基于nerdctl + buildkitd构建容器镜像
nerdctl + buildkitd构建镜像
buildkit 从Docker公司的开源的镜像构建工具包,支持OCI标准的镜像构建
buildkitd组成部分
buildkitd(服务端),目前支持runc和containerd作为镜像构建环境,默认是runc,可以更换containerd。
buildctl(客户端),负责解析Dockerfile文件、并向服务端buildkitd发出构建请求。
安装buildkit
Github项目地址:
https://github.com/moby/buildkit/releases
解压复制到/usr/local/bin
root@master1:~# tar xf buildkit-v0.10.3.linux-amd64.tar.gz
root@master1:~# cd bin/
root@master1:~/bin# cp * /usr/local/bin/
创建buildkit.socket
root@master1:~# vim /lib/systemd/system/buildkit.socket
[Unit]
Description=BuildKit
Documention=https://github.com/moby/buildkit
[Socket]
ListenStream=%t/buildkit/buildkitd.sock
[Install]
WantedBy=sockets.target
创建buildkitd.service
root@master1:~# vim /lib/systemd/system/buildkitd.service
[Unit]
Description=BuildKit
Require=buildkit.socket
After=buildkit.socketDocumention=https://github.com/moby/buildkit
[Service]
ExecStart=/usr/local/bin/buildkitd --oci-worker=false --containerd-worker=true
[Install]
WantedBy=multi-user.target
配置buildkitd配置文件,添加镜像仓库使用http访问
root@master1:/dockerfile# mkdir /etc/buildkit/
root@master1:/dockerfile# vim /etc/buildkit/buildkitd.toml
[registry."harbor.cncf.net"]
http = true
insecure = true
启动buildkitd
root@master1:~# systemctl daemon-reload
root@master1:~# systemctl start buildkitd
root@master1:~# systemctl enable buildkitd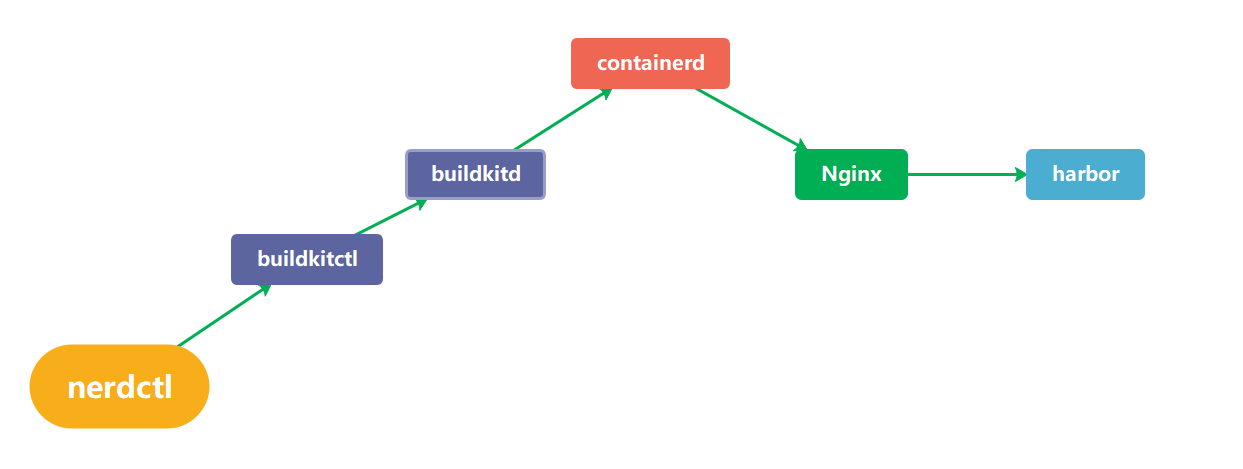
测试镜像构建
1、nerdctl构建镜像
