“华为杯”第二届中国研究生网络安全创新大赛初赛 RE
easy_xor
反调试直接patch
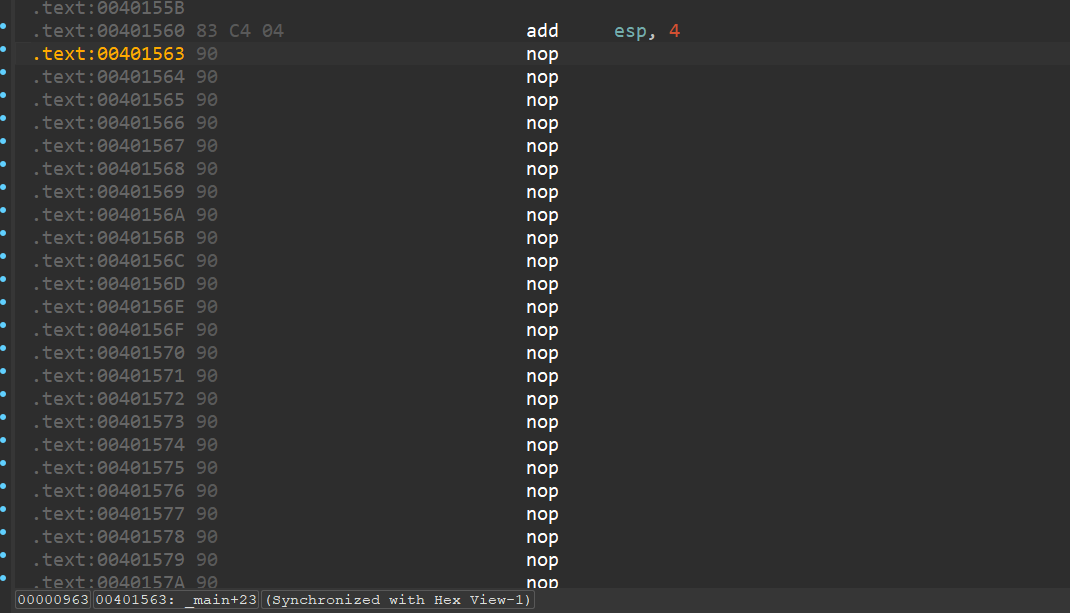
关注异或
enc=[ 0x99, 0x48, 0x5E, 0xBD, 0xC5, 0x9B, 0x85, 0x96, 0x20, 0xFC,
0x18, 0xB2, 0x00, 0xC5, 0xDA, 0xC0, 0xB1, 0xC8, 0x6C, 0x81,
0x63, 0xBD, 0x09, 0x50, 0xC2, 0xBB, 0xEC, 0x33, 0xD6, 0xD7,
0x8F, 0xAF, 0xAD, 0xCE, 0x14, 0xED, 0x8C, 0xCE, 0x6F, 0xA9,
0xA8, 0x02, 0x8C, 0x90, 0x94, 0x67]
xorkey=[ 0xFF, 0x24, 0x3F, 0xDA, 0xBE, 0xA9, 0xB6, 0xF7, 0x12, 0x8F,
0x29, 0xD0, 0x73, 0xF7, 0xF7, 0xA2, 0x83, 0xAD, 0x5F, 0xB0,
0x51, 0x90, 0x3F, 0x68, 0xF6, 0x8C, 0xC1, 0x0A, 0xB7, 0xB5,
0xBC, 0x82, 0xCC, 0xFC, 0x67, 0xDE, 0xE9, 0xFF, 0x5B, 0xCB,
0xC9, 0x67, 0xEA, 0xF6, 0xA6, 0x1A, 0x39, 0x56, 0xCA, 0x23,
0x46, 0xE3, 0xC8, 0x71, 0x43, 0x53, 0xFF, 0x72, 0x2F, 0xC3,
0x5C, 0x1C, 0x5B, 0x94]
for i in range(len(enc)):
enc[i]^=xorkey[i]
print(bytes(enc))
##b'flag{23a2s1bs2-b2e312-6847-9ab3-a2s3e14baeff2}'
Plant A tree
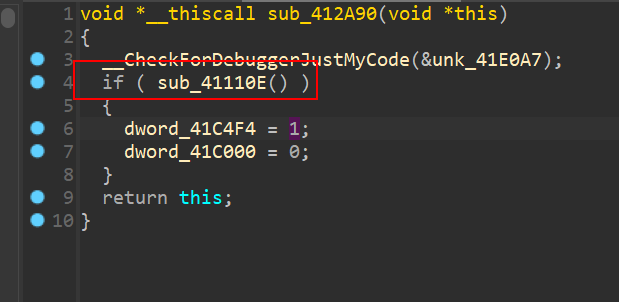
反调试,patch
enc=[0x2C, 0x40, 0xCE, 0x88, 0xEA, 0xB3, 0xA7, 0xFA, 0xBE, 0xE3,
0x32, 0xD9, 0x8B, 0xE4, 0x1C, 0x77, 0xFC, 0xD4, 0x76, 0xAB,
0x87, 0x41, 0xB0, 0xCE, 0xF5, 0x5E, 0x61, 0x86, 0xA8, 0xCF,
0x71, 0x99, 0x5C, 0xB1]
index=[4, 19, 9, 1, 24, 14, 5, 0, 18, 31, 21, 16, 11, 29, 12, 2, 30, 13, 3, 15, 8, 7, 17, 32, 33, 6, 25, 20, 26, 10, 23, 22, 27, 28]
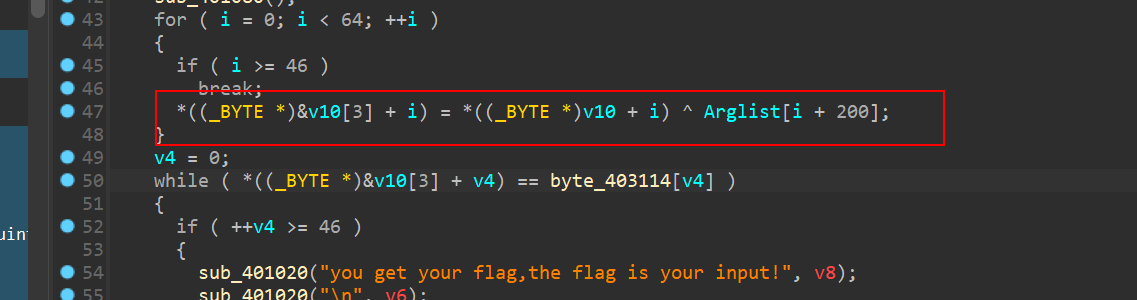
先检验长度->导入input
再RC4
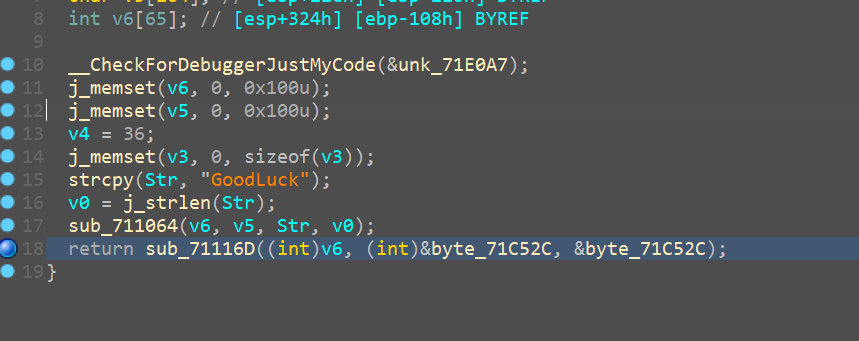
再进行自异或
