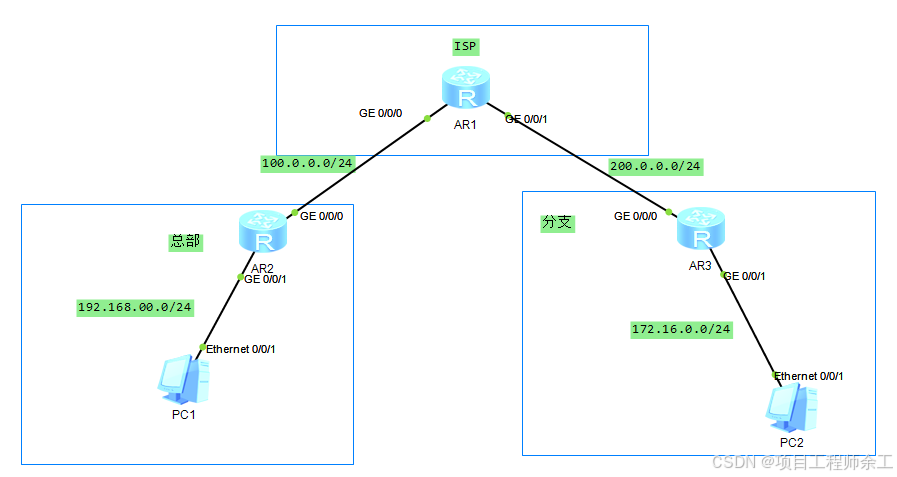
需求分析
1、ipsecvpn部署
2、总部和分支ipsec建立访问(不用隧道tunnel口)
3、使用DPD模式检测隧道存活
配置过程
1、配感兴趣流
2、ipsec安全提仪
3、ike安全提仪
4、ike对等体并关联ike安全提仪
5、ipsec安全策略并关联上面1-3步内容
6、出接口调用ipsec安全策略
R1
interface GigabitEthernet0/0/0
ip address 100.0.0.1 255.255.255.0
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
R2
dhcp enable
acl number 3000 //感兴趣流
rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.0.0 0.0.0.255
ipsec proposal ipp //ipsec安全提仪
ike proposal 1 //IKE安全提仪
ike peer r3 v1 //IKE对等体
pre-shared-key cipher Huawei@123
ike-proposal 1 //关联IKE安全提仪
dpd type on-demand //开启对等体存活检测,防止数据黑洞及时关闭隧道,类似于gre中的keepalive检测