修改nerdctl默认命名空间
root@master1:/dockerfile# mkdir -p /etc/nerdctl
root@master1:/dockerfile# vim /etc/nerdctl/nerdctl.toml
namespace = "k8s.io"
debug = false
debug_full = false
insecure_registry = true
需提前安装nerdctl工具
root@master1:~# nerdctl login --insecure-registry harbor.cncf.net
root@master1:~# nerdctl pull ubuntu:20.04
root@master1:~# nerdctl tag ubuntu:20.04 harbor.cncf.net/baseimages/ubuntu:20.04
root@master1:~# nerdctl push harbor.cncf.net/baseimages/ubuntu:20.04
添加私有仓库harbor https证书认证
root@master1:~# mkdir /etc/containerd/certs.d/harbor.cncf.net -p
#containerd会将crt识别为ca证书,Harbor需要将证书格式转换为cert格式
root@Harbor:/usr/local/harbor/certs# openssl x509 -inform PEM -in cncf.net.crt -out cncf.net.cert
root@Harbor:/usr/local/harbor/certs# scp ca.crt cncf.net.cert cncf.net.key 192.168.119.6:/etc/containerd/certs.d/harbor.cncf.net/
nerdctl打包构建dockerfile
root@master1:/dockerfile# cat Dockerfile
FROM harbor.cncf.net/baseimages/ubuntu:20.04
MAINTAINER LXH
ADD sources.list /etc/apt/
RUN apt-get update && \
apt-get install -y make libpcre3 libpcre3-dev \
zlib1g-dev libssl-dev build-essential \
openssl gcc vim make telnet iproute2 iputils-ping
ADD Shanghai /usr/share/zoneinfo/Asia/
RUN ln -snf /usr/share/zoneinfo/Asia/Shanghai /etc/localtimes
#构建镜像
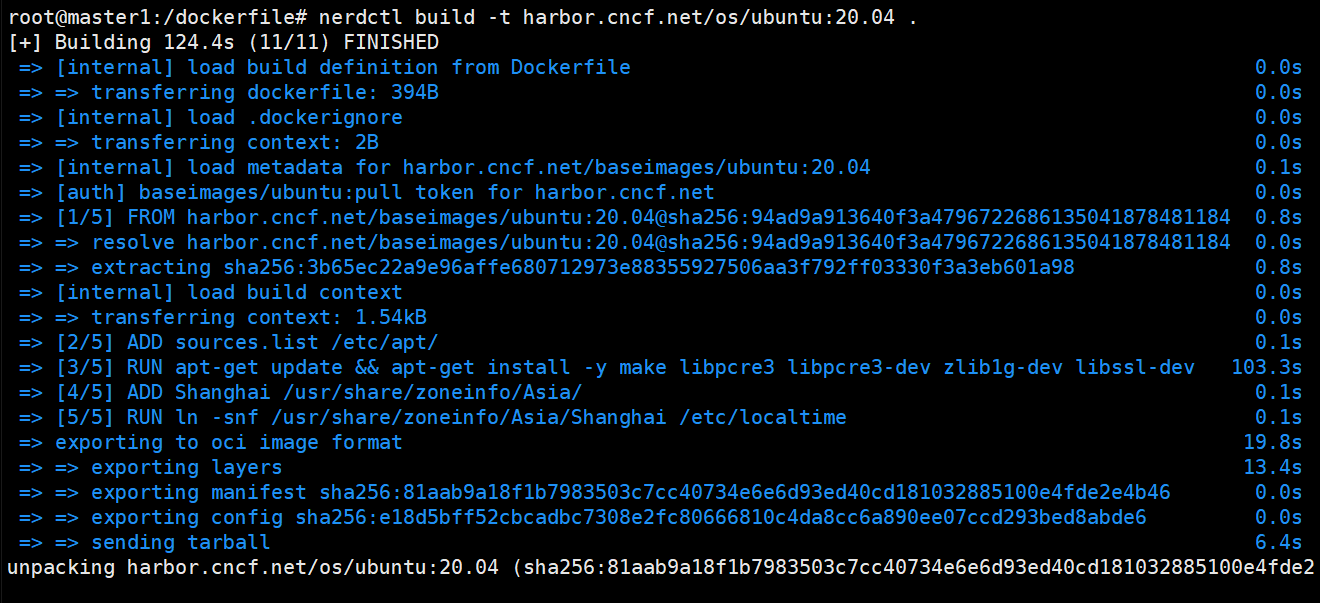
root@master1:/dockerfile# nerdctl build -t harbor.cncf.net/os/ubuntu:20.04 .
