Previously, it was shared that on Android 14, it is possible to perform APK Downgrade Extraction by using the parameter --bypass-low-target-sdk-block, allowing the installation of an older version of an apk to extract app data, as shown in the following article:
https://www.cnblogs.com/pieces0310/p/18198819
Now the question is: does APK Downgrade Extraction still work on Android 15?
You guys might infer that it does, based on what we know from Android 14. However, for a forensic examiner, it never hurts to be extra cautious. So, let's walk through a demonstration to clarify the situation.
First, I use an Android 14 device and installed the latest version of WhatsApp. The version information is shown below:
Then, I proceed with APK Downgrade Extraction. The critical step of installing the older version apk went smoothly without any issues, which once again confirms that APK Downgrade Extraction works as expected on Android 14.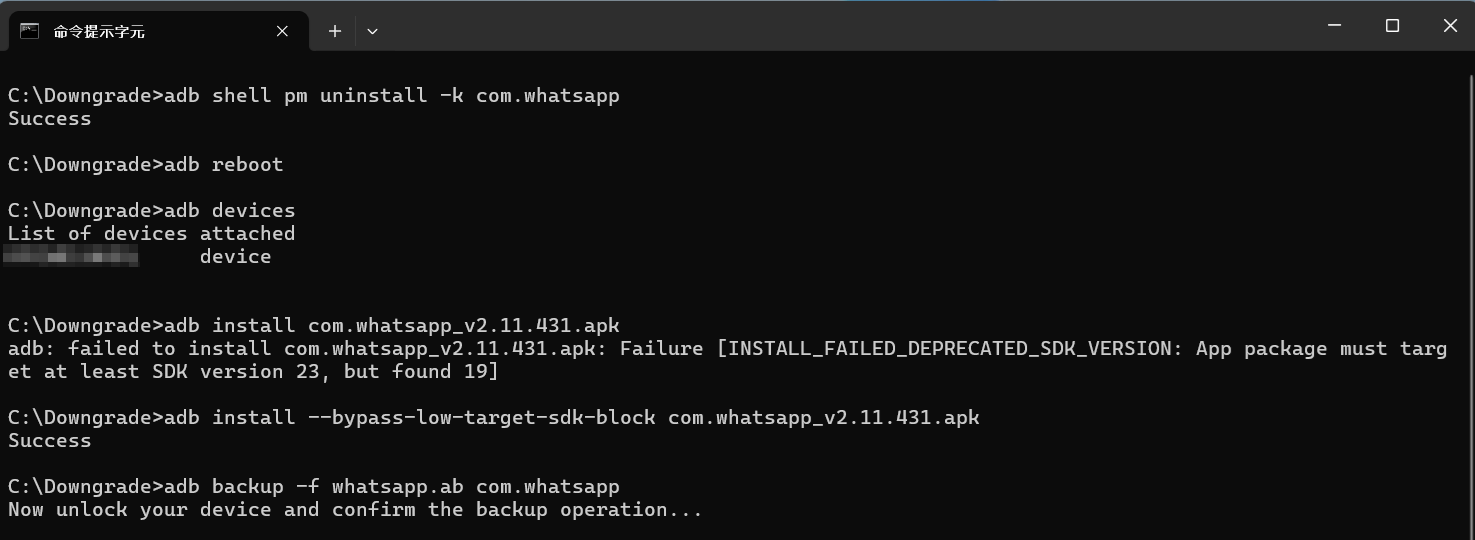
Next, I switch to an Android 15 device and installed the same latest version of WhatsApp to maintain consistency. Let’s see if the siutation differs. When I attempt to install the older version apk, the following error message appeared:
This error appears to be related to new security enhancements introduced in Android 15. Android 15 enforces stricter protections when installing legacy apk/apks, including downgrade protection and enhanced runtime permission management. The intention seems to be preventing malicious actors from bypassing security mechanisms through downgrade attacks.
However, this change poses a significant challenge to forensic examiners. When dealing with non-rooted Android 15 devices, attempting APK Downgrade Extraction to retrieve app data will now fail.
The only practical fallback is to reinstall the original apk/apks that was backed up at the beginning, to ensure that WhatsApp is restored to its original state.
In conclusion, forensic examiners should be especially cautious when dealing with APK Downgrade Extraction on Android 15. Some may believe that commercial forensic tools could bypass this limitation, but to be frank, these tools actually run the same commands as shown above—thus leading to the same outcome.
Of course, I shouldn't draw conclusions based solely on my own observations.
If any forensic examiner is willing to give it a try and see whether they obtain different results, your insights would be greatly appreciated.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号