CVE-2020-13957 Solr未授权Configset上传绕过
CVE-2020-13957跟踪分析
描述
The checks added to unauthenticated configset uploads can be circumvented.
Solr prevents some features considered dangerous (which could be used for remote code execution) to be configured in a ConfigSet that's uploaded via API without authentication/authorization. The checks in place to prevent such features can be circumvented by using a combination of UPLOAD/CREATE actions.
远程调试
solr start -c -m 1g -a "-Xdebug -Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=1044"
issue
Created:17/Jul/20 15:08
Resolved:07/Oct/20 03:56
https://issues.apache.org/jira/browse/SOLR-14925
https://issues.apache.org/jira/browse/SOLR-14663
分析一
1.The Configsets API enables you to upload new configsets to ZooKeeper, create, and delete configsets when Solr is running SolrCloud mode.
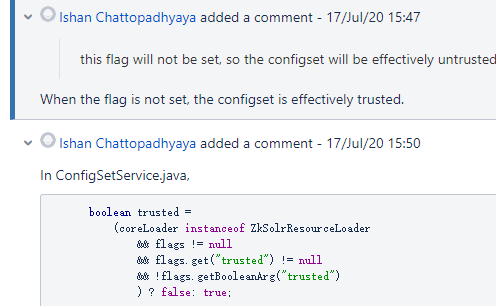
2.发现cve-2017-12629的修复补丁存在对RunExecutableListener的处理如下,得出的结论为当ConfigSet为不受信任的时候,RunExecutableListener不再被初始化。
补丁处理1:
Upload a ConfigSet, sent in as a zipped file. Please note that a ConfigSet is uploaded in a "trusted" mode if authentication is enabled and this upload operation is performed as an authenticated request. Without authentication, a ConfigSet is uploaded in an "untrusted" mode. Upon creation of a collection using an "untrusted" ConfigSet, the following functionality would not work:
- * RunExecutableListener does not initialize, if specified in the ConfigSet.
* DataImportHandler's ScriptTransformer does not initialize, if specified in the ConfigSet.
* XSLT transformer (tr parameter) cannot be used at request processing time.
* StatelessScriptUpdateProcessor does not initialize, if specified in the ConfigSet.
补丁处理2:
@Override
- public void inform(SolrCore core) {
- if (!core.getCoreDescriptor().isConfigSetTrusted()) {
- throw new SolrException(ErrorCode.UNAUTHORIZED, "The configset for this collection was uploaded without any authentication in place,"
- + " and this operation is not available for collections with untrusted configsets. To have this component, re-upload the configset"
- + " after enabling authentication and authorization.");
- }
补丁处理3:
Uwe Schindler added a comment - 18/Oct/17 08:08 - edited
Hi [~steve_rowe],
I reopen, because you removed the inform() method completely. But the original patch added a warning message inside the inform, so the user known when booting up Solr that he is using the listener. With your current commit, the user gets only an error message, but cannot see on bootup that the listener won't work.
My patch looked like this:
@@ -75,17 +91,22 @@ class RunExecutableListener extends AbstractSolrEventListener implements SolrCor
+ " and this operation is not available for collections with untrusted configsets. To have this component, re-upload the configset"
+ " after enabling authentication and authorization.");
}
+ log.warn(WARNING_MESSAGE);
}
/**
* External executable listener.
*
* @param callback Unused (As of solr 1.4-dev)
- * @return Error code indicating if the command has executed successfully. <br />
- * 0 , indicates normal termination.<br />
+ * @return Error code indicating if the command has executed successfully.
+ * 0 , indicates normal termination.
* non-zero , otherwise.
*/
protected int exec(String callback) {
+ if (!enabled) {
+ throw new SolrException(ErrorCode.UNAUTHORIZED, WARNING_MESSAGE);
+ }
+
int ret = 0;
3:修复补丁信息
@@ -297,6 +297,8 @@ Bug Fixes
---------------------
* SOLR-14751: Zookeeper Admin screen not working for old ZK versions (janhoy)
+* SOLR-14663: Copy ConfigSet root data from base ConfigSet when using CREATE command (Andras Salamon, Tomás Fernández Löbbe)
分析二
Upload a ConfigSet, sent in as a zipped file. Please note that a ConfigSet is uploaded in a "trusted" mode if authentication is enabled and this upload operation is performed as an authenticated request. Without authentication, a ConfigSet is uploaded in an "untrusted" mode. Upon creation of a collection using an "untrusted" ConfigSet, the following functionality would not work:
RunExecutableListener does not initialize, if specified in the ConfigSet.
DataImportHandler 's ScriptTransformer does not initialize, if specified in the ConfigSet.
XSLT transformer (tr parameter) cannot be used at request processing time.
StatelessScriptUpdateProcessor does not initialize, if specified in the ConfigSet.
RunExecutableListener ,DataImportHandler 都存在对应的RCE问题:
结论
1.根据当前披露的信息,在未授权的情况下可上传受信任(绕过)的ConfigSet文件,从而可能导致RCE,根据cve-2017-12629的披露信息,和分析其他CVE,猜测可以通过历史三个RCE进行利用,:CVE-2017-12629/CVE-2019-0193/CVE-2019-17558。
2.后续进行一一确认。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号