推送镜像到harbor
root@master1:/dockerfile# nerdctl push harbor.cncf.net/os/ubuntu:20.04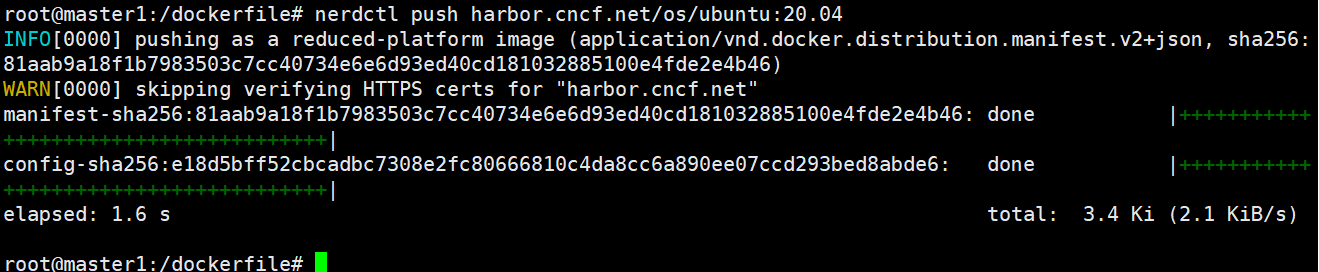
访问harbor验证
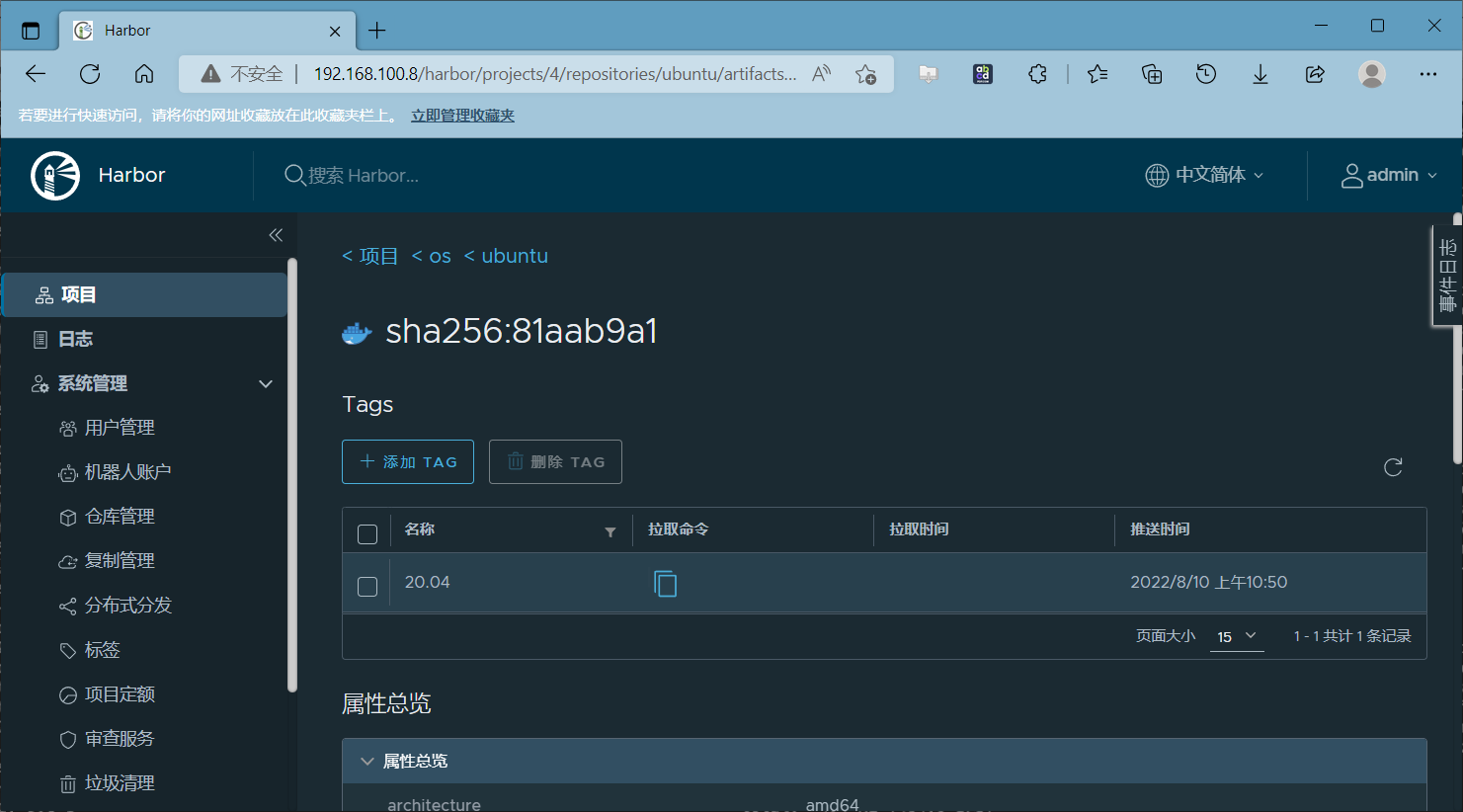
2、修改harbor自签发证书验证
如果harbor使用的是自签发的https认证,则containerd打包镜像就会出现证书认证错误:unkown authority未知的签发机构。
root@master1:/dockerfile# nerdctl build -t harbor.cncf.net/os/ubuntu:20.04 .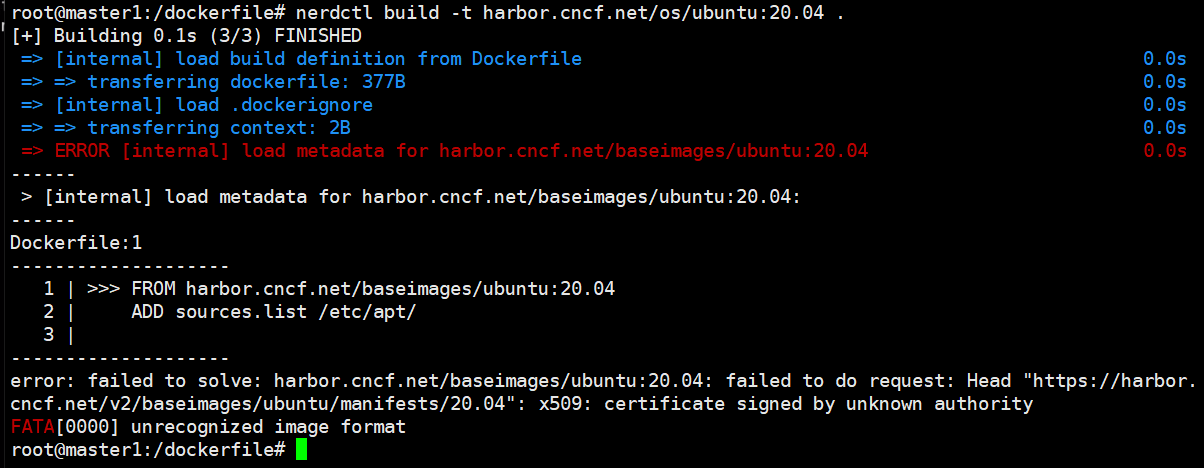
解决方法:
1、harbor仅使用http。
编辑harbor.yaml注释https配置
root@harbor:/usr/local/harbor# docker-compose stop
root@harbor:/usr/local/harbor# ./prepare
root@harbor:/usr/local/harbor# docker-compose up -d
2、可以使用机构签发的证书。(可选)
3、搭建nginx使用https,反向代理harbor http。
root@etcd1:/usr/local/nginx/conf# mkdir /usr/local/nginx/conf/certs
#harbor分发证书到nginx
root@harbor:/usr/local/harbor/certs# scp cncf.net.crt cncf.net.key 192.168.100.8:/usr/local/nginx/conf/certs/
