haproxy 负载均衡 https
haproxy 负载均衡 https
| DR | 192.168.170.128 |
|---|---|
| RS1 | 192.168.170.129 |
| RS2 | 192.168.170.132 |
三台虚拟机都关闭防火墙
[root@DR ~]# systemctl disable --now firewalld
Removed /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
[root@DR ~]# setenforce 0
[root@RS1 ~]# systemctl disable --now firewalld
Removed /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
[root@RS1 ~]# setenforce 0
[root@RS2 ~]# systemctl disable --now firewalld
Removed /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
[root@RS2 ~]# setenforce 0
DR上操作
[root@DR ~]# yum -y install openssl
//创建CA证书
[root@DR CA]# openssl version -a
OpenSSL 1.1.1k FIPS 25 Mar 2021
platform: linux-x86_64
options: bn(64,64) md2(char) rc4(16x,int) des(int) idea(int) blowfish(ptr)
.......
policies/back-ends/openssl.config"
OPENSSLDIR: "/etc/pki/tls" #查看openssl证书的存放路径
ENGINESDIR: "/usr/lib64/engines-1.1"
Seeding source: os-specific
engines: rdrand dynamic
//创建为根证书CA所需的目录及文件
[root@DR ~]# mkdir /etc/pki/CA
[root@DR ~]# cd /etc/pki/CA
[root@DR CA]# touch serial
[root@DR CA]# touch index.txt
[root@DR CA]# ls
index.txt serial
[root@DR CA]# echo 01 > serial //指明证书的开始编号
//生成根证书的私钥(注意:私钥的文件名与存放位置要与配置文件中的设置相匹配
[root@DR CA]# mkdir private
[root@DR CA]# openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048 //私钥默认是2048,和根证书绑定
Generating RSA private key, 2048 bit long modulus (2 primes)
.............................................................+++++
.......................................................................................................+++++
e is 65537 (0x010001)
[root@DR CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN //国名
State or Province Name (full name) []:HB //省名
Locality Name (eg, city) [Default City]:WH //城市
Organization Name (eg, company) [Default Company Ltd]:WX //公司
Organizational Unit Name (eg, section) []:YW //单位
Common Name (eg, your name or your server's hostname) []:hostlocal //名字或主机名
Email Address []: //邮箱地址
参数说明:
-new:表示生成一个新证书签署请求
-x509:专用于CA生成自签证书,如果不是自签证书则不需要此项
-key:用到的私钥文件
-out:证书的保存路径
-days:证书的有效期限,单位是day(天),默认是openssl.cnf的default_days
根证书CA就已经生成完成
[root@DR CA]# ls
cacert.pem index.txt private serial
RS1端
[root@RS1 ~]# yum -y install httpd
//创建一个放证书的路径
[root@RS1 ~]# cd /etc/httpd/
[root@RS1 httpd]# ls
conf conf.d conf.modules.d logs modules run state
[root@RS1 httpd]# mkdir ssl
[root@RS1 httpd]# cd ssl/
[root@RS1 ssl]# openssl genrsa -out test.key 2048 //生成一个私钥文件
Generating RSA private key, 2048 bit long modulus (2 primes)
.................................+++++
.............................+++++
e is 65537 (0x010001)
//把私钥文件和证书绑定在一起
[root@RS1 ssl]# openssl req -new -key test.key -out test.csr -days 365
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH\
Organization Name (eg, company) [Default Company Ltd]:WX
Organizational Unit Name (eg, section) []:YW
Common Name (eg, your name or your server's hostname) []:hostlocal
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:www.lzx.com
An optional company name []:
DR端
[root@DR ~]# cd /etc/pki/CA/
[root@DR CA]# mkdir req
[root@DR CA]# ls
cacert.pem index.txt private req serial
RS1端
[root@RS1 ssl]# pwd
/etc/httpd/ssl
[root@RS1 ssl]# scp test.csr 192.168.170.128:/etc/pki/CA/req /传到DR端的req文件夹
The authenticity of host '192.168.170.128 (192.168.170.128)' can't be established.
ECDSA key fingerprint is SHA256:xE4Baio7gSlQf+oZvM9sS8SuJW2O51GXEyIpNmn3vF8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.170.128' (ECDSA) to the list of known hosts.
root@192.168.170.128's password:
test.csr 100% 1017 801.9KB/s 00:00
DR上查看
[root@DR CA]# cd req/
[root@DR req]# ls
test.csr
//RS1端传过来的csr请求文件给CA服务器来颁发
[root@DR req]# cd ..
[root@DR CA]# mkdir newcerts
[root@DR CA]# cd req/
[root@DR req]# openssl ca -in /etc/pki/CA/req/test.csr -out /etc/pki/CA/req/test.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Aug 15 16:33:07 2022 GMT
Not After : Aug 15 16:33:07 2023 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = WX
organizationalUnitName = YW
commonName = hostlocal
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
0B:2E:E6:50:53:B1:B4:23:21:CF:3B:72:48:03:BF:6F:AB:E9:F1:AA
X509v3 Authority Key Identifier:
keyid:2B:4B:BE:62:1D:DD:74:EF:62:E5:EC:7C:64:5A:55:79:BB:B0:7C:68
Certificate is to be certified until Aug 15 16:33:07 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
//把DR上面的crt证书文件传送给RS1端下面的/etc/httpd/ssl文件
[root@DR req]# scp test.crt 192.168.170.129:/etc/httpd/ssl/
The authenticity of host '192.168.170.129 (192.168.170.129)' can't be established.
