异常。
s = gmpy2.gcdext(e1,e2)
a = s[1]
b = s[2]
if a<0:
a = -a
c1 = gmpy2.invert(c1,n1)
else:
b = -b
c2 = gmpy2.invert(c2,n1)
m = (gmpy2.powmod(c1,a,n1)*gmpy2.powmod(c2,b,n1))%n1
print(binascii.unhexlify(hex(m)[2:]))
运行得到flag
8.cr4-poor-rsa
解压文件
打开查看
flag.b64 0000644 0001750 0001750 00000000105 13023213602 012420 0 ustar oddcoder oddcoder Ni45iH4UnXSttNuf0Oy80+G5J7tm8sBJuDNN7qfTIdEKJow4siF2cpSbP/qIWDjSi+w=
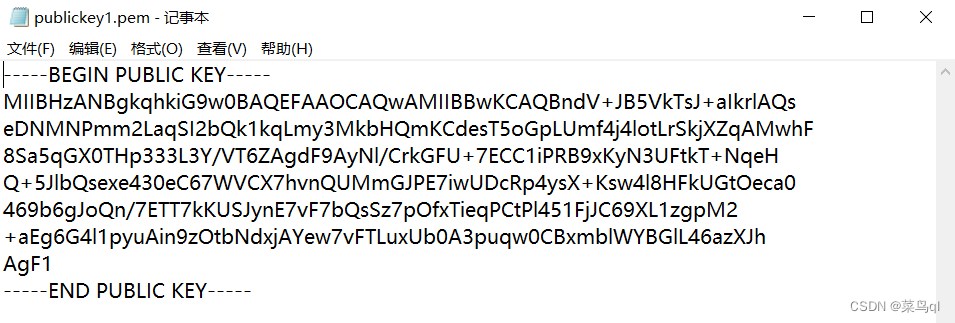
key.pub 0000644 0001750 0001750 00000000242 13023212532 012475 0 ustar oddcoder oddcoder -----BEGIN PUBLIC KEY-----
ME0wDQYJKoZIhvcNAQEBBQADPAAwOQIyUqmeJJ7nzzwMv5Y6AJZhdyvJzfbh4/v8
bkSgel4PiURXqfgcOuEyrFaD01soulwyQkMCAwEAAQ==
-----END PUBLIC KEY-----值得注意的有两部分:
flag.b64 Ni45iH4UnXSttNuf0Oy80+G5J7tm8sBJuDNN7qfTIdEKJow4siF2cpSbP/qIWDjSi+w=
上述推测其为base64加密过的密文
-----BEGIN PUBLIC KEY-----
ME0wDQYJKoZIhvcNAQEBBQADPAAwOQIyUqmeJJ7nzzwMv5Y6AJZhdyvJzfbh4/v8
bkSgel4PiURXqfgcOuEyrFaD01soulwyQkMCAwEAAQ==
-----END PUBLIC KEY-----上述为公钥
代码为:
from Crypto.Util.number import *
from Crypto.PublicKey import RSA
import gmpy2
import rsa
import base64
#将第二部分放入key.txt,读出n和e
pub=RSA.importKey(open('./key.txt').read())
n= pub.n
e= pub.e
#根据n算出p,q
p = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
#根据p,q,e算出phi与d
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
#生成私钥
priv = rsa.PrivateKey(n, e, d, p, q)
#将第一部分的base64编码放入1.txt并读出
with open("./1.txt", "rb") as file:
cipher = file.read()
#base64解码
cipher = base64.b64decode(cipher)
#利用私钥和解码后的字符cipher解密
m = rsa.decrypt(cipher, priv).decode()
print(m)
待补充

 扔到
扔到 
 浙公网安备 33010602011771号
浙公网安备 33010602011771号