#配置nginx
root@etcd1:/usr/local/nginx/conf# vim nginx.conf
client_max_body_size 2000m;
server {
listen 80;
server_name harbor.cncf.net;
listen 443 ssl;
ssl_certificate /usr/local/nginx/conf/certs/cncf.net.crt;
ssl_certificate_key /usr/local/nginx/conf/certs/cncf.net.key;
ssl_session_timeout 10m;
ssl_session_cache shared:sslcache:20m;
location / {
proxy_pass http://192.168.100.15;
}
}
#启动nginx
root@etcd1:/usr/local/nginx/conf# cd ../sbin/
root@etcd1:/usr/local/nginx/sbin# ./nginx
修改containerd服务器hosts 解析harbor地址为nginx
root@master1:/dockerfile# vim /etc/hosts
192.168.100.8 harbor.cncf.net
测试拉取镜像
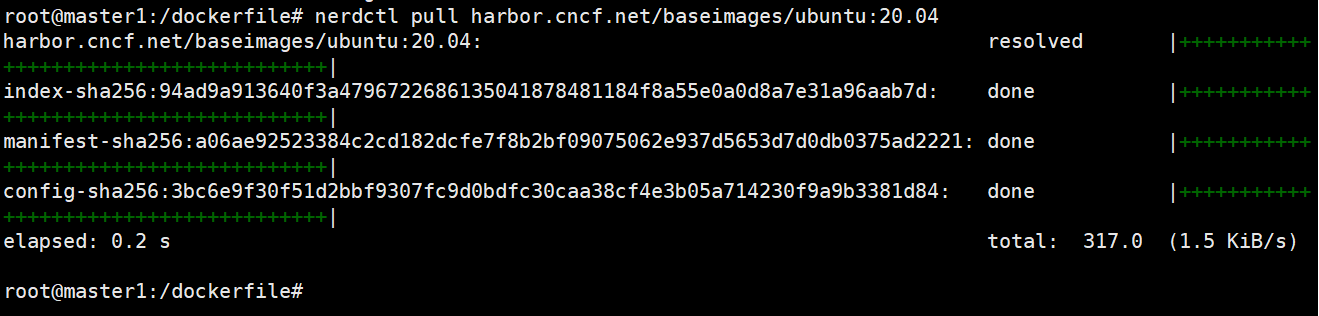
本文来自博客园,作者:PunchLinux,转载请注明原文链接:https://www.cnblogs.com/punchlinux/p/16575328.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号