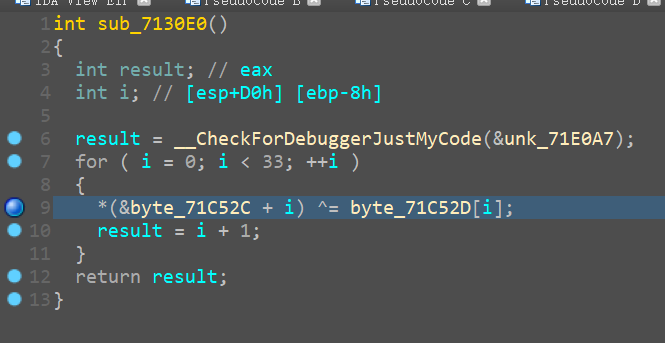
最后密文对比
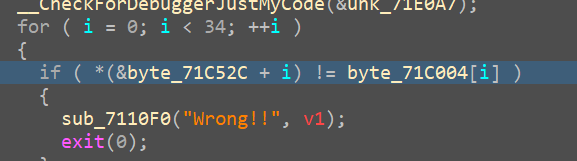
enc=[ 0x2C, 0x40, 0xCE, 0x88, 0xEA, 0xB3, 0xA7, 0xFA, 0xBE, 0xE3,
0x32, 0xD9, 0x8B, 0xE4, 0x1C, 0x77, 0xFC, 0xD4, 0x76, 0xAB,
0x87, 0x41, 0xB0, 0xCE, 0xF5, 0x5E, 0x61, 0x86, 0xA8, 0xCF,
0x71, 0x99, 0x5C, 0xB1]
for i in range(len(enc)-2,-1,-1):
enc[i]^=enc[i+1]
for i in range(len(enc)):
print(hex(enc[i])[2:].zfill(2),end='')#ffd3935dd53f8c2bd16f8cbe67ec0814639f4b3d961150e02edb85e462ca0574edb1
然后RC4
{k_leeTf@!s_rpaayvgleeM!}4_eHTm_@p
s='{k_leeTf@!s_rpaayvgleeM!}4_eHTm_@p'
m=[0]*len(s)
index=[4, 19, 9, 1, 24, 14, 5, 0, 18, 31, 21, 16, 11, 29, 12, 2, 30, 13, 3, 15, 8, 7, 17, 32, 33, 6, 25, 20, 26, 10, 23, 22, 27, 28]
for i in range(len(s)):
m[index[i]]=ord(s[i])
print(bytes(m))#b'flag{T4ee_Travel_M@kes_me_H@ppy!!}'
Robbie gave up

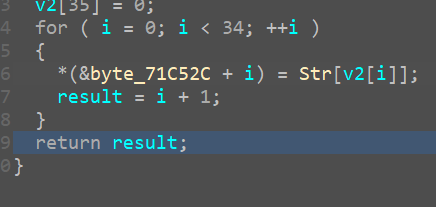
提取数据
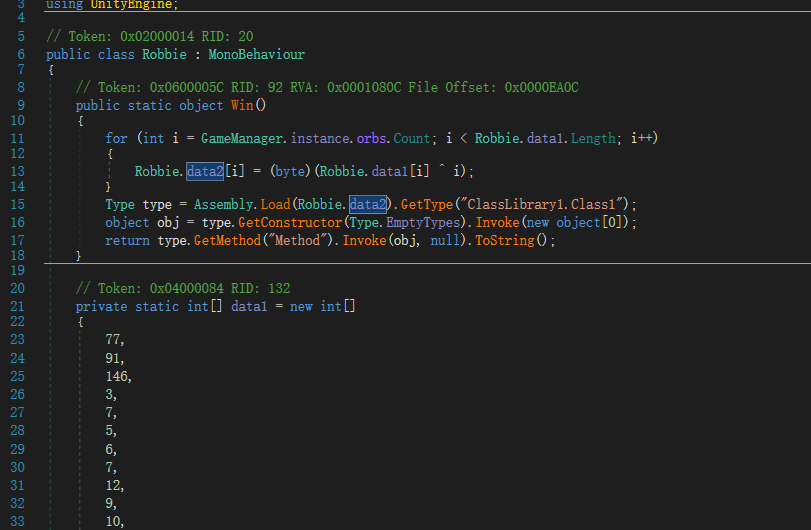
using System;
using System;
using System.Collections.Generic;
using System.Text;
namespace ConsoleApp3
{
// Token: 0x02000003 RID: 3
public class Crypt
{
// Token: 0x06000003 RID: 3 RVA: 0x00002058 File Offset: 0x00000258
public Crypt()
{
this.T = new List<char>();
this.K = "あいうえおかきくけこさしすせそたちつてとなにぬねのはひふへほまみむめもやよらりるれろわをぐげござじずぞだぢづでばびぶべぱぴぷぺぽ";
}
// Token: 0x17000001 RID: 1
// (get) Token: 0x06000004 RID: 4 RVA: 0x00002076 File Offset: 0x00000276
// (set) Token: 0x06000005 RID: 5 RVA: 0x00002150 File Offset: 0x00000350
public string Token
{
get
{
if (this.S != null)
{
return this.S;
}
return this.K;
}
set
{
this.T.Clear();
this.S = value;
if (this.S == null)
{
foreach (char item in this.K)
{
this.T.Add(item);
}
return;
}
if (this.S.Length < 64)
{
foreach (char item2 in this.S)
{
this.T.Add(item2);
}
for (int j = 0; j < 64 - this.S.Length; j++)
{
this.T.Add(this.K[j]);
}
return;
}
for (int k = 0; k < 64; k++)
{
this.T.Add(this.S[k]);
}
}
}
// Token: 0x06000006 RID: 6 RVA: 0x0000208D File Offset: 0x0000028D
public string Encode(string x)
{
if (!string.IsNullOrEmpty(x))
{
return this.InternalEncode(Encoding.UTF8.GetBytes(x));
}
return x;
}
// Token: 0x06000007 RID: 7 RVA: 0x000020AA File Offset: 0x000002AA
public string Decode(string x)
{
if (!string.IsNullOrEmpty(x))
{
return Encoding.UTF8.GetString(this.InternalDecode(x));
}
return x;
}
// Token: 0x06000008 RID: 8 RVA: 0x000020C7 File Offset: 0x000002C7
public byte[] Encode(byte[] x)
{
if (x != null)
{
return Encoding.UTF8.GetBytes(this.InternalEncode(x));
}
return null;
}
// Token: 0x06000009 RID: 9 RVA: 0x000020DF File Offset: 0x000002DF
public byte[] Decode(byte[] x)
{
if (x != null)
{
return this.InternalDecode(Encoding.UTF8.GetString(x));
}
return null;
}
// Token: 0x0600000A RID: 10 RVA: 0x000020F7 File Offset: 0x000002F7
private void CheckToken()
{
if (this.T.Count != 64)
{
this.Token = this.K;
}
}
// Token: 0x0600000B RID: 11 RVA: 0x00002240 File Offset: 0x00000440
private byte[] InternalDecode(string x)
{
this.CheckToken();
int num = 0;
int num2 = x.Length / 4;
int num3 = x.Length % 4;
byte[] array;
if (num3 == 0)
{
array = new byte[3 * num2];
}
else
{
array = new byte[3 * num2 + num3 - 1];
string text = string.Empty;
for (int i = num3; i > 0; i--)
{
text += this.ByteToBin((byte)this.T.IndexOf(x[x.Length - i])).Substring(2);
}
for (int j = 0; j < num3 - 1; j++)
{
array[3 * num2 + j] = this.BinToByte(text.Substring(8 * j, 8));
}
}
for (int k = 0; k < num2; k++)
{
string text = string.Empty;
for (int l = 0; l < 4; l++)
{
text += this.ByteToBin((byte)this.T.IndexOf(x[4 * k + l])).Substring(2);
}
for (int m = 0; m < text.Length / 8; m++)
{
array[num++] = this.BinToByte(text.Substring(8 * m, 8));
}
}
return array;
}
// Token: 0x0600000C RID: 12 RVA: 0x00002378 File Offset: 0x00000578
private string InternalEncode(byte[] x)
{
this.CheckToken();
string text = string.Empty;
int num = x.Length / 3;
int num2 = x.Length % 3;
for (int i = 0; i < num; i++)
{
string text2 = string.Empty;
for (int j = 0; j < 3; j++)
{
text2 += this.ByteToBin(x[3 * i + j]);
}
text += this.cryptEncode(text2);
}
if (num2 == 1)
{
string text2 = this.ByteToBin(x[x.Length - 1]).PadRight(12, '0');
text += this.cryptEncode(text2);
}
else if (num2 == 2)
{
string text2 = string.Empty;
for (int k = num2; k > 0; k--)
{
text2 += this.ByteToBin(x[x.Length - k]);
}
text2 = text2.PadRight(18, '0');
text += this.cryptEncode(text2);
}
return text;
}
// Token: 0x0600000D RID: 13 RVA: 0x0000245C File Offset: 0x0000065C
private string cryptEncode(string x)
{
string text = string.Empty;
for (int i = 0; i < x.Length / 6; i++)
{
text += this.T[(int)this.BinToByte(x.Substring(6 * i, 6))].ToString();
}
return text;
}
// Token: 0x0600000E RID: 14 RVA: 0x00002114 File Offset: 0x00000314
private string ByteToBin(byte x)
{
return Convert.ToString(x, 2).PadLeft(8, '0');
}
// Token: 0x0600000F RID: 15 RVA: 0x00002125 File Offset: 0x00000325
private byte BinToByte(string x)
{
return Convert.ToByte(x, 2);
}
// Token: 0x04000001 RID: 1
private string S;
// Token: 0x04000002 RID: 2
private string K;
// Token: 0x04000003 RID: 3
private List<char> T;
}
class Program
{
public static string Method()
{
string x = "はりずめはばぐだすだちずそぬけびせやのぞはとらよはやこらのとほめせだむばのだのぢはやよぢせりにやのばぢ";
return new Crypt().Decode(x);
}
static void Main(string[] args)
{
Console.WriteLine(Method());
//flag{33419b8662e9df2ea7a787c64f946ecc}
}
}
}
小林的世界
第一个挑战
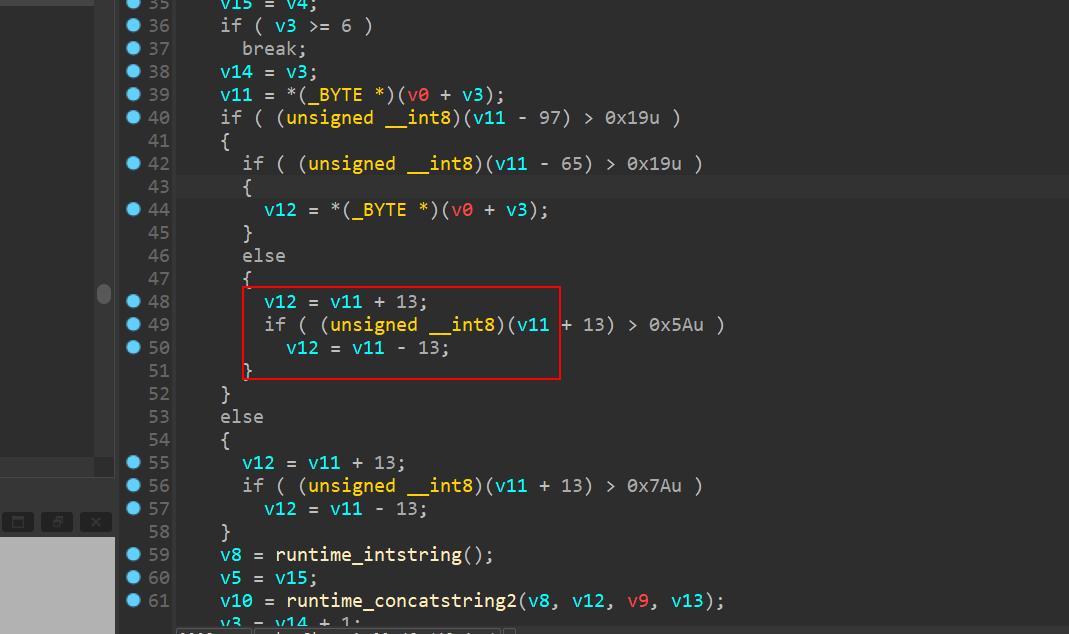
rot13,发现和最后base64解密出的DASCTF{hasaki-pdtzptz-vxnfnu}
铜钥匙 hasaki对应
挑战2,银钥匙对应vxnfnu
挑战3,密文是pdtzptz,凯撒加密,5
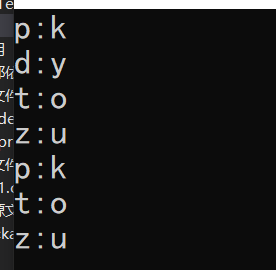
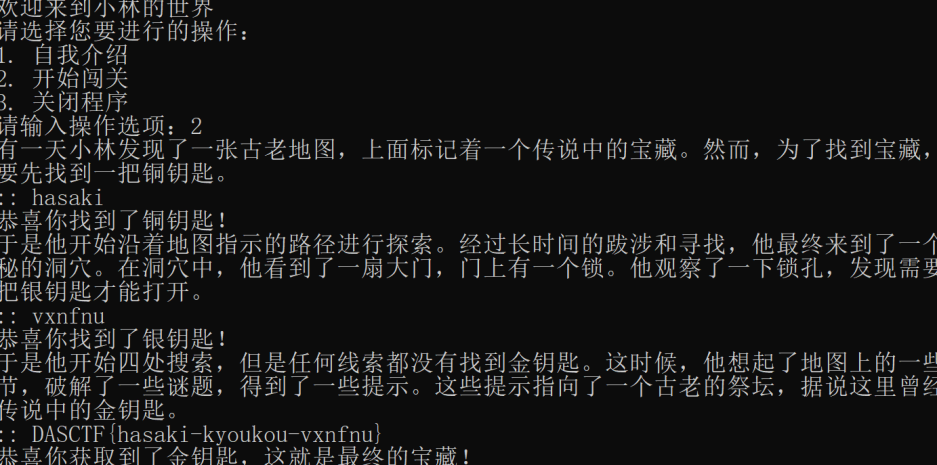
所以最后的flag为
DASCTF{hasaki-kyoukou-vxnfnu}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号