ECDSA key fingerprint is SHA256:qaKQJmPYIS5ZJ95xnw1qr/aKcWnQVf7B9KJCxs1ru9A.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.170.129' (ECDSA) to the list of known hosts.
root@192.168.170.129's password:
test.crt 100% 4388 6.1MB/s 00:00
RS1端
[root@RS1 ]# vim /etc/httpd/conf.d/ssl.conf
......
43 DocumentRoot "/var/www/html" # 两行取消注释
44 ServerName www.example.com:443
.......
85 SSLCertificateFile /etc/httpd/ssl/test.crt # 修改为证书存放文件位置
......
93 SSLCertificateKeyFile /etc/httpd/ssl/test.key # 修改为密钥文件存放位置
.....
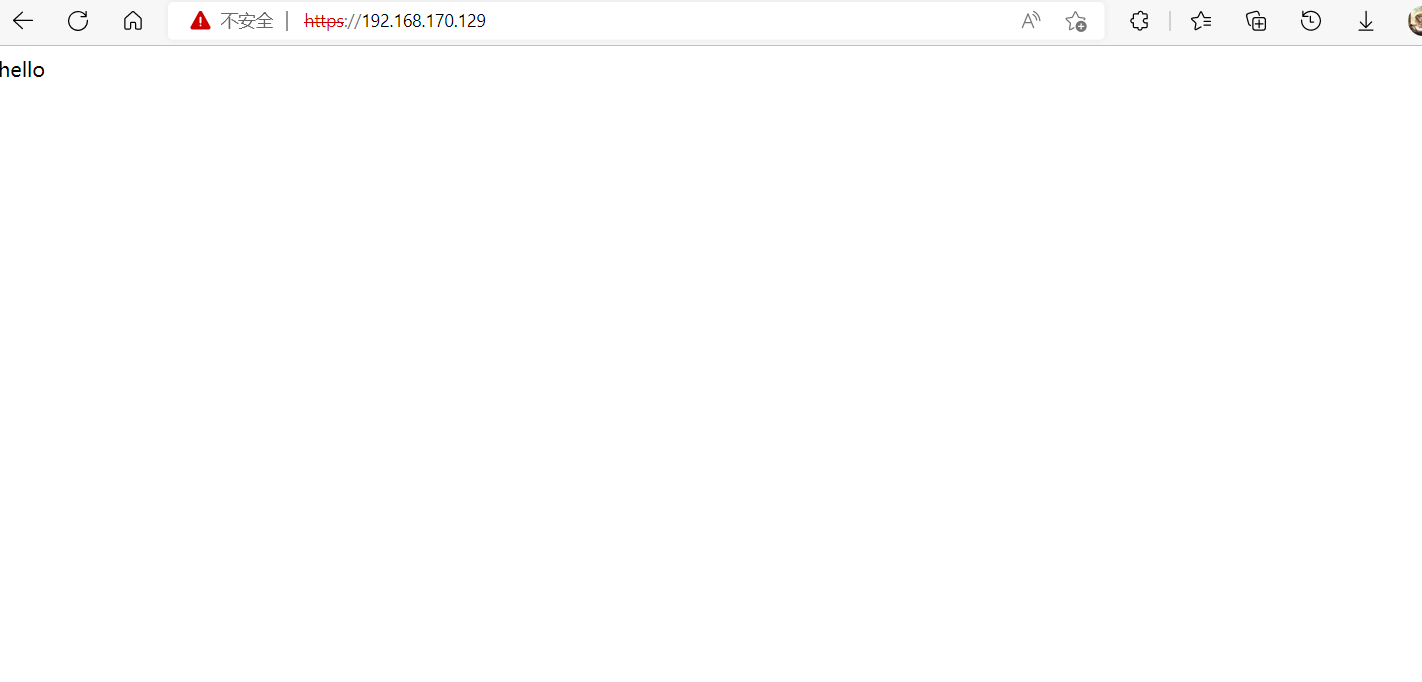
[root@RS1 ]# echo "hello" > /var/www/html/index.html
重启
[root@RS1 ssl]# systemctl restart httpd
[root@RS1 ssl]# ss -antl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 5 127.0.0.1:631 0.0.0.0:*
LISTEN 0 128 0.0.0.0:111 0.0.0.0:*
LISTEN 0 32 192.168.122.1:53 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 5 [::1]:631 [::]:*
LISTEN 0 128 *:443 *:*
LISTEN 0 128 [::]:111 [::]:*
LISTEN 0 128 *:80 *:*
web页面


 浙公网安备 33010602011771号
浙公网安备 33010602011771号