强网拟态决赛_re_movemove
demovfucator可以去除一些混淆
https://github.com/kirschju/demovfuscator
之后便可以F5
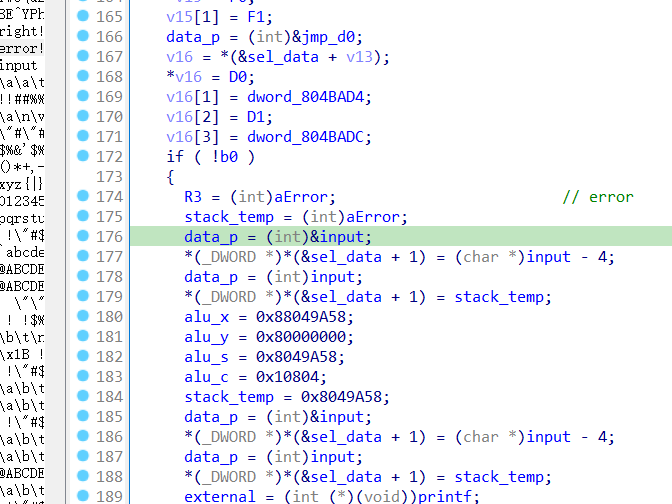
这里的if判断,手动fuzz了一下,发现可以进行单字节爆破
祭出很久没用的pintools进行爆破
pintools脚本
// 强网拟态决赛 · 32位elf文件 ,最常规的pintools爆破 #include <iostream> #include <fstream> #include "pin.H" using std::cerr; using std::endl; using std::string; static UINT64 icount = 0; VOID docount(VOID* addr) { if ((int)addr == 0x804990F) { icount++; } } VOID Instruction(INS ins, VOID* v) { INS_InsertCall(ins, IPOINT_BEFORE, (AFUNPTR)docount, IARG_INST_PTR, IARG_END); } KNOB< string > KnobOutputFile(KNOB_MODE_WRITEONCE, "pintool", "o", "inscount.out", "specify output file name"); VOID Fini(INT32 code, VOID* v) { std::cout << "Count " << icount << endl; } INT32 Usage() { cerr << "This tool counts the number of dynamic instructions executed" << endl; cerr << endl << KNOB_BASE::StringKnobSummary() << endl; return -1; } int main(int argc, char* argv[]) { if (PIN_Init(argc, argv)) return Usage(); INS_AddInstrumentFunction(Instruction, 0); PIN_AddFiniFunction(Fini, 0); PIN_StartProgram(); return 0; }
python爆破脚本:
# pintools 爆破 # 下面是爆破脚本 # 这里我直接把指令输出到控制台上然后获取 # md 字符表太长,抽空优化一下,还要设置一个break的选项... import subprocess import time import copy STR_LEN = 30 start_time = time.time() out_file_path = r"ttext.txt" dll_path = r"/home/tlsn/Desktop/QWNT_js/MyPinTool.so" exe_path = r"/home/tlsn/Desktop/QWNT_js/movemove" record_ins_nums = {} # 指令计数器 except_str = "" #flag{m0v3Fu3c@t0r_i3_7uring_C0mp1ete} except_inss = 0 find_str = "" # s_map = "0123456789qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM_-{}@#$!^&*().?<>," s_map = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{}@_#" s_map2 = "!@#$%^&*()_+-=QWERTYUIOP[]ASDFGHJKL;\'ZXCVBNM,./?><" def sub_intreaction(input_msg): global start_time sh = subprocess.Popen(['pin','-t',dll_path,'-o',out_file_path,'--',exe_path], stdin=subprocess.PIPE, stdout=subprocess.PIPE, stderr=subprocess.PIPE) sh.stdin.write(str.encode(input_msg.ljust(37,"0"))) # 必须补齐,不然后面的sh.stdout 会出错 # 即将缓冲区中的数据立刻写入文件,同时清空缓冲区,不需要是被动的等待输出缓冲区写入 sh.stdin.flush() sh.stdout.flush() get_input = sh.stdout.readlines() # print(get_input[1]) record_ins_nums[input_msg] = int(get_input[1][6:]) sh.kill() print(input_msg," : ",get_input) if b"right" in get_input[0]: print("Oh,my sir, you may got the flag:") print(input_msg) print(time.time() - start_time) exit() return def intreaction(): for i in range(len(s_map)): sub_intreaction(except_str + s_map[i]) def pintools(): global except_str,v,record_ins_nums,except_inss intreaction() ans = 0 for k,v in record_ins_nums.items(): if v >= except_inss: # 出错原因,之前用的 '>' 号,发现input_msg 填充的数据 0 也是input的数据,导致 0123456789 和 01234567890 指令数一样,从而导致无线循环 if v > except_inss: ans = 1 except_str = copy.deepcopy(k) except_inss = v if ans == 0: print("可能发生了错误,遍历一遍字符表后,icount的数量没有增加...请更改字符表或者爆破条件") # exit() print(except_str," ",except_inss) record_ins_nums = {} pintools() if __name__ == '__main__': pintools()
漫长的爆破后,爆破结果如下:
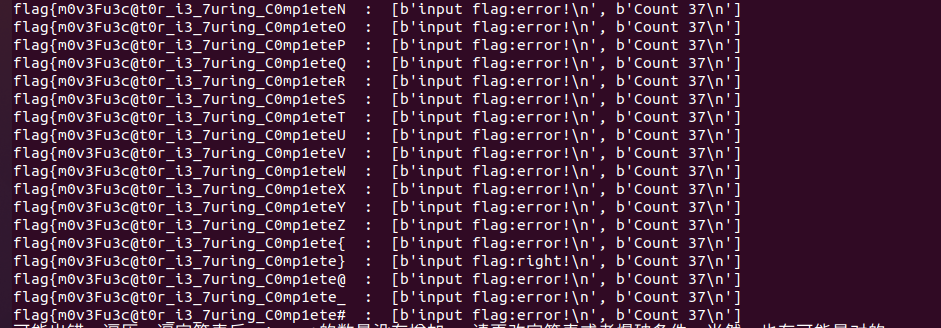
flag即为:
flag{m0v3Fu3c@t0r_i3_7uring_C0mp1ete}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号