With the increasing severity of cybersecurity threats on mobile devices, awareness of personal privacy protection is also growing. Consider this scenario: if you temporarily lend your phone to someone else and it remains unlocked, would you also worry about your personal privacy being compromised by apps being accessed?
Take iPhone as an example, the App Lock feature has been available since iOS 16.4, which is actually a built-in feature on some Android devices from certain manufacturers. Now, users on iPhone can achieve automation through setting shortcuts, enabling the phone to automatically lock when specific apps are opened, requiring unlocking before accessing those apps.

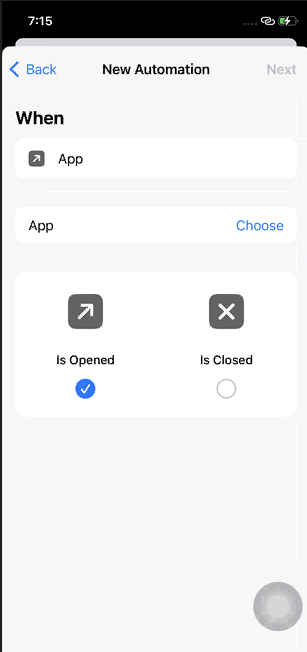
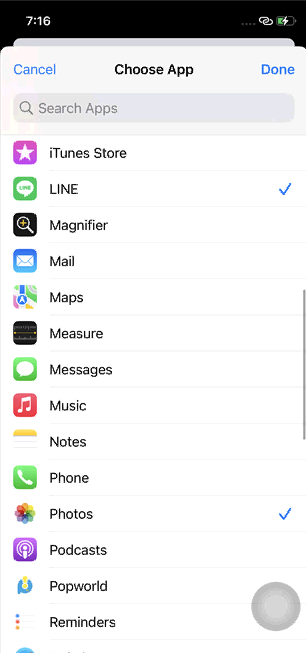
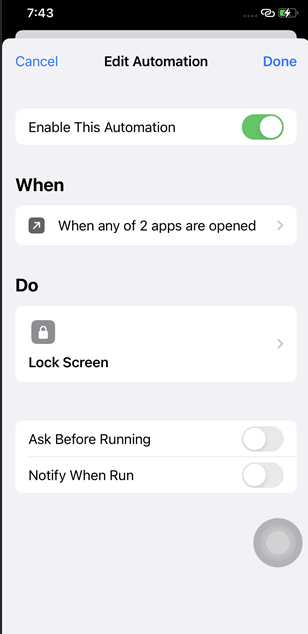
Once any app from the protected list is opened, the phone will automatically lock the screen, requiring the user to unlock it again to access the app smoothly. This effectively prevents unauthorized individuals from sneakily opening the app without your notice.
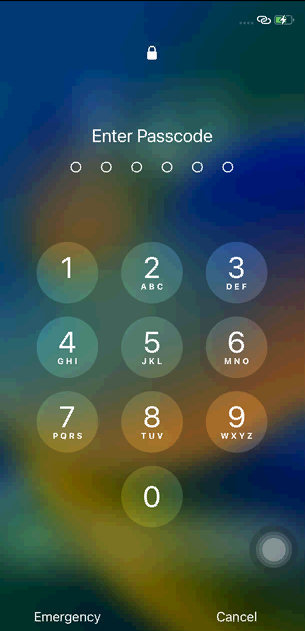
It is worth noting that if the PIN code is known or guessed due to its simplicity, the protection mechanism of the aforementioned App Lock becomes essentially ineffective.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号