remote-address 200.0.0.2
ipsec policy r2 1 isakmp //ipsec安全策略
security acl 3000 //关联感兴趣流
ike-peer r3 //关联IKE对等体
proposal ipp //关联ipsec安全提仪
interface GigabitEthernet0/0/0
ip address 100.0.0.2 255.255.255.0
ipsec policy r2 //调用ipsec安全策略
interface GigabitEthernet0/0/1
ip address 192.168.0.1 255.255.255.0
dhcp select interface
ip route-static 0.0.0.0 0.0.0.0 100.0.0.1
R3
dhcp enable
acl number 3000
rule 5 permit ip source 172.16.0.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
ipsec proposal ipp
ike proposal 1
ike peer r2 v1
pre-shared-key cipher %%kerE(q-se7BvE0Hy>c!=,.2n%%
ike-proposal 1
dpd type on-demand
remote-address 100.0.0.2
ipsec policy r3 1 isakmp
security acl 3000
ike-peer r2
proposal ipp
interface GigabitEthernet0/0/0
ip address 200.0.0.2 255.255.255.0
ipsec policy r3
interface GigabitEthernet0/0/1
ip address 172.16.0.1 255.255.255.0
dhcp select interface
ip route-static 0.0.0.0 0.0.0.0 200.0.0.1
DPD查看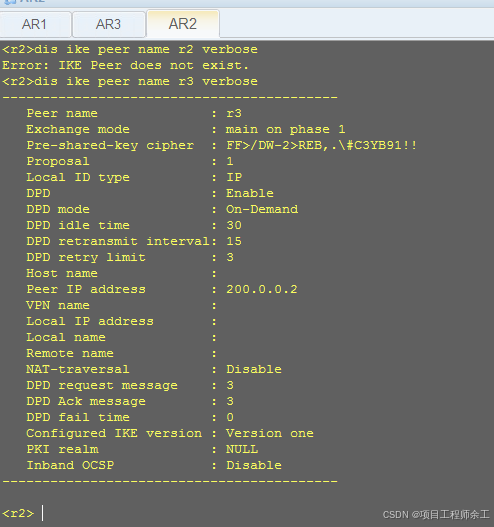
IKE建立查看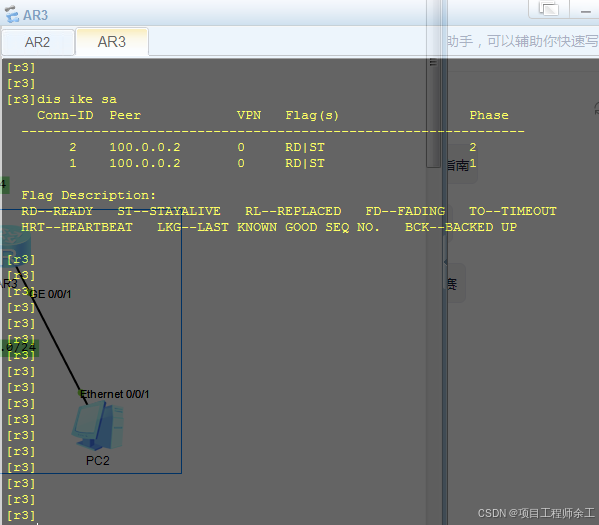
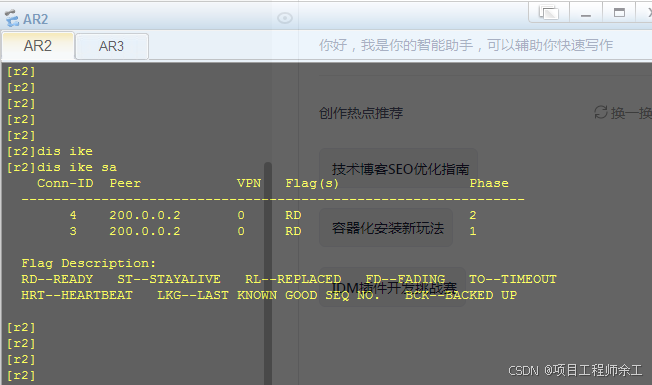
ipsec sa查看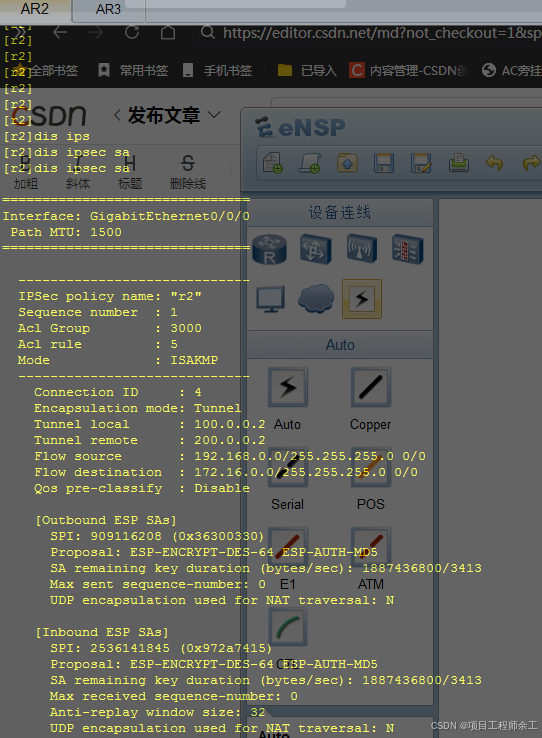
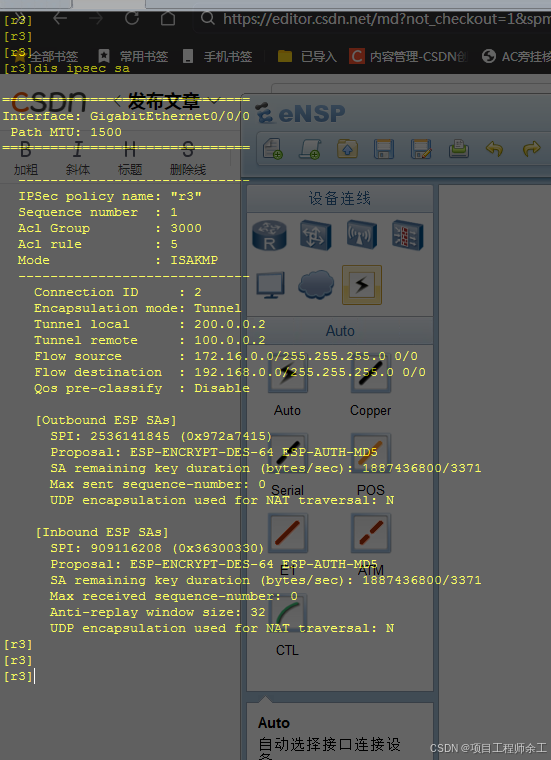
互通测试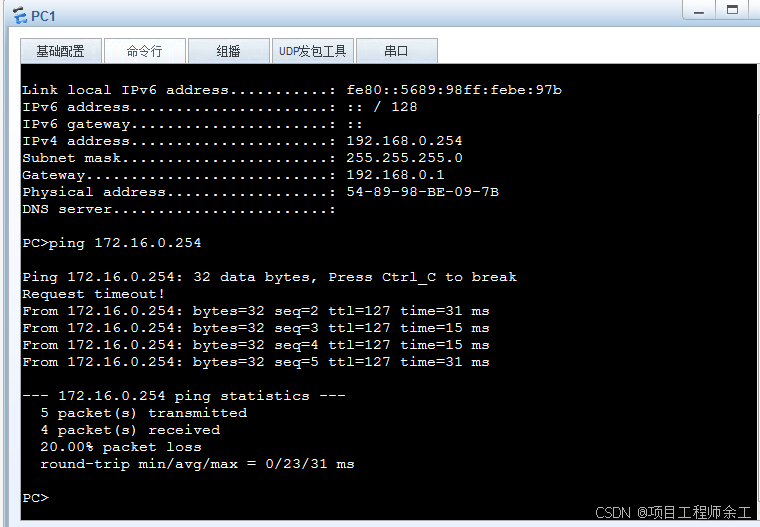
加密传输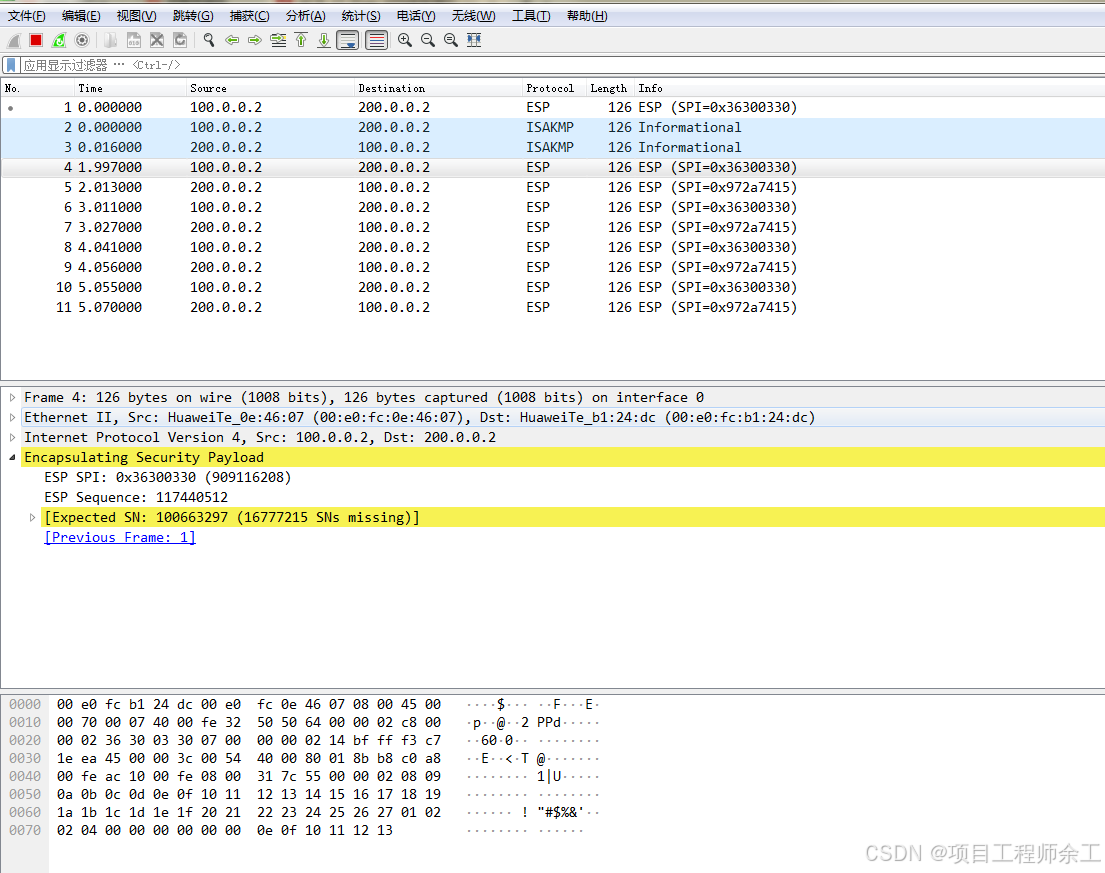



 浙公网安备 33010602011771号
浙公网安备 33